Sneaking an .exe file into a system without the anti-virus being aware of it is like trying to get a server rack past a security guard — it’s just that big and conspicuous.
To get around this problem, attackers use packers — utilities that compress files and, in case of run-time packers, also obfuscate the code. The goal is to make the source code impossible to detect and analyze. It’s like taking that same rack, putting it in a hydraulic press, and squeezing it down to a size that will fit in the pocket of your coat.
In this article, we’ll look at how attackers use basic packers, what to watch out for in a cloud sandbox, and how to use the information you can get during dynamic analysis for static research.
What is a packer?
In general, a packer is a program that compresses a file using an algorithm. For example, ZIP, RAR. Some packers, such as UPX, are specifically designed to compress an executable, obfuscating the code in the process. In the context of malware, this can be used as an evasion method.
There are many types of packers. Both legitimate utilities (VMprotect, ASpack, Enigma Protector), and custom code written by hackers. But these are either less popular in attacks, so we’ll leave them out, or too complex for the scope of this article.
ZIP, SFX and UPX: how and why hackers use them
This trio is the most commonly used for malicious purposes. The table below explains what they do, from simpler to more advanced:
| Type: | Used to: | Used by: |
|---|---|---|
| ZIP | Compress a file or files into an archive. | Various phishing campaigns |
| SFX | Bundle a compressed payload and executable module into a single archive. | Malware (E.g. Lu0bot) , Various phishing campaigns |
| UPX | Obfuscate the code by compressing and encrypting an executable. Can be corrupted to prevent unpacking. | AgentTesla, Gh0stRAT, RedLine, PlanetStealer malware |
Note: ZIP, SFX and UPX are packers in a general sense, but they can be divided into two groups.
- Group 1 – ZIP and SFX. These are archivers. They compress the payload into an archive. In the context of malware, this archive can then be attached to an email and sent to a victim. The difference is that the SFX archive contains both the file and an installer which can extract the content and initiate the installation process.
- Group 2 – UPX. A full packer. Compresses executables directly and encrypts and obfuscates their code. Then the file compressed by UPX can be packed into an archive with the tool from group 1 and sent to the destination.
Let’s take a look at each of these utilities in more detail, and explain how and why they may be used maliciously:
ZIP
Unlike true packers, ZIP doesn’t encrypt the code. Archivers are used to distribute malware by hiding it within legitimate files or password-protecting archives attached to emails. This tactic allows the malicious code to bypass email security measures that would otherwise block executable attachments.
- Compresses and extracts files or directories.
- Needs an outside utility to extract files.
- Lacks instructions, users need to manually click on content to engage it.
SFX
An SFX (self-extracting archive) contains a compressed program and an unpacking module, often an installer, that extracts the contents and initiates the installation. This means that it can decompress its contents without the need for an external decompression utility. What does that mean in practice? If you click on a ZIP archive, the contents will be extracted into a folder. When you click on SFX, the content installation process begins. In the context of malware, this could be a fake-installer or a hidden installation.
- Often bundles compressed malware and an extractor.
- Initiates malware installation process upon interaction.
- Does the above without a separate decompression utility.
UPX
UPX (Ultimate Packer for eXecutables) is an open-source packer distributed under the GNU GPL license. It’s been around since 1998. UPX is a different beast from ZIP and SFX. It compresses an executable file and encrypts its contents. When executed, the file is decompressed into memory, where it runs normally.
- Compresses and encrypts the executable.
- Executes compressed code by unpacking it in memory.
- Not just compresses but also obfuscates the code.
UPX files can be modified after packing
There’s a known technique that hackers use with UPX to make analysis more difficult, and you need to be aware of it. Corrupted UPX files can’t be decompressed with standard versions of UPX, meaning you can’t view what’s inside. However, it doesn’t affect its ability to execute potentially malicious code inside, which means the payload remains armed.
How do hackers “break” the archive Then either:
- Pack the archive with an unreleased version of UPX.
- Or modify l_info and p_info structures in an archive.
These two actions have the same effect. Namely, the archive will not be openable by the standard version of UPX, which can hinder both you as a researcher if you want to unpack the contents and view them in a file browser, and a security system that won’t be able to reliably apply signature-based detection to an encrypted UPX file.
What’s the solution?
One way around this is to restore the archive. Here’s a tool you can use to do this:
Use this UPX recovery tool to fix corrupted UPX files.
Analyzing malicious archives: real-world examples
Now let’s look at some specific techniques that will allow you to identify the type of archive you’re dealing with. For .ZIP archives, this is self-explanatory — just look at the file extension, right-click and use the context menu to decompress.
SFX and UPX are a bit more complicated and interesting, as you’ll need to look at the file headers to determine the type of archive. Here are a couple of tools you can use to do this.
- “file” command on Unix: In the terminal, type “file” followed by a path to the archive to identify the file type.
- TrID: This utility, available for both Windows and Linux, provides detailed file information. To use it, first install it and then run it from the terminal with the command trid followed by the path to the file.
- Hex editors: Editors such as xxd and hexdump allow you to manually inspect the hex magic bytes of a file.
