Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Socelars is an information-stealing Trojan (often categorized as spyware/stealer) that focuses on collecting sensitive data from Windows systems, with standout reporting around Facebook Ads Manager and session cookie theft. Unlike “noisy” malware that immediately breaks something, Socelars quietly converts a single infected machine into access: logged-in sessions, business account data, and pathways to monetization.
|
Stealer
Type
:
|
Unknown
Origin
:
|
|
1 December, 2019
First seen
:
|
19 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 December, 2019
First seen
:
|
19 February, 2026
Last seen
:
|

 38
38
 0
0

 289
289
 0
0

 1778
1778
 0
0
Built for ad account takeover: Socelars is explicitly associated with stealing data tied to Facebook Ads Manager operations, putting marketing budgets, brand pages, and business accounts at risk.
Cookie theft enables fast account abuse: Reported behavior includes stealing session cookies (Facebook and Amazon mentioned in public reporting), which can allow attackers to access accounts immediately without waiting for password resets.
Social-engineering friendly delivery: Campaigns have used a fake PDF reader lure to get users to install the malware, taking advantage of routine workplace behavior around “helper” tools.
Spyware/stealer family: Security vendors classify Socelars as a spyware/credential-stealing threat, built for quiet data theft rather than loud disruption.
ANY.RUN’s Threat Intelligence Lookup helps SOCs quickly understand Socelars activity at scale and uncover relationships between related samples and infrastructure.
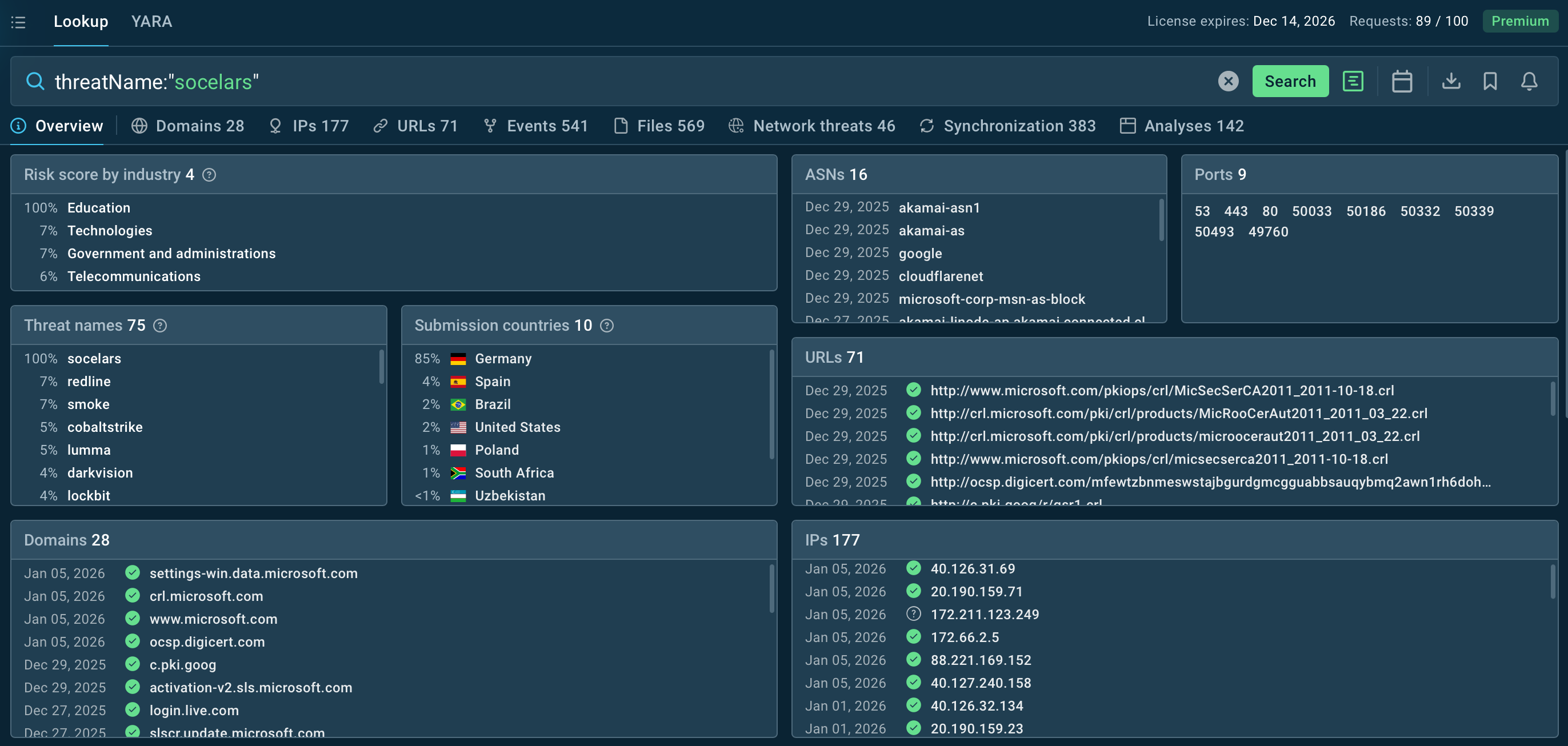
Socelars overview in TI Lookup: targeted industries and countries, IOCs, samples
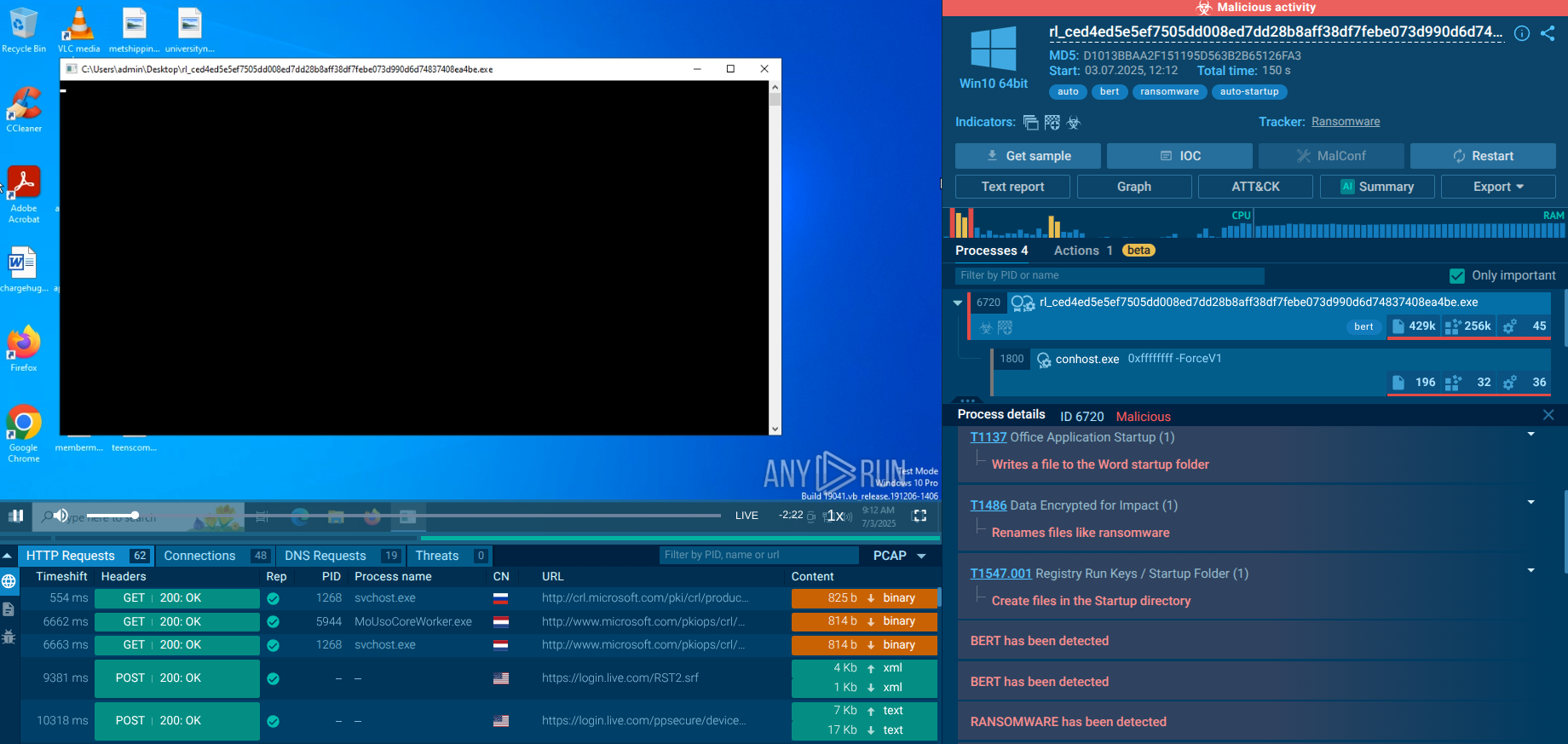
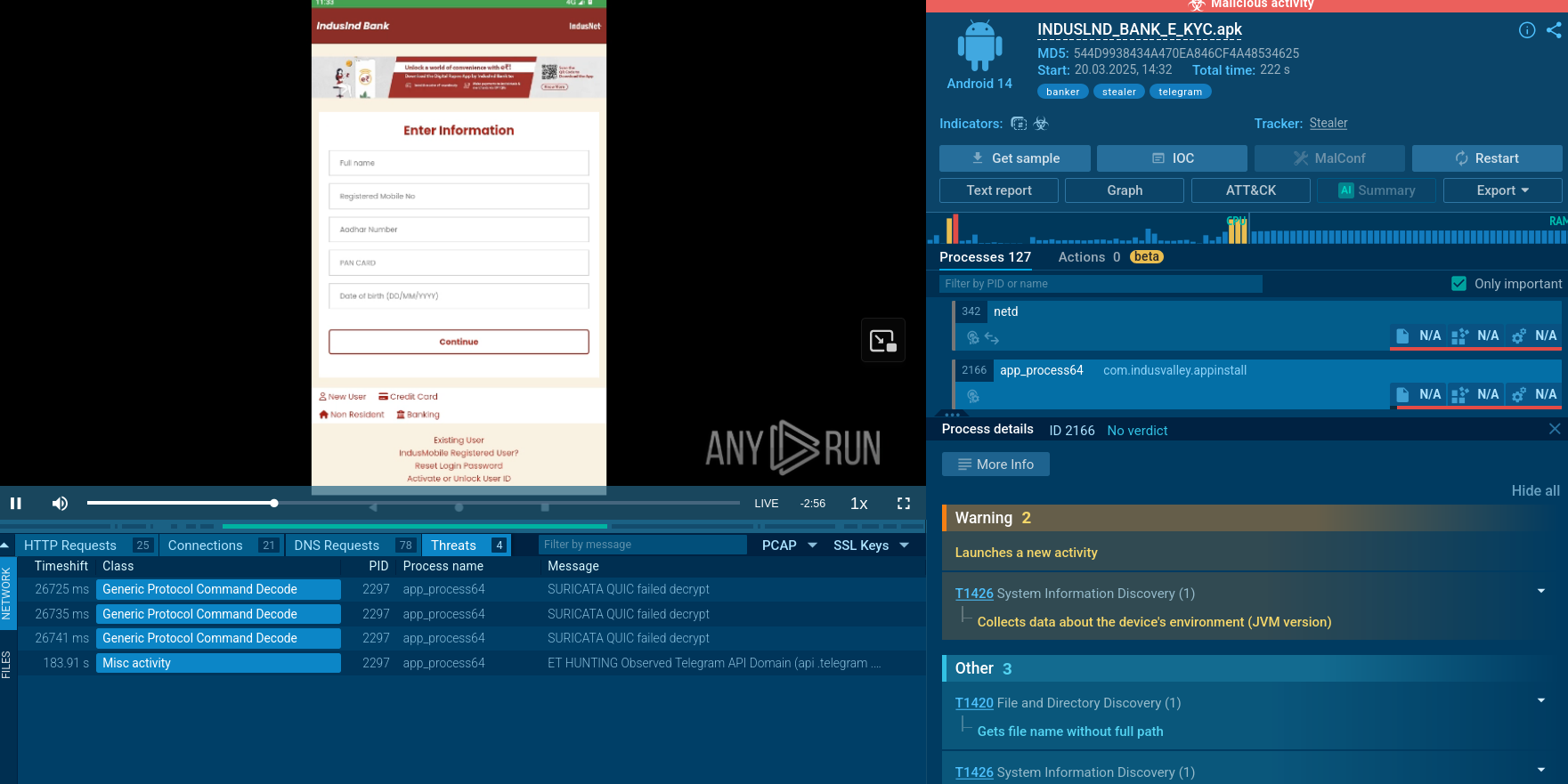
 Socelars stealer detected by ANY.RUN sandbox
Socelars stealer detected by ANY.RUN sandbox
