TI Lookup from ANY.RUN is a versatile tool for gathering up-to-date intelligence on the latest cyber threats. The best way to demonstrate its effectiveness is to hear from actual security professionals about how they use the service in their daily work.
This time, we asked Jane_0sint, an accomplished network traffic analyst and the first ANY.RUN ambassador, for her real-world cases of using TI Lookup. Lucky for us, she agreed to share her insights and sent us a few examples, which include finding intel on phishing kits like Mamba2FA and Tycoon2FA.
About Threat Intelligence Lookup
TI Lookup is a searchable hub for investigating malware and phishing attacks and collecting fresh cyber threat data. Powered by a massive public database of millions of samples analyzed in ANY.RUN’s Interactive Sandbox, it contains various Indicators of Compromise (IOCs), Indicators of Attack (IOAs), and Indicators of Behavior (IOBs), from threats’ network activity to system processes and beyond.
The service provides you with extensive search capabilities, allowing you to create custom requests that feature different data points to home in on specific threats. It offers:
- Quick Results: Searches for events and indicators from the past six months take just 5 seconds on average
- Unique Data: It contains over 40 types of threat data, including malicious IPs, URLs, command line contents, mutexes, and YARA rules
- Large Database: TI Lookup is updated daily with thousands of public samples uploaded to ANY.RUN’s sandbox by a global community of over 500,000 security professionals
Investigating the Mamba2FA Phishing Kit
Mamba2FA is a phishing kit that has seen a significant rise over the past several months. To investigate this threat and gather more context, we can utilize a typical URL pattern commonly found in its campaigns. This pattern follows the structure {domain}/{m,n,o}/?{Base64 string}.
When translating this into an actual query for TI Lookup, we can use the following search string:
Let’s break down this query:
- Asterisk (*): This wildcard character indicates any character string. It helps expand our search to include all domains used in Mamba2FA attacks, ensuring a comprehensive investigation
- Question Mark (?): This is another wildcard character that indicates exactly one character or none at all. In our case, there are two question marks in the query. The first one is the wildcard that serves as a stand-in for the characters “m”, “n”, and “o” that are commonly used in Mamba2FA URLs. The second question mark is a part of the address. To escape it, we use the \ slash symbol
- c3Y9: This is a Base64-encoded parameter found across Mamba2FA attacks. When decoded, it translates to sv=, which specifies the appearance of the phishing page
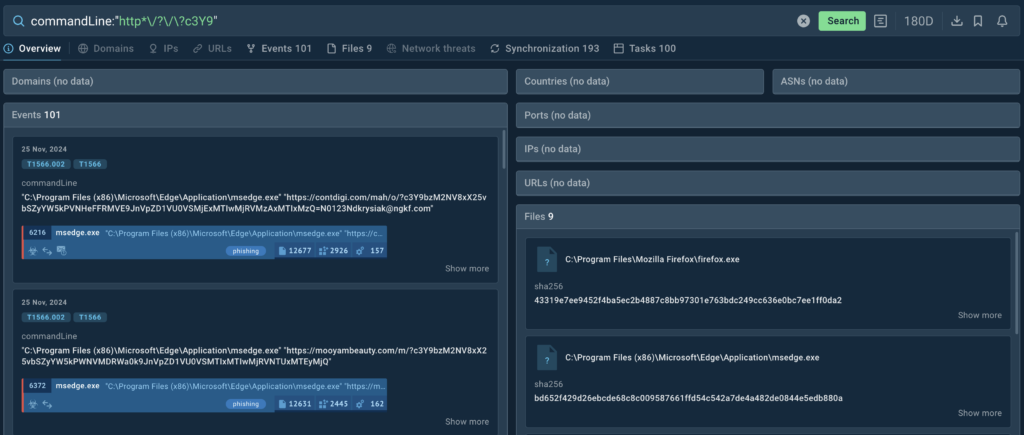
Submitting this search query to TI Lookup allows us to access plenty of results that match our string, from command lines with URLs to sandbox sessions where these command lines were logged.
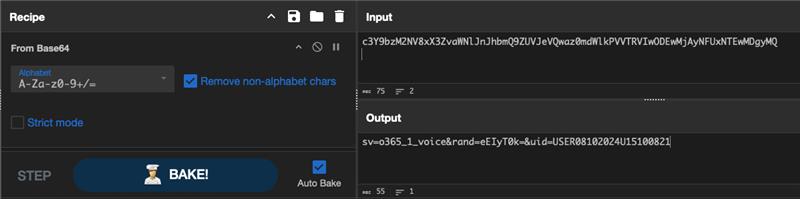
We then can collect the full URLs found and decode the base64-encoded parts to reveal more information on the attack and extract the list of domains from them.
Investigating the Tycoon2FA Phishing Kit
Tycoon2FA is another phishing kit, which is known for faking Microsoft authentication pages to steal victims’ credentials. With the help of TI Lookup, we can collect plenty of intel on its latest samples and wider infrastructure.
A good practice for constructing queries in TI Lookup is to link each condition of the query to specific features of the phishkit:
- If the phishkit hides its pages behind Cloudflare Turnstile, we add a condition for this;
- If there is content encryption, we add a condition for the encryption library;
- If the phishing page stores content on a specific CDN (Content Delivery Network), we add a condition for that as well.
An example of this query construction method for searching Tycoon2FA phishkit attacks can be seen below.
As noted, one of the signature features of this threat is the abuse of Cloudflare’s Turnstile challenges as a barrier for automated security solutions. For the challenge to work, Tycoon2FA loads the library api.js.
During the challenge, Tycoon2FA also loads another library, crypto-js.min.js, which it uses at later stages of the attack to encrypt its communication with the command-and-control center (C2).
The phish kit also accesses elements stored on the legitimate domain ok4static[.]oktacdn[.]com and utilizes them to build phishing pages designed to imitate Microsoft’s login pages.
The two libraries and the domain make solid pieces of intel to pivot on using TI Lookup to find instances of Tycoon2FA attacks.
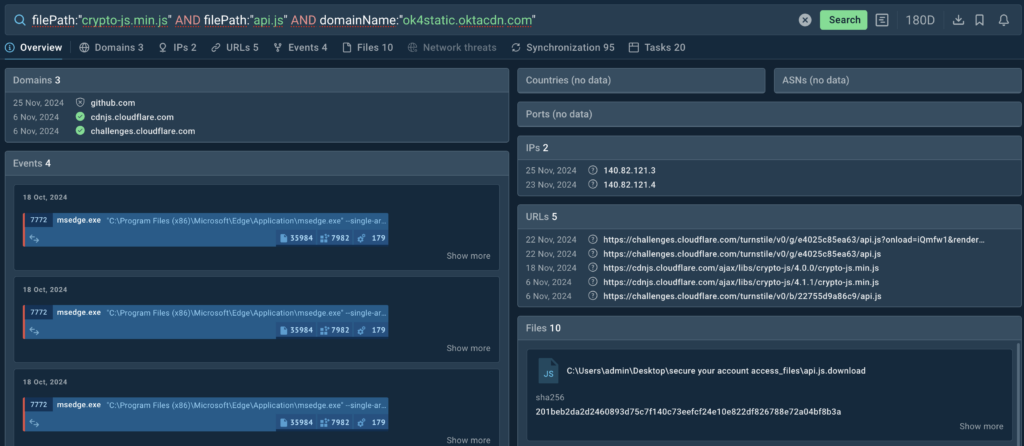
In response to the query, the service provides a list of matching events found in 20 decrypted sandbox sessions over the past 180 days. Search queries created on this principle based on domains bring more results because they work not only on decrypted network sessions but also require a larger number of conditions in the query. We can collect the information and take a closer look at the sessions to observe attacks as they unfolded in real time.
