Welcome to ANY.RUN‘s monthly updates, where we share what our team has been working on over the past month.
In June, we introduced new search capabilities for mutexes, added numerous YARA rules and config extractors, implemented packer detection, and expanded our Suricata ruleset. We also added several new signatures for enhanced threat detection.
Here’s a closer look at what we’ve done.
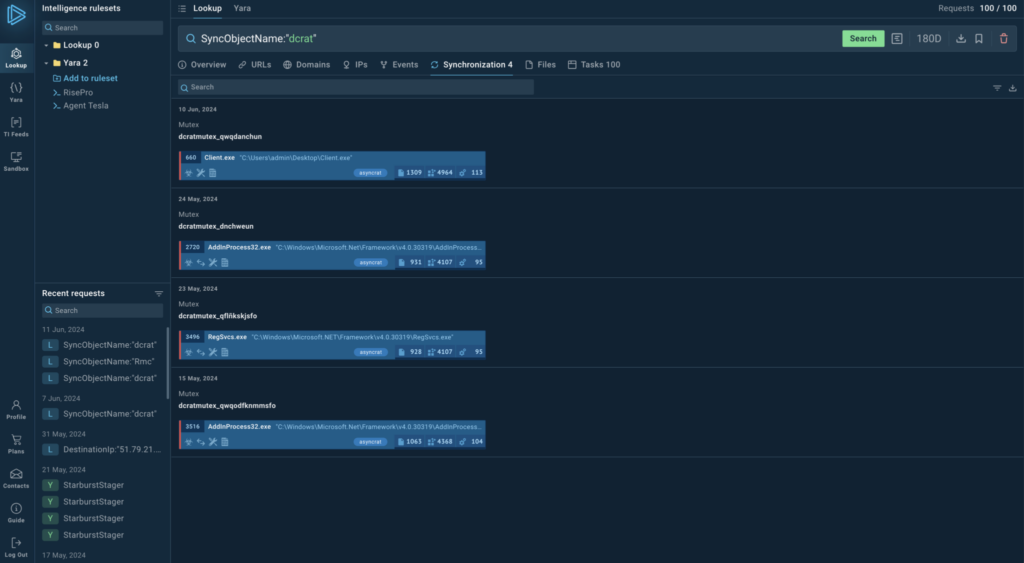
Mutex Search in TI Lookup
We’ve released an update that allows you to search for mutexes in TI Lookup and add them to your IOCs. The search results now make it easier to distinguish between malicious and legitimate mutexes, significantly speeding up your threat investigations.
New YARA Rules and Config Extractors
We’ve added a substantial number of new YARA rules and updated existing ones, many with config extractors. Here are some highlights:
- Rhadamanthys (shellcode detection)
- MoonstoneSleet (may drop SplitLoader and YouieLoad)
- SweetSpecter (RAT) and T9000 (backdoor)
We’ve also updated the config extractor for Danabot: implemented a fix and added C2 verification.
New Packer Detection
We’ve implemented detection for various packers, including:
Expanded Suricata Ruleset
We’ve significantly expanded our Suricata ruleset, adding 127 new rules:
- 101 rules for various phishing detection
- Additional auxiliary rules
- Creal Stealer detection
- Detection for abuse of Telegram/Steam websites as dead drop resolvers (DDR)
- NjRat variant (2.3R tXRAT) detection
New Signatures
In June, we added a total of 11 new signatures. Here are some highlights:
- Multiple phishing detection signatures (example one, example two)
- Shinra signatures
- Additional behavioral signatures
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free
2 comments








It’s interesting that after scrolling thru this entire website, there is NO direct mention of subscription costs …. Maybe too pricey for the average user?
Hi Demas,
Thank you for your comment.
You can find pricing details for ANY.RUN’s current plans at https://app.any.run/plans.
You can also ask any questions you may have directly at https://app.any.run/contact-us.
Best,
The ANY.RUN team