Welcome to ANY.RUN’s quarterly malware trends report!
At ANY.RUN, we process hundreds of thousands of tasks each month. While we’ve traditionally shared yearly statistics, we’ve decided to introduce a new format: quarterly malware trends.
This allows us to offer timely insights into the latest threats and developments within the cybersecurity space.
Summary

In this quarter’s analysis, we processed a total of 775,613 tasks in ANY.RUN. Our sandbox identified 257,006 tasks (33.1%) as malicious and 38,884 tasks (5%) as suspicious. We also collected 282,172,811 Indicators of Compromise (IOCs)
Top Malware Types in Q1 2023
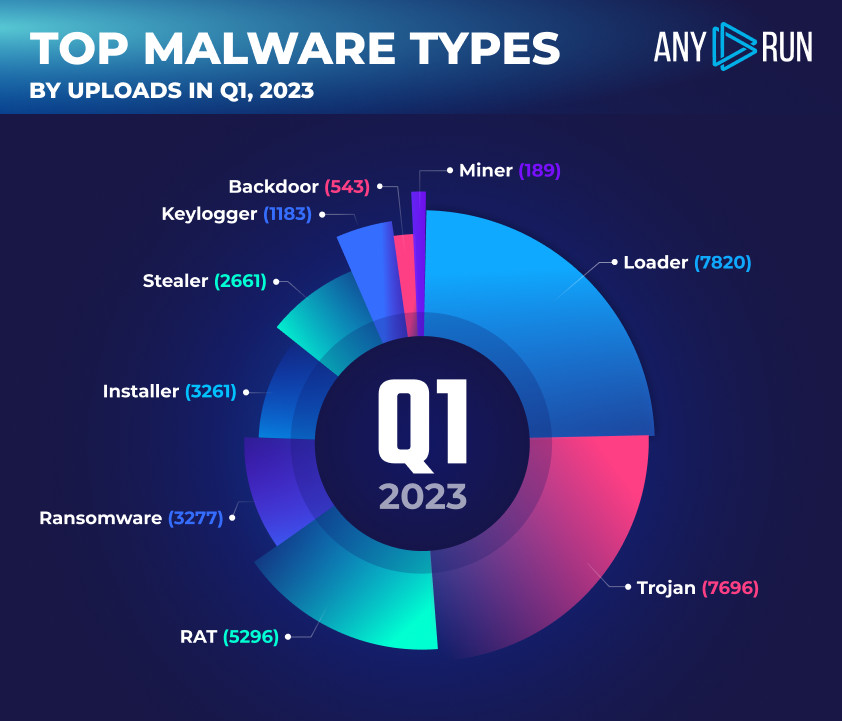
Highlights:
- Loaders top the list of most popular malware types: With 7,820 uploads loaders secured the first position in Q1 2023. emphasizing the widespread popularity of this attack vector.
- Trojans are the second most popular malware type. We recorded 7696 trojan submissions, in Q1 2023. Their versatility and ability to deliver various payloads make Trojans a persistent challenge for researchers and analysts.
- RATs occupy the third spot. Remote Access Trojans (RATs), were recorded in 5,296 uploads in Q1 2023. This underscores the importance of securing remote access channels and closely monitoring network activity to protect against unauthorized access and data exfiltration.
Top Malware Families in Q1 2023
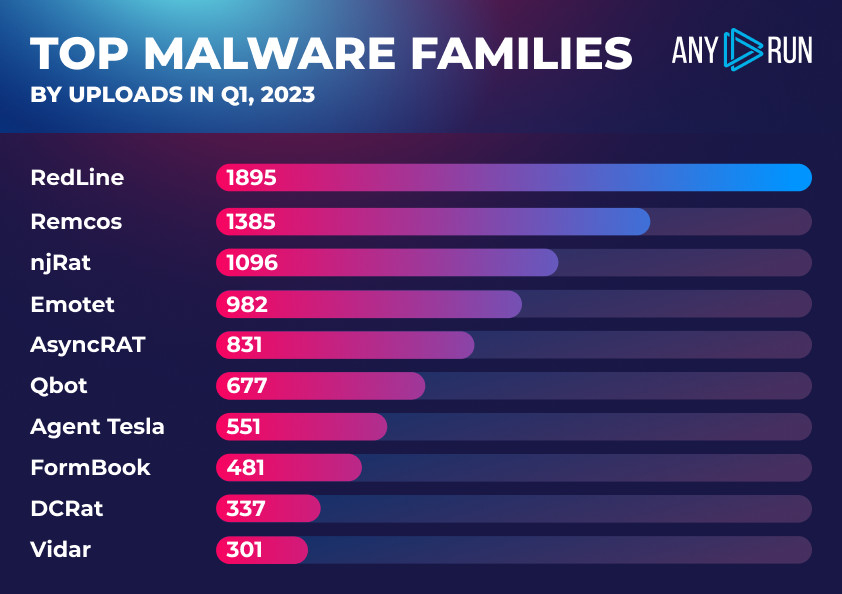
Highlights:
- RedLine remains a top concern: RedLine remains a significant threat — it has been near the top of our charts for two years in a row but has snatched the top spot from other families in Q1 2023 with 1,895 uploads.
- Remcos is in the top two: Remcos — despite being first spotted around 2015 — is still among the top malware families by popularity. It remains a significant threat in Q1 2023, with 1,385 uploads, placing it in the second spot.
