ANY.RUN‘s latest malware trends analysis for Q4 2023 is here, offering a quarterly update on the most prevalent malware families, types, and TTPs.
Summary
In the fourth quarter of 2023 ANY.RUN users created a total of 748,298 submissions. Within these, 170,202 tasks, or 22.7%, were identified as malicious, and 6.4% (48,180 tasks) — as suspicious.
Comparing this to last quarter’s numbers, the proportion malicious tasks stayed about the same (23.4% to 22.7%). The share of suspicious tasks, on the other hand, almost doubled from 4.5% to 6.4%.
When it comes to Indicators of Compromises, our users collected a grand total of 210,469,912 IOCs this quarter.

In our report, we’re going to:
- Check out the most common malware types and families in Q4 2023, based on data from ANY.RUN
- Dive into the top MITRE ATT&CK TTPs used in this quarter
Let’s сheck it out.
Top Malware Types in Q4 2023
Here’ is a closer look at the most frequent malware types identified by ANY.RUN’s sandbox. At ANY.RUN, we’re processing a lot of submissions — about 14k a day — which gives us a unique vantage point over the threats that are most likely to impact your organization.
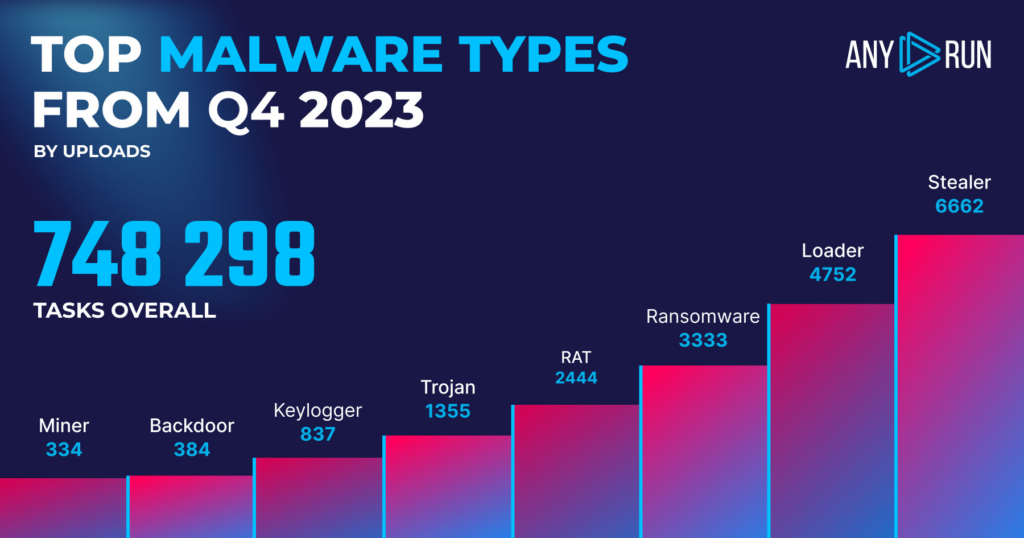
- Stealer: 6662
- Loader: 4752
- Ransomware: 3333
- Rat: 2444
- Trojan: 1355
- Keylogger: 837
- Backdoor: 384
- Miner: 334
Top malware types: highlights
In Q4 2023, stealers became the most popular category, overtaking loaders.In Q3, mind you, loaders were at the top spot, then stealers.
Breaking down the numbers, stealers hit 6,662 instances in Q4, which is up from 5,423 submissions in Q3. This represents a 22.8% jump. Consequently, loaders are now at 4,752 instances in Q4. This is a decrease from 6,203 in Q3, marking a 23.4% drop. It seems loaders are losing some ground in comparison to other malware types.
Ransomware is now in third place with 3,333 instances, a slight increase from 3,283 in Q3. RATs, on the other hand, are down to 2,444 instances from 3,963 in Q3. This is a 38.3% decline. Trojans have dropped by a lot, to 1,355 instances from 2,426 in Q3, a 44.1% decrease. This is the biggest percentage change in all categories.
