Researchers warn about a new wave of phishing attacks.
The attacks exploit Cloudflare Workers and HTML smuggling to steal user credentials from Microsoft, Gmail, Yahoo!, and cPanel Webmail.
What’s happening?
Threat actors are using Cloudflare Workers to act as reverse proxy servers for legitimate login pages, intercepting traffic between victims and the login pages. The aim is to capture credentials, cookies, and tokens.
Users in Asia, North America, and Southern Europe are targeted.
Breaking down the attack chain
The phishing campaigns use a unique approach where the malicious payload is a phishing page itself, reconstructed and presented to the user in their web browser.
This phishing page prompts the victim to sign in with their Microsoft Outlook or Microsoft 365 account, claiming that they need to do so to view a supposed PDF document.
If the victim falls for the trick and enters their credentials, they are redirected to fake sign-in pages hosted on Cloudflare Workers. These pages are designed to harvest not only the victim’s login information but also their MFA codes.
The entire phishing page is built using a modified version of an open-source Cloudflare Adversary in the Middle (AitM) toolkit.
When the victim visits the spoofed login page, the attacker collects the web request metadata. They then redirect the victim, who logs in to the legitimate site, and the attacker collects tokens and cookies from the response.
This allows the attacker to track what the victim does after they log in.
What is HTML smuggling?
HTML smuggling, used in this campaign, is a payload delivery mechanism that has gained traction in recent years. Hackers use this technique to “smuggle” malicious code behind firewalls without triggering security alerts.
Here’s how it works:
- The attacker first encodes malicious script within an HTML document.
- When a user opens the page in their web browser, the browser decodes the malicious script.
- The script then assembles the payload on the user’s device.
In practice, this means that the malicious executable doesn’t have to pass through a firewall — instead, the attacker builds the malware locally on the target system.
In this campaign, the attackers use HTML smuggling in a creative way — to build the actual phishing page on the user’s device.
New phishing tactics?
The phishing campaigns, in general, are becoming more sophisticated, researchers warn. Many employ an array of well-known and new phishing tools:
- Phishing-as-a-Service toolkits like Greatness to steal Microsoft 365 login credentials and circumvent MFA.
- DNS tunneling to detect when victims interact with phishing content.
- GenAI to write convincing phishing emails.
- QR codes inside PDF files to redirect victims to fake login pages.
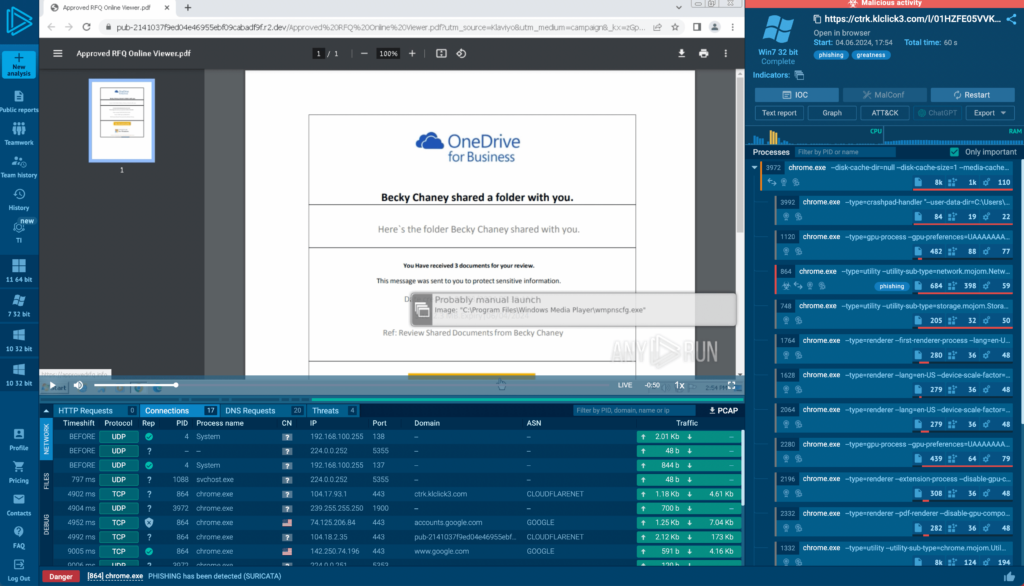
Analyzing phishing campaigns in ANY.RUN
Phishing campaigns have become increasingly sophisticated, and hackers are now integrating legitimate tools into their attacks.
CAPTCHAs
One tactic we’ve seen is to place a real CAPTHCA, such as one from CloudFlare or another provider, in front of malicious content.
This creates a scenario where attackers pit one security system against another — the CAPTCHA prevents automated security products like web crawlers from reaching the malicious content, and detection doesn’t work.
Realistic sign-in forms
In another technique, hackers create copies of web pages that mimic popular services, commonly login portals.
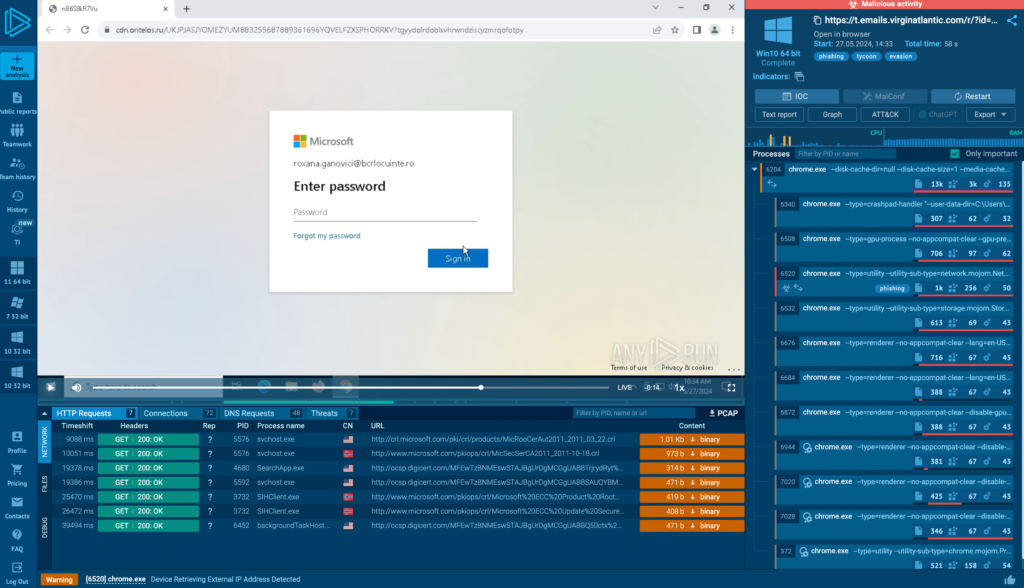
In the example above, they mimic a Microsoft login page. In reality, the form sends the login credentials to the server that is under the control of the attacker.
Attackers often place these fake pages behind CAPTHCHAs, and to capture their malicious behavior, you need to go through the entire login flow, from accessing the resource to filling out the CAPTHCHA and submitting the form data.
ANY.RUN Sandbox can help streamline the analysis of these phishing campaigns. Our users can navigate through captchas in two ways:
- Manually by clicking on them within the task.
- Automatically, by using the automated interactivity (ML) feature.
Automated Interactivity (ML) intelligently mimics human actions during the analysis session, using machine learning to recognize and prioritize buttons based on their importance.
Simply put, it smartly clicks through CAPTHCHAS and login forms for you, so you can sit back and watch the analysis complete itself.
QR-codes
Embedding QR codes in emails or documents that link to malicious resources is another growing trend that replaces sending links directly.
Many email providers have implemented security measures to block malicious links and spam phishing emails containing them, but few can extract links from QR codes. By default, inboxes don’t view QR-codes as malicious and allow them through to the inbox.
In ANY.RUN, you can submit a URL extracted from QR codes for a new analysis.