Socelars is an information-stealing malware family designed to harvest authenticated session data, system identifiers, and other artifacts that enable rapid account takeover and financial abuse.
Rather than disrupting systems immediately, it focuses on quietly collecting the access attackers need to operate inside trusted business services and logged-in environments.
Public reporting links Socelars activity to the theft of session cookies associated with platforms such as Facebook and Amazon, which can allow attackers to access accounts without waiting for password resets or triggering obvious security alerts.
This makes the threat especially dangerous for organizations that rely on advertising platforms, e-commerce accounts, or cloud-based business tools, where stolen sessions can be monetized quickly.
From a technical perspective, Socelars combines:
As the malware’s primary goal is immediate operational access rather than destruction, traditional defenses that focus on ransomware-style behavior may detect the incident too late.
In practice, Socelars turns a single unnoticed infection into a pathway for account compromise, financial loss, and compliance exposure, making early behavioral detection and threat-intelligence visibility critical for effective defense.
Socelars is dangerous not because it disrupts systems immediately, but because it quietly targets the accounts and sessions that drive revenue and operations.
Instead of triggering visible alarms, the malware focuses on stealing authenticated browser data and business platform access, allowing attackers to act as legitimate users while remaining unnoticed.
Key business risks include:
Direct financial loss through ad account abuse: Access to Facebook Ads Manager sessions enables attackers to launch fraudulent campaigns, drain advertising budgets, or resell compromised accounts on underground markets.