- ANY.RUN: This is our interactive malware analysis sandbox, which has a Static Discovering module with built-in TrID and hex editor — it automatically extracts all necessary information from the header.
Actually, despite all this preamble, ANY.RUN makes it very easy to identify both an SFX and a UPX file. Below we take a look at a real-world case of each.
Case 1. Identifying an SFX archive in ANY.RUN
In this recording of an interactive research session in the ANY.RUN sandbox, we have a Lu0bot stealer packed with SFX.
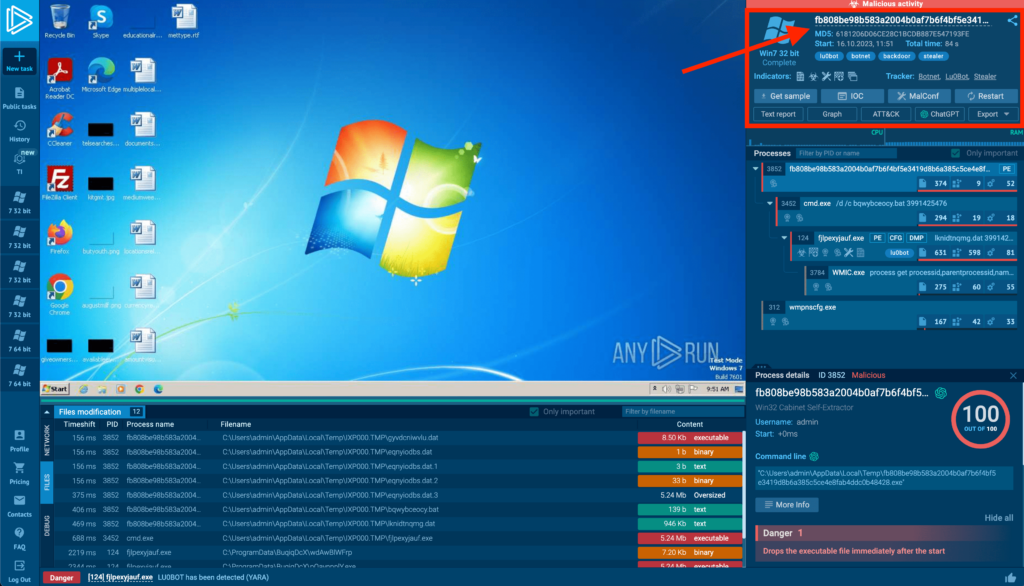
The sandbox has already flagged this file as malicious, as indicated by the red banner and threat tags in the top right corner. However, if we want to analyze the sample further and determine the packing method used, we need to examine the file headers.
To do this, we can open the Static Discovering window by clicking on the file itself.
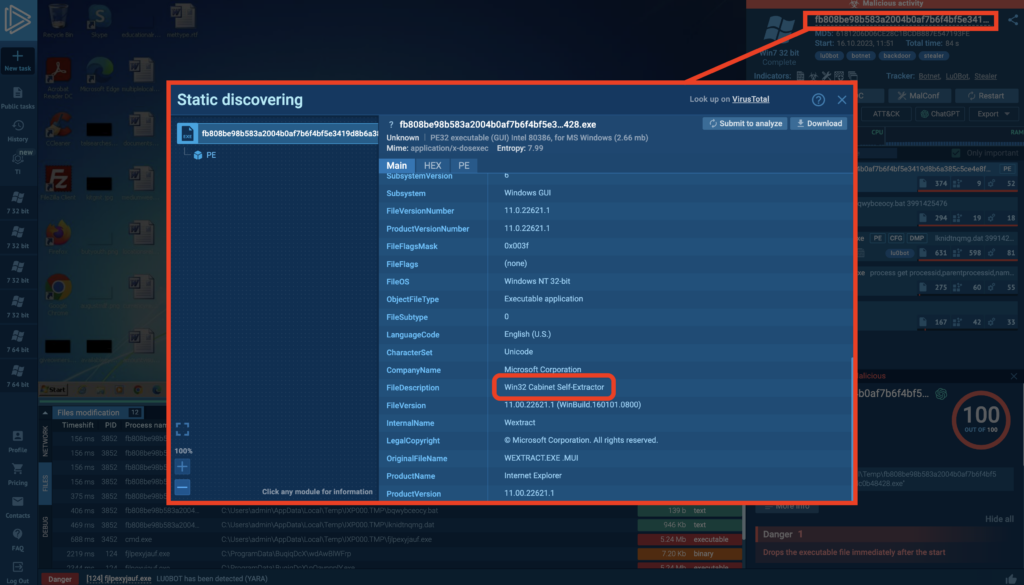
The file description “Win32 Cabinet Self-Extractor” suggests the file uses SPX compression. If we download and decompress this self-extracting archive, then explore its contents in a file browser, we’ll find a collection of files inside.
