A sophisticated campaign is targeting Chinese-speaking users, distributing a malware known as ValleyRAT.
What’s happening?
There’s a new campaign spreading a multi-stage threat designed to monitor and control infected systems while deploying additional plugins to cause further damage.
Key components of the campaign:
| Component | Details |
|---|---|
| Target | Chinese-speaking users |
| Attack Method | Email messages with URLs pointing to compressed executables |
| Malware | ValleyRAT |
| Affected systems | Windows |
ValleyRAT employs a range of techniques to evade detection, including the use of shellcode to execute its components directly in memory, minimizing its footprint on the victim’s system. The campaign initially came to light in June 2024, with the latest iteration featuring enhanced capabilities for persistence and privilege escalation.
Breaking down the attack chain
The attack begins with a first-stage loader disguised as legitimate applications like Microsoft Office, using filenames such as “工商年报大师.exe” or “补单对接更新记录txt.exe” to appear non-threatening. When launched, the executable drops a decoy document and loads shellcode that advances the attack to the next stage.
This shellcode initiates communication with a command-and-control (C2) server, downloading two critical components: RuntimeBroker and RemoteShellcode. These components are responsible for setting persistence on the host, gaining administrator privileges through exploitation techniques, and further escalating privileges by abusing legitimate binaries like fodhelper.exe and the CMSTPLUA COM interface.
RuntimeBroker’s primary task is to retrieve another loader from the C2 server, which repeats the initial infection process while performing additional checks to determine if it is running in a sandbox. It also scans the Windows Registry for keys related to apps like Tencent WeChat and Alibaba DingTalk, reinforcing the notion that ValleyRAT is specifically targeting Chinese systems.
RemoteShellcode is configured to fetch the ValleyRAT downloader, which uses network protocols like UDP or TCP to connect to the C2 server and receive the final payload. ValleyRAT, attributed to the Silver Fox threat group, is a fully-featured backdoor capable of remotely controlling compromised systems, taking screenshots, executing files, and loading additional plugins.
Remote Shellcode, on the other hand, is responsible for fetching the ValleyRAT downloader, which then uses network protocols to connect to the server and receive the final payload.
Analyzing ValleyRAT in ANY.RUN
ValleyRAT can be analyzed in ANY.RUN sandbox, a powerful tool that provides detailed insights into the malware’s behavior.
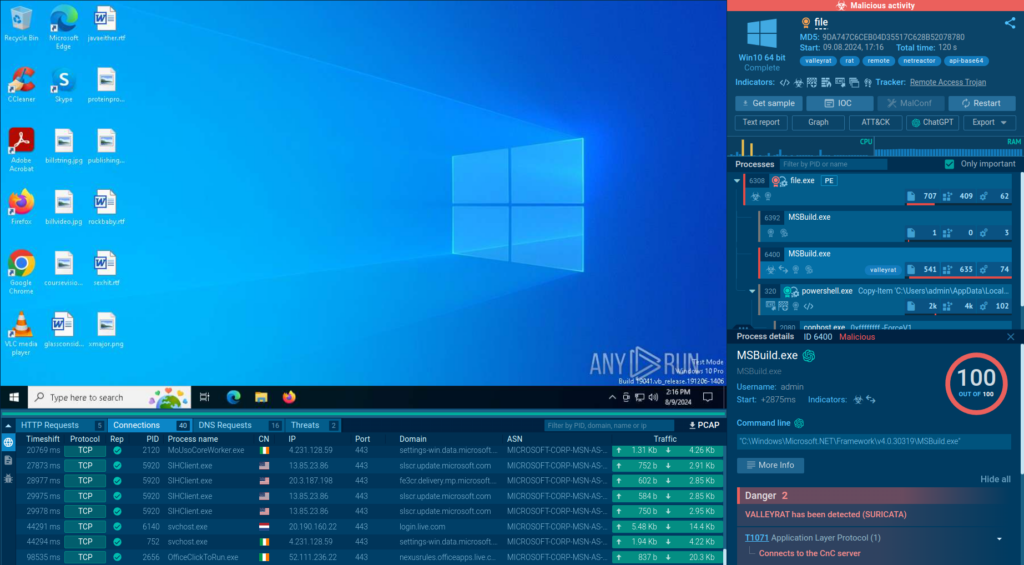
The sandbox analysis shows that the MSBuild.exe executed with a command line pointing to the file.exe located in the Temp directory.
Legitimate programs often use MSBuild.exe, a Microsoft build engine, to compile and build projects, especially those developed using .NET Framework.
In a malicious context, the use of MSBuild.exe indicates an attempt to hide malicious activities within a seemingly legitimate process.
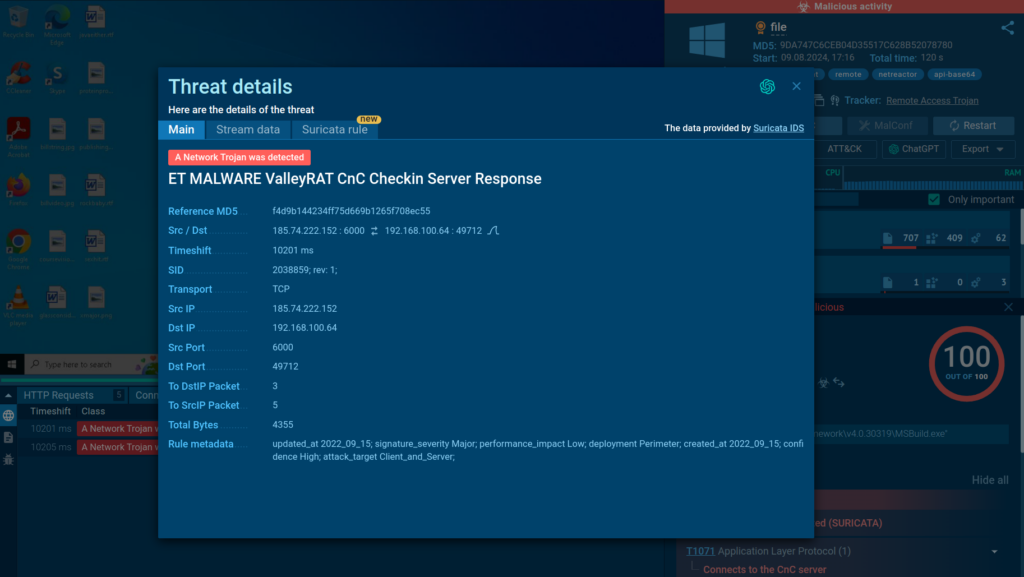
The sandbox also provides information on ValleyRAT’s command-and-control (C2) server communication detected by a Suricata IDS rule.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide.
Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.










0 comments