Account takeover without traditional credential theft: By extracting active session cookies, attackers may bypass password resets and, in some cases, multi-factor authentication flows, gaining immediate control over business services.
Reputational and customer-trust damage: Compromised advertising or brand pages can be used to distribute scams, malicious links, or misleading promotions that impact customer confidence and brand integrity.
Compliance and data-protection exposure: Unauthorized access to business platforms and stored user data may trigger regulatory obligations, breach notifications, and potential financial penalties.
Hidden dwell time before discovery: Because Socelars operates quietly in the background, attackers may maintain access long enough to monetize accounts or expand compromise before defenders notice suspicious activity.
This means a single infected workstation can escalate into a multi-department business incident affecting marketing, finance, legal, and security teams simultaneously.
Socelars targets business accounts and browser sessions, not infrastructure, so risk is the highest where authenticated access maps directly to money.
Most exposed sectors include:
Marketing and advertising-driven companies: Heavy use of Facebook Ads Manager creates direct budget and account-takeover risk.
Agencies managing client ad accounts: One infected workstation can impact multiple customers at once.
E-commerce and consumer brands: Ad abuse can quickly translate into lost spend, fraud, and customer trust damage.
SMEs: More likely to fall for fake utility lures (such as PDF tools) due to lighter controls and training.
In practice, exposure depends less on industry and more on how much the organization relies on long-lived browser sessions for business-critical platforms.
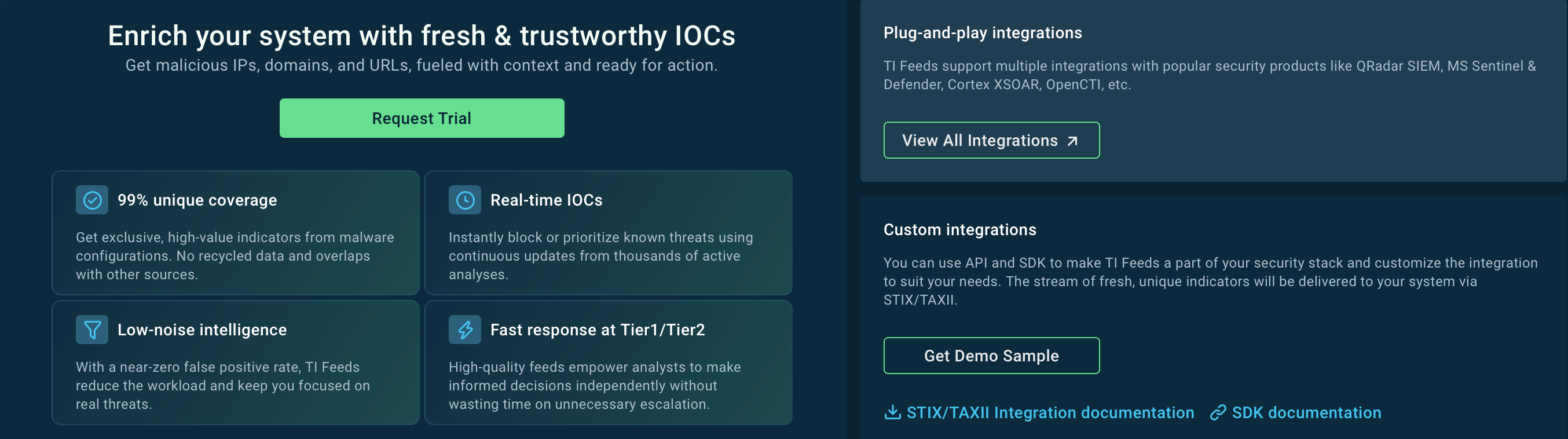
ANY.RUN’s Threat Intelligence Feeds deliver real-time, actionable indicators derived from sandbox detonations and global community submissions.
