Our threat intelligence product lineup has recently expanded with an exciting new release — YARA Search, a service for searching malicious files by their content.
Who can use the service?
If you’ve purchased a quota for our ANY.RUN Threat Intelligence products, your quota already includes requests for Lookup and YARA Search.
Not using our TI products yet? No problem – request a trial period from our support team.
We outlined what YARA Search can do in the release post. Today, we’d like dive deeper into its interface and show you how to actually use it.
How YARA Search assists analysts
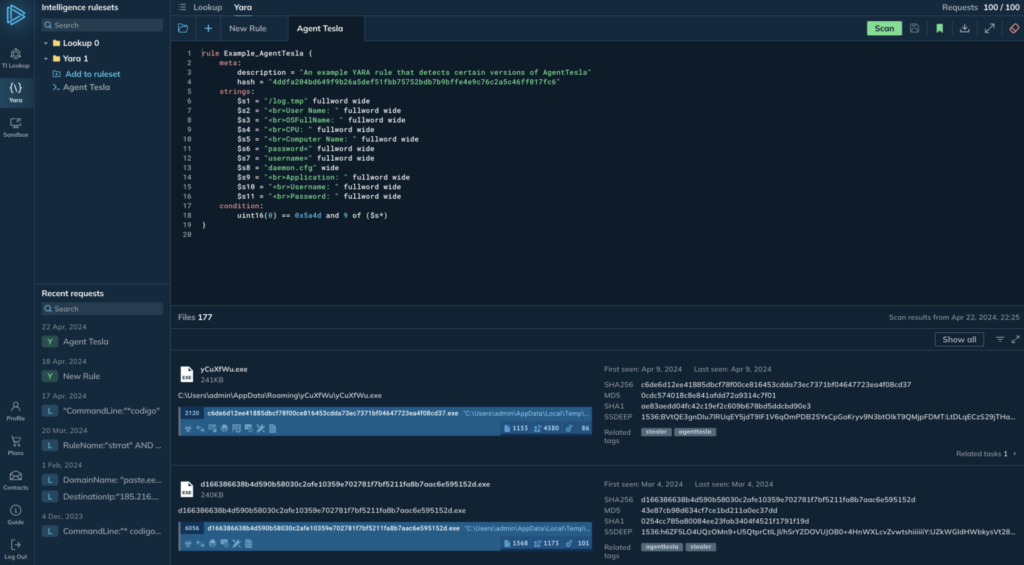
In YARA Search, analysts can hunt for malicious file samples using YARA rules. The search scans our 2TB database of malware samples, which contains threats identified by analysts and enriched with real-world examples of malware in action.
This provides you, as a user, with a valuable resource for working with YARA rules:
- Write new YARA Rules or test and validate existing ones.
- Discover samples for further analysis.
- Download files for reversing.
It takes just 5 seconds for the first matched files to render. You can run multiple searches in parallel or switch between TI Lookup and YARA Search and your YARA searches will keep working in the background.
(Note: You will lose the progress of your TI Lookup request if you leave the TI tab before your search is complete. However, this is not a problem: TI Lookup returns results almost instantly.)
As for the intuitive interface, it will take you only a minute to get used to it, and we will highlight all the main features below.
YARA Search Homescreen
When you first open the YARA Search app, you’ll see the Homescreen organized into three main sections:
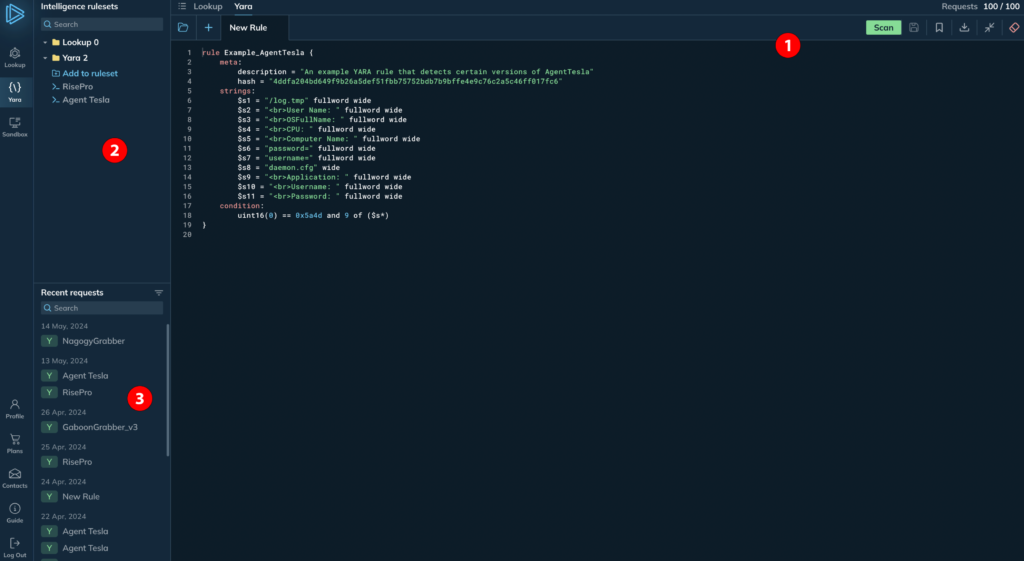
- Online editor: This is the central area where you can write and validate your YARA rules. The online editor takes up the majority of the screen, making it easy to focus on crafting your rules.
- Your Rules and Lookups: On the left sidebar, you’ll find two sections. The upper section allows you to save and manage your YARA rules. This is also where you can access any saved Lookup queries you’ve created previously.
- Recent searches: At the bottom of the left sidebar, you’ll see a history of your most recent searches, providing quick access to rules and queries you’ve worked on recently.
Let’s break down each of these sections in more detail, starting with the online editor.
Online editor
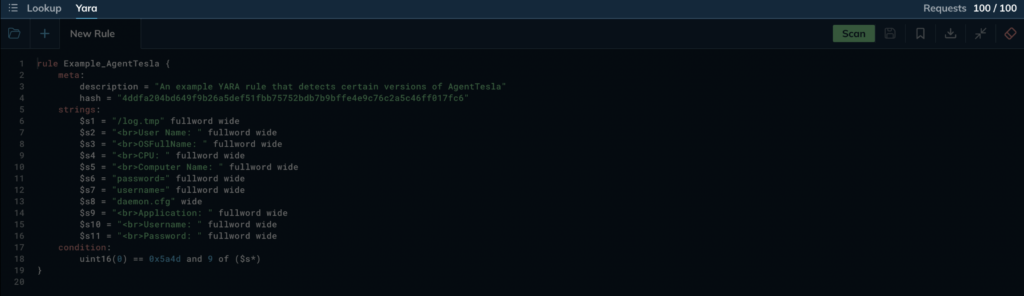
At the top you’ll find the tabs that allow you to switch between YARA Search and Lookup.
The application remembers the last state and your active searches remain in progress when you switch between the two tabs.
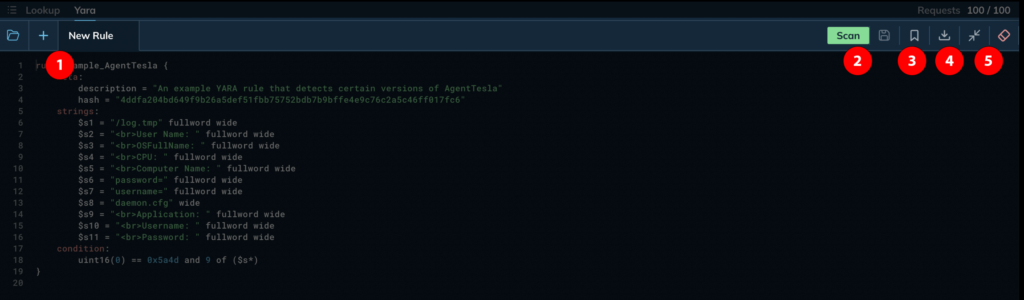
Below, you’ll find a row of buttons for managing your YARA rules and the online editor:
- Rule management buttons: On the left side, there are buttons for uploading a YARA rule from a file on your system, creating a new empty tab, and managing your existing editor tabs containing YARA rules.
- Scan button: This button initiates a new search using the rules you’ve written or loaded into the editor.
- Save button: Clicking the ribbon-shaped button saves the current rule to your personal collection of saved rules in the sidebar.
- Download button: If you need to download a copy of the rule to your local system, you can use the download button.
- Editor size button: The arrows button allows you to minimize or expand the size of the online editor window, giving you more or less screen real estate as needed.
Finally, the rightmost red eraser icon resets the content of the online editor, providing a clean slate for you to start writing a new rule from scratch.
The text editor itself is feature-rich. It comes with syntax highlighting, tabulation, and keyboard shortcuts to make writing and editing rules convenient.
Intelligence rulesets
This sidebar section allows you to manage your personal collection of saved YARA rules. Simply hover over any rule, and a […] icon will appear. Clicking this icon reveals a context menu with several handy options.