Tracking APT-C-36 Phishing Campaigns
Threat Intelligence Lookup can be helpful in your investigations into campaigns that are attributed to advanced persistent threats (APTs).
Consider the example of Blind Eagle, also known as APT-C-36, which is a group that targets Latin America. You can learn more about their activity in ANY.RUN’s article on the threats discovered in October 2024.
Knowing that APT-C-36 uses phishing emails with attachments that contain malware, such as AsyncRAT and Remcos, and attempts to reach targets in LATAM countries like Colombia, we can put together a TI Lookup query to find more relevant samples related to their attacks:
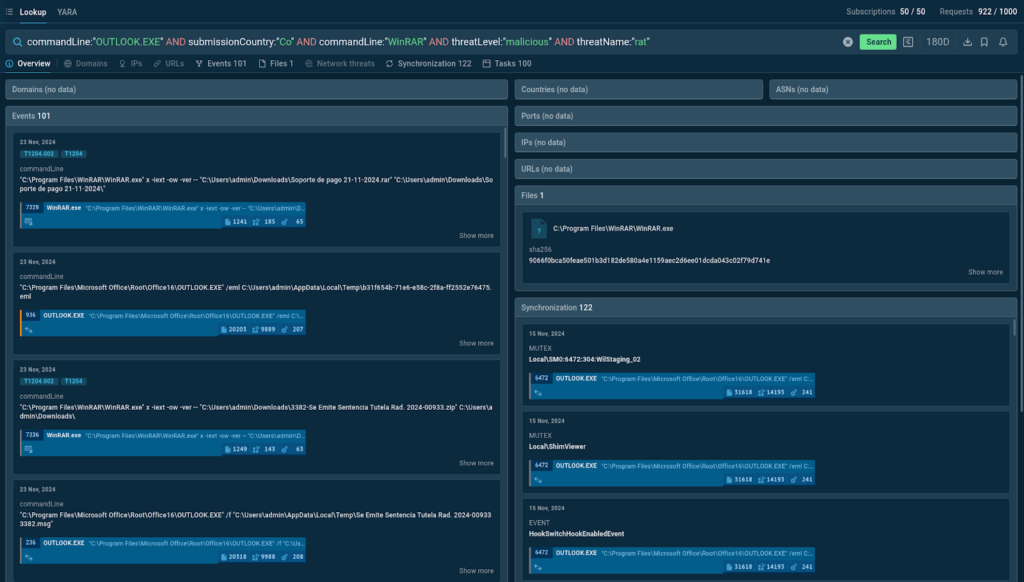
The service provides 100 sandbox sessions that match our request along with events from those sessions.
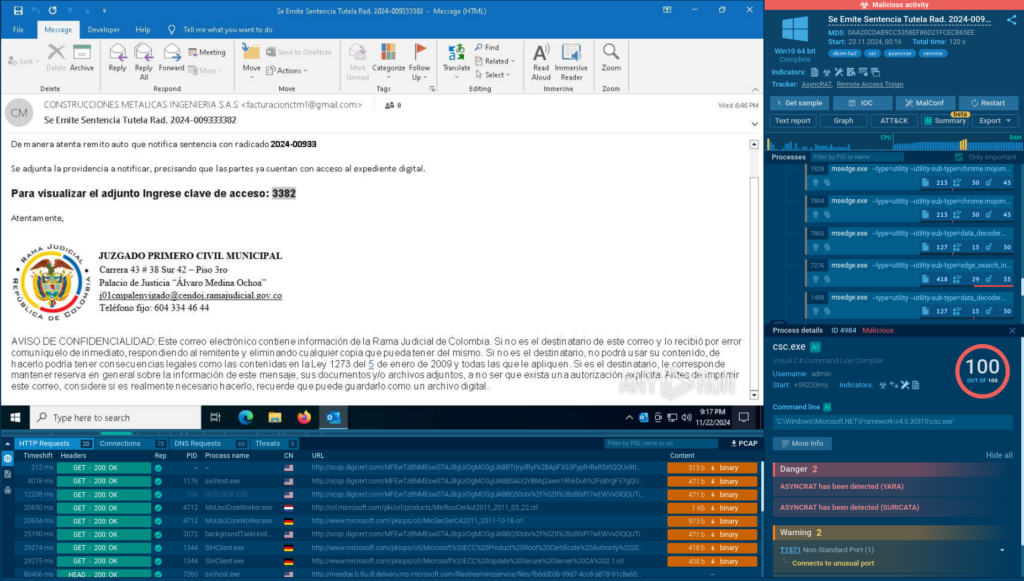
Among them, we can find samples of actual phishing emails belonging to Blind Eagle’s campaigns which were publicly uploaded to ANY.RUN’s sandbox for analysis by users in Colombia.
Identifying Phishing Attacks Abusing Microsoft’s Infrastructure
Another useful way to utilize TI Lookup is to proactively research phishing attacks that use legitimate resources to access content as legitimate account login pages do. For example, attackers often use parts of the Azure Content Delivery Network (CDN), like backgrounds or login forms.
To find these examples with TI Lookup, you can specify the Azure domain. However, it’s important to filter out non-malicious instances. You can do this by excluding Microsoft’s domains from the query using the NOT operator and setting the threat level to “suspicious.” You are free to add exceptions at your discretion if you wish to cleanse your query results of unsolicited submissions.
We can also include parameters with empty values. This signals the system to show all possible results for those parameters.
Adding domainName:”” and suricataMessage:”” will display all domains and Suricata messages found across sandbox sessions that match our query.
In response to our query, TI Lookup provides extensive threat data, including the Suricata rules that were triggered during analysis.
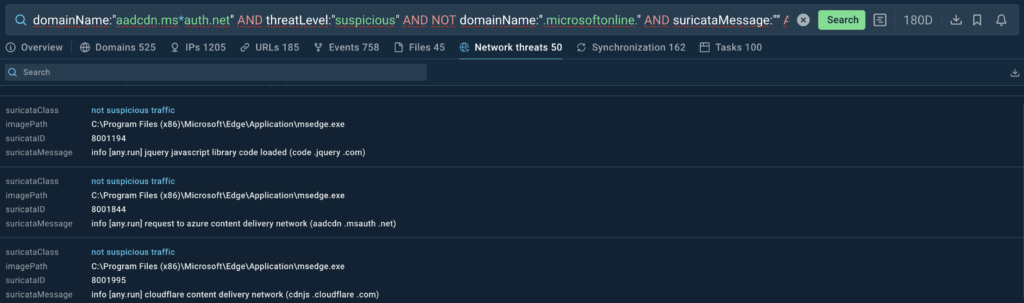
We can also observe all the domains in sessions involving phishing attacks. We can collect them and examine each of them separately to check if they are used as part of attackers’ infrastructure.
