Pivoting in cyber threat intelligence refers to using one piece of data to find and explore related information and expand your understanding of a threat. It lets you discover hidden connections between indicators of compromise and find potential vulnerabilities before they are exploited.
Why pivoting matters
Cyber threat intelligence concentrates on indicators of compromise, IOCs. These are data points or artifacts (like IP addresses, domain names, file hashes, email addresses, etc.) that indicate a potential or actual malicious activity. Pivoting is researching links and correlations between IOCs and thus discovering new IOCs relevant to the same attack, malware, or threat agent.
Pivoting helps make CTI proactive, helps predict and prevent the unfolding of an attack or the emergence of new threats.
Threat intelligence and pivoting are critical for businesses and corporate security because they enhance an organization’s ability to anticipate, detect, and respond to cyber threats. By leveraging actionable insights from threat intelligence and pivoting to discover deeper connections, businesses can protect their assets, reduce risk, and strengthen overall cybersecurity posture.
Note that the definition of pivoting in threat intelligence is different to that in cyber security. Generally, it’s a popular term used in many other fields.
In CS the term is usually used by pentesters and hackers. Here pivoting is the act of an attacker moving from one compromised system to one or more other systems within the same or other organizations. Pivoting is fundamental to the success of advanced persistent threat (APT) attacks.
How it works
Pivoting for CTI shows its potential when IOCs are viewed not as “atomic” but rather as complex objects. Taken by themselves, they are, so to say, “backward-looking”, they lack context. IOCs are good forensic material, but not enough for predictive, proactive security effort.
Pivoting focuses on behaviors. Indicators are linked through their behavioral commonalities. This approach grasps IOC relationships, helps discover new ones, predict their behavior, generalize tendencies, and eventually build strong and adaptive defense based on the understanding of adversaries.
Pivoting routine
Pivoting is not just about techniques and tools; it is rather about a certain approach or dare say a certain mindset. Once adopted, it’ll give your threat intelligence a new depth and perspective.
The most basic algorithm is:
- Select an initial indicator. For example, a suspicious IP. Or a domain name associated with a known threat or attack.
- Analyze the indicator with a tool of your choice.
- Decompose the indicator. Understand its parameters. Define which of them could signal malicious behavior or be linked to other artifacts.
- Find and analyze linked artifacts. Pay attention to those that haven’t been yet connected with a threat or an attack.
- Research the discovered data.
- Draw actionable insights.
Where to start
You can start with network indicators pivoting. Basic network IOCs are IPs, domains, SSL/TSL certificates. They all have certain parameters: for example, registrar and registrant for domains, hosting provider or server type for an IP address, issue date or issuer for a certificate.
One of the most powerful tools for IOC research is ANY.RUN’s Threat Intelligence Lookup. It lets you search threat artifacts with over 40 search parameters, including YARA and Suricata rules, combine them and get real-time updates on search results.
TI lookup is integrated with the Interactive Sandbox used for researching malware in action within a safe virtual environment.
For example, let us try using ASN to identify network infrastructure.
