Welcome to ANY.RUN’s monthly update series, where we share what the team has been working on this past month.
In February, we released our biggest Threat Intelligence product yet — the ANY.RUN Lookup portal. We also introduced a new email analysis workflow with an RSPAMD Static Discovering Module, expanded threat coverage in the sandbox to include malware like HAMAS, WhiteSnake, and KitStealer.
New features
Threat Intelligence Lookup
Undoubtedly, the most significant release in February, Threat Intelligence Lookup, provides you with a portal to explore a centralized repository of millions of IOCs extracted from ANY.RUN’s database of interactive malware analysis sessions (sandbox tasks).
What makes our TI Lookup portal stand out? Because our data comes from sandbox tasks, we can connect all events that occurred within a single research session. You can search across all public sandbox tasks launched in ANY.RUN over the last 6 months and build precise queries using wildcards (*) and logical conditions (AND).
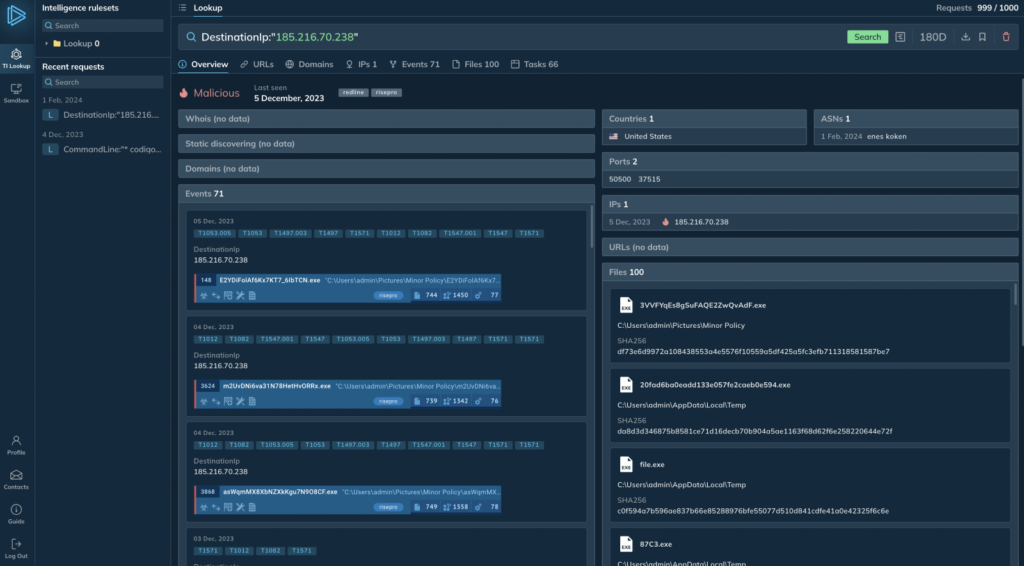
Analysis of linked processes, modules, files, network traffic, and registry activities helps a SOC team better understand encountered threats. Then, they can minimize potential damage to the infrastructure.
Read more about Threat Intelligence Lookup →
RSPAMD module
We’ve added a new module to Static Discovering. It integrates RSPAMD into ANY.RUN — an open-source email filtering system. RSPAMD is designed to detect and flag spam, phishing attempts, and other malicious content in emails.
With the RSPAMD module, analyzing emails becomes easier, helping you determine if you’re dealing with phishing. Features like Score, Content, and Header Descriptions allow you to gauge the email’s maliciousness even before opening it in the virtual machine, saving you time. However, it’s important to note that the information provided by this module is advisory.
RSPAMD’s description covers both the entire email and specific suspicious parts, such as headers or content. This allows you to make your own decision about the email’s safety.
Read more about using RSPAMD in ANY.RUN (case-study) →
SSO Improvements
We’ve addressed several SSO issues and added new features: the logout feature is now working smoothly, we’ve resolved the setup problem with SSO, and we’ve introduced a new feature allowing users to log in not only through our authorization window but also via third-party services. Now, with our SSO service, you can simply click on the designated block with ANY.RUN and seamlessly proceed already authorized.
Also, we’ve ensured compatibility with Azure and Okta, two of the most popular SSO providers, and tackled various other issues along the way.