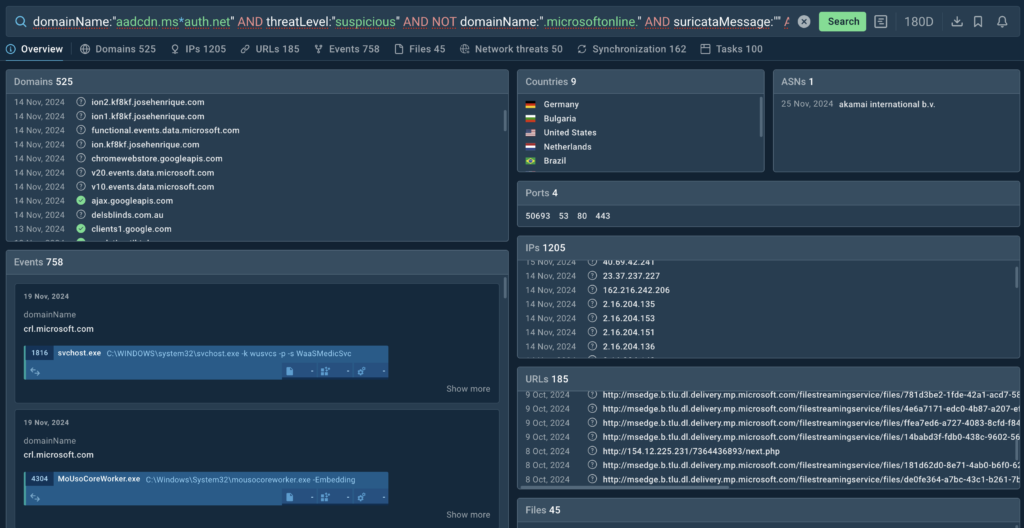
We also get a list of sandbox sessions that feature examples of actual phishing attacks abusing Microsoft’s infrastructure.
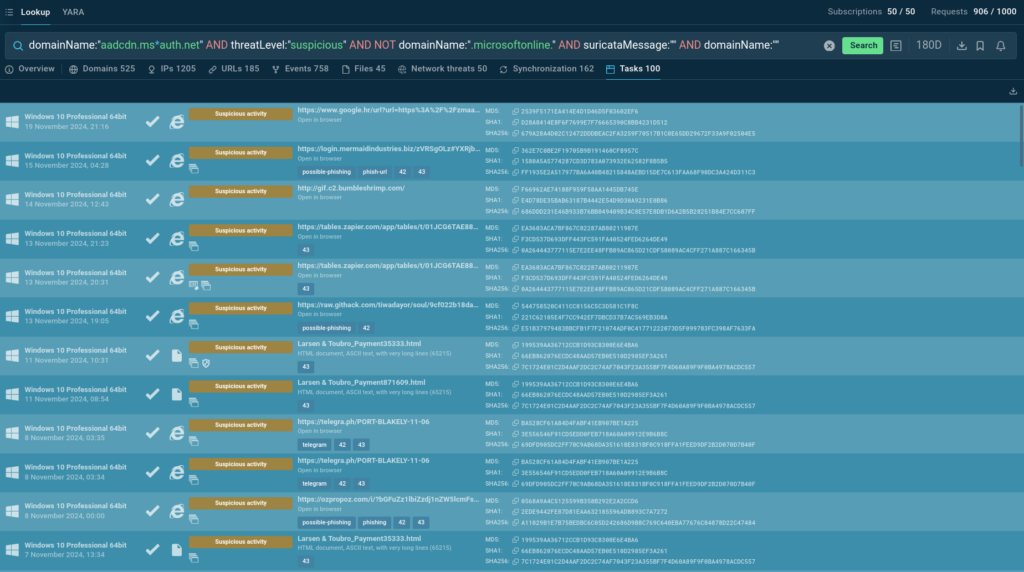
Let’s explore one of them in greater detail.