1. Find IPs assigned to the “Autonomous System of Iranian Research Organization for Science and Technology” using TI Lookup. The search query is:
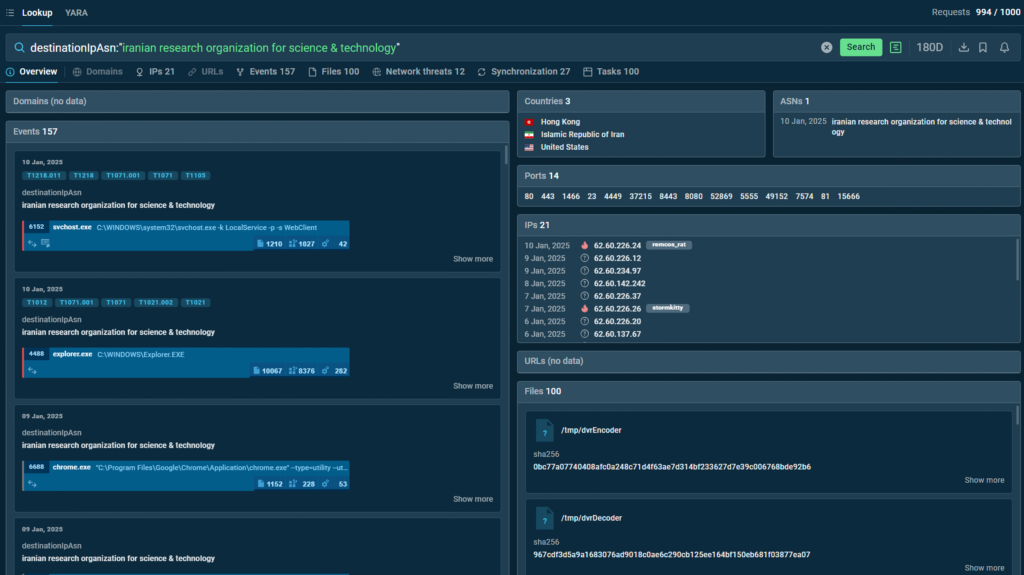
2. Look at the list of IP addresses in the search results. Some of them have tags assigned to them. The tag “Stormkitty” refers to the eponymous stealer — StormKitty.
Hover over the tagged IP and click the magnifying glass that appears next to it. This will include the IP address in the search request.
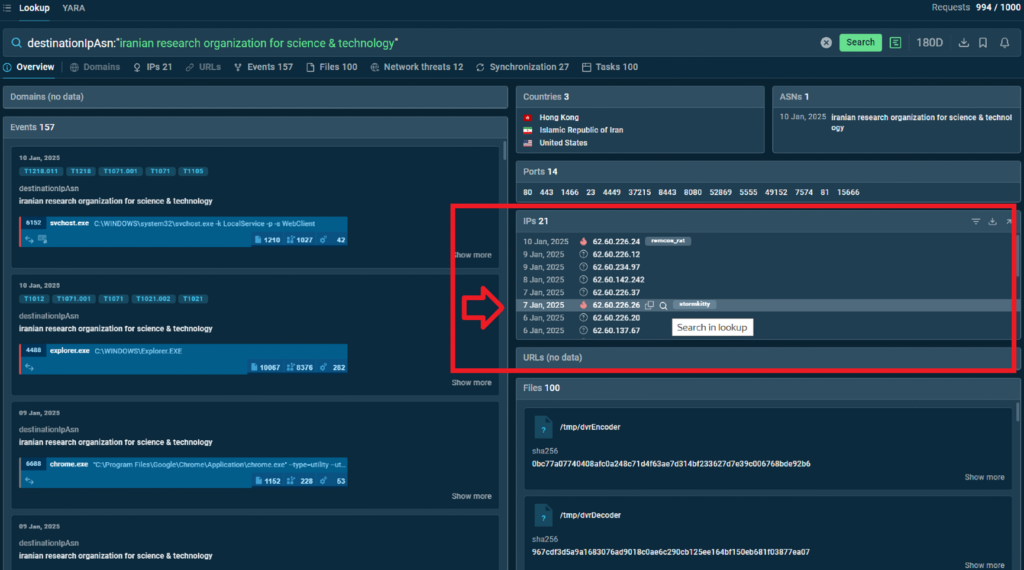
The request now is:
3. In the search results we see a number of events linked to the IP address and associated with the activity of AsyncRAT, a well-known multifunctional malware.
