Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Gunra ransomware, a financially motivated threat actor that emerged in April 2025, deploys double-extortion tactics to encrypt victims' data and threaten leaks of exfiltrated information, primarily targeting Windows and Linux systems across healthcare, manufacturing, and other sectors worldwide.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
23 January, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
23 January, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
You can also use TI Lookup to contextualise Gunra’s campaigns and defend proactively. Search by the threat’s name and analyze its sandbox detonations with full kill chains, IOCs, and TTPs.
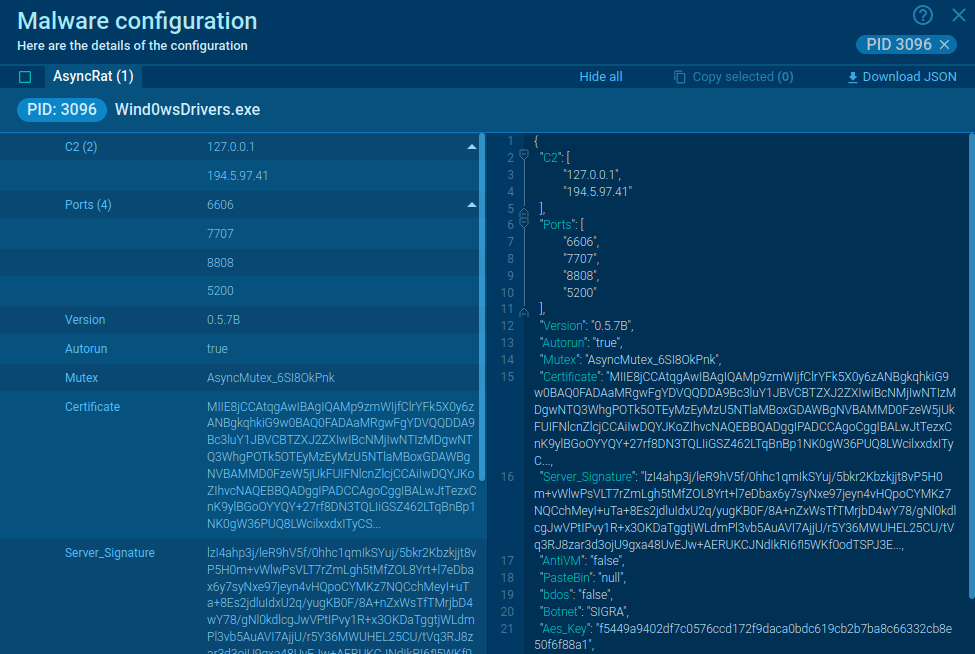
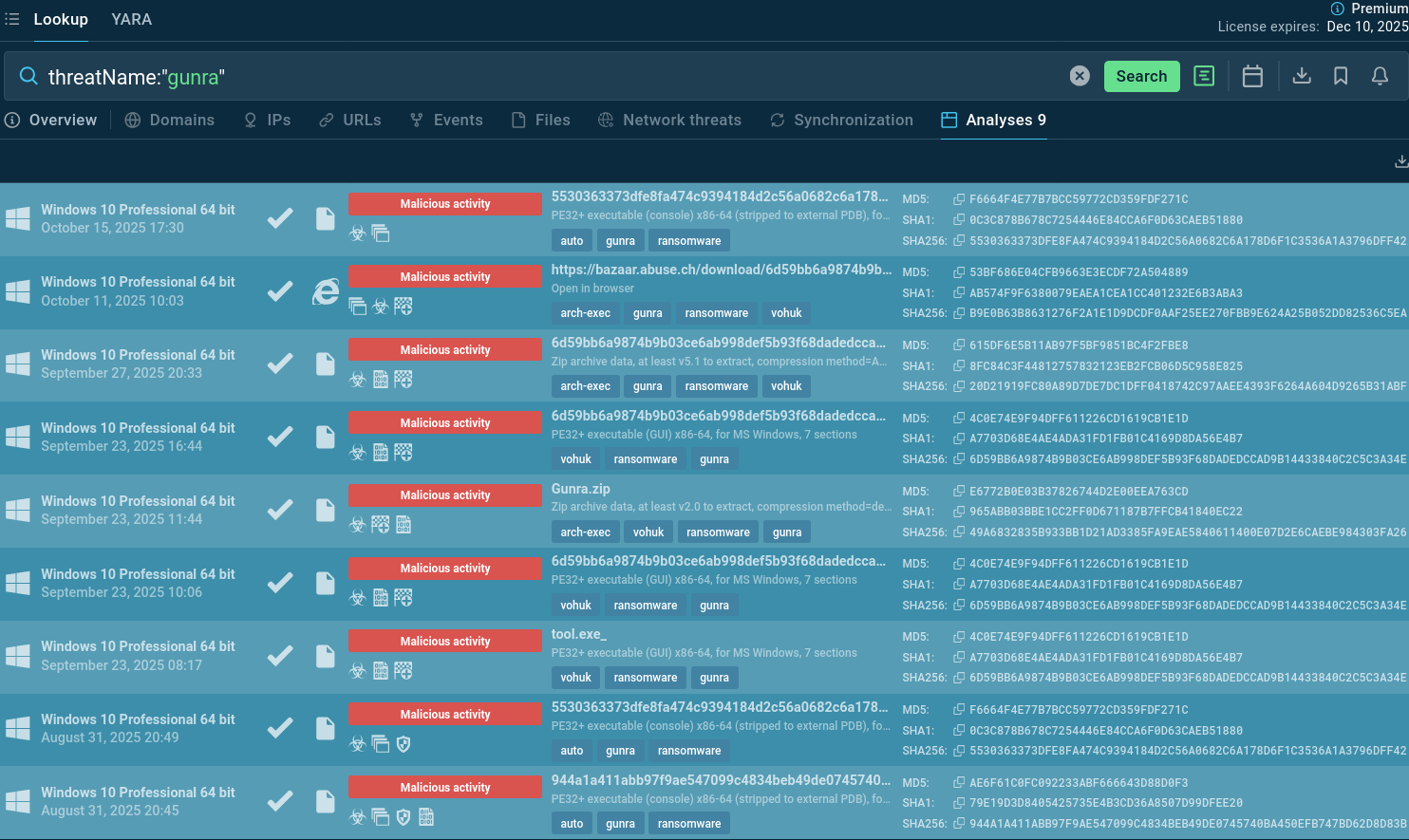 Gunra samples Sandbox analyses found via TI Lookup
Gunra samples Sandbox analyses found via TI Lookup
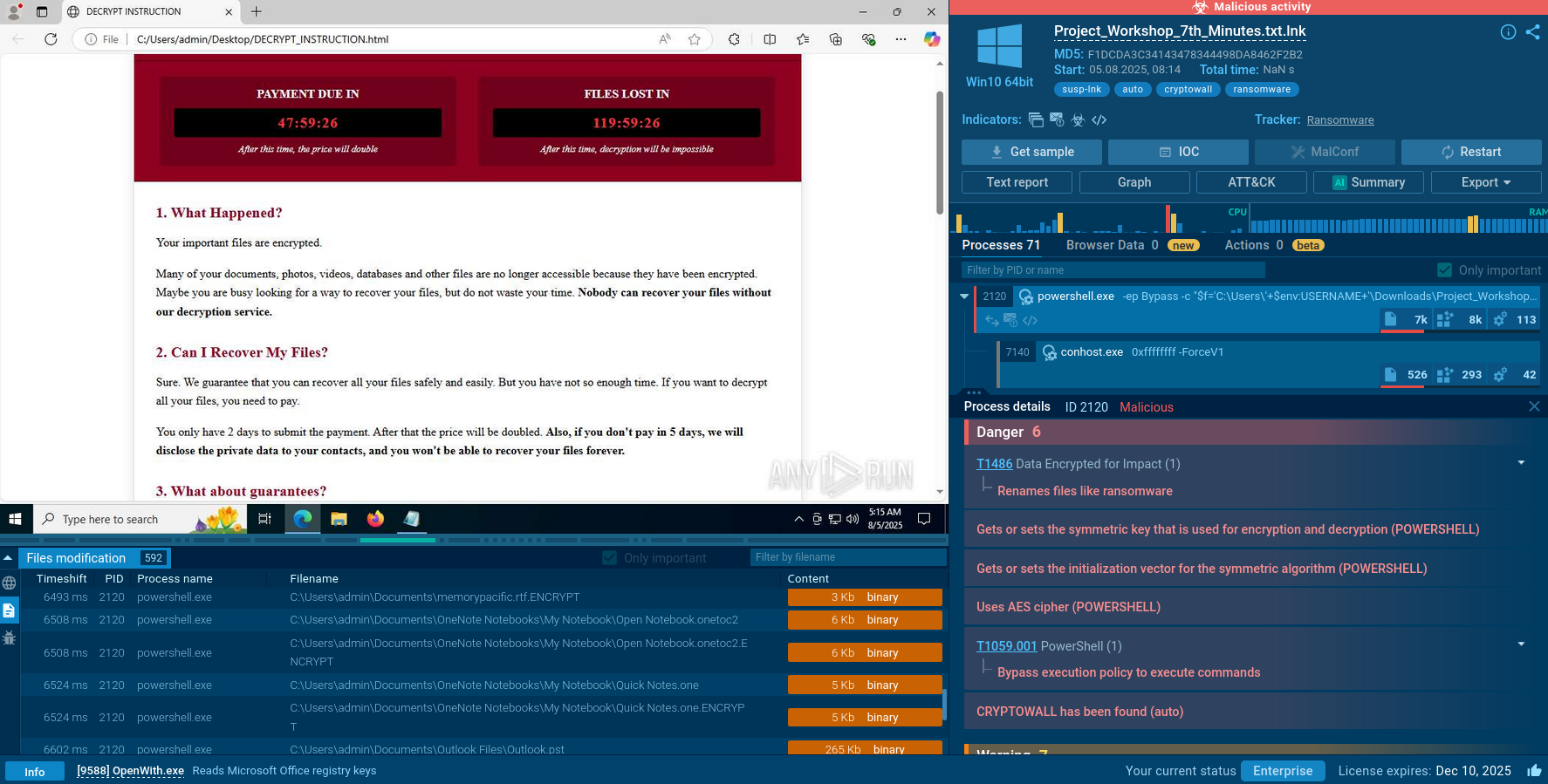
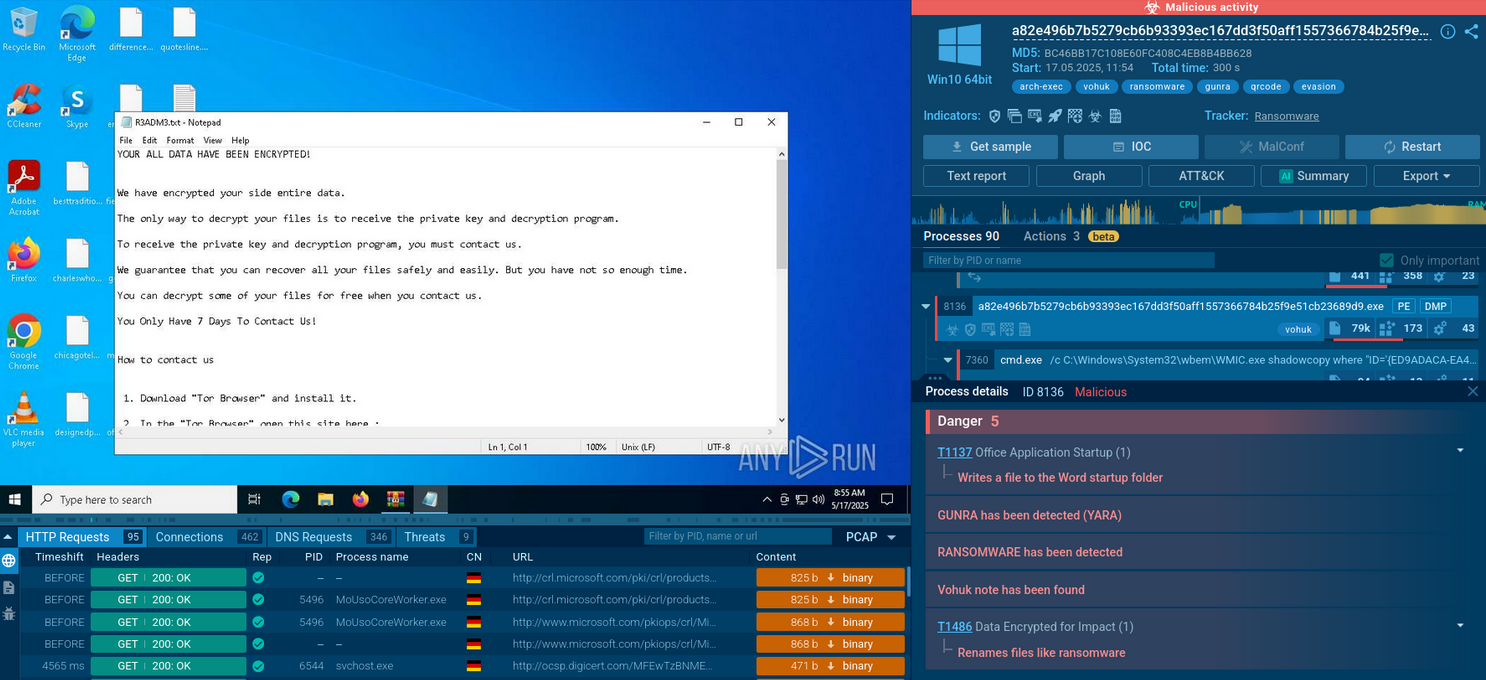 Gunra sample detonated in the Sandbox
Gunra sample detonated in the Sandbox
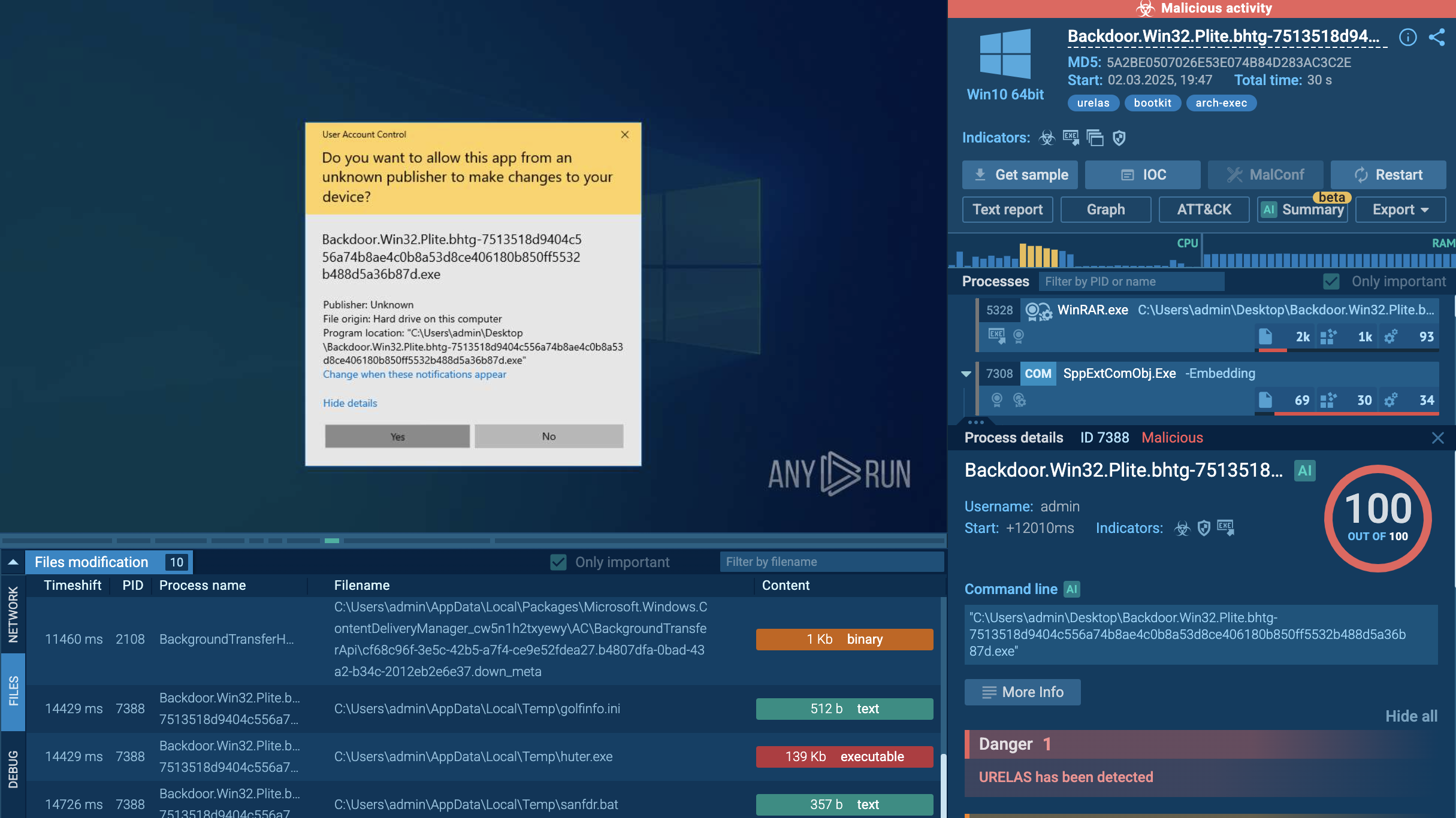
Gunra is a modern ransomware strain believed to be based on the leaked Conti ransomware source code, written in C/C++, and specifically designed to target Windows and Linux operating systems. The malware employs advanced encryption methods combining ChaCha20 symmetric encryption with RSA-2048 asymmetric keys, making unauthorized decryption virtually impossible without the attackers' private key.
