The financial sector resembles a treasure vault under constant siege. Banks, insurers, and fintech firms are not just custodians of money. They are guardians of irreplaceable personal and corporate data, payment flows, transactional integrity, and trust itself.
When cybercriminals strike, the ripple effects cascade outward, threatening individual savings, corporate balance sheets, national infrastructures, and broader economic confidence.
The Biggest Cybersecurity Risks for Financial Businesses
The threat landscape for finance keeps getting worse, and the numbers make that clear:
- 90% of attacks start with phishing, based on sandbox analyses from 15,000 organizations using ANY.RUN’s solutions
- 65% of financial organizations were hit by ransomware, the highest rate across industries
- Ransomware recovery costs reached $2.73M on average in 2024, excluding ransom payments (Sophos)
- Nearly one-third of attacks bypass existing defenses, despite increased security spend (Picus Blue Report)
- 14.5 million stolen credit cards were listed on underground markets in 2024, a 20% YoY increase (Bitsight)
Together, these numbers point to the same underlying risk: attacks are getting faster, stealthier, and more expensive, while traditional controls struggle to keep up.
For financial organizations, even small gaps in visibility or delayed decisions can lead to halted transactions, customer impact, and regulatory scrutiny. The difference between early detection and late response is not measured in alerts, but in downtime avoided, losses prevented, and trust preserved.
Why Traditional Cyber Defenses Are Not Enough in Finance
Most financial SOCs already have SIEM, EDR, and email security in place. The problem is not a lack of tools, but a lack of actionable data on the latest attacks that can help them prevent incidents rather than react to them.
Common issues include:
- Too many alerts, too little context: SOC analysts in financial organizations spend hours validating indicators with no clear verdict.
- Late visibility into real campaigns: Traditional threat intelligence sources provide information on threats after damage has started elsewhere.
- Slow escalation decisions: Teams hesitate between false positives and overreaction.
- High investigation costs: Manual research consumes Tier 1 and Tier 2 capacity.
These gaps directly translate into higher MTTR, higher incident costs, and higher operational risk.
How Threat Intelligence Helps Reduce Business Risks

Threat intelligence changes the situation by shifting security from reaction to prevention. Instead of waiting for incidents to unfold, it lets SOC teams spot and stop threats earlier in the attack lifecycle.
ANY.RUN’s Threat Intelligence supports this across three core SOC processes.
Monitoring: Spot Threats Before They Reach Your Infrastructure

ANY.RUN’s Threat Intelligence Feeds bring unique advantages to financial institutions seeking to strengthen their defensive posture against the sophisticated threats targeting the sector.
TI Feeds are powered by a global community of over 600,000 cybersecurity professionals and 15,000+ organizations who analyze threats daily in ANY.RUN’s Interactive Sandbox.
Plus, each indicator comes with a sandbox analysis that gives SOC teams a full attack context that eliminates the need for additional investigations and allows analysts to move on to the remediation stage instantly, significantly cutting MTTR.
What this means for your SOC and business:
- 36% higher detection rate of threats: Helps SOC teams spot real threats to the financial industry before they reach critical systems, reducing the risk of fraud and service outages.
- Visibility into emerging attacks not covered by traditional feeds: Gives security teams a head start on new campaigns, lowering the chance of being hit by previously unseen threats.
- Cleaner alerts with fewer false positives: Analysts spend less time on noise and more time on real incidents, keeping response fast during peak attack periods.
- Faster triage and confident response decisions: Clear context around indicators shortens investigations and limits attacker dwell time in financial environments.
- Proactive protection instead of reactive firefighting: Threats are blocked earlier, helping prevent business disruption, regulatory exposure, and customer impact.
Indicators can be streamed directly into SIEM and SOAR platforms using APIs, SDKs, and STIX/TAXII, enabling automated detection, enrichment, and response without changing established workflows.
Triage: Make Faster, More Confident Security Decisions

Threat Intelligence Lookup gives analysts immediate context for suspicious IPs, domains, URLs, and over 40 other types of indicators. This helps financial SOCs close more alerts faster and with more confidence, reducing the risk of a missed attack and a resulting business impact due to incidents.
What this means for your SOC and business:
- Clear understanding of threats to your company: Analysts immediately see whether an indicator is tied to real malicious activity, reducing uncertainty and missed risks.
- 21-minute faster MTTR: Alerts are validated or closed quickl, helping SOC teams stay in control even when attack volume increases.
- Lower investigation effort per incident: Less manual research means faster containment and fewer resources spent on non-critical alerts.
Shorter investigations mean lower response costs and reduced operational impact during incidents.
To demonstrate how TI Lookup accelerates the triage processes, we simulate a typical scenario where a SOC analyst needs to verify an alert about a suspicious URL. Instead of checking it across multiple sources and wasting precious time, the analyst can submit it to TI Lookup and get a 2-second response with full context.
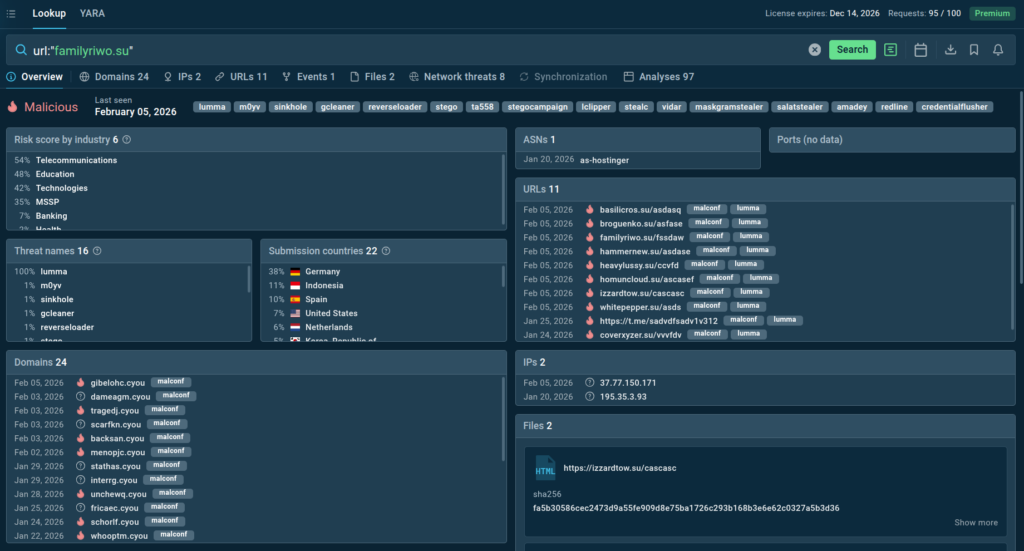
TI Lookup shows that this URL is related to a currently active Lumma Stealer campaign, which has been observed by companies in banking, telecommunications across Germany, Spain, and the United States.
Threat Hunting: Find Risks Before Alerts Exist
Threat Intelligence Lookup also supports proactive threat hunting by exposing patterns across real campaigns, not just isolated IOCs.
What this enables:
- Focus on threats that actually matter: Hunters prioritize campaigns, techniques, and infrastructure relevant to financial organizations, not generic threat noise.
- Earlier visibility into hidden or low-noise attacks: Real attack patterns help uncover threats before they escalate into full incidents.
- More effective detection improvements: Hunting insights translate into better rules and coverage, reducing blind spots over time.
Earlier risk exposure prevents silent compromises that lead to major incidents later.
For example, TI Lookup provides a clear picture of the current threat landscape for companies in different industries and countries.
By combing the three parameters for the industry, country, and threat type, we can instantly see phishing threats facing financial organizations in the United Kingdom:
industry:”Finance” AND submissionCountry:”gb” and threatName:”phishing”
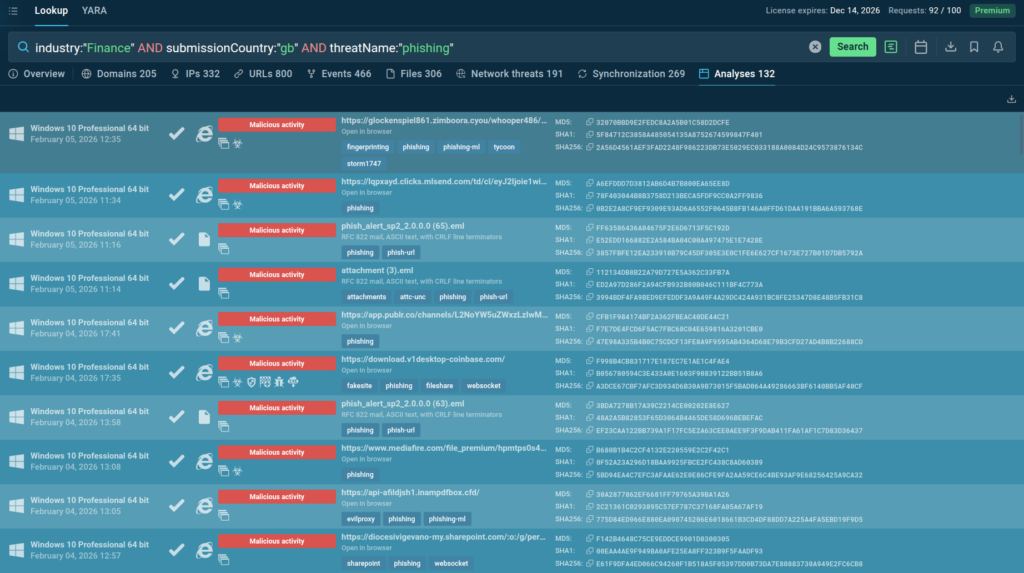
TI Lookup shows the latest phishing attacks analyzed in the sandbox, allowing analysts to view each of them to study the current attack flows used by criminals.
