Visit any cybersecurity news website, and you’re likely to see a top article about a critical vulnerability being exploited in a major company or a ransomware attack on an enterprise.
High-profile cyberattacks were rampant in 2023. Notable examples include ransomware groups like AvosLocker, Black Basta, and BlackMatter targeting VMware ESXi servers and Linux systems. Or the incident In March, when a supply chain attack called “SmoothOperator” breached 3CX platform infrastructure, a popular voice and video-calling client developer, impacting over 600,000 organizations and millions of end-users.
Such attacks have widespread consequences and can be financially devastating for their victims. But, in reality, these aren’t the threats most likely to affect you.
Statistically, for every targeted APT against a large enterprise, there are millions of phishing, malspam, and social engineering attacks aimed at small and medium businesses.
Did you know, for example, that small businesses experience 350% more social engineering attacks than larger enterprises?
That’s why, while reading about hacks that make the news headlines is important, understanding the more common methods cyber attackers use to infect a system with malware is, perhaps, even more crucial. That’s the knowledge that will help in your day-to-day work and will keep you safe online.
There are many different methods — or attack vectors — that malware can use to infect your PC. Here are some of the most common ones:
1. Infected malware attachments in phishing emails
Attackers design emails to look like they’re from trusted sources such as banks, government agencies, or well-known corporations. The goal is to create urgency or fear, leading the recipient to download an infected attachment.
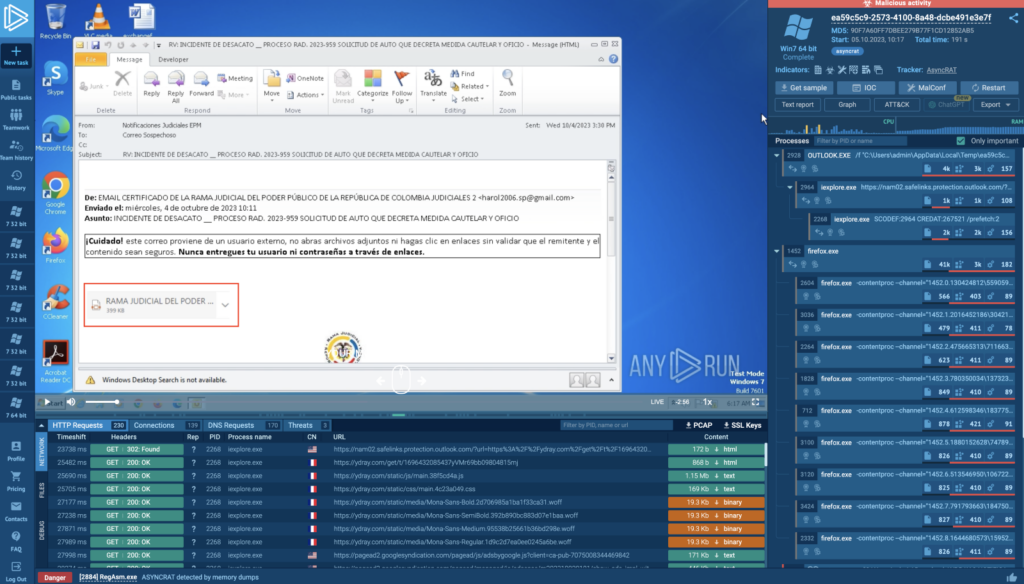
Examples include a bogus IRS notice about overdue taxes or a fake business communication attaching a payment invoice.
Read about the types of phishing attacks, and how to protect against them.
The attachments are often infected Microsoft Office or PDF files, which may contain malicious macros triggering malware download or execution. Sometimes, these attachments are executable files disguised as documents, installing malware when opened.
How to spot phishing emails
Phishing emails typically have poor grammar, mismatched sender addresses, and create a sense of urgency.
With tools like ChatGPT, however, grammar errors in phishing emails are less common. And attackers are now using more sophisticated methods like distributing password-protected attachments through file-sharing links in emails.
Read about advancing tactics of recent phishing campaigns.
2. Credential harvesting websites
Credential harvesting websites are a prevalent attack vector where attackers create fake websites mimicking legitimate ones. These sites are designed to steal sensitive information, such as usernames, passwords, and financial details.
