Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


GravityRAT is a sophisticated spyware and remote access trojan that has been actively targeting organizations and government entities since 2016. It uses innovative anti-analysis techniques and made an evolution from a Windows-only threat to a cross-platform espionage tool capable of compromising Windows, Android, and macOS systems.
|
RAT
Type
:
|
Unknown
Origin
:
|
|
1 January, 2016
First seen
:
|
29 January, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 January, 2016
First seen
:
|
29 January, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
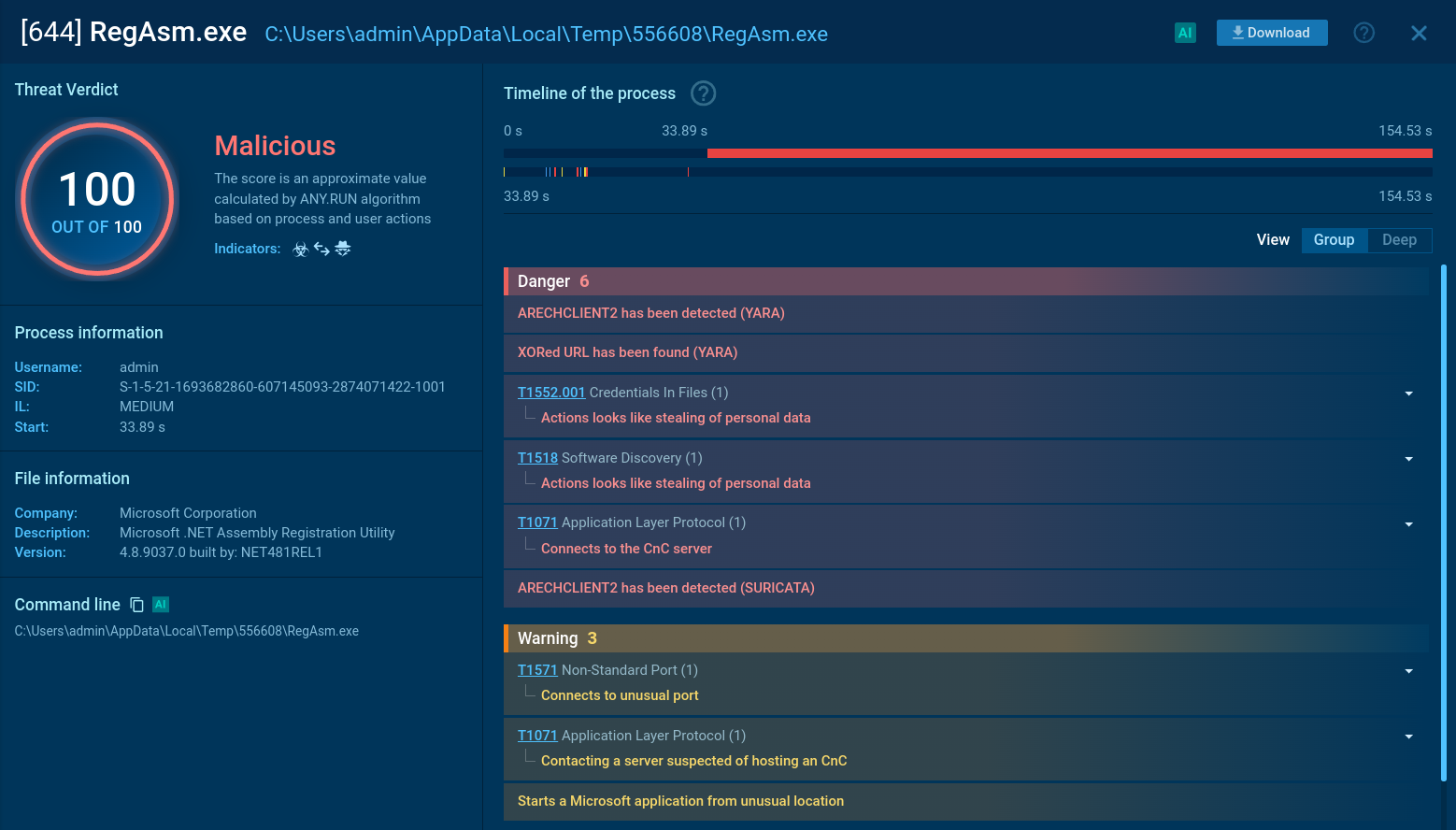
 GravityRAT sandbox analyses with IOCs and TTPs
GravityRAT sandbox analyses with IOCs and TTPs
 GravityRAT malware detonated in ANY.RUN’s Sandbox
GravityRAT malware detonated in ANY.RUN’s Sandbox
GravityRAT is a remote access trojan designed for long-term espionage operations. The malware has undergone continuous development over nearly a decade, with operators consistently adding new capabilities while maintaining the same command-and-control infrastructure.