Looking at other malware types, there’s a mix of changes. Keylogger usage is up, going to 837 from 752. Backdoors, however, decreased to 384 from 545. Miners also showed some growth, increasing to 334 from 231.
Top Malware Families in Q4 2023
Now that we’ve taken a look at top malware categories, let’s see which families were the most widely used.
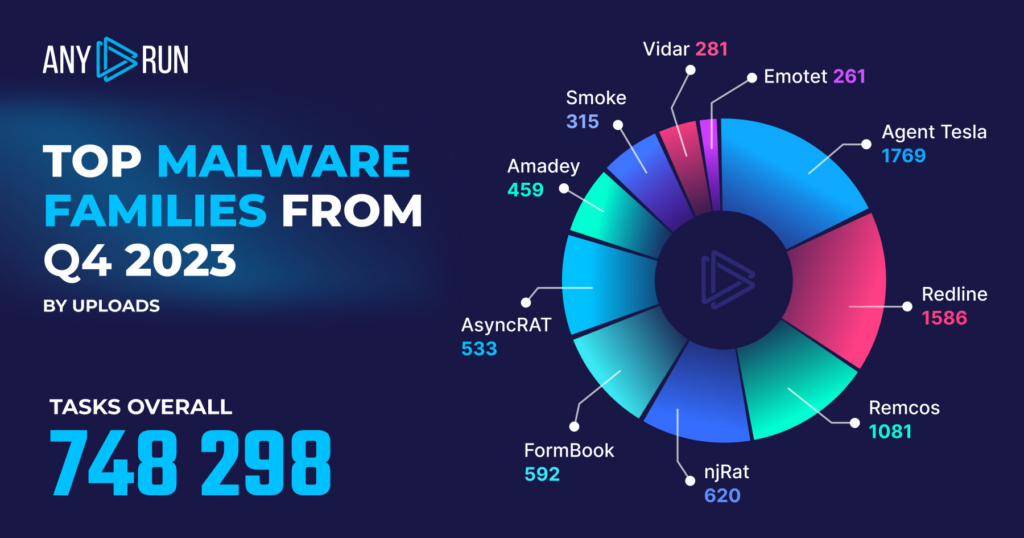
- Agent Tesla: 1769
- Redline : 1586
- Remcos: 1081
- NjRAT: 620
- Formbook: 592
- AsyncRAT: 533
- Amadey: 459
- Smoke: 315
- Vidar: 281
- Emotet: 261
Top malware families: highlights
In Q4 2023, Agent Tesla took the lead again, replacing RedLine as the most prevalent malware, and Remcos made a huge comeback.
- Agent Tesla jumped to the top spot with 1769 instances, which is a 16.1% increase from 1524 in Q3.
- RedLine, previously the most dominant, slipped to second place with 1586 instances, a drop of 31.4% from 2312 in Q3.
- Remcos climbed to the third position with 1081 instances, an increase of 40.0% from 772 in Q3.
Top MITRE ATT&CK techniques in Q4 2023
MITRE ATT&CK is a well-known framework worldwide, breaking down different enemy behaviors into tactics and techniques. It’s a crucial tool for malware analysts to spot, evaluate, and tackle threats more efficiently.