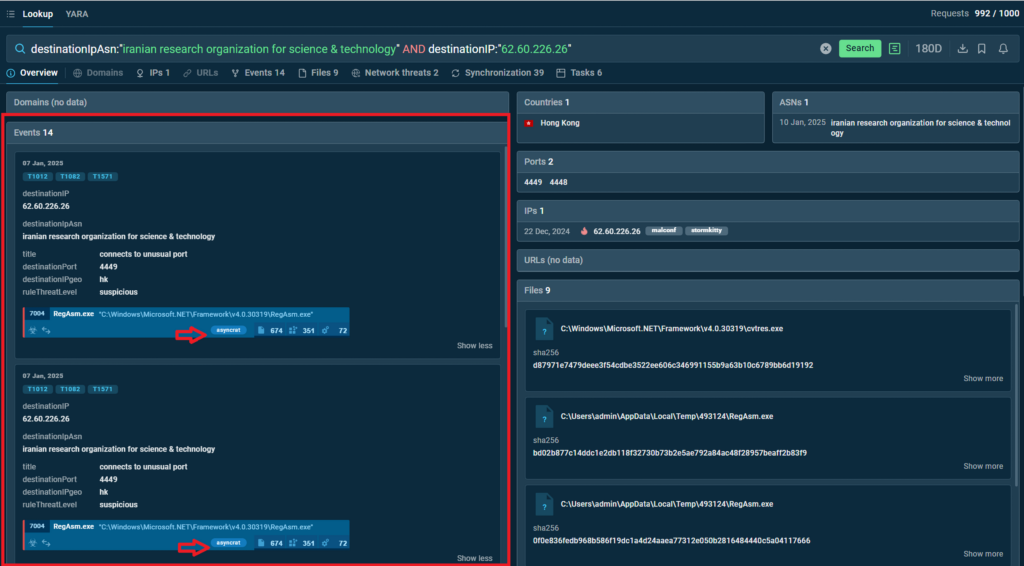
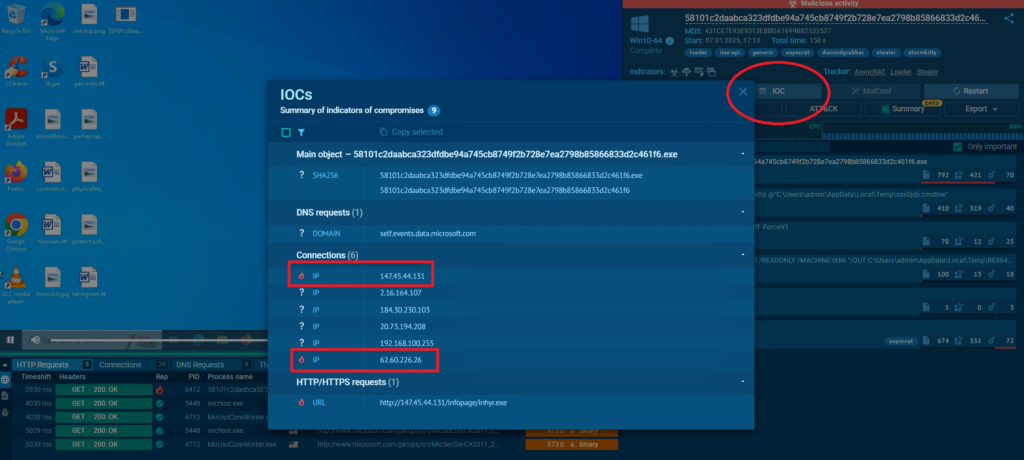
4. By clicking the Tasks tab (under the search query) open a list of Interactive Sandbox sessions that featured the IP address and AsyncRAT malware.