The threat demonstrates remarkable persistence and sophistication, utilizing digital signatures to appear legitimate, employing multiple programming languages (.NET, Python, Electron), and disguising itself as various legitimate applications including secure messaging apps, file-sharing tools, media players, and cloud storage services.
The malware's most distinctive feature is its extensive use of anti-virtual machine and anti-sandbox techniques. Researchers have identified seven different VM detection methods employed by GravityRAT, including checking BIOS versions, searching for hypervisor artifacts, counting CPU cores, and most notably, querying CPU temperature through Windows Management Instrumentation.
This temperature check is particularly effective because most hypervisors including Hyper-V, VMware Fusion, VirtualBox, KVM, and Xen do not support temperature monitoring, causing them to return error messages that immediately reveal the presence of a virtual environment.
The malware operates through a sophisticated infrastructure managed by GravityAdmin, a custom administration panel that allows operators to coordinate multiple campaigns simultaneously. Each campaign operates under specific codenames such as FOXTROT, CLOUDINFINITY, CHATICO for Android-based infections, and CRAFTWITHME, SEXYBER, and CVSCOUT for Windows-based attacks using the HeavyLift loader.
GravityRAT campaigns have predominantly targeted entities within the Indian subcontinent, with a particular focus on military organizations, government agencies, defense contractors, police departments, and other sensitive institutions. The threat actor behind GravityRAT, attributed to Pakistani state-sponsored groups with tactical overlaps to Transparent Tribe (also known as APT36), has expanded its targeting beyond military and government sectors to include educational institutions and commercial enterprises.
Between 2016 and 2018, approximately 100 infections were documented among defense, police, and government employees in India. More recent campaigns from 2022 through 2024 have shown continued activity, including the attempts to compromise WhatsApp backups and target both Indian military personnel and individuals within the Pakistan Air Force. The highly targeted nature of these campaigns is evidenced by distribution methods that require specific credentials, geographic locations, or time windows to access malicious download sites.
GravityRAT typically spreads through targeted spear-phishing emails containing malicious Office documents with macros or exploits for Windows infections. On Android, it disguises itself as legitimate apps, such as fake messaging platforms (e.g., BingeChat, Chatico, or SoSafe Chat), distributed via third-party sites or social engineering. It does not self-propagate laterally but relies on initial access through social engineering, with recent campaigns combining Android trojans and Windows loaders like HeavyLift.
When macros are enabled, the malicious code copies the document to a temporary directory, renames it as a ZIP archive, decompresses it to extract the executable payload, and creates a scheduled task to execute the malware while maintaining persistence.
The RAT operates through a multi-stage infection and command-and-control architecture. Upon initial execution, the malware first performs extensive environment checks to determine if it's running in a physical machine or a virtual/sandbox environment. These checks include querying the MSAcpi_ThermalZoneTemperature WMI entry for CPU temperature, examining BIOS versions for VM indicators (VMware, Xen, AMI), searching for VM hypervisor artifacts, analyzing MAC addresses for known VM prefixes, and counting CPU cores.
