Every day, malware researchers, SOC, and DFIR professionals generate over 14,000 public tasks in ANY.RUN. This data helps us to uncover unique insights, such as which malware types have been most prevalent over the last three months.
Top malware families in Q2 2023
Our Q2 malware trends report showed that RATs and loaders were once again at the forefront of cyber threats, with RAT usage displaying an increase of 12.8% quarter over quarter.
In this article we will take a closer look at the threats you are most likely to face and examine the three most prominent malware families in Q2 2023:
- RedLine
- Remcos
- njRAT
1. RedLine
RedLine stealer, which first surfaced in March 2020, has quickly become the most widely used malware family. This is largely due to its ease of use, availability, and beginner-friendly C2 panel.
RedLine’s growth rate was notably high during the COVID-19 pandemic, and it remains a top threat today, using mostly mail spam as its primary delivery mechanism. It’s worth noting that adversaries utilize a wide range of formats to deliver this threat, including:
- Office documents
- PDF files
- RAR and ZIP archives
- Executables
- JavaScript files
RedLine Instances Were up 80% in Q2 2023
While RedLine has been the most commonly observed malware on our service for a while, its usage has grown quite a bit this quarter, jumping from 1895 detections in Q1 to 3415 in Q2 — that’s an 80% increase.
RedLine Execution Process
RedLine’s execution process, which you can emulate in ANY.RUN is generally straightforward. In essence, the main binary initiates itself, and the parent process ceases. The malware might originate from an alternate binary or could be the primary binary itself.
When a new process is instigated by the malware, RedLine begins its primary task: information gathering. It collects sensitive data from the compromised system, including items such as passwords, and transmits this data to C2.
Once the data collection and transmission tasks are complete, RedLine halts its operation. Worth noting is that the stolen data is dispatched in two formats: non-encrypted and base64 encoded.
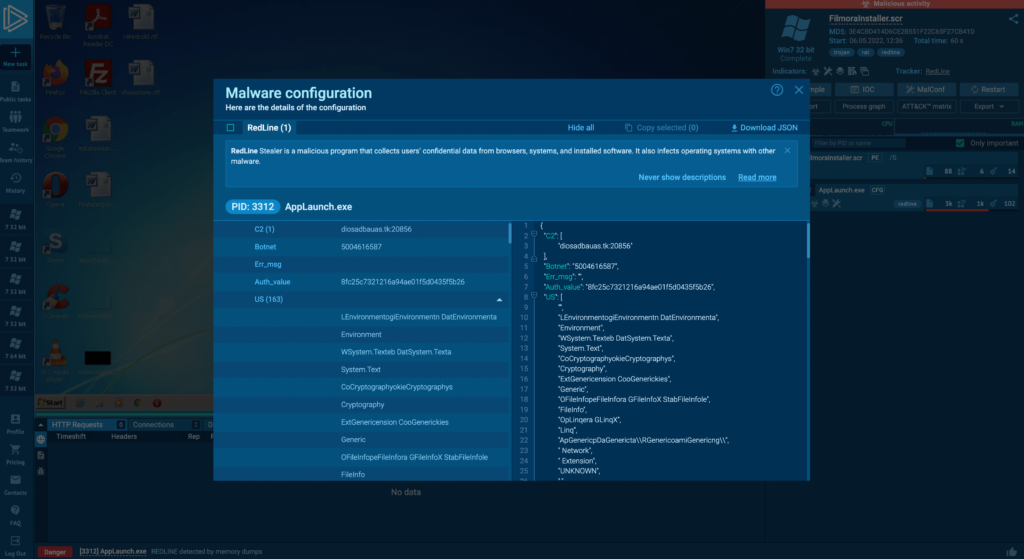
RedLine features an extensive configuration file which ANY.RUN can extract automatically.
2. Remcos
Remcos RAT was the second most popular malware family in Q2 2023, sitting at over 1300 detections.
This threat first emerged in 2016, when it was initially offered for sale within underground hacker groups operating on the dark web.
The creators of Remcos RAT have been consistently enhancing its capabilities throughout its existence. The malware is kept highly active, with new versions being rolled out nearly every month. Back in April 2019, this malware could be bought for a price ranging from just above $60 to over $400, depending on the chosen package — which contributes to its popularity.
Remcos Usage Remains Consistently High
Remcos saw a very marginal decrease of 1.2% quarter over quarter — this malware family is consistently just behind RedLine in terms of popularity. ANY.RUN users detected it 1368 times in Q2, compared to 1385 times in Q1.
Remcos Execution Process
Remcos can be deployed in a variety of forms. For example, it can be propagated as an executable file, named in a way that persuades users to open it. Alternatively, it can masquerade as a Microsoft Word file and exploit system vulnerabilities to download and execute its primary payload, as well as to obfuscate the server component.
In our analysis, once Remcos successfully infiltrated a device and initiated its execution process, it triggered the execution of a VBS script. This script operated through the command line and proceeded to unload an executable file.
The file constituted the primary payload, which undertook the main malicious actions: data theft, modification of the autorun value in the registry, and establishing a connection with the C2 server.