For Socelars, these feeds surface emerging distribution artifacts, related samples, and infrastructure linked to session-stealing activity, enabling automated detection and blocking across firewalls, EDR, and SIEM platforms.
This allows organizations to identify compromise before stolen sessions are abused, shorten attacker dwell time, and prevent follow-on fraud or account takeover, which is critical for threats designed to monetize access quickly rather than disrupt systems immediately.
Reduced Mean Time to Detect (MTTD): Fresh indicators help teams identify Socelars activity within minutes, limiting the window for silent session theft.
Prevention of Account Abuse and Financial Loss: Blocking known artifacts and related infrastructure reduces the chance of fraudulent ad spending, unauthorized campaigns, and account resale.
Protection of Brand Trust and Compliance Posture: Early detection lowers the risk of customer-facing scams, data exposure, and regulatory consequences tied to compromised business accounts.
Stronger Security ROI Through Shared Intelligence: Leveraging threat intelligence contributed by 15,000+ organizations improves detection coverage without requiring proportional investment in new tooling or staffing.
 TI Feeds: data & capabilities
TI Feeds: data & capabilities
Socelars is primarily distributed through social-engineering techniques designed to appear routine and trustworthy rather than overtly malicious.
Public reporting links campaigns to fake software utilities, including installers presented as legitimate PDF readers or similar everyday tools, which encourages users to execute the malware without suspicion.
These delivery methods rely on common workplace behavior: downloading quick-fix utilities, opening attachments tied to business activity, or installing software outside approved channels.
Because the initial file often looks harmless, traditional security controls may not flag the threat before execution.
After execution on a victim system, Socelars focuses on local data collection and session extraction rather than noisy self-spreading behavior.
Typical post-infection activity includes:
Accessing browser storage and session cookies tied to business services;
Collecting authentication data that enables immediate account takeover or fraud;
Preparing stolen information for exfiltration and attacker monetization.
This approach allows attackers to move directly from a single user action to business-level impact, without requiring lateral movement or complex network propagation.
In practice, Socelars spreads less through automated worm-like behavior and more through repeatable social-engineering campaigns, making user interaction and early detection the critical defensive boundary.
Socelars is designed to quietly extract high-value authentication data from an infected Windows system rather than cause immediate disruption. Its goal is to obtain information that allows attackers to access business-critical online services, especially advertising platforms and other authenticated web applications, without triggering obvious alerts.
After a victim runs the disguised installer or utility, Socelars begins operating in the background with minimal visible activity.
At this stage, the malware prepares the environment for data collection, ensuring it can access local browser storage, session artifacts, and user profile data without interrupting normal system use.
The core capability of Socelars is harvesting information that provides ready-to-use access rather than just raw credentials.
This includes:
Active browser session cookies that may allow attackers to bypass login prompts
Stored authentication data tied to business platforms such as advertising or e-commerce services
Additional local information useful for account takeover or monetization
As session data can remain valid even after passwords change, this stage enables immediate unauthorized access and rapid financial abuse.
Once sensitive data is collected, Socelars prepares it for exfiltration to attacker-controlled infrastructure.
The stolen access can then be used to:
Launch fraudulent advertising campaigns or drain marketing budgets
Resell compromised business accounts on underground markets
Expand compromise into related services or customer-facing assets
Unlike ransomware, which reveals itself through visible disruption, Socelars completes its objective silently, allowing attackers to profit before defenders detect the intrusion.
To understand how Socelars behaves in a real environment, analysts can detonate a suspected sample inside ANY.RUN’s Interactive Sandbox, where execution unfolds safely and every action is recorded in real time.