If the malware determines it's running on a real system, it proceeds to establish persistence through scheduled tasks and begins its data collection operations. The malware communicates with its command-and-control infrastructure via HTTP, typically using PHP endpoints with variant-specific URI paths. For example, different versions contact paths like /ROMEO/[hash].php or /TANGO/[hash].php. Initial connections often retrieve dynamic C2 addresses from hardcoded domains, allowing operators to rotate infrastructure while maintaining control.
GravityRAT implements a modular architecture where different components handle specific functions. The Android version, for instance, uses background services that periodically contact C2 servers, sending IMEI identifiers and device status while awaiting commands. The malware employs AES encryption for certain operations, with some versions using distinctive strings like "lolomycin2017" as encryption salts. File exfiltration occurs in batches, with the malware creating ZIP archives of collected documents before transmission to attacker-controlled servers.
The GravityAdmin panel provides operators with real-time visibility into infected systems, displaying lists of compromised machines organized by campaign codename and offering buttons to trigger various malicious actions against one or multiple systems simultaneously. This centralized management enables efficient coordination of large-scale espionage operations across multiple campaigns.
ANY.RUN’s Interactive Sandbox provides isolated, instrumented environments where security researchers and analysts can safely execute suspicious files without risking production systems.
View a GravityRAT sample analysis
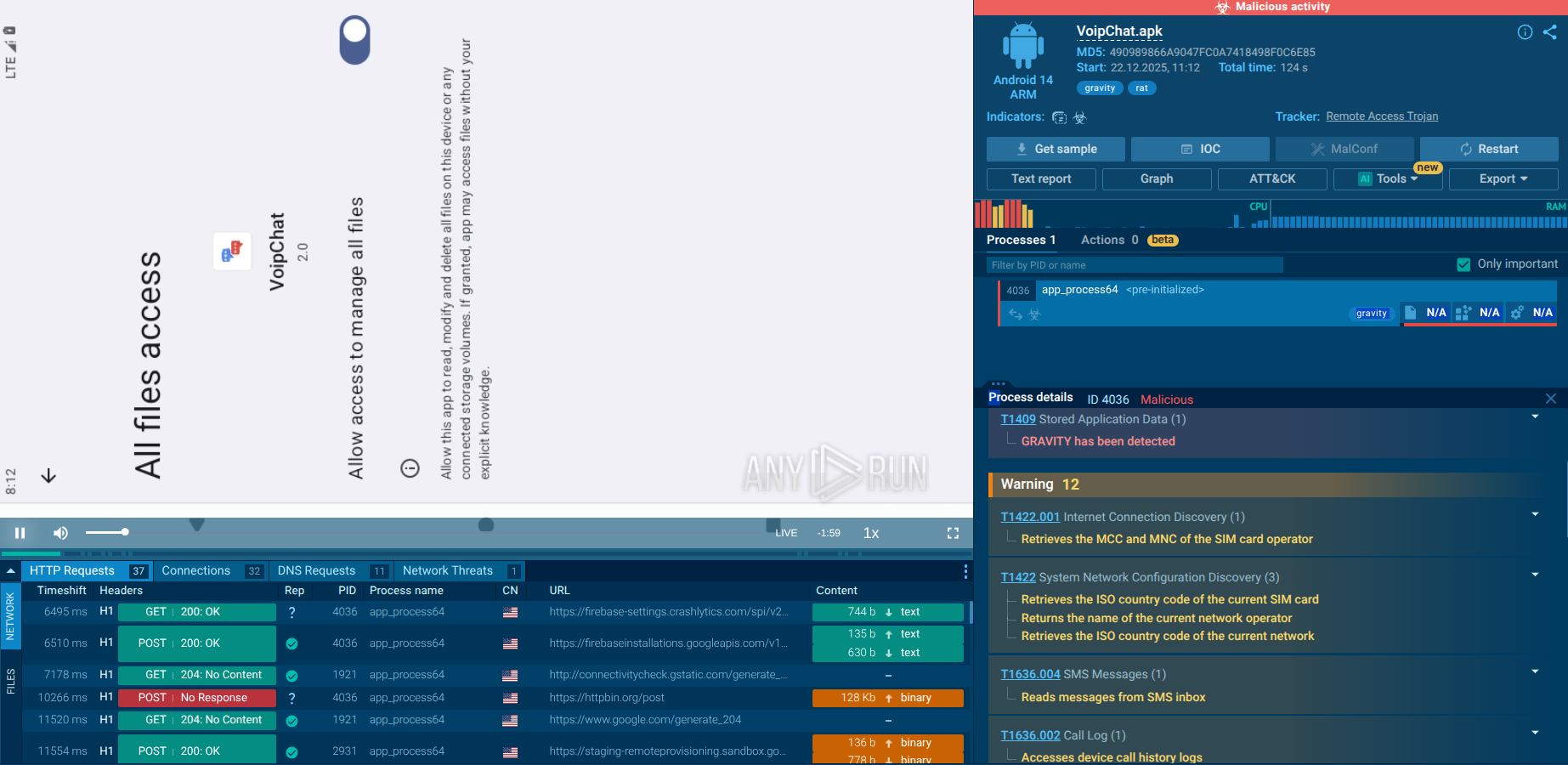
 GravityRAT Android version detonated in the Interactive Sandbox
GravityRAT Android version detonated in the Interactive Sandbox
The analyzed sample is disguised as a messaging app and is typically distributed through websites that advertise a “free messenger.”
App appearance
The malicious APK presents itself as “Speak Freely,” an allegedly encrypted messaging app with the tagline:
“Say ‘Hello’ in a different messaging experience. An encrypted focus on privacy, combined with all of the features you expect.”
 GravityRAT impersonating an Android messenger
GravityRAT impersonating an Android messenger
Network information collection
GravityRAT retrieves the MCC and MNC of the SIM card operator, the SIM card’s country ISO code, the name of the current network operator, and the current network’s ISO code. This allows the malware to verify the device’s network configuration and confirm internet connectivity, which is required for further communication with the C2 server.
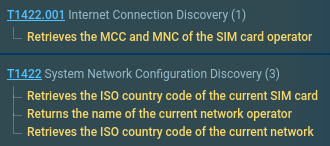 GravityRAT’s proccess tree exposed in the Sandbox
GravityRAT’s proccess tree exposed in the Sandbox
Observed MITRE ATT&CK techniques (network discovery):
File and directory scanning
The malware scans files and directories, listing file names without full paths to identify potential exfiltration targets (T1420 File and Directory Discovery – Get file name without full path).
 GravityRAT’s proccess tree exposed in the Sandbox
GravityRAT’s proccess tree exposed in the Sandbox
Data theft
GravityRAT extracts SMS messages and call logs from protected user data, saving them in text files (e.g., /storage/emulated/0/bc/ms.log) before exfiltrating them to the C&C server.
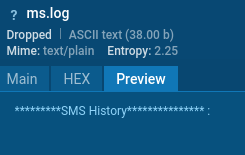 GravityRAT creates SMS history log
GravityRAT creates SMS history log
Observed MITRE ATT&CK techniques:
The malware also targets files with extensions such as .jpg, .pdf, .txt, and WhatsApp backups.
Exfiltration and cleanup
Stolen files are sent to the attacker and then deleted from the device (in the case of logs). Communication with the C2 server uses HTTPS, providing an encrypted channel for data exfiltration and command reception.
Observed MITRE ATT&CK technique: T1521 Encrypted Channel – Establishing a connection.
It is worth emphasizing once again the importance of installing applications only from trusted sources and not from random websites—this practice significantly reduces the risk of device infection.
Utilize TI Lookup to query known indicators and discover related infrastructure and samples. Conduct proactive malware hunting using YARA rules specifically developed for GravityRAT detection.