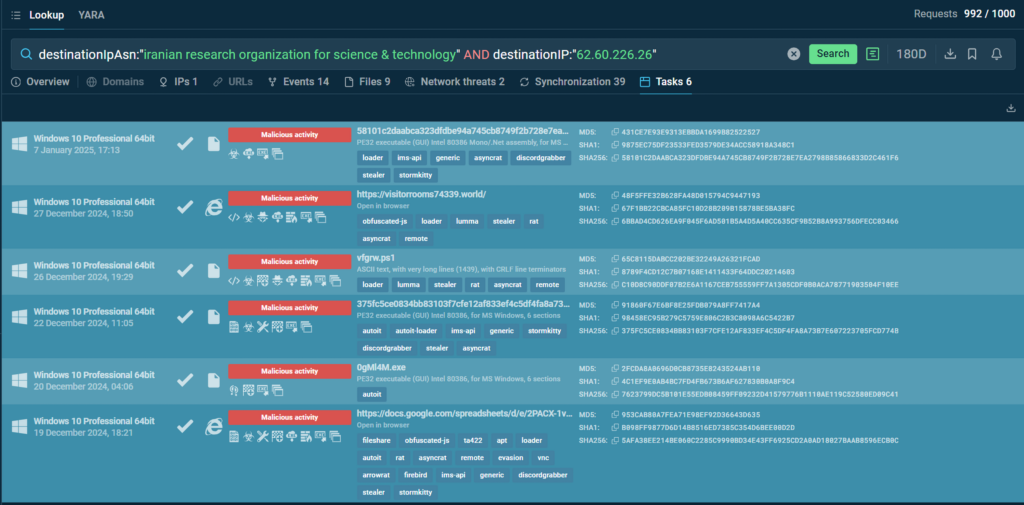
5. Select one of the sessions. Click the IOC button to the right of the virtual machine’s screen. A collection of indicators involved in the attack contains more IP addresses marked as malicious. Any of them can be copied and subjected to research via TI Lookup.
Boosting cybersecurity with TI pivoting
Let’s look at another example and see how pivoting results in action for strengthening your network protection.
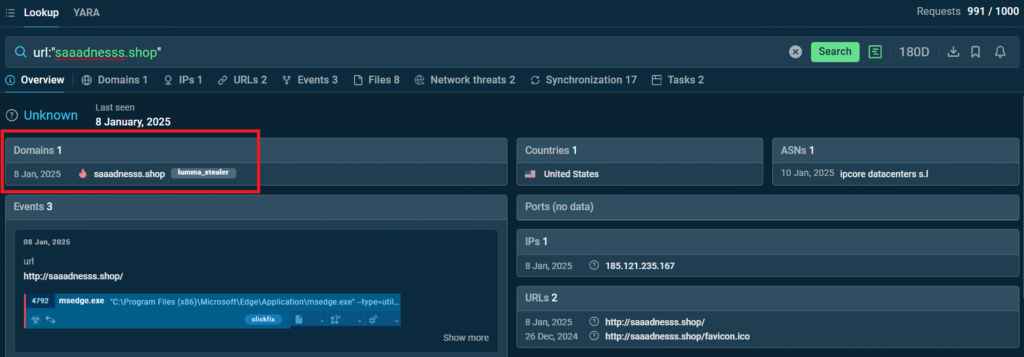
1. Use a suspicious URL address saaadnesss[.]shop as a search request in TI Lookup. Instantly find out that the domain is associated with the notorious Lumma stealer.