View analysis session with Socelars
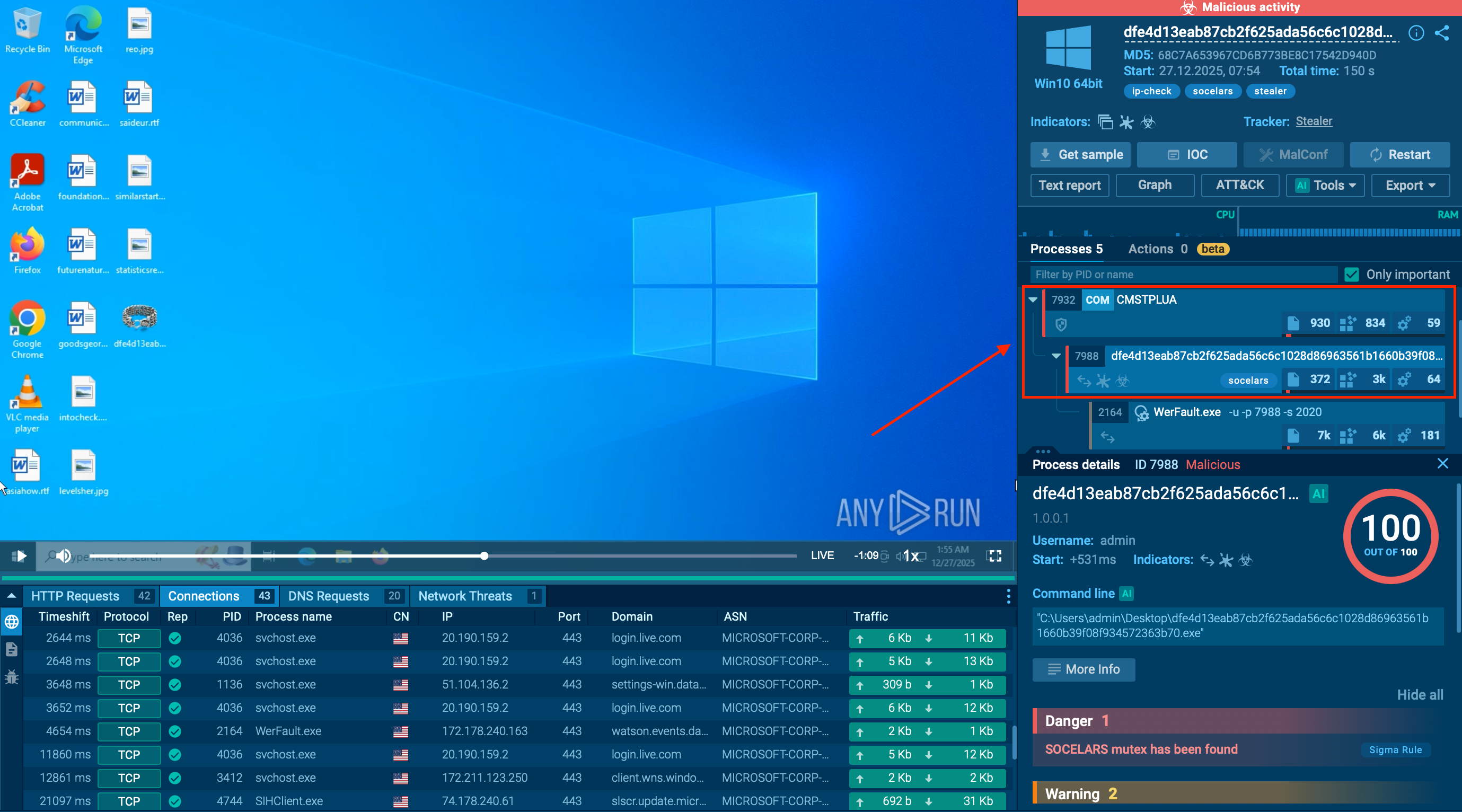 Socelars stealer detected by ANY.RUN sandbox
Socelars stealer detected by ANY.RUN sandbox
Immediately after execution, the malware begins system reconnaissance on the infected host. It collects the computer name, extracts the Machine GUID from the registry, checks installed system languages, reads Internet Settings parameters, and inspects system certificate configuration.
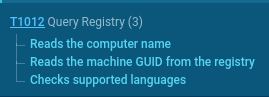 System reconnaissance by Socelars stealer
System reconnaissance by Socelars stealer
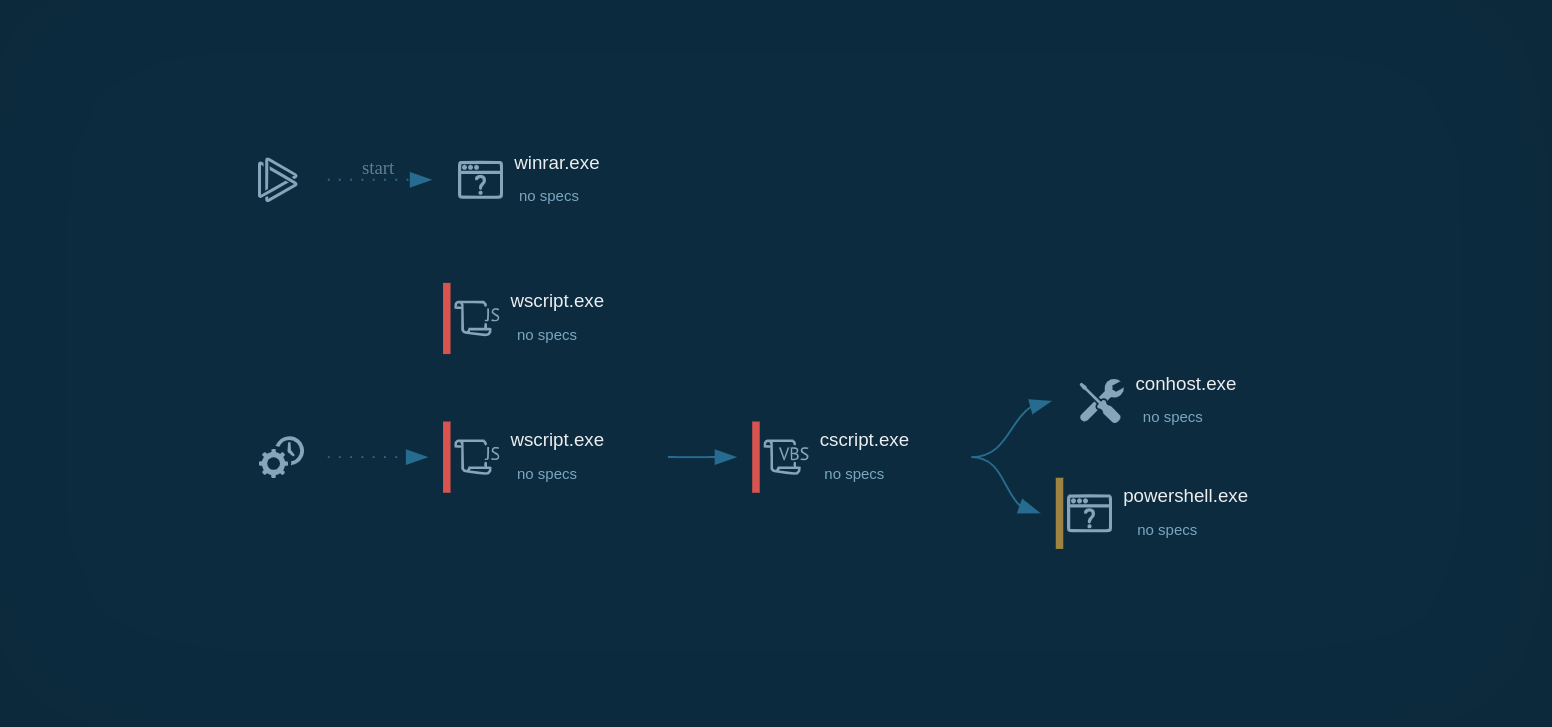
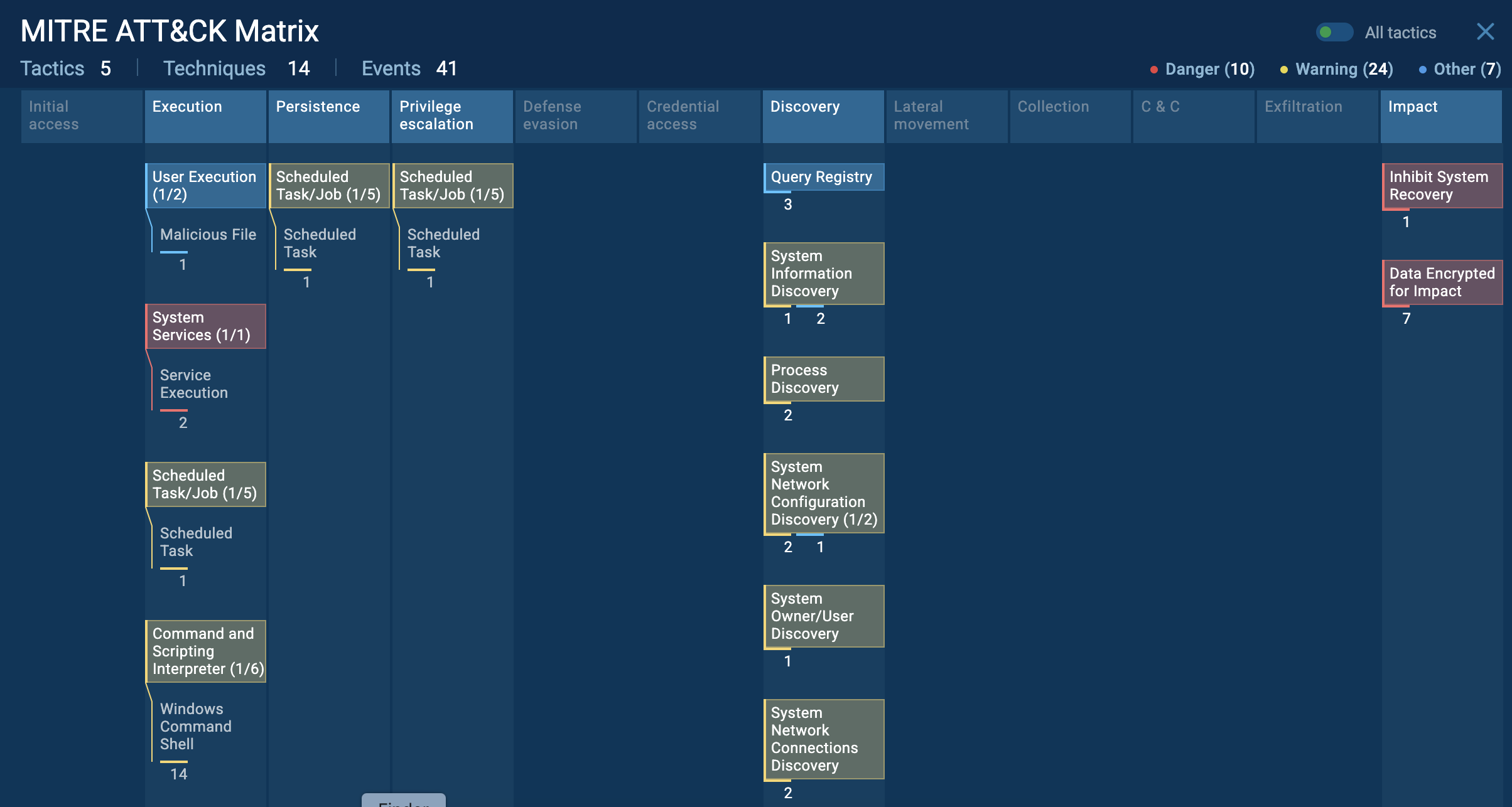
The next stage involves a User Account Control (UAC) bypass. Socelars launches dllhost.exe with the parameter /Processid:{CLSID}, where the CLSID corresponds to the ICMLuaUtil interface from cmlua.dll, a component that allows auto-elevated privilege execution.
Through this COM object, the malware invokes the **ShellExec method to run its payload with elevated rights.