A single IOC lookup can tell whether your business sector and geographical location are actively targeted by GravityRAT campaigns:
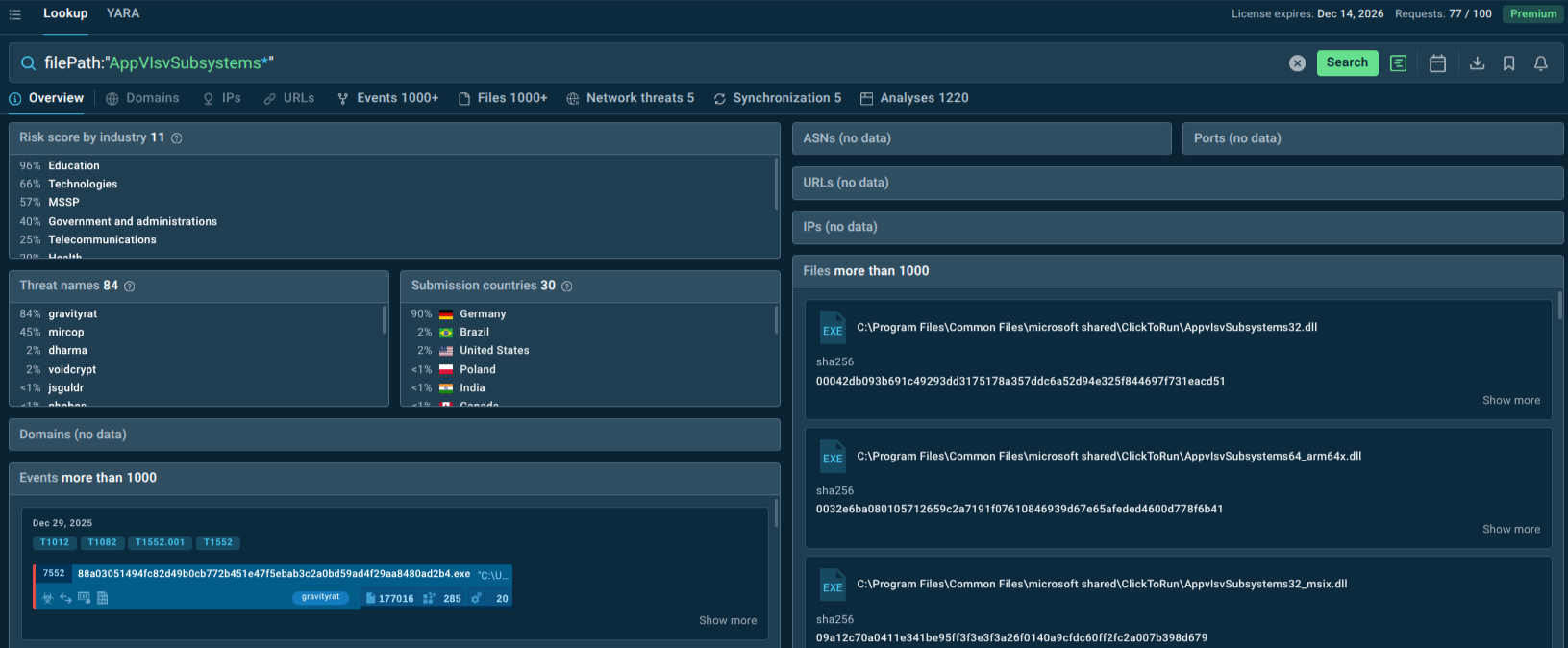 Search by malicious files spotted in GravityRAT campaigns
Search by malicious files spotted in GravityRAT campaigns
GravityRAT stands out among RAT families due to its persistence, stealth, and multi-platform reach. Its targeted distribution, virtualization evasion, and ability to exfiltrate sensitive data make it a formidable threat for enterprises and high-value individuals alike. Proactive defense, threat intelligence, and robust detection tooling are key to mitigating its impact.