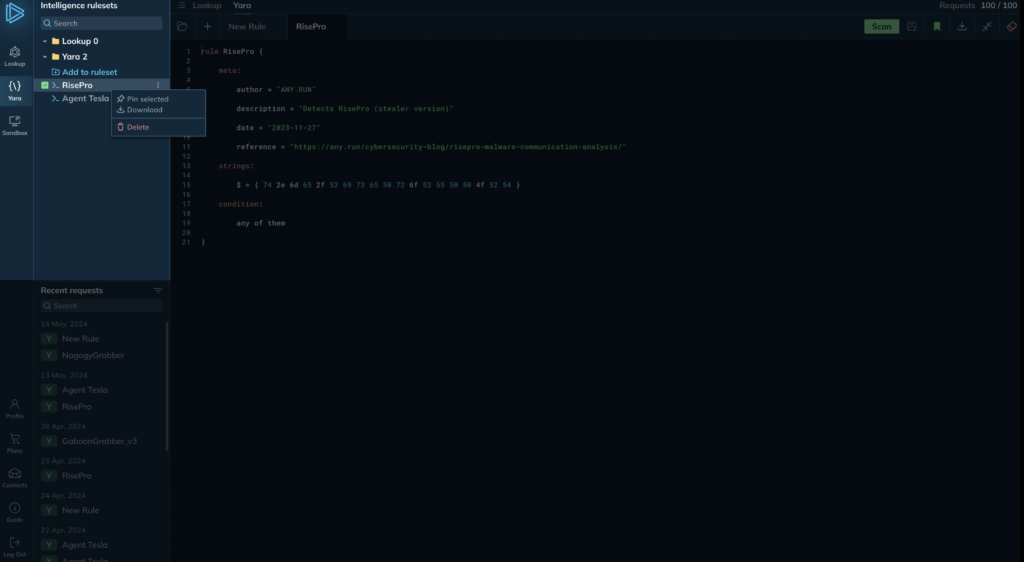
From this menu, you can:
- Optionally, select multiple rules to manage them in bulk operations.
- Download the selected rules to your local machine for offline editing or analysis.
- Pin frequently used rules to keep them at the top of the list for quick access.
- Remove any rules you no longer need by deleting them from your collection.
Recent request
In recent requests, you’ll see a list of your previous searches.
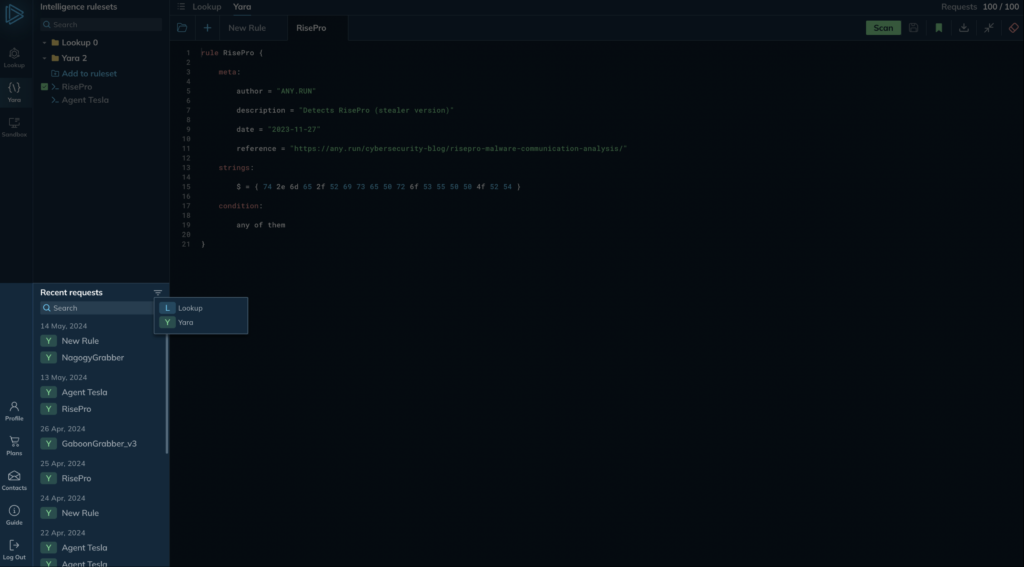
- You can easily re-run any of those searches by clicking on the specific query.
- The filter icon allows you to toggle between viewing your lookup search history or your YARA search history.
Note: if a search is in progress, you will see a spinning wheel icon next to it.