- njRAT is a common threat. With 1,096 uploads, njRAT was the third most popular malware family in Q1 2023, closely following the Remcos RAT.
- Emotet declined in popularity: Emotet — which used to firmly lead various malware charts — is now dethroned with only 982 uploads in Q1 2023, placing it in the fourth place. This shows the impact of Emotet gang arrests.
Top MITRE ATT&CK techniques in Q1 2023
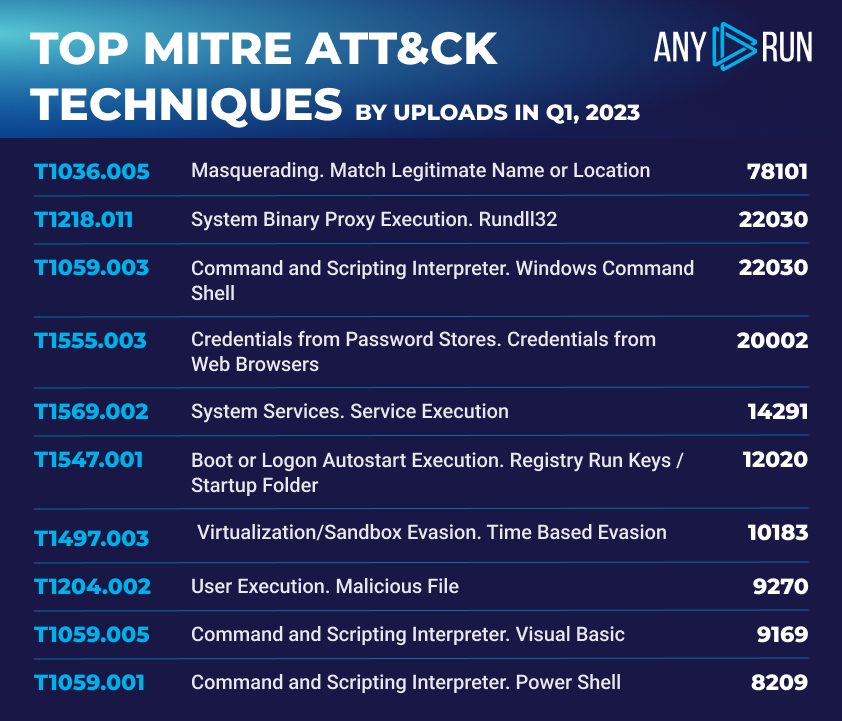
Highlights:
- T1036.005 Masquerading. Match Legitimate Name or Location. A total of 78,101 uploads were found involving this technique, which involves attackers disguising their malicious activities by matching legitimate names or locations. How often do you encounter malicious “svchost” processes on a daily basis?
- T1218.011 System Binary Proxy Execution. Rundll32. With a total of 22,030 uploads, this technique is used by attackers to execute malicious code through the legitimate Windows system binary Rundll32.
- T1059.003 Command and Scripting Interpreter. Windows Command Shell. A total of 20,225 uploads were detected, showcasing the prevalence of this technique used by attackers to execute commands and scripts through the Windows Command Shell. Keep an eye on CMD executions.
- T1555.003 Credentials from Password Stores. Credentials from Web Browsers. This technique, which targets web browser-stored credentials, accounted for 20,002 uploads. A substantial portion of malware consists of stealers, so it’s not surprising that this technique has risen to prominence.
- T1569.002 System Services. Service Execution. With a total of 14,291 uploads, this technique demonstrates the widespread use of service execution by attackers to perform malicious activities on compromised systems.
Key takeaways
After Microsoft restricted the use of macros in Microsoft Office, the focus of attackers shifted from malicious documents to other tactics and techniques (TTPs). In addition to the increasingly popular delivery method of using IMG (iso) files, OneNote files are currently very relevant.
OneNote allows embedding scripts directly into files, almost via drag-and-drop, and with some modifications the malicious document is ready for infection. You can find this type of file in ANY.RUN’s public submissions by filtering for Microsoft Office extensions.
- Trojans remain a significant threat due to their versatility and ability to deliver various payloads. Every year, trojans are becoming increasingly complex, making them harder to detect. ANY.RUN allows you to thoroughly examine a sample from all angles and test its functionality on various versions of the Windows operating system.
- Security specialists should be on the lookout for Redline as the most widespread malware family. The risk of an attack evolving Redline is growing — researchers should be prepared to deal with current threats. Our service will extract the configuration for you, and all you’ll need to do is copy this information and add it to your EDR\IDS.
- The top MITRE ATT&CK techniques used by attackers indicate a focus on obtaining unsecured credentials, subverting trust controls, and manipulating system processes. To better protect against these tactics, organizations and individuals should prioritize securing credentials, monitoring network activity, and maintaining up-to-date security measures.
Report methodology
We’ve examined data submitted to our public threat database by a diverse community of over 300,000 researchers, who have opted to make their analyses public, totaling 775,613 tasks.
While this report should not be regarded as an exhaustive representation of the global malware threat landscape, we believe it can provide valuable insights into the most prevalent threats, as observed through the perspective of our sandbox.
Did we overlook something significant? What information would you like to see in our next report? Share your thoughts in the comments below, and we’ll be sure to consider including it.
2 comments








RSAC attention-seeking behavior
Awesome work!