2. Check whether the “.shop” zone domain names tend to be linked to Lumma. The search query is:
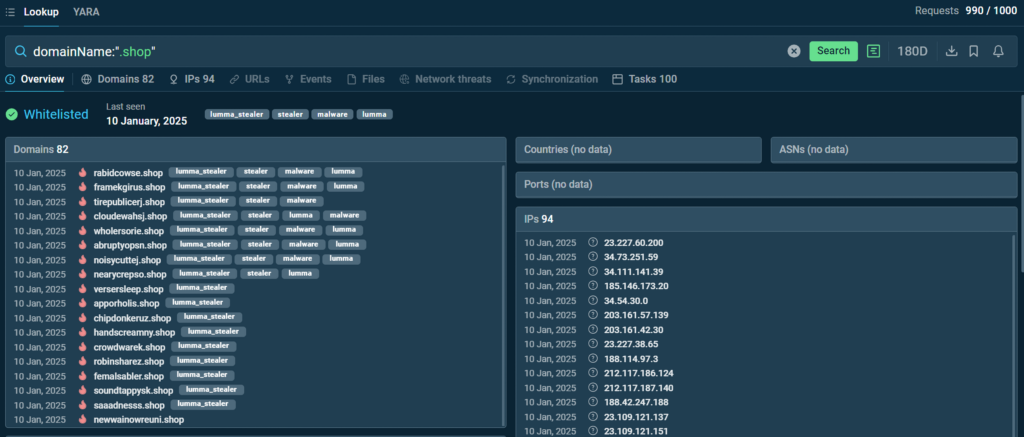
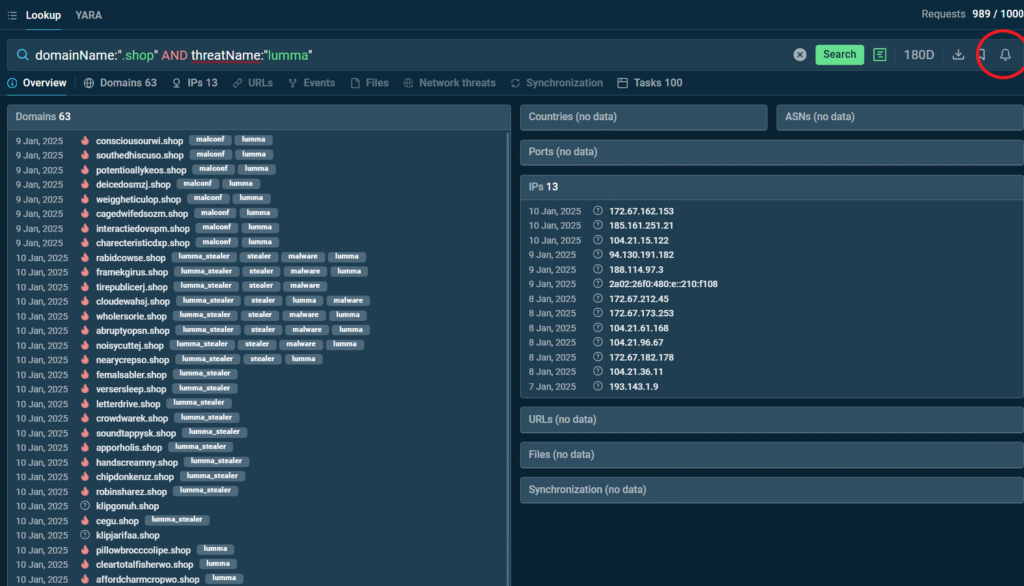
We see that Lumma massively employs .shop domains. We can update our security system to recognize them as a potential threat and give an alert in case they emerge.
To get the list of malicious .shop domains filled automatically based on real-time search results, subscribe to the results of the search request by clicking a bell in the top-right corner:

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
How TI Lookup can help businesses
TI Lookup offers a lot of benefits that align with businesses’ priorities, helping them strengthen overall security:
- Enhances Risk Management: TI Lookup helps businesses identify and manage risks more effectively, enabling leaders to prioritize security investments and mitigate potential threats.
- Improves Security Team Operations: By offering a user-friendly interface for collecting and analyzing threat intelligence, TI Lookup simplifies the process for security teams. This allows them to gather and act on critical information more efficiently.
- Optimizes Resource Allocation: By reducing false alarms and speeding up threat investigations, TI Lookup allows security teams to focus on genuine threats.
- Supports Compliance: With detailed threat intelligence, TI Lookup aids businesses in meeting industry regulations and compliance standards.
Conclusion
Pivoting is particularly valuable for corporate security teams because it helps uncover the “big picture” behind isolated security events. It reveals attackers’ infrastructure, such as related IP addresses, malware families, or phishing campaigns. It also speeds up threat investigation, enhances threat actor profiling and enables holistic defense, preventing organizations from addressing only part of the problem while leaving other vulnerabilities exposed.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.







0 comments