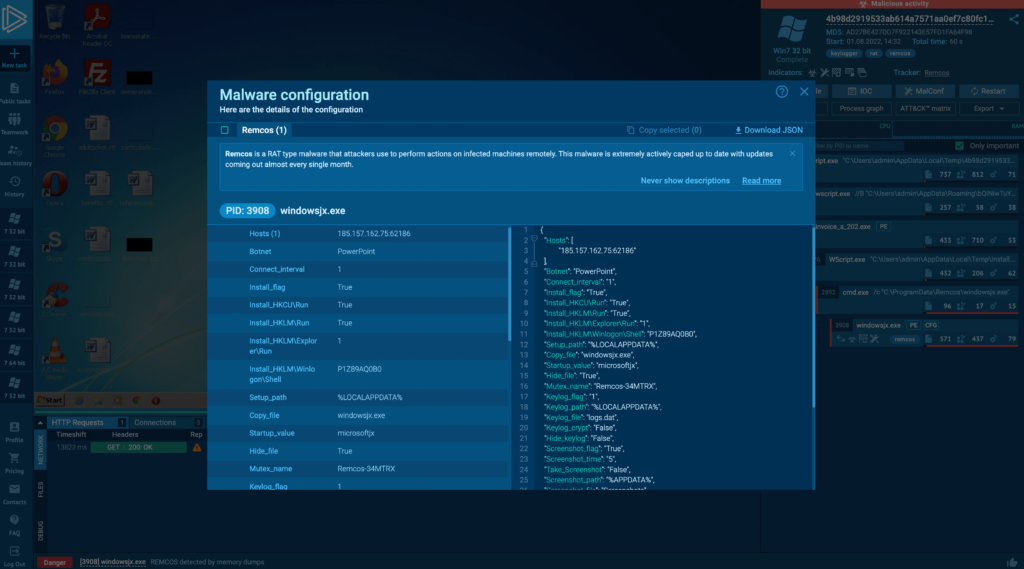
Using ANY.RUN, we were able to easily extract and decrypt Remcos config file, which provides valuable information about how our sample was set up.
For example, the adversary used a system environmental variable %LOCALAPPDATA% to point to a location where keylogging data will be stored. This usually corresponds to a path similar to “C:\Users[username]\AppData\Local“.
3. njRAT
njRAT, alternatively known as Bladabindi or Njw0rm, is notable for its accessibility, wealth of online tutorials, an abundance of information, and a comprehensive core feature set.
Though it was first detected in 2013, some related RATs were noted by researchers as early as 2012. Built on the .NET framework, njRAT equips hackers with the capability to remotely control a victim’s PC.
Its capabilities include:
- Recording the webcam
- logging keystrokes
- Extracting passwords from web browsers and a range of desktop applications.
Additionally, this malware provides hackers with command-line access to the compromised machine, facilitating process termination and remote execution and manipulation of files.
Also, njRAT also has the ability to alter the system registry. Once a system is infected, the trojan gathers multiple pieces of information about the infiltrated PC, including the computer’s name, operating system, location, usernames, and version of the operating system.
njRAT Popularity is up Slightly in Q2 2023
The usage of njRAT has gone up by 4.2%, jumping from 1096 detections in Q1 to 1142 detections in Q2.
njRAT Execution Process
NjRAT arrives in different forms — it can come attached to a phishing email as a malicious attachment, an archive with an executable file inside, or a malicious document which downloads NjRAT from a C2 server through macros.
In our task, we have a VBS file containing a script which initiates PowerShell to download the main payload from winupdt2023.000webhostapp[.]com/Att.jpg. After that, it injects itself into the RegSvcs.exe process to proxy the execution of code through a trusted Windows utility (MITRE T1218.009).
Once the process has been injected, it begins malicious activities such as connecting to a C2 server for commands, collecting information about the infected system, and stealing credentials.
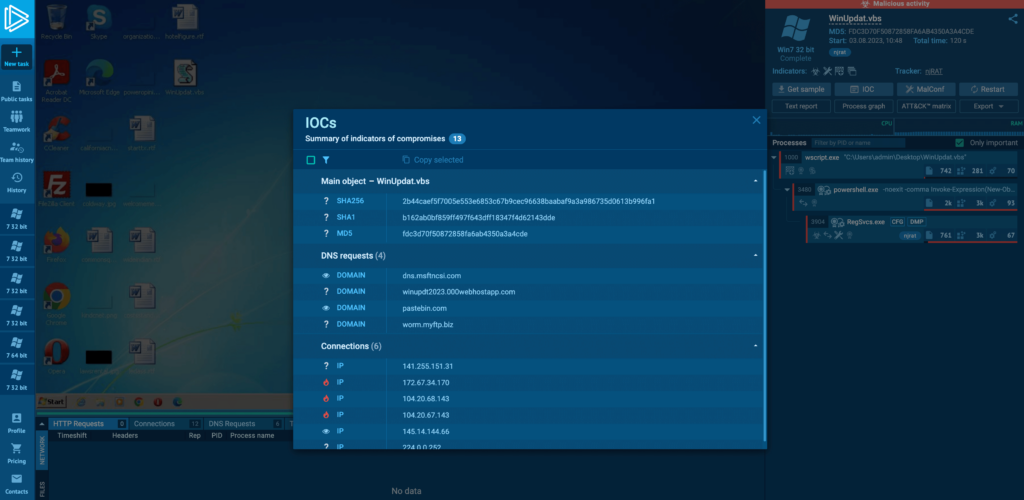
In ANY.RUN, you can easily collect njRAT IOCs.
Outtakes
The top 3 most popular families remained unchanged during all of the H2 of 2023:
- RedLine tops the chart. And it’s usage increased by 80.2% in Q2 2023, jumping from 1895 detections to 3415.
- Remcos is in the second spot. This RAT saw a marginal decrease of 1.2% quarter over quarter. It was spotted in ANY.RUN 1368 times in Q2 and 1385 times in Q1 2023.
- njRAT, concludes the top 3. It has seen an increase in usage by 4.2% in Q2 2023 with 1096 detections in Q1 and 1142 — in Q2
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments