As an enterprise considering ANY.RUN, you may have concerns about the privacy of your sensitive data.
We know that entrusting your information to a third-party can be daunting, especially in the context of a sandbox where you often have to upload confidential files for analysis.
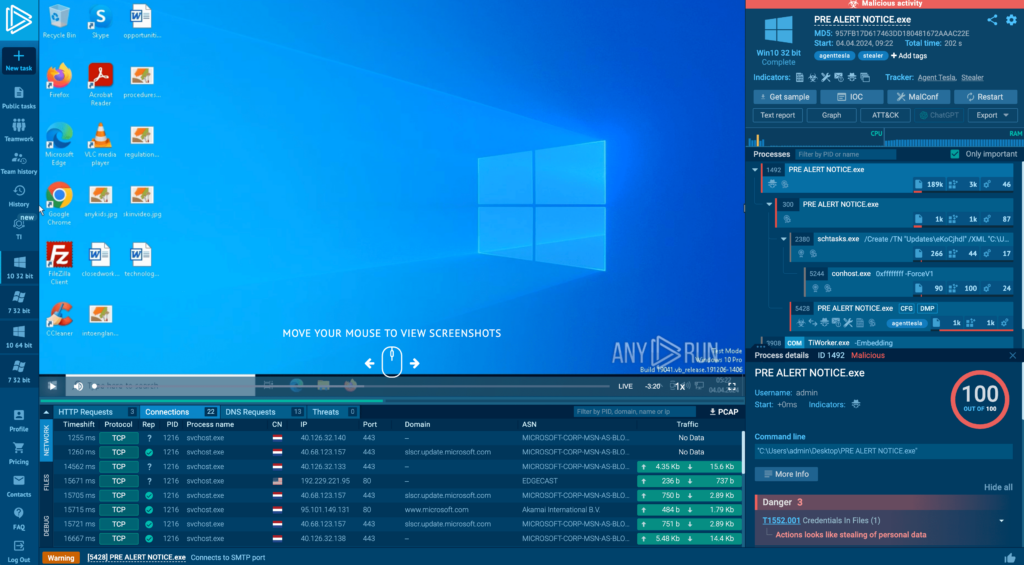
Here’s an overview of the ANY.RUN security features that help keep your data protected:
- ANY.RUN is hosted entirely in Germany, Europe, so you can rest assured that we are GDPR compliant.
- We follow the AICPA Trust Services Criteria as our preferred security framework: data is encrypted at-rest with the latest state-of-the-art AES-256 encryption; all data in transit is secured with TLS 1.3.
- We have several employees dedicated to ensuring that security measures are enforced throughout the company.
What’s more, we’ve implemented specific tools — most of which are exclusive to our Enterprise plan clients — to help you maintain control over your data.
Here’s a list of privacy and security tools ANY.RUN offers to our Enterprise customers:
Control who has access to your team’s tasks
Our Enterprise plan is designed for teams working together on malware analysis. But the larger the team, the higher the chances of someone making a mistake — like accidentally making a task public, visible to the whole ANY.RUN community, when they meant for it to be private.
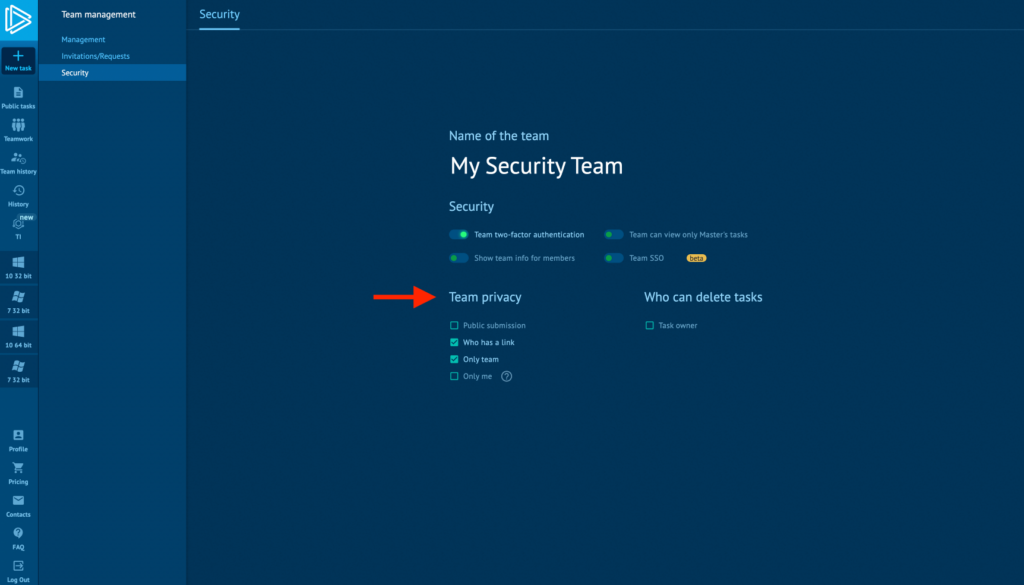
But this scenario is easily preventable by configuring your account settings correctly. In the team privacy settings, you can control what types of tasks your team members are allowed to create. For example, you could restrict junior analysts to only launch private tasks, while prohibiting them from deleting tasks they’ve created.
In ANY.RUN, you can launch tasks with 4 different visibility levels:
- Public submission: Anyone can view these tasks, and the information from them is used to improve our threat intelligence services.
- Who has a link: This setting works similar to a shared Google Doc, allowing you to share access with anyone who has the link.
- Only team: Visibility is restricted to users connected to your organization’s Master enterprise account.
- Only me (private): With this setting, no one except you can view the task.
For companies, you can configure it so that all tasks launched by your team are private, and only the Master account can view them. This can be useful, for example, when you temporarily bring an independent expert on board who doesn’t need to see the contents of your previous investigations.
Enforce 2FA across your entire team
For companies that need to comply with regulations such as GDPR and ISO 27001, one of the requirements is that all team members have two-factor authentication (2FA) configured.
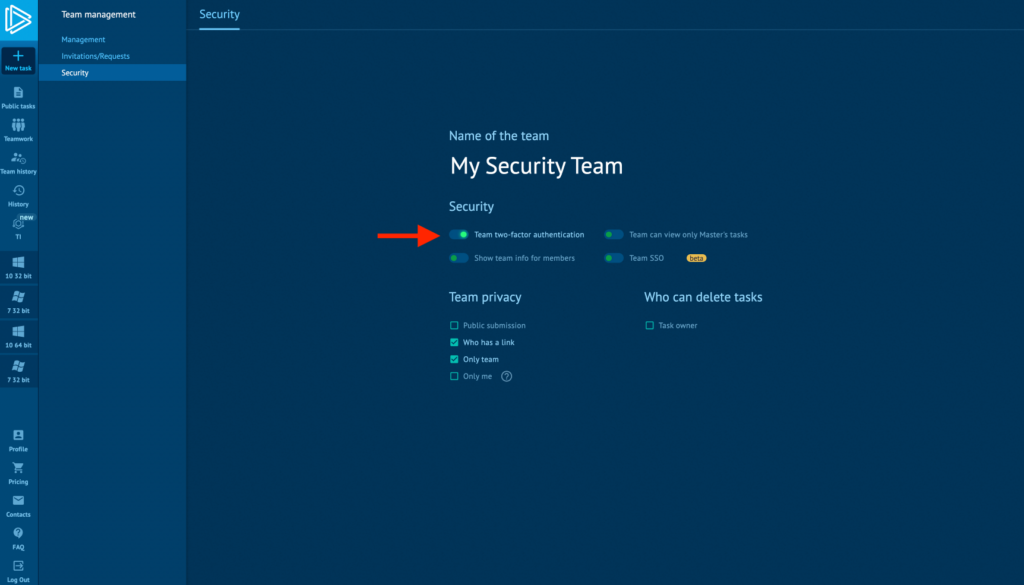
In ANY.RUN, enabling 2FA is just as easy to manage as in your own infrastructure — you can simply make it mandatory across your entire team. Also, you can set up single sign-on (SSO) to allow access to ANY.RUN using your employees’ universal set of credentials.
Change the visibility of tasks after they are created or delete them
We have already mentioned that sometimes confidential data is exposed by mistake. But what if you’ve already made that mistake? Perhaps, you’ve created a public task instead of a private one. Or maybe you just changed your mind about the availability of information and want to undo your decision to share it.
In ANY.RUN you can control the visibility of your tasks at any time, and if you don’t want your data to be stored at all — delete it. Here’s how it works.
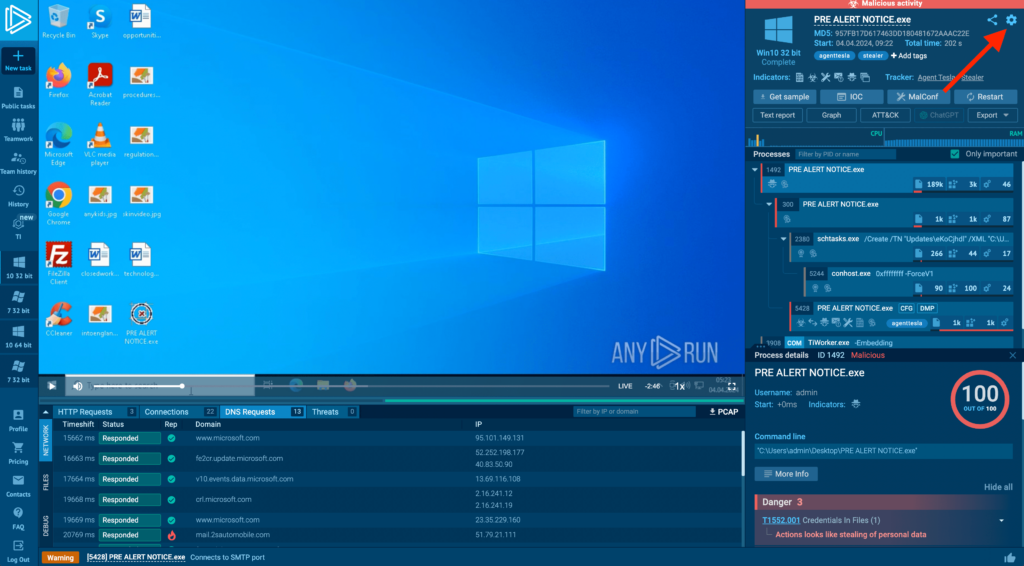
After you’ve selected a task that you want to change the visibility of or delete — you can do this either from the quick access menu in the left sidebar or from your Team History — click on the gear icon in the upper-right corner of the screen. This will bring up a configuration menu:
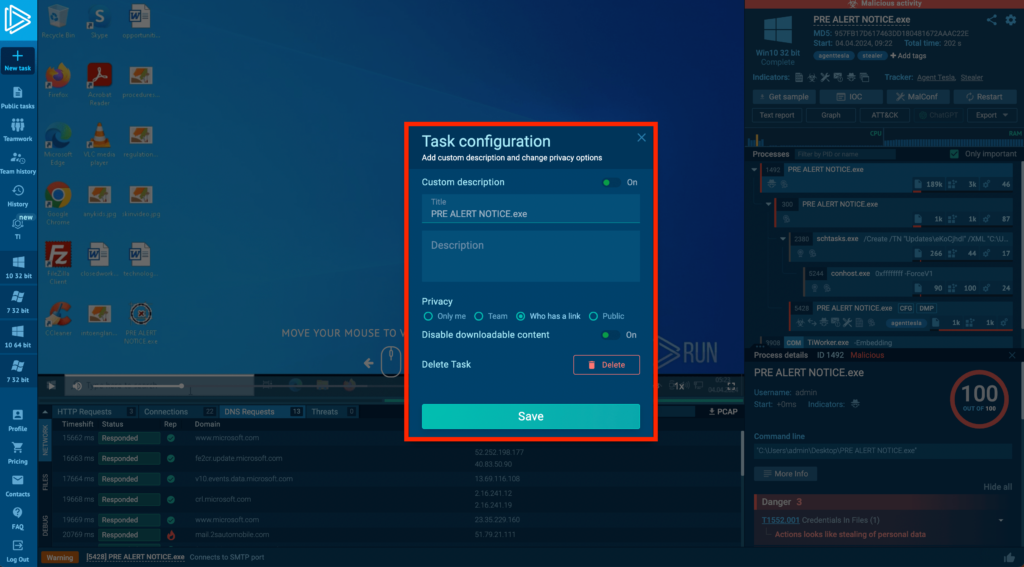
Use this menu to control general task settings. You can:
- Enable and write a custom description to remind yourself later what the task was about, or to explain it to your team.
- Change the task’s privacy setting: who can see the task and how they access it.
- Disable content download, which is a useful security guard rail, but also allows you to upload and analyze proprietary EXE files without worrying about their code being extracted.
- Delete the task, which will inadvertently erase all data associated with it from our database.
This goes without saying, but there’s no way to recover deleted tasks, so make sure you don’t need them in the future before committing.
Wrapping up
We understand that as an enterprise, your analysts need to upload sensitive files, documents, and executables into a sandbox.
That’s why we’refocused on giving you the tools to control who has access to your data and to keep it private at all times, even after a task has been created.
If you’d like to learn more about these features — or the privacy measures we take to protect your data — and how they can help you integrate our sandbox into your security posture, don’t hesitate to schedule a quick call with our sales team.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
We’ll show you in an interactive presentation how ANY.RUN can help your security team.








0 comments