Trial TI Lookup to start gathering actionable threat intelligence on emerging malware: just sign up to ANY.RUN.
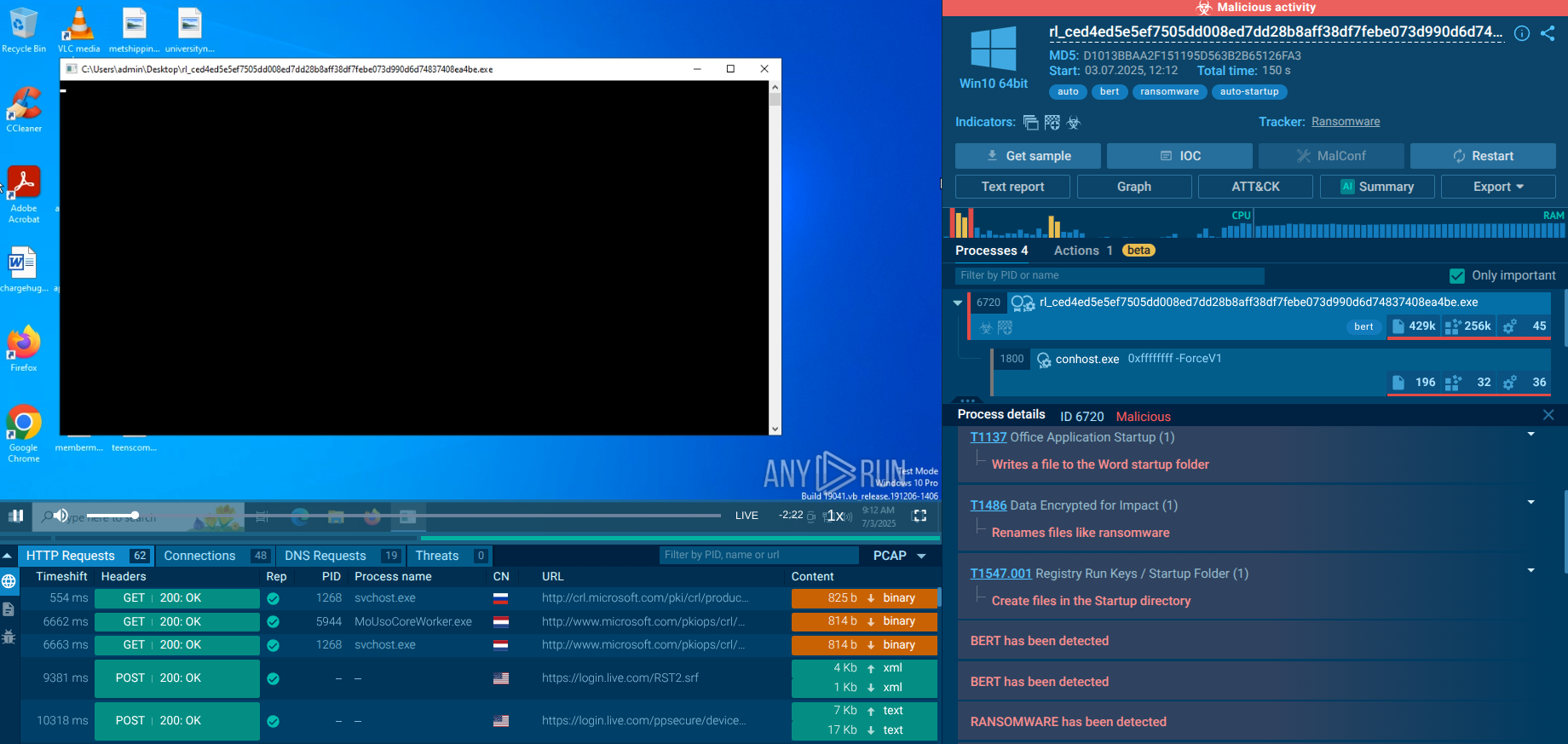
.png)