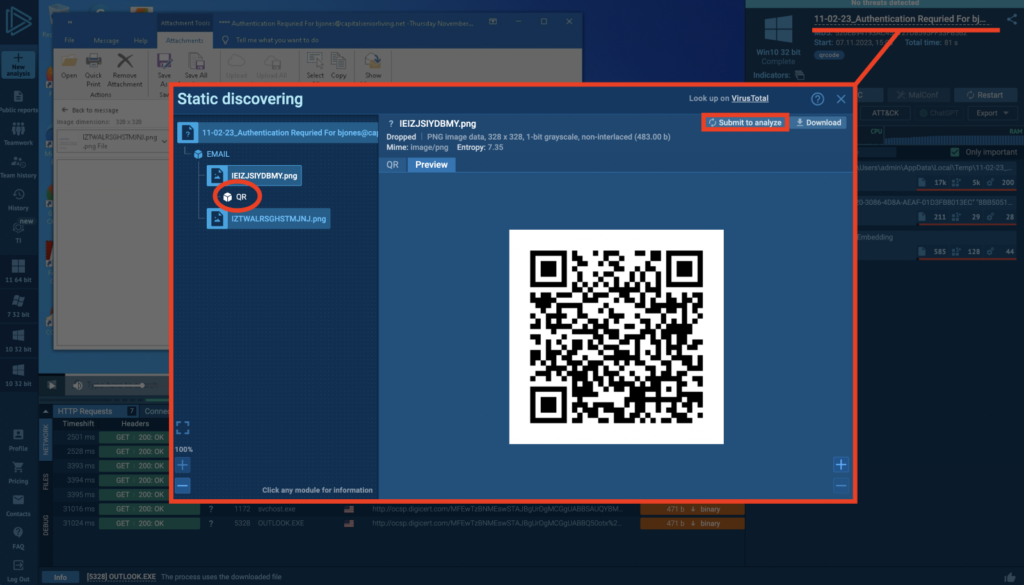
In the example above we have a phishing email.
By clicking on the filename at the top right of the screen, we can open the Static discovering view. Click on the QR and then Submit to analyze“to start a new session, this time focusing on the link within the QR.
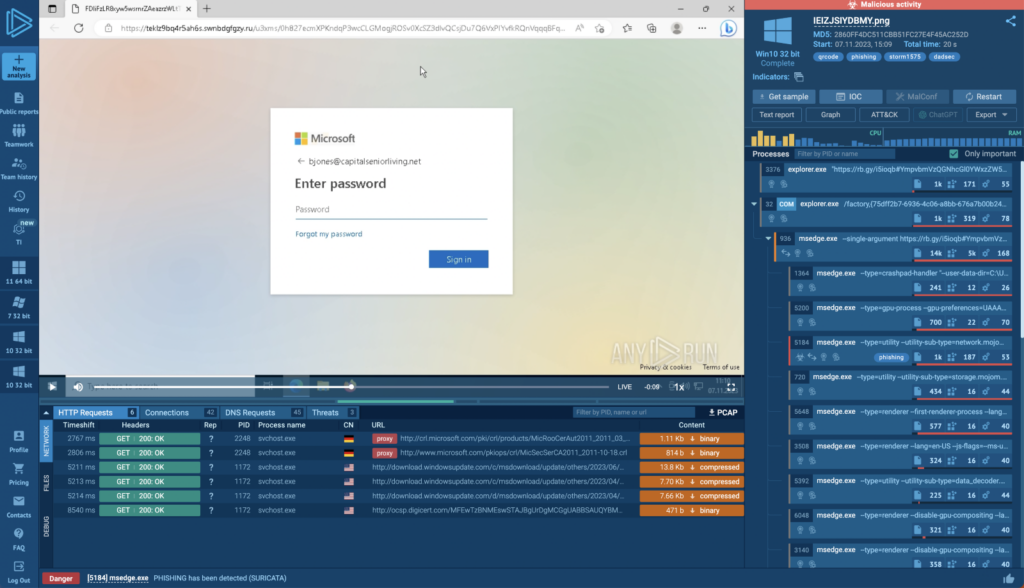
We can see that the QR took us to a fake login page, and that the phishing was detected by Suricata — note the message at the bottom left of the screen.
(Phishing is a big topic, and if you want to learn more about these tactics and see more examples, check out our dedicated article on new phishing tools).
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real-time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free







0 comments