Expanded threat coverage
In February, we implemented a new generic rule for Discord grabbers. These grabbers are typically coded in JavaScript (using Electron) or Python, with Discord being their primary target. Typically, their objective is to steal payment data, although some are capable of also nabbing passwords and cookies from web browsers, capturing screenshots, and executing other typical actions associated with stealers.
ANY.RUN now also detects KitStealer. This malware functions as both a downloader and a stealer, targeting clipboard contents and taking screenshots, with a primary focus on pilfering cryptocurrency wallets. It communicates with the server via HTTP in JSON format and employs XOR encryption for data transmission. Note its unconventional communication pattern: the server issues configurations for all malware, and each specific malware variant either seeks its own configuration or employs a standard one. Sometimes, it also drops QuasarRAT.
New Yara Rules
In February, we’ve added Yara rules that cover the following threat:
- HAMAS
- WhiteSnake stealer
- ZLoder (we’ve also fixed the exrtactor)
- CVE-2017-0199, an MS Office exploit
- RaspberryRobin
The Yara rule covering XMRig was fixed.
New Signatures
In February, we’ve added 26 new signatures to ANY.RUN. Here are the highlights:
- Phishing through the abuse of Squarespace Service (RGDA Domain Structure) has been detected.
- We’ve also covered a Mirai-based botnet, Gafgyt.DDoS, for which we’re developing rules specifically for Linux systems.
- We found a new and rare backdoor called TheClient. Additionally, we’ve detected the CodRun clicker, KeyBonza SockClipper, along with two stealers: KitStealer, and StealIt.
- We’re closely monitoring the activities of the Stegocampaign APT TA558 and the Dadsec phishing kit.
- We’ve expanded the set of rules covering the Meduza Stealer and shared them with the ET community.
Additionally, we’ve clarified rules for the CVE-2017-11882 exploit, specifically targeting obfuscated RTF documents with CLSID Equation Editor. We’ve also begun monitoring the SilentCryptoMiner miner with rules provided by the ET community.
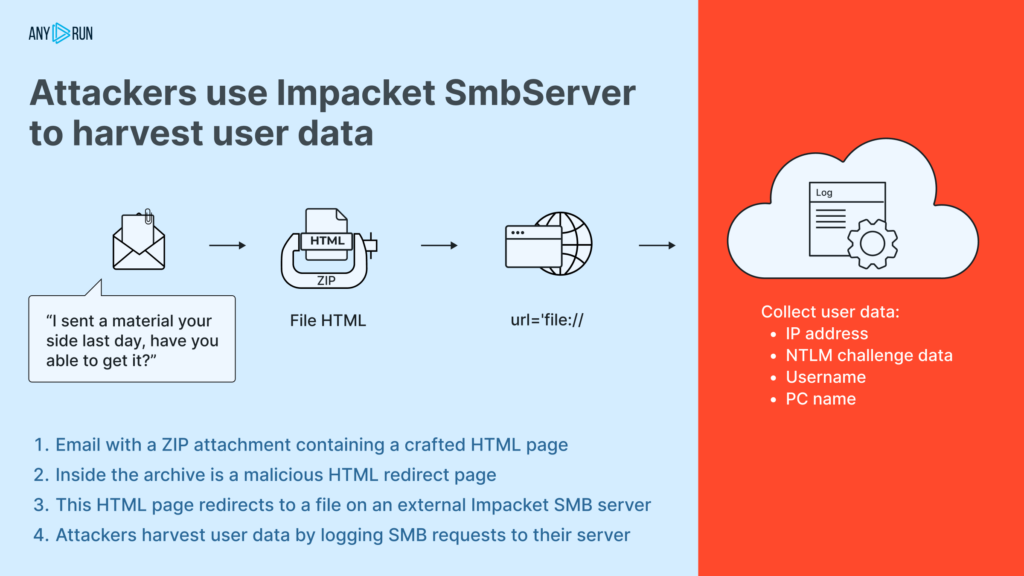
And last but not least, attackers have been using the Impacket SmbServer to harvest data from victims during a mass malicious email campaign from February 23 to February 29:
We talked about this threat in this tweet.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 400,000 professionals use our platform to investigate incidents and streamline threat analysis.








0 comments