In the rapidly evolving landscape of cybersecurity, access to high-quality threat intelligence feeds is crucial for detecting and mitigating threats in real time. Not all feeds are created equal, however, and choosing the right one can make a significant difference in your organization’s defense strategy.
Let’s explore five key characteristics of good threat intelligence feeds and demonstrate how ANY.RUN meets these essential standards.
Quality of indicators
False positives can cause unnecessary alerts, diverting the security team’s focus from real threats.
A good threat intelligence feed should focus on the accuracy and relevance of indicators. High-quality feeds filter out false positives, duplicates, and outdated data to ensure that the indicators of compromise (IOCs) are actionable.
At ANY.RUN, we emphasize the purity of our data. Our feed data undergoes rigorous pre-processing, leveraging advanced algorithms and proprietary technology to minimize false positives.
Thanks to our interactive sandbox, we capture valuable information such as domains and URLs from each session, ensuring that our users get only the most relevant and accurate IOCs in their feeds.
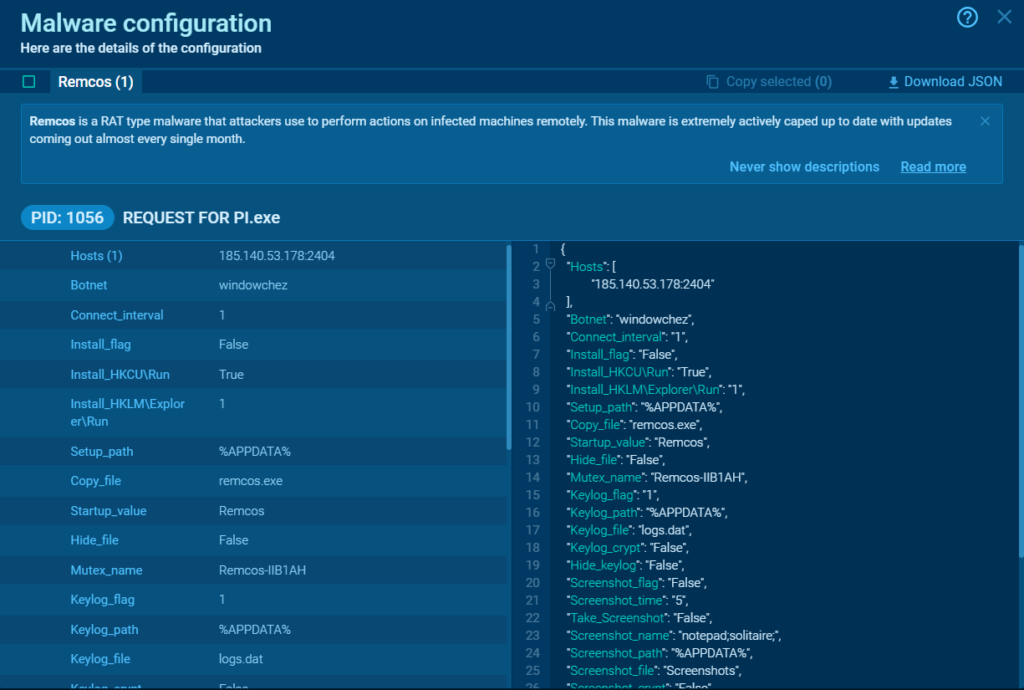
We also extract IOCs from malware configurations. This is the most valuable source of quality IOCs, as it contains critical data that threat actors use to run their operations.
Volume of threat data
While quality is essential, the quantity of data should not be overlooked. A good threat intelligence feed draws from a large, diverse pool of sources to provide a broad view of emerging threats. The more varied and widespread the data sources, the more comprehensive the threat intelligence.
At ANY.RUN, we have an expansive community of over 500,000 analysts from around the globe, continuously submitting fresh samples of malware and phishing to our sandbox for analysis. In Q2 2024 only, ANY.RUN users ran 881,466 public interactive analysis sessions.
This ensures our threat intelligence feeds are populated with indicators from various geographical regions and attack vectors.
Freshness of data
The speed at which threat intelligence feeds are updated is another critical factor. Timely data is essential for defending against fast-moving cyber threats. Feeds that rely on outdated data leave organizations vulnerable to attacks. The best feeds provide real-time or near-real-time updates to ensure their users stay ahead of emerging threats.