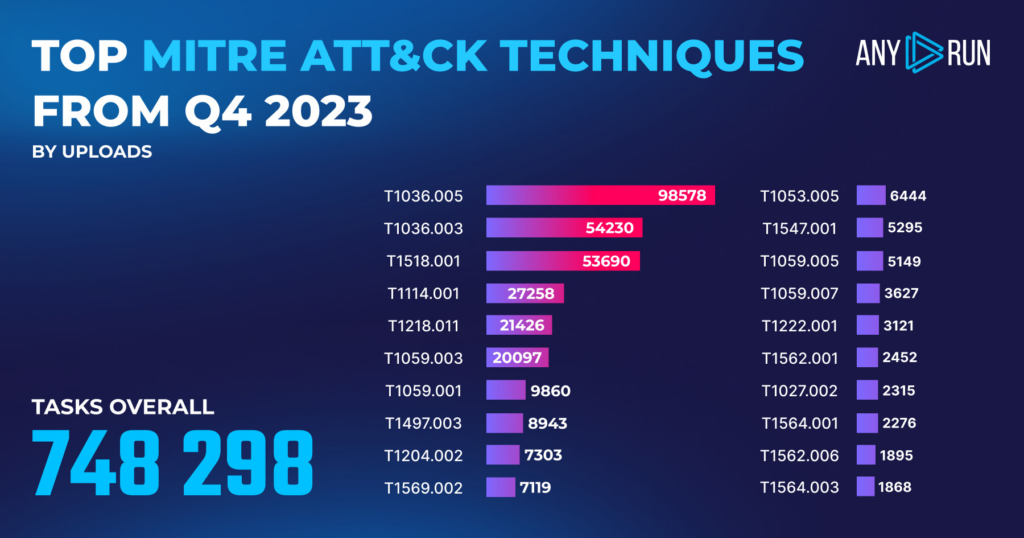
In ANY.RUN, we automatically match malware behaviors to specific techniques. This quarter, our service made 248,820 matches overall, which lets us put together this list:
| MITRE ATT&CK Technique | Count |
|---|---|
| T1036.005 Masquerading: Match Legitimate Name or Location | 98,578 |
| T1036.003 Masquerading: Rename System Utilities | 54,230 |
| T1518.001 Software Discovery: Security Software Discovery | 53,690 |
| T1114.001 Email Collection: Local Email Collection | 27,258 |
| T1218.011 Signed Binary Proxy Execution: Rundll32 | 21,426 |
| T1059.003 Command and Scripting Interpreter: Windows Command Shell | 20,097 |
| T1059.001 Command and Scripting Interpreter: PowerShell | 9,860 |
| T1497.003 Virtualization/Sandbox Evasion: Time Based Evasion | 8,943 |
| T1204.002 User Execution: Malicious File | 7,303 |
| T1569.002 System Services: Service Execution | 7,119 |
| T1053.005 Scheduled Task/Job: Scheduled Task | 6,444 |
| T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | 5,295 |
| T1059.005 Command and Scripting Interpreter: Visual Basic | 5,149 |
| T1059.007 Command and Scripting Interpreter: JavaScript/JScript | 3,627 |
| T1222.001 File and Directory Permissions Modification: Windows File and Directory Permissions Modification | 3,121 |
| T1562.001 Impair Defenses: Disable or Modify Tools | 2,452 |
| T1027.002 Obfuscated Files or Information: Software Packing | 2,315 |
| T1564.001 Hide Artifacts: Hidden Files and Directories | 2,276 |
| T1562.006 Impair Defenses: Indicator Blocking | 1,895 |
| T1564.003 Hide Artifacts: Hidden Window | 1,868 |
Top TTPs: highlights
- T1036.005, Masquerading: Match Legitimate Name or Location had a big drop in numbers, going from 151,442 to 98,578 cases between Q3 and Q4.
- T1036.003, Masquerading: Rename System Utilities, popped into the top 3 TTPs in Q4 with 54,230 cases.
- T1518.001, Software Discovery: Security Software Discovery also saw a big decrease, cutting down from 108,077 to 53,690 instances.
- And T1059.001, ‘Command and Scripting Interpreter: PowerShell’, went up, from 7,715 to 9,860 instances, indicating that PowerShell is becoming a more popular tool for malicious activities.
Report methodology
For our report, we looked at data from 748,298 tasks that were sent to our public threat database. This information comes from researchers in our community who contributed by running public tasks in ANY.RUN.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments