Editor’s Note: This is an edited version of an article originally posted in October 2023. It has been updated with some new information about ANY.RUN’s threat intelligence products.
As a business owner, you’ve likely invested in a range of security tools like SIEMs, antivirus software, and IDS/IPS systems to safeguard your operations.
You might even have a dedicated cybersecurity team that monitors your systems and responds to incidents such as a SOC (Security Operations Center) or a DFIR (Digital Forensics and Incident Response) team.
But here’s the question: Are your teams equipped to go beyond simply reacting to cybersecurity incidents? If your company underutilizes threat intelligence, chances are they’re not.
Understanding the role of Cyber Threat Intelligence
Cyber threat intelligence involves collecting, analyzing, and interpreting data on potential or current cybersecurity threats. It plays an important role in helping organizations detect and prevent cyberattacks by offering insights into adversaries’ tactics, techniques, and procedures (TTPs).
CTI spans a wide range of activities, from identifying malware variants to monitoring trends in cybercrime, and it involves the use of specialized tools to protect against evolving threats.
Types of threat intelligence tools
| Category | Primary Use Cases | Primary Consumers |
|---|---|---|
| Threat Intelligence Feeds | Expand threat coverage of your security systems like SIEMs, firewalls, and IPS/IDS with the latest IOCs. |
1. SOC Team
2 Incident Response Team |
| Threat Intelligence Lookup | Provide linked, contextual data around indicators, allowing to query databases for known IOCs such as malicious IPs, URLs, or file hashes. |
1. SOC Team 2. Threat Analysts |
| Sandboxing Solutions | Analyze suspicious files or URLs in isolated environments to understand their behavior and impact. |
1. SOC Team
2. Threat Analysts |
| Aggregation Platforms | Enable to combine multiple threat feeds for analysis and correlation, enhancing decision-making during an incident. |
1. SOC Team 2. Threat Intelligence Analysts |
| Threat Sharing Platforms | Facilitate the sharing of structured threat information within a community or organization. |
1. Threat Intelligence Team 2. SOC Team |
Keep in mind that internal organizational structures differ among companies. Your team names and responsibilities may vary, but the table above should give you a solid understanding of who typically uses which threat intelligence tools and for what purpose.
Read more about cyber threat intelligence definition.
What happens in teams that don’t have threat intelligence
Without threat intelligence tools, your teams are essentially flying blind. Consider a situation where a suspicious artifact shows up in your system logs, like an unfamiliar IP address. How does the SOC team immediately identify what this IP means and how to address it effectively?
In short, without threat intelligence, they can’t.
Manual research will be needed instead, requiring the team to pull data from various open-source sources to understand the threat. This process takes time, and time is something you can’t afford to lose during an active attack.
One of the primary goals of threat intelligence is to provide context for artifacts and indicators. Linking an IOC to a specific threat and then to TTPs helps the team understand the exact steps needed to counter the threat.
ANY.RUN’s Threat Intelligence Lookup changes that by delivering real-time contextual data, allowing your teams to link IOCs to threats and threat actor tactics, techniques, and procedures (TTPs) quickly and effectively. Instead of sifting through disparate sources, teams can get actionable insights instantly.
Threat Intelligence Benefits for a Business
But the benefits don’t stop there. Here are 7 more reasons why threat intelligence is crucial for a strong security posture:
1. Reducing the risk of successful cyberattack
Reducing attack risk is a key advantage of threat intelligence. Your SOC team can use real-time threat feeds to get ahead of new threats and deepen their knowledge of TTPs and IOCs.
The data helps in proactively adjusting firewall rules, IDS/IPS signatures, and other security measures, making your defenses stronger. At the same time, the incident response team gains valuable context about attacks, speeding up containment and removal.
2. Preventing Financial Loss
According to IBM, the average cost of a data breach in 2023 is $4.45 million. Finding and containing a breach usually takes months, making prevention a top priority.
Threat intelligence helps your SOC team spot phishing campaigns, fraud attempts, and data exfiltration risks. This protects both financial assets and customer data. By doing this, you avoid expensive breaches, regulatory fines, and the erosion of customer trust that financial setbacks bring.
3. Improving security operations and detection accuracy
Alert fatigue happens when too many alerts overwhelm security specialists, causing them to miss genuine threats. This is often due to frequent false positives and lack of prioritization.
Threat intelligence allows SOC analysts to sort alerts by relevance and risk. They can zero in on high-fidelity alerts that truly matter, cutting down on the noise from low-level threats. This focus lets the team fine-tune IDS/IPS signatures and craft better correlation rules for SIEM systems. The result is a more efficient SOC, with fewer false positives and faster threat identification.
4. Managing vulnerability more accurately
Your vulnerability management team can use threat intelligence to smartly prioritize patches. Instead of wasting time on low-risk vulnerabilities, they can focus on those actively targeted or with known exploits.
Threat intelligence also guides the creation and updating of secure configuration baselines. This data-driven strategy ensures you’re actually shrinking your attack surface, not just ticking boxes.
5. Refining risk analysis
Your risk management team can enhance their risk assessments by incorporating threat intelligence. This gives them a real-time, nuanced view of threats, beyond just historical data or industry benchmarks. They can factor in current events like emerging APTs or zero-days to better gauge risk impact and attack likelihood.
This alignment with the current threat landscape improves decision-making for resource allocation, policy setting, and incident response planning.
6. Improving threat hunting capabilities
Threat intelligence provides crucial insights into the tactics, techniques, and procedures (TTPs) used by attackers, allowing threat hunters to be more proactive. By understanding
these methods, your security teams can actively seek out potential threats before they escalate into full-blown incidents. This proactive approach enables faster detection of anomalous behaviors, reducing the time an adversary can stay in your network undetected.
7. Learning from real-world examples
TI Lookup allows teams to learn more about threat behavior by instantly accessing real-world dynamic analysis. This gives your business access to up-to-date examples of how threats operate, helping security teams better understand malware behavior and strengthen their defenses accordingly.
How Threat Intelligence Lookup Enhances Your Company’s Defense
Threat Intelligence Lookup services, like ANY.RUN’s TI Lookup, provide a powerful way to connect the dots between seemingly unrelated indicators of compromise. This service will help your team gain a clearer understanding of cybersecurity threats, leading to faster and more informed responses.
Here’s why you need to implement Threat intelligence lookup tools into your company’s cybersecurity activities:
- Instant context: TI Lookup quickly links important indicators, like IP addresses and file hashes, to known cyber threats, enabling your security team to respond faster to emerging dangers. This saves valuable time and minimizes the risk of costly incidents.
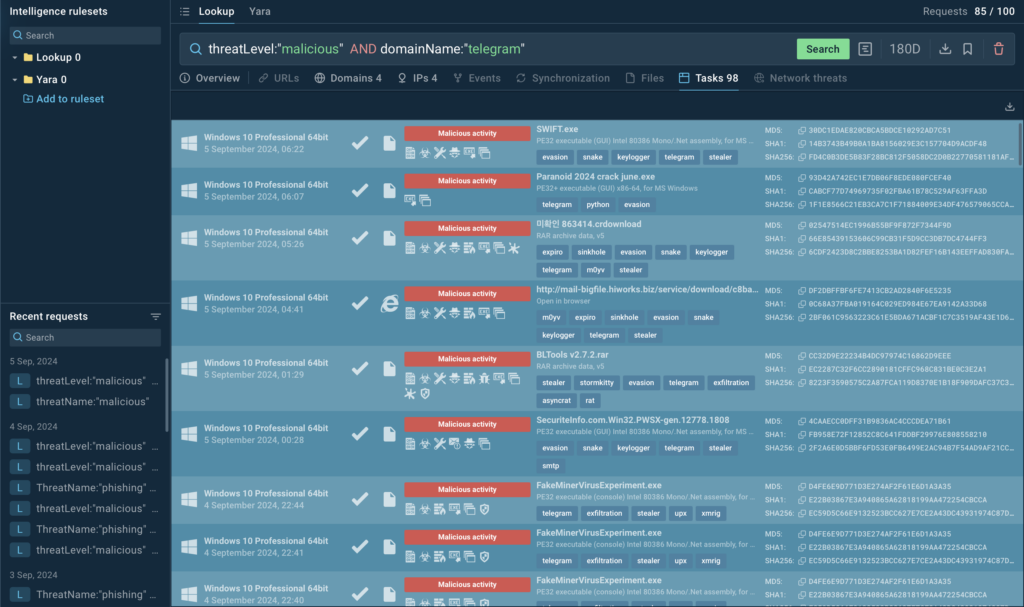
- Advanced OS artifacts: ANY.RUN’s TI Lookup goes beyond surface-level IOCs, providing detailed visibility into OS artifacts, including command lines, registry changes, and mutexes. These insights equip your business with the deeper information needed to investigate complex security threats effectively.
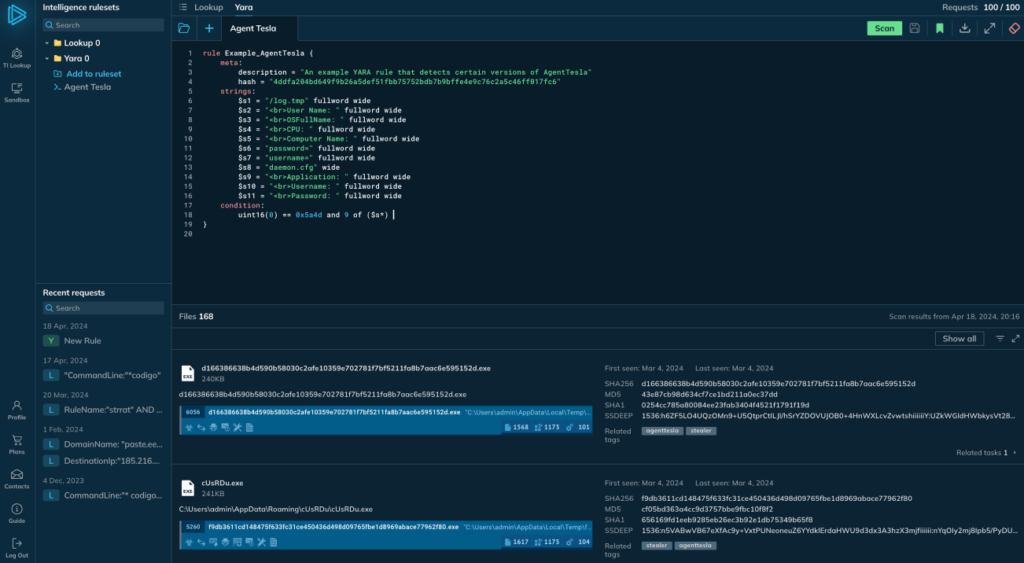
- Malware detection with YARA search: By applying YARA rules, TI Lookup can help your team detect malware variants based on file content, making it easier to identify similar malicious samples in your infrastructure.
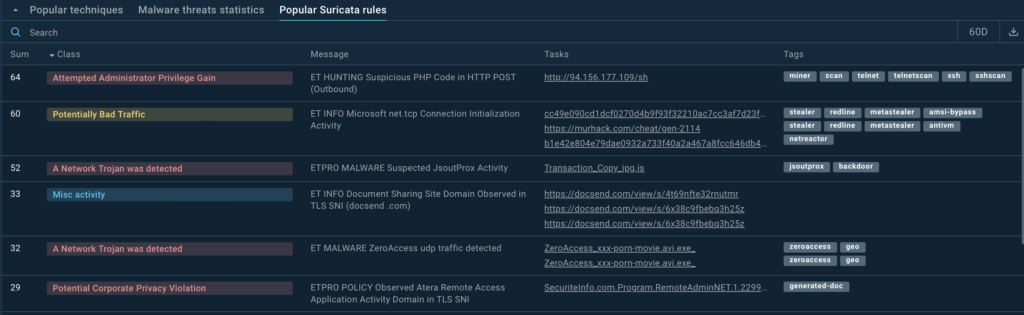
- Suricata network protection: TI Lookup integrates Suricata detection rules to track network-based threats, identifying malicious traffic patterns that could otherwise go unnoticed. This means, your business is shielded from cyberattacks using the latest network defense strategies.
