Welcome to ANY.RUN‘s monthly updates, where we share what our team has been working on over the past month.
In April, we released YARA Search, a new threat intelligence service that allows you to find files, threats, and malware by YARA in 2TB of real-world threat data collected by the ANY.RUN sandbox community and our team.
We’ve also made several updates to the existing features: our RSPAMD module has been improved to reduce false positives even further, and we’ve increased the amount of data supplied based on the results of traffic checking using Suricata rules.
We’ve also enhanced the mechanism for adding tags to sandbox tasks, and, as always, we’ve expanded our threat coverage with new YARA and Suricata rules.
Let’s dive into these updates one by one.
New features
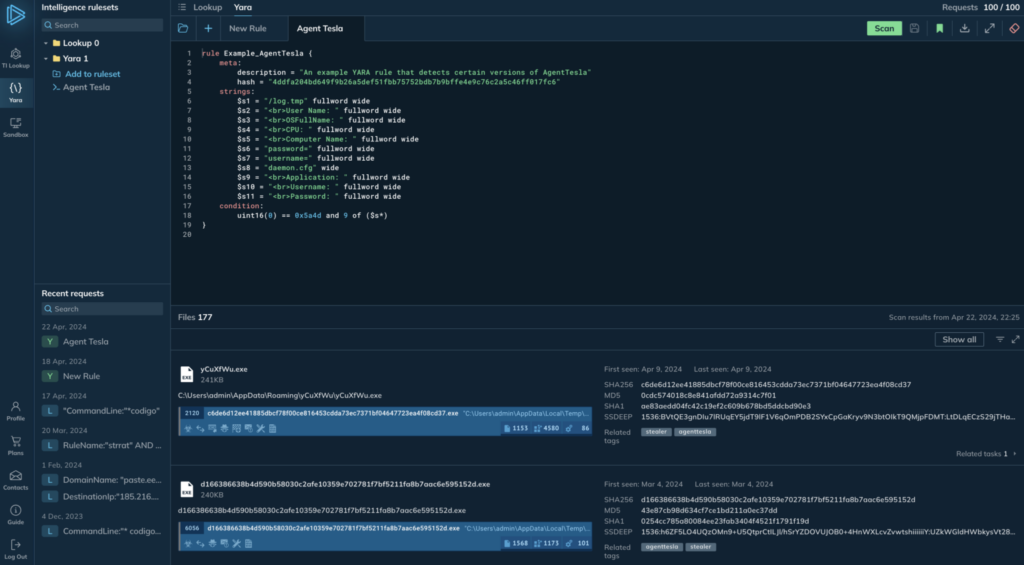
YARA Search
YARA Search allows you to find files, malware, and threats using YARA rules, which analyze the contents of files themselves. This is a massive update to ANY.RUN’s threat intelligence capabilities — it provides a new way to search for threat data in our growing database, supplied by over 400,000 sandbox users who analyze real malware on a daily basis.
The service also lets you write, edit, test, download, and manage your rules seamlessly within ANY.RUN using a powerful online text editor with syntax highlighting. And, like all our products, it’s incredibly fast, delivering initial search results in under 5 seconds.
Various improvements
This month, we didn’t just push out new features. We also focused heavily on improving existing ones.
- We’ve updated the RSPAMD module script, further reducing the occurrence of false positives.
- The data from checking traffic against Suricata rules is now richer in the network tab.
- We’ve refined the mechanism that assigns tags (such as “phishing” to an analysis session where phishing was detected) for improved precision.
New YARA rules and fixes
We’ve updated detection and config extraction of GuLoader. It now extracts not only C2 but also other strings. We’ve also updated the config extractor and the YARA rule covering Vidar. This stealer, based on Arkei, collects information about 2FA and Tor. Its configuration extracts Telegram API and Steam account or group used for data exfiltration, as well as decoded strings.
Other new rules added in April include:
- Blackwood
- PlanetStealer
- INC ransomware
- SideTwist
- Blister loader
- Carbanak
- ReverseSSH
- Donex ransomware
- RaspberryRobin
We’ve also made several fixes to existing rules.
- We’ve implemented a fix to LaplasClipper rule.
- Amadey detection and extractor was fixed.
New signatures
In total, we’ve added 16 signatures in April. Here are the standout ones:
New network rules
In April, we’ve released the following new network rules:
- Phishing which directs victims to Telegram.
- Phisihing with tracking.
- MadMxShell, a Windows backdoor distributed through Google Ads malwertising campaign, which we’ve written about here.
- Mirai Generic Botnet — which made a comeback — and Miori.
- A cross-platform, post-exploit, red teaming framework Mythic С2 with Apollo and Poseidon agents in HTTP setting — rules both for Windows and Linux
- A Suricata detection for DinodasRat on Linux has been added.
We’ve also added new rules that cover Botnet Kinsing, Adwind, StreamBot, and GCleaner Loader.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
Let us give you an interactive presentation of ANY.RUN and show you how it can help your security team.








0 comments