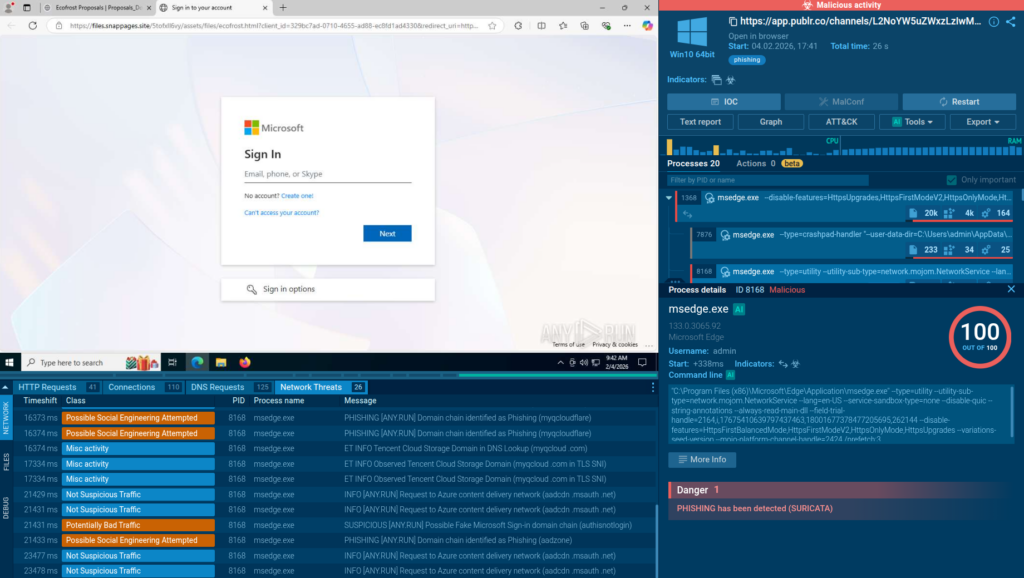
Fresh, extensive intelligence from TI Lookup gives SOC teams the ability to enrich the existing detection capabilities and ensure that the organization’s defenses stay relevant and impenetrable for active attacks.
Business Outcomes of Integrating Threat Intelligence in Finance
ANY.RUN’s Threat Intelligence delivers value when it protects business operations, not just SOC metrics.
Key outcomes include:
- Risk Reduction: By enabling earlier detection and prevention of attacks, threat intelligence directly reduces the probability and impact of security incidents. This translates to lower financial losses from breaches, reduced regulatory fines, and minimized business disruption.
- Compliance Demonstration: Documentation of threat intelligence integration shows due diligence to auditors and regulators, supporting compliance with frameworks like PCI DSS, GDPR, DORA, and SEC cybersecurity rules.
- Operational Efficiency: Automated threat intelligence integration reduces the manual effort required for threat research and indicator validation. Security teams can handle more alerts with the same resources, improving overall SOC efficiency and enabling organizations to do more with existing budgets.
- Cost Optimization: While threat intelligence feeds represent an investment, they deliver ROI through reduced breach costs, lower cyber insurance premiums, minimized overtime and emergency response costs, and decreased need for expensive forensics and recovery services.
- Customer Trust and Reputation: Demonstrating robust security measures through threat intelligence integration helps maintain customer confidence.
For financial institutions, these outcomes directly protect revenue and operational continuity.
Conclusion
Threat intelligence is most effective when it supports clear decisions at the right time. By combining early signals, real attack context, and continuous updates, SOC teams can act before small issues turn into business-critical incidents.
That is where security starts protecting the business, not after the damage is done.
About ANY.RUN
ANY.RUN develops advanced solutions for malware analysis and threat hunting, trusted by 600,000+ cybersecurity professionals worldwide.
Its interactive malware analysis sandbox enables hands-on investigation of threats targeting Windows, Linux, and Android environments. ANY.RUN’s Threat Intelligence Lookup and Threat Intelligence Feeds help security teams quickly identify indicators of compromise, enrich alerts with context, and investigate incidents early. Together, the solutions empowers analysts to strengthen overall security posture at financial institutions and banks.
Request ANY.RUN access for your company
FAQ
Because it combines direct access to money, sensitive personal data, and critical infrastructure with strict uptime and regulatory pressure.
Threat intelligence exposes malicious infrastructure, tools, and behaviors at the earliest stages of attacks, enabling preventive blocking.
By enriching alerts with context, it helps analysts quickly distinguish real threats from false positives and prioritize incidents.
Yes. It supports continuous monitoring, documented response processes, and risk-based security controls required by financial regulations.
ANY.RUN combines real-time threat feeds with interactive analysis and deep behavioral context, making intelligence immediately actionable.







0 comments