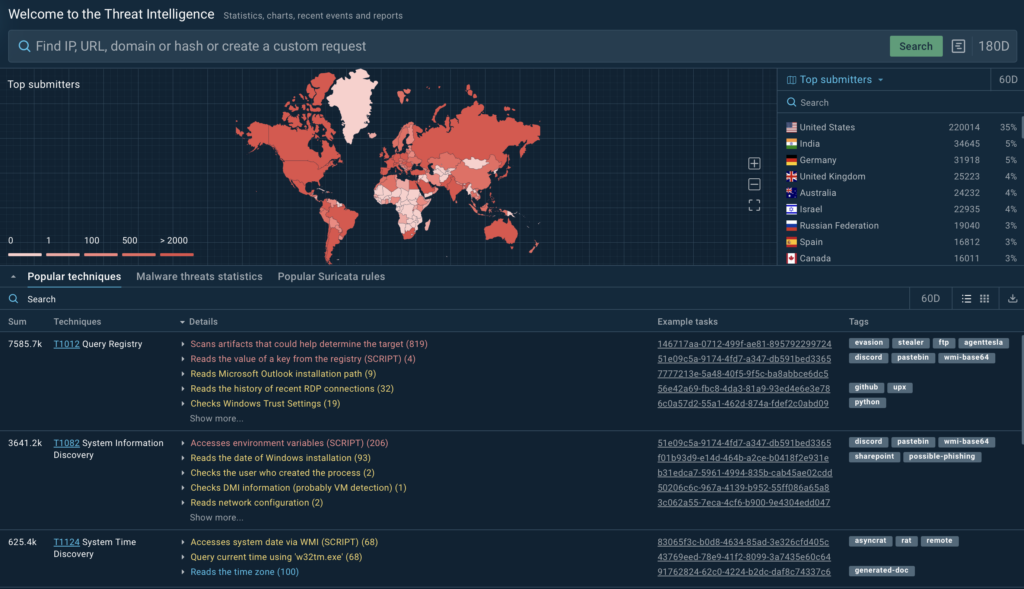
- Real-world threat intelligence: Data from live, interactive sessions in TI Lookup ensures that your security team deals with up-to-date, actionable intelligence. This leads to more informed decision-making and quicker mitigation of ongoing threats.
- C2 locations lookup: ANY.RUN’s geolocation feature allows users to track and visualize Command and Control (C2) server origins on a live map. By identifying malware families associated with these C2 servers and accessing relevant analysis sessions, your team can filter results based on geography or malware type, making it easier to understand and counter threats targeting your organization.
- Malware popularity tracking: ANY.RUN’s malware family tracking feature provides real-time insights into trending malware. You can monitor shifts in malware popularity, easily extract fresh IOCs, and analyze which regions are most affected by specific threats, helping adjust defenses accordingly.
Wrapping up
As you can see, threat intelligence offers multiple business benefits. To sum up, it:
- Lowers the chance of successful attacks
- Helps prevent or cut down financial losses
- Boosts the efficiency and accuracy of security operations
- Enables precise vulnerability management
- Enhances risk analysis
Interested in expanding your threat coverage?
Right now, you can integrate ANY.RUN’s Threat Feeds to receive the latest IOCs directly from ANY.RUN’s sandbox. They are pre-processed and filtered for false positives.
You can also utilize Threat Intelligence Lookup to speed up your investigations by contextualizing your alerts or artifacts with more information on the malware family and its TTPs, extra IOCs, samples, etc. from our large repository of threat data.
Contact sales to get a 14-day free trial and discover how you can strengthen your company’s cybersecurity today.
Stay tuned for more exciting updates!








0 comments