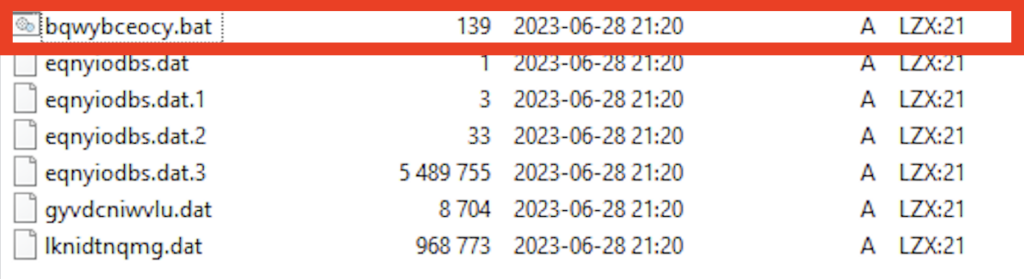
The file with a .bat extension is the malicious payload that gets executed by the instructions within the self-extracting routine. The other files present are just decoys or dummy files.
Case 2. Identifying a UPX file in ANY.RUN
In this example, we have a stealer packed with UPX.
Follow the initial steps from case one until you open the Static Discovery pop-up window. Then open the Hex Editor tab and scroll down until you find an entry for the compression method.
ANY.RUN automatically converts hex values to plain text, so you’ll be looking for strings like “UPX0”, “UPX1” or “UPX!”
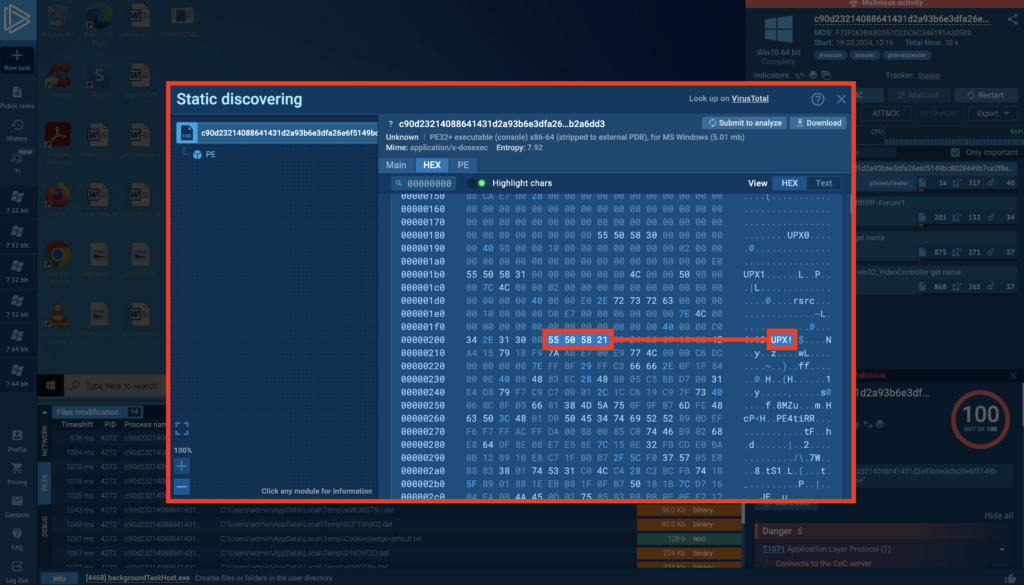
Sure enough, there’s a sequence of bytes at the beginning of the file that indicates the use of a compression method — after a bit of scrolling we see the typical ASCII characters “UPX!”
Wrapping up
In conclusion, basic packers such as ZIP, SFX and UPX are legitimate tools, but hackers use them to compress large payloads and deliver them into the system without alerting security systems. ZIP and SFX simply compress the file and are used to bundle malicious code in an archive with legitimate content. UPX also obfuscates the code.
Here are the key takeaways:
- The three most common packers used maliciously are plain ZIP archives, SFX, and UPX.
- ZIP and SFX archives are often used in phishing campaigns to bundle malicious executables with legitimate content, bypassing the email server’s binary protection.
- UPX is more complex, encrypting the executable and extracting the code into memory upon interaction, where it runs normally.
- In addition, UPX files can be corrupted to prevent decompression while still allowing malicious payloads to run.
When encountering packed malware, you can identify the packer used by examining the file header (or file extension in the case of ZIP files), and then extract the content using the appropriate utility. An easy way to do this is through ANY.RUN’s Static Discovery module, which comes pre-configured with TrID and includes a built-in hex editor.
About ANY.RUN
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware.
Every day, a community of 400,000 analysts and 3000 corporate clients use our cloud-based platform to analyze Windows and Linux threats.
Key advantages of ANY.RUN for businesses:
- Interactive analysis: Analysts can “play with the sample” in a VM to learn more about its behavior.
- Fast and easy configuration. Launch VMs with different configurations in a matter of seconds.
- Fast detection: Detects malware within roughly 40 seconds of uploading a file.
- Cloud-based solution eliminates setup and maintenance costs.
- Intuitive interface: Enables even junior SOC analysts to conduct malware analysis.
Learn how ANY.RUN can benefit you or your security team. Schedule a free demo with one of our sales representatives, and we’ll walk you through real-world examples.









0 comments