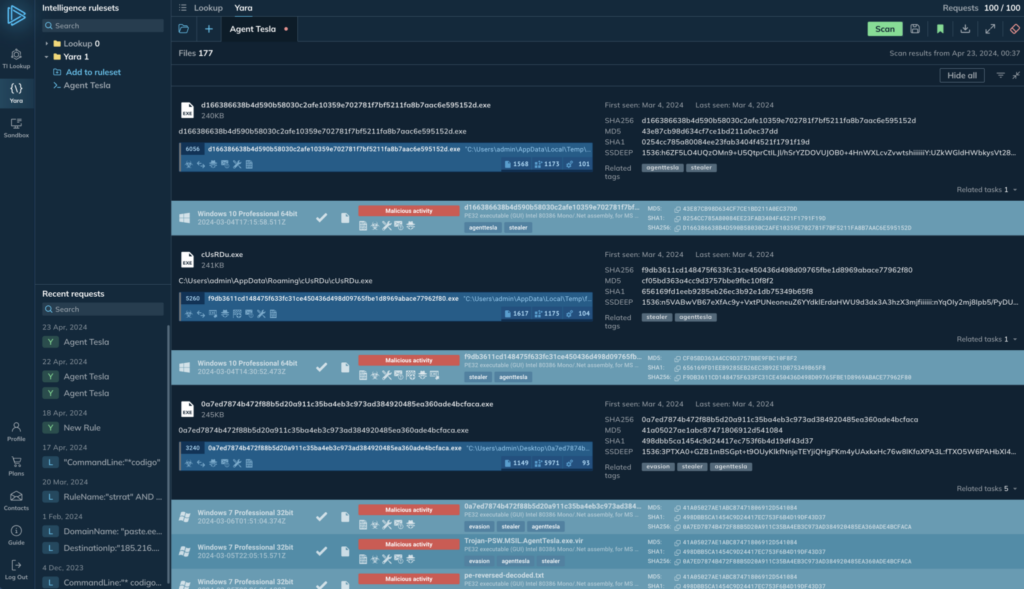
Query results
Now that we’ve covered the editor and rule management capabilities, let’s go over the different features you’ll see on the search results page after running a search.
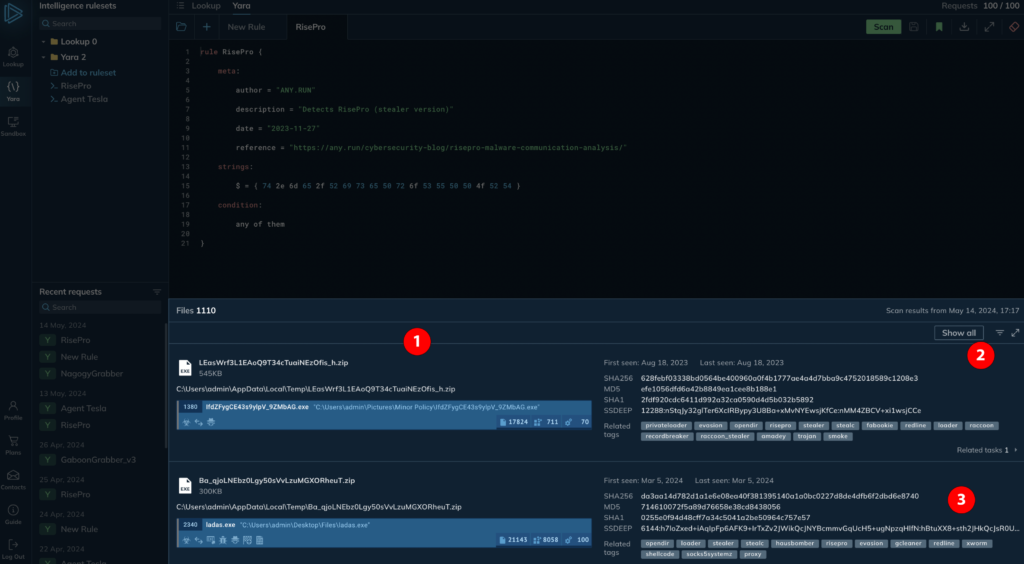
When you get your search results, you’ll see a progress indicator while the search is active, and then a list of matches. Here’s a breakdown of what’s included:
- On the left, you’ll find general information about each file, as well as details on the associated process.
- At the top-right, you have various controls. You can show or hide any associated sandbox sessions for each file match, filter the results by date, and minimize or maximize the view of results to optimize your screen space as needed.
- You can quickly view file metadata, IOCs, and threat names displayed as tags.
Hover over each file to reveal additional controls (seen below):
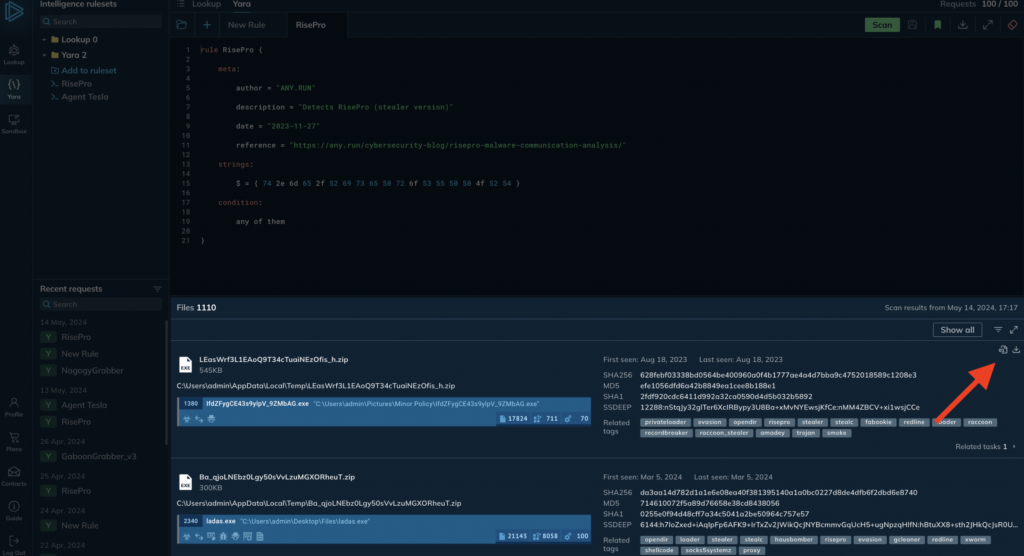
Moving from right to left, the rightmost button allows you to download a file for local analysis. As mentioned earlier, with ANY.RUN YARA Search, you have full access to all files you find, including the ability to download them.
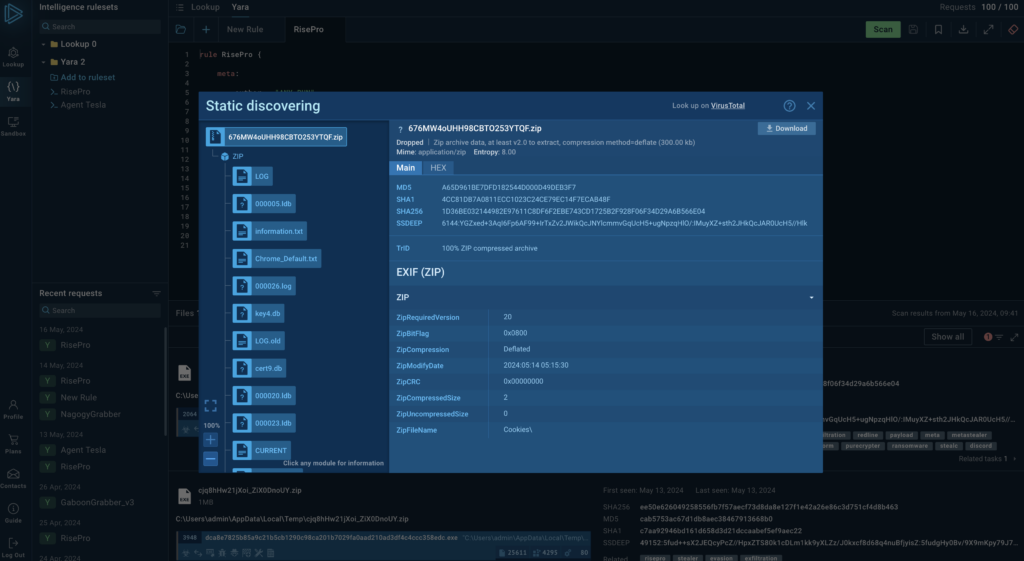
To the left of the download icon, there’s a file icon that opens the Static Analysis window. This module will be familiar to our sandbox users, as it’s the same interface used to view static file content like TrID and file HEX values.
With that, we’ve covered all the main functions of ANY.RUN YARA Search. We hope this overview has been helpful and that, even though the interface is already intuitive, it will allow you to get oriented with the UI even more quickly.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
We’ll show you in an interactive presentation how ANY.RUN can help your security team.







0 comments