Upon execution it enumerates running processes and system information, detects debugging tools, injects into trusted processes, deletes Volume Shadow Copies (via Windows Management Instrumentation (WMI)), then begins encryption of files (appending a “.ENCRT” extension) and drops a ransom note “R3ADM3.txt” in every folder.
The malware not only encrypts victims' files but simultaneously exfiltrates sensitive data, threatening to publish stolen information on Tor-hosted leak sites if ransom demands are not met.
The ransomware group behind Gunra operates with clear financial motivation, utilizing professional infrastructure including negotiation portals styled after messaging applications like WhatsApp, complete with assigned roles such as "Manager" to facilitate communication with victims. This level of organization suggests a well-resourced operation capable of sustained campaigns against high-value targets.
The group's strategy emphasizes speed: victims must initiate contact within five days, or stolen data, often terabytes in volume, is published on underground forums. This urgency, combined with free decryption of sample files as proof-of-concept, has pressured organizations into rapid negotiations, with demands ranging from $7 million to $10 million, though inconsistent pricing suggests an evolving operation.
Attackers maintain an active data leak site on the dark web where they publicly shame victims who refuse to pay, a tactic designed to maximize pressure and demonstrate their willingness to follow through on threats.
Gunra exhibits a broad, opportunistic victimology, prioritizing industries with high-value data and operational dependencies over geographic or size-based selectivity. Primary sectors include manufacturing (six confirmed victims, the most targeted), healthcare, pharmaceuticals, real estate, electronics, beverage production, energy, and IT services.
The group avoids U.S.-based entities, focusing instead on international operations in Asia (Japan, South Korea, Taiwan), the Middle East (UAE, Egypt), Latin America (Brazil, Panama, Argentina), Europe (Italy, Turkey, Canada), and beyond.