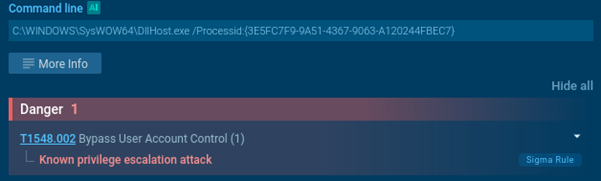 Socelars bypassing user account control, detected in ANY.RUN sandbox
Socelars bypassing user account control, detected in ANY.RUN sandbox
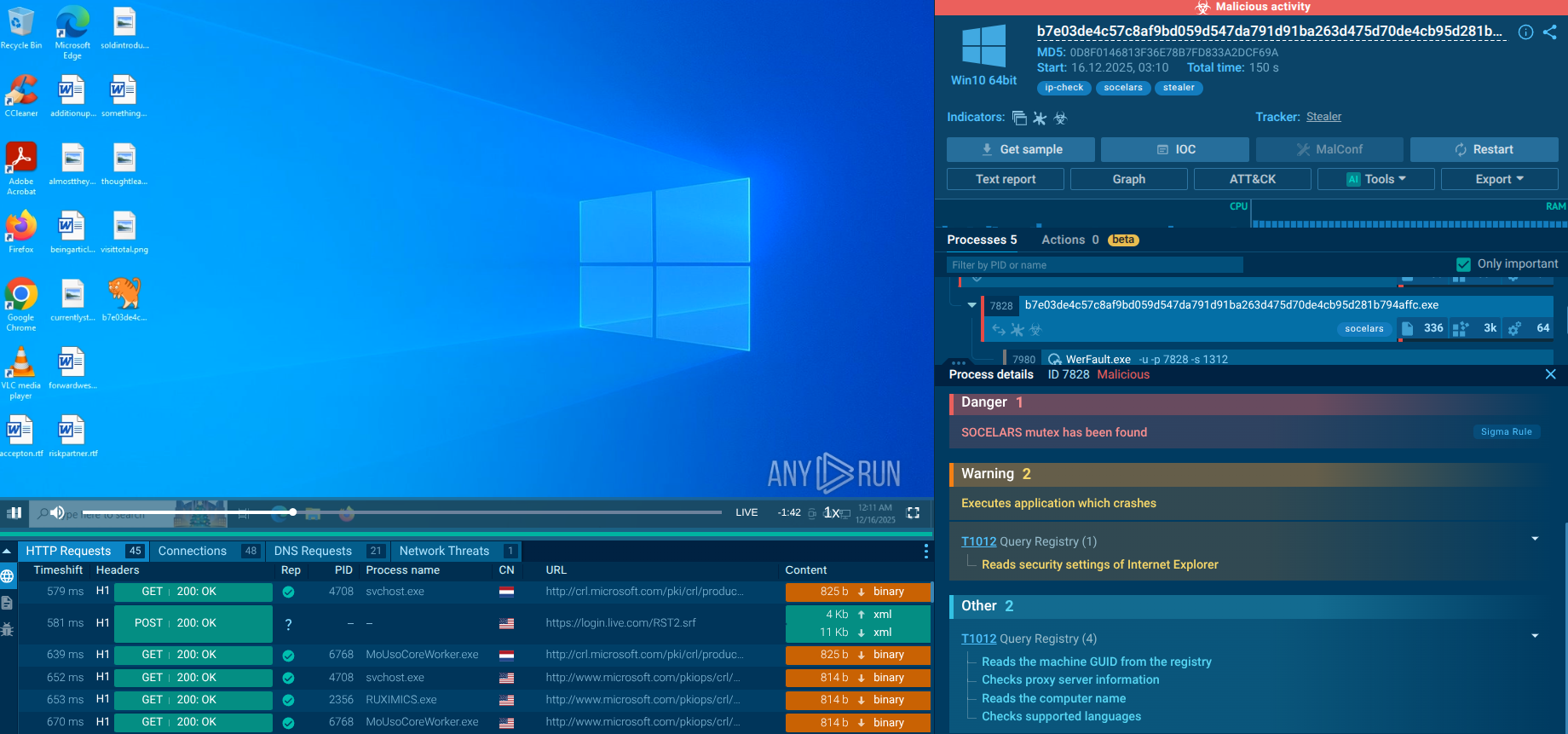
After successful privilege escalation, the sample creates a mutex named “patatoes”, a distinctive artifact associated with this Socelars variant.
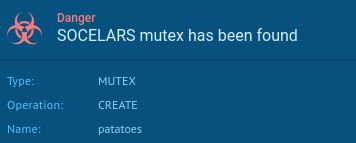 The Interactive Sandbox detected Socelar’s mutex
The Interactive Sandbox detected Socelar’s mutex
The malware then contacts the iplogger[.]org service. In this context, the public IP-logging service acts as a proxy layer, recording the victim’s IP address, User-Agent, timestamp, and geographic location for the attacker before transparently redirecting the request further, potentially toward a command-and-control server or the next attack stage.
At this point, all analyzed samples were observed to terminate intentionally with a crash, preventing further visible execution while preserving the attacker’s collected reconnaissance and telemetry.
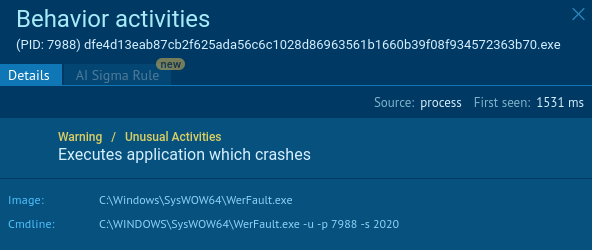 Intentional application crash to prevent visible execution
Intentional application crash to prevent visible execution
ANY.RUN’s Threat Intelligence Lookup provides critical capabilities for detecting, investigating, and responding to Socelars activity across environments.