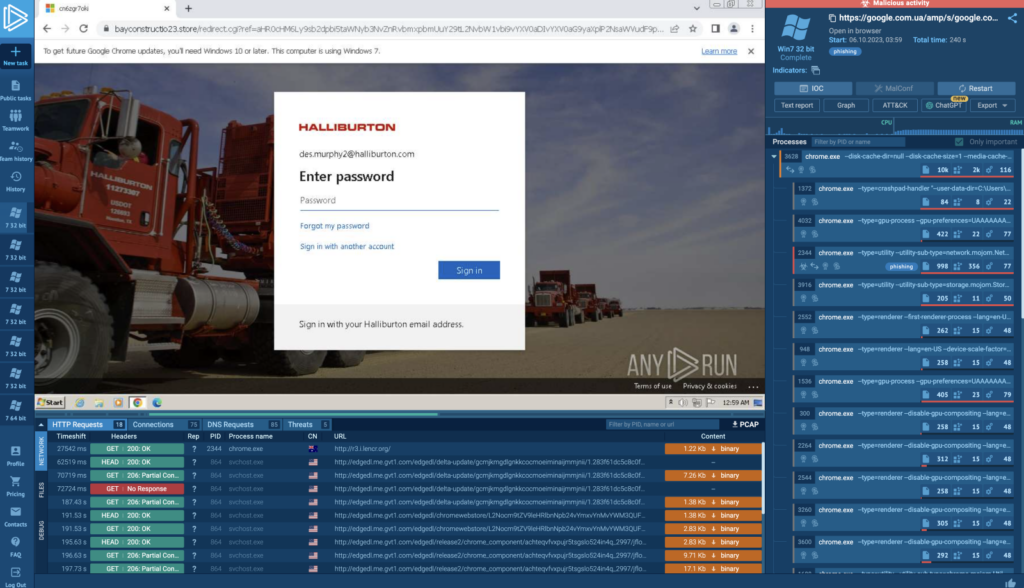
These fake pages often appear almost identical to their legitimate counterparts, making it challenging to spot the difference.
They are typically promoted through phishing emails or malicious online advertisements. For instance, an email pretending to be from a well-known bank might direct users to a fraudulent site where they are prompted to enter their banking credentials.
How to spot credential harvesting websites
- URL discrepancies: The website’s URL might have subtle differences from the legitimate site, such as misspellings or a different domain (e.g., .net instead of .com).
- Lack of security features: Legitimate websites often have security measures like HTTPS and SSL certificates. Fake sites might lack these, indicated by the absence of a padlock icon in the address bar.
- Unsolicited requests for information: Be wary of websites that ask for sensitive information without a clear, legitimate reason, especially if you reached the site through an email link.
3. Drive-by downloads
Drive-by downloads occur when a user unknowingly downloads malware by simply visiting a compromised website, without any interaction like clicking a malicious link. This technique exploits vulnerabilities in web browsers, operating systems, or software plugins — especially outdated ones.
Attackers embed malicious scripts into webpages, which are executed when the page is loaded in the user’s browser. Infection usually occurse thrwough one of the three methods:
- Exploit kits
- Malvertising
- Watering hole attacks
Exploit kits are automated tools that probe for vulnerabilities and deliver malware when a weakness is found.
Malvertising, the use of malicious ads in legitimate advertising networks, can redirect users to malicious sites or execute drive-by download scripts.
In watering hole attacks, attackers compromise sites frequented by a target group, infecting the users who visit these sites. Often, legitimate websites are hijacked to host and spread malware, loading additional malicious content from other domains. Once the malware reaches the device, it typically installs itself silently. The malware exploits security holes, like outdated software or unpatched systems, to gain access and privileges on the user’s device.
How to Spot Drive-By Download Attacks:
- Unusual browser behavior: Watch for unexpected changes in your browser, such as new toolbars, changed homepage settings, or unexplained slowdowns, which could indicate a drive-by download.
- Redirects to unknown websites: If your browser redirects you to a site you didn’t intend to visit, this could be a sign of a compromised webpage.
- Security software alerts: Pay attention to alerts from antivirus or anti-malware software, as they can often detect and block malicious scripts and downloads.
- Check for legitimacy: If you’re unsure about a website, verify its legitimacy by checking its URL, looking for HTTPS, and searching for reviews or reports about the site online.
4. Brute-forcing through Remote Desktop Protocol (RDP)
Brute-forcing RDP is a common attack vector where cybercriminals attempt to gain unauthorized access to systems via the Remote Desktop Protocol. This protocol, often used for remote system management and virtual desktops, becomes a target due to its direct connection to a system’s login interface.
Attackers use automated tools to systematically try a vast number of username and password combinations.
Unlike other attack vectors, brute-forcing can continue for extended periods, sometimes evading detection due to its low-profile nature. RDP services exposed to the internet, without features like multi-factor authentication or VPN protection, are prime targets for these attacks.
How to protect against RDP brute-forcing
- Use strong passwords and multi-factor Authentication: Implement complex passwords and change default credentials to prevent easy guessing. Use MFA to add an extra layer of security
- Limit RDP access: Restrict RDP access to internal networks or VPNs. This will instantly reduce exposure to external attacks.
- Regularly monitor and audit: Keep an eye on RDP logs for unusual login attempts or patterns indicative of a brute-force attack.
Wrapping up
This list doesn’t cover all the ways attackers can introduce malware into a system. Yet, these attack vectors remain highly prevalent. While analyzing or exploring targeted ransomware can be flashy and fun, it’s crucial to also have a comprehensive understanding of these fundamental attack types. This knowledge just might safeguard you or your organization in the future.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.









0 comments