Mid-sized to large enterprises dominate the victim pool, with examples like energy firms and hospitals facing 8-40 TB data exfiltration. This pattern aligns with double-extortion goals, exploiting sectors where downtime or data exposure incurs regulatory fines, reputational damage, or supply chain disruptions.
As of October 2025, Gunra's DLS lists 19 victims, with a surge in manufacturing and critical infrastructure attacks signaling intent to escalate against high-impact targets
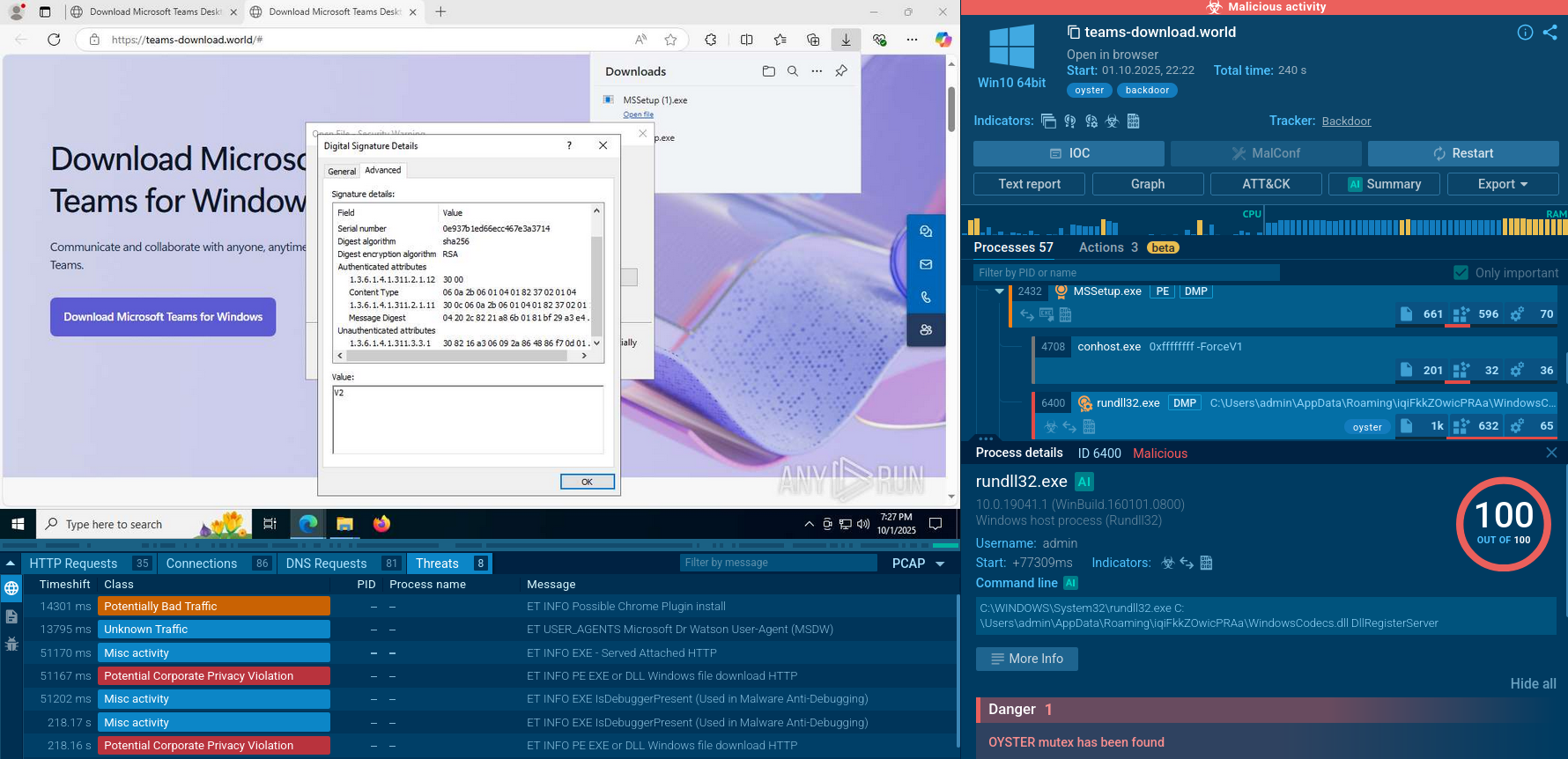
Gunra ransomware gains initial access primarily through phishing emails with malicious attachments or links, exploiting human error to deliver payloads via exploit kits. Weak Remote Desktop Protocol (RDP) configurations serve as another vector, allowing brute-force or credential-stuffing entry.
Once inside, the DONOT loader deploys the ransomware, enabling lateral movement via SMB shares, PsExec, or WMI for network propagation. It spreads by enumerating domains, injecting into remote processes, and exploiting unpatched vulnerabilities in Windows/Linux environments.
Cross-platform binaries facilitate hybrid network traversal, while obfuscation evades EDR tools during exfiltration over Tor or proxies. Post-compromise, it self-propagates to mapped drives, ensuring widespread encryption before detection
Upon initial execution, the malware creates a unique mutex to prevent multiple instances from running simultaneously, ensuring efficient resource utilization and avoiding detection anomalies that might result from duplicate processes. It immediately calls GetNativeSystemInfo to assess the host system's capabilities, sizing its thread pool based on available CPU cores to maximize encryption speed.
The reconnaissance phase involves system enumeration, with the malware cataloging running processes, installed software, network configurations, and available storage volumes. This intelligence gathering allows Gunra to identify high-value targets like database servers, file shares, and backup systems. The malware uses functions like FindNextFileExW to recursively scan directories and build a target list of files matching specific extensions.
Before encryption begins, Gunra executes its anti-recovery procedures, systematically deleting Volume Shadow Copies through WMI commands. The malware may also terminate processes associated with backup software, database management systems, and security tools that could interfere with encryption or detect the attack in progress.
For each file, Gunra generates a unique ChaCha20 key, encrypts the file content, then encrypts that ChaCha20 key with the RSA public key hardcoded in the malware. This ensures that even if victims obtain the malware sample, they cannot decrypt their files without the attackers' RSA private key. The Linux variant includes additional flexibility, supporting partial encryption modes where only portions of large files are encrypted—dramatically accelerating the attack while still rendering files unusable.
Throughout execution, Gunra maintains minimal network communication, with the RSA public key embedded in the malware itself rather than retrieved from command-and-control servers. This reduces network traffic indicators that security tools might detect. The malware also employs obfuscation techniques and anti-debugging checks to hinder analysis by security researchers. Upon completing encryption, Gunra leaves behind ransom notes containing instructions for accessing the Tor-based negotiation portal, where victims can communicate with attackers to discuss decryption payment terms.
ANY.RUN’s Interactive Sandbox allows to observe Gunra’s tactics in action
The ransomware collects general information about the runtime environment.
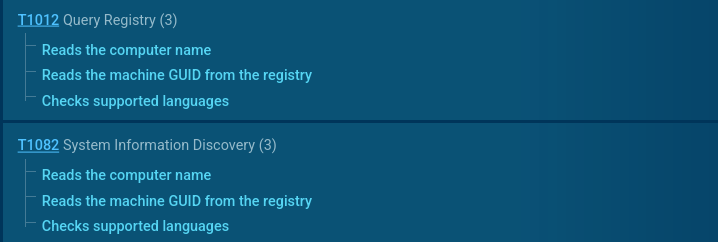 Gunra performs reconnaissance
Gunra performs reconnaissance
If the system passes all checks, the encryption process begins. The typical extension added by Gunra is .ENCRT.
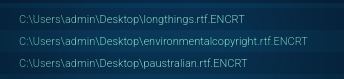 Gunra encrypting files
Gunra encrypting files
A ransom note usually named R3ADM3.txt is generated and is placed in each encrypted directory. Here is a typical snippet:
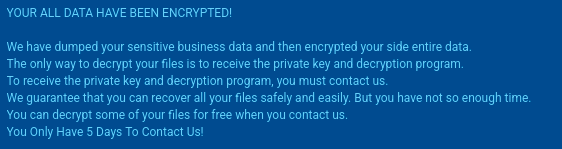 An extract from Gunra’s ransom note
An extract from Gunra’s ransom note
The note emphasizes urgency (5 days to make contact), offers free decryption of test files, and threatens data leakage, directing victims to a Tor site for negotiations.
Also, in many cases, Gunra deletes shadow copies via WMIC, with the command following the pattern:
cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{id}'" delete
The command is executed with different IDs. This prevents system recovery through VSS, enhancing the attack's impact and minimizing the chances of independent data recovery.
Threat intelligence provides early warnings about Gunra’s campaigns, leak sites (.onion URLs), known victims, TTPs (techniques, tactics, procedures) and IOCs (hashes, IPs, domains). This intelligence enables organizations to proactively hunt for signs of compromise, block malicious infrastructure, and tailor detection/prevention controls.
Search TI Lookup with the threat name and a region ID to sort out Gunra samples analyzed by Sandbox users from your country and be aware of the trends:
threatName:"Gunra" and submissionCountry:"NG"
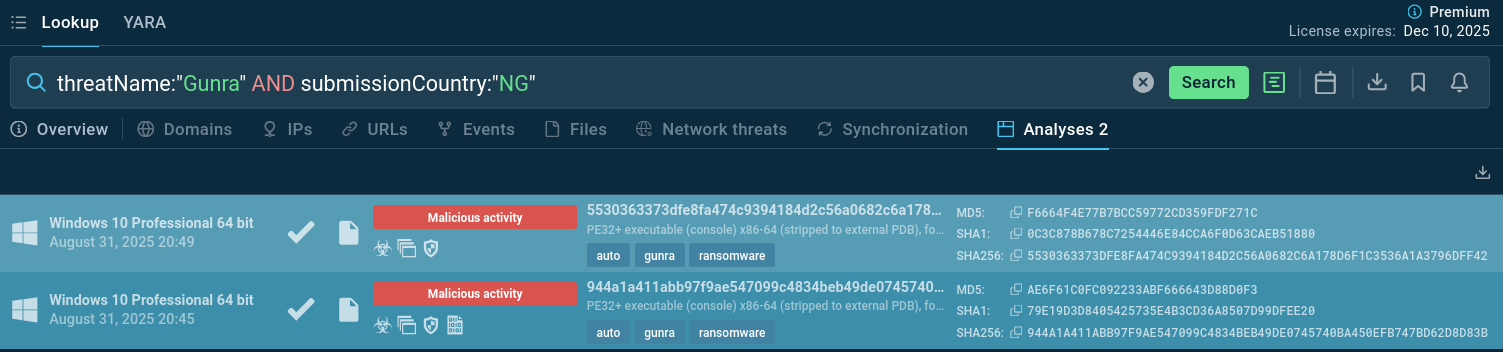 Gunra samples submitted to the Sandbox from Nigeria
Gunra samples submitted to the Sandbox from Nigeria
Nigeria has been one of the first targeted regions, but as we can see it’s not being under Gunra’s pressure recently.
Gunra ransomware is a potent and rapidly emerging threat: blending advanced evasion, encryption and data exfiltration in a double-extortion model. Organisations across sectors must take it seriously: not just as an endpoint or IT issue but as a business risk encompassing operations, legal/regulatory, reputational and financial exposures.
Defending effectively requires combining strong endpoint/network controls, backup and recovery strategies, detection/response capabilities, threat intelligence and sandbox-driven analytics. By anticipating threats like Gunra, organisations improve their resilience and reduce the likelihood of becoming the next victim.
Start gathering actionable threat intelligence on Gunra by signing up to ANY.RUN’s TI Lookup: protect your business with timely detection and response.