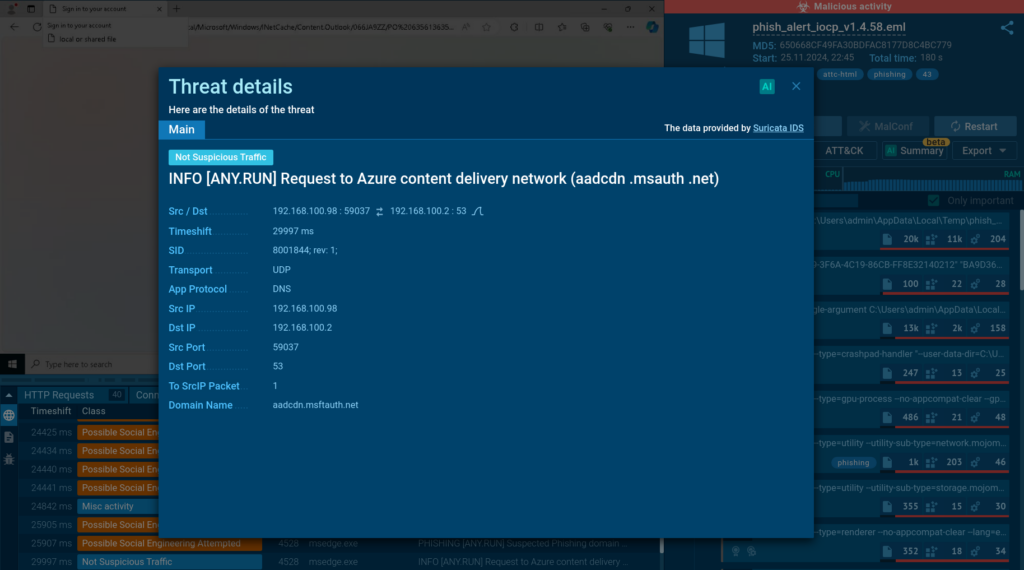
In this session we can see a Suricata rule that indicates a request to Azure’s content delivery network.
You can build upon this search by adding a commandLine parameter. Specifically, we can tell the service to look for command lines that include URLs with the # anchor, which attackers use to add a victim’s email address.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
To find results with URLs containing email addresses, include the @ symbol in your query. Use the * wildcard to account for any characters between the anchor and the @ symbol.
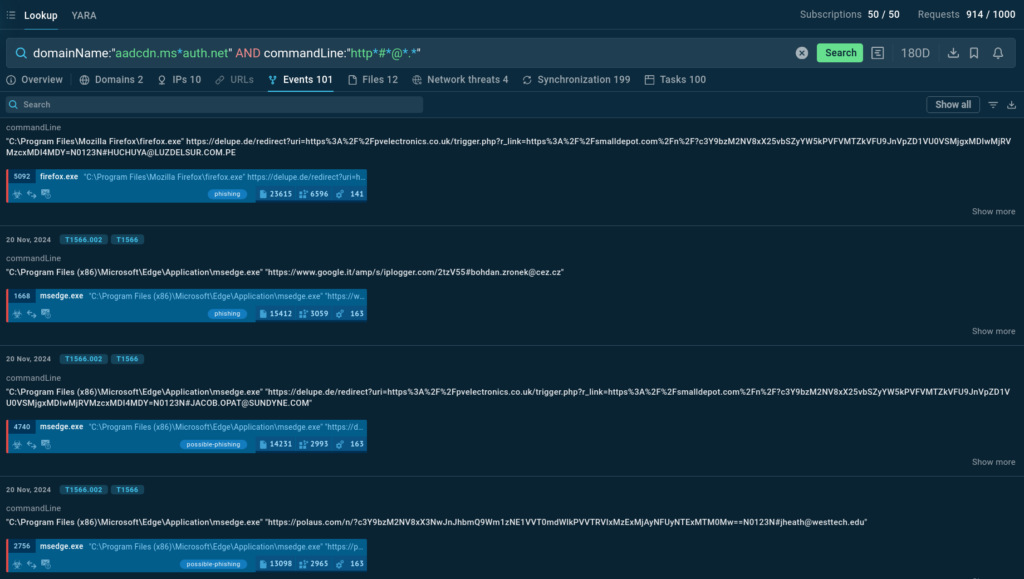
Apart from relevant sandbox sessions, the service returns a list of command lines extracted from these, allowing us to see the URLs used by attackers that include emails of victims.
About ANY.RUN
ANY.RUN’s Threat Intelligence Lookup and YARA Search services allow for precise threat hunting and the extraction of valuable insights into current cyber threat trends. What’s impressive is how fast these scans are—they significantly speed up the analysis process, allowing for quick detection of threats and malware.










0 comments