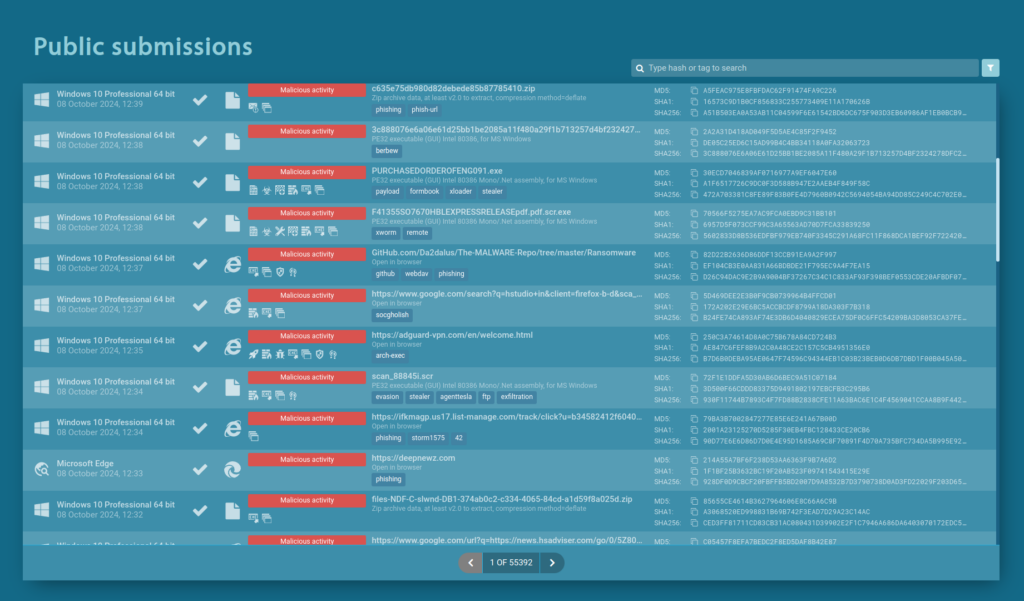
ANY.RUN’s Threat Intelligence Feeds are continuously updated in real time, drawing from live analysis sessions in our sandbox environment. This rapid update cycle ensures that our users receive fresh data on the latest threats, significantly reducing the detection lag. With near real-time updates, security teams can react quickly to new threats and enhance their overall defense strategy.
Data enrichment
Basic threat feeds usually offer limited information, such as IP addresses or file hashes. However, enriched threat intelligence provides valuable context, such as TTPs, URLs, and full analysis reports. This additional context allows security teams to better understand the nature of the threat, enabling more effective responses.
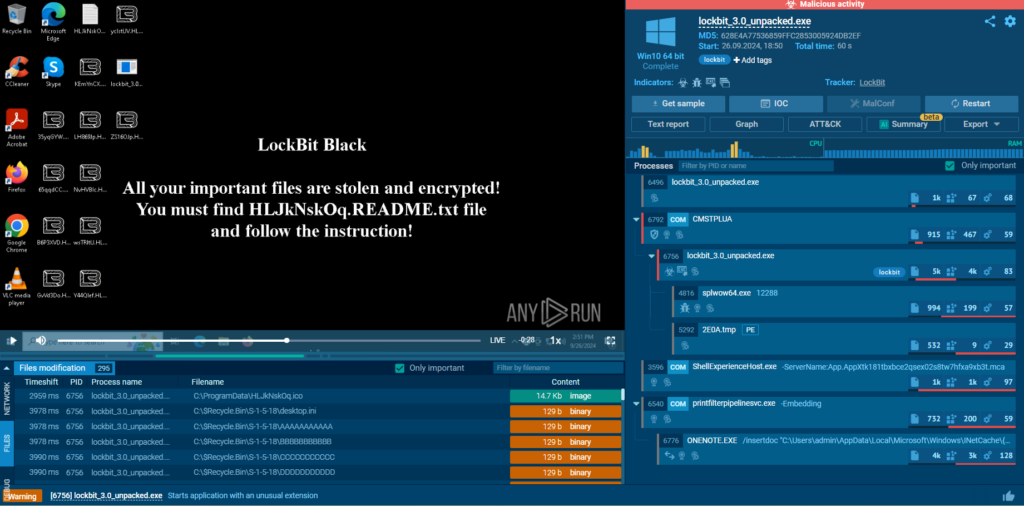
Our feeds go beyond simple IOCs by providing direct links to full sandbox analysis sessions. For each indicator in our feeds, users can view the entire malware interaction, including memory dumps, network traffic, and event timelines.
This level of enrichment gives analysts deeper insight into the behavior of the malware, helping them make more informed decisions. Moreover, we support integrations with tools like OpenCTI to pull in even more enriched data for a holistic analysis.
Compatibility and format
Threat intelligence feeds should be easy to integrate into existing systems, using widely supported formats such as STIX or TAXII. Compatibility is key to ensuring that feeds can be effectively utilized by Security Information and Event Management systems, Threat Intelligence Platforms, and other security tools.
At ANY.RUN, we deliver our threat intelligence feeds in the STIX format, making it simple for security teams to integrate our data into their existing infrastructure. Here is how it looks like:
{
"type": "ipv4-addr",
"id": "ipv4-addr--8c851c0c-ee42-5e7e-af06-f849efc0ffb4",
"value": "194.104.136.5",
"created": "2022-04-20T15:05:54.181Z",
"modified": "2024-02-19T11:21:47.728Z",
"external_references": [
{
"source_name": "ANY.RUN task c761d29c-a02a-4666-bc34-b89c4aab5cd1",
"url": "https://app.any.run/tasks/c761d29c-a02a-4666-bc34-b89c4aab5cd1"
},
{
"source_name": "ANY.RUN task 49e5fc75-a203-4d98-b055-ce41b0597a42",
"url": "https://app.any.run/tasks/49e5fc75-a203-4d98-b055-ce41b0597a42"
},
{
"source_name": "ANY.RUN task 3438d5ce-3cfa-4ccc-9638-5d92ad34b406",
"url": "https://app.any.run/tasks/3438d5ce-3cfa-4ccc-9638-5d92ad34b406"
},
{
"source_name": "ANY.RUN task e4ca3451-ce2c-4974-a6f5-baf3e81b5aff",
"url": "https://app.any.run/tasks/e4ca3451-ce2c-4974-a6f5-baf3e81b5aff"
}
],
"labels": [
"RedLine"
]
}The STIX format ensures that our enriched threat data is compatible with a wide variety of tools and platforms, enabling organizations to seamlessly incorporate our feeds into their broader threat detection and response workflows.
Read more about ANY.RUN’s TI Feeds in the official documentation.
Try Demo TI Feeds from ANY.RUN
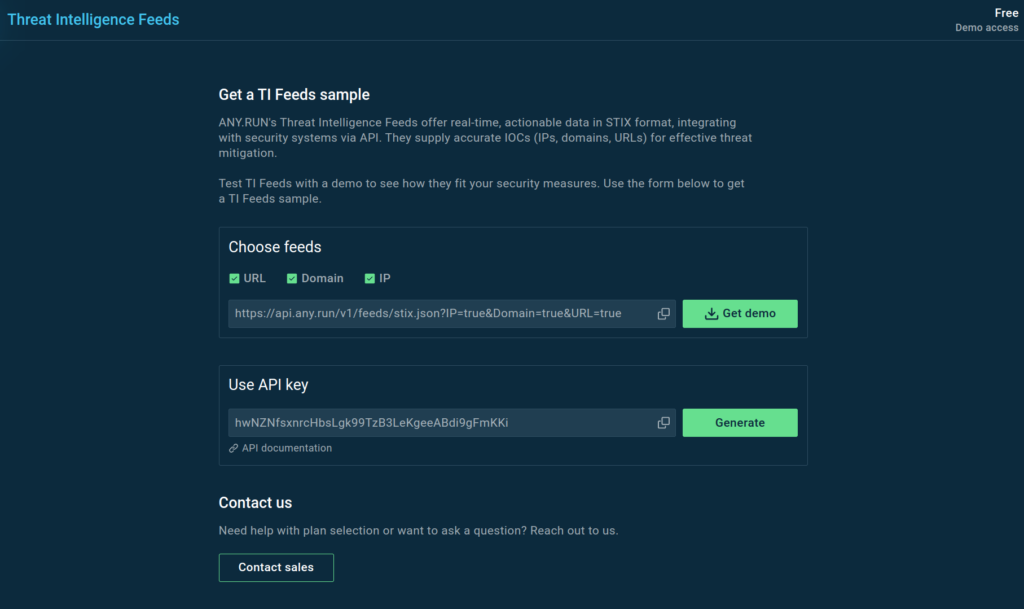
You can experience the power of threat intelligence feeds with ANY.RUN. Our feeds include accurate IOCs for precise threat identification:
- Command-and-control (C2) IP addresses: Addresses used by malware to communicate with attackers.
- URLs and domain names: Suspicious sites associated with malicious activities.
Try a demo sample of our TI Feeds to test them and see how they can contribute to your security.
Wrapping up
Good threat intelligence feeds are accurate, comprehensive, timely, enriched with contextual information, and easy to integrate. ANY.RUN’s Feeds check all these boxes, offering a robust solution to stay ahead of the ever-evolving threat landscape.
Whether you’re a small business or a large enterprise, integrating high-quality threat intelligence like ours can significantly enhance your cybersecurity posture.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need








0 comments