When security alerts surface potential Socelars-related artifacts, such as suspicious installers, file hashes, domains, or browser-data access behavior, SOC analysts can query TI Lookup to immediately determine whether those indicators are linked to known session-stealing campaigns.
TI Lookup enriches raw indicators with:
This turns isolated alerts into actionable intelligence within seconds, enabling faster containment of threats that monetize access quickly.
TI Lookup connects indicators to interactive sandbox sessions where Socelars attack chains have already been executed and recorded.
Instead of re-analyzing suspicious files from scratch, teams can:
Start exploring Socelar’s activity using a threat-name search:
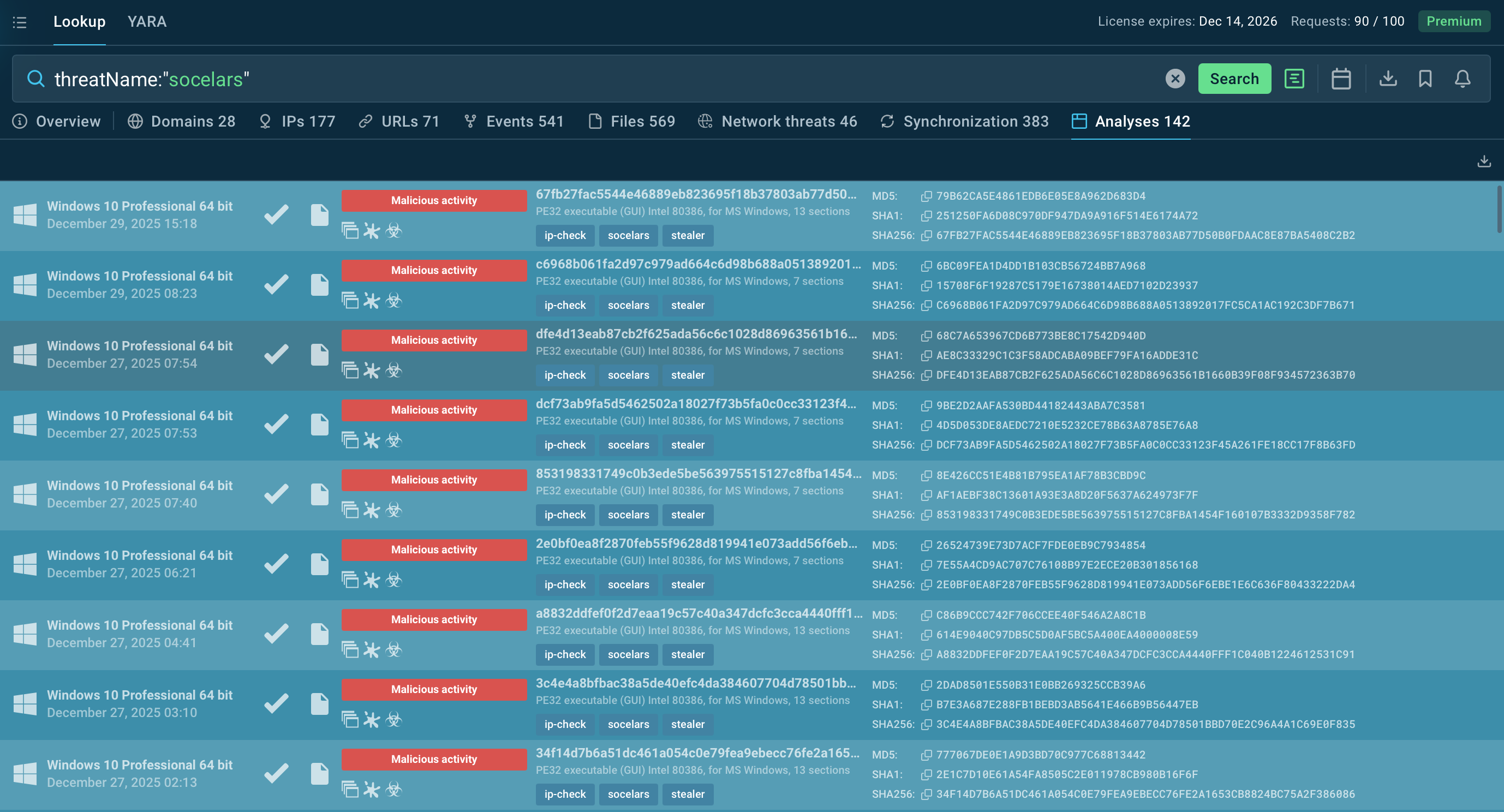 Fresh Socelar’s sandbox analyses found via TI Lookup
Fresh Socelar’s sandbox analyses found via TI Lookup
This immediate visibility shortens investigation time and accelerates response decisions.
With 40+ searchable parameters, including process activity, command lines, file paths, registry interaction, and network indicators, analysts can investigate Socelars infections from multiple angles.
For example, correlating browser-data access patterns or suspicious installer execution across submissions can reveal:
This allows defenders to move from single-incident response to campaign-level understanding.
TI Lookup supports YARA-based searching and validation, allowing security teams to test custom detection logic against a large corpus of analyzed malware.
For Socelars, this helps teams:
Beyond reactive investigation, analysts can use TI Lookup to hunt for hidden Socelars activity that may have bypassed initial alerts, particularly important for malware focused on quiet session theft rather than visible disruption.
Combining sandbox intelligence with large-scale threat correlation delivers measurable outcomes:
Socelars is dangerous because it targets business access instead of systems, stealing sessions and account data that attackers can monetize quickly, often before teams realize anything is wrong. The fastest way to reduce impact is to confirm behavior early and widen visibility beyond a single alert with threat intelligence.
Try TI Lookup to find related Socelars activity, validate indicators in seconds, and understand campaign scope fast: just sign up to ANY.RUN.