As we wrap up 2024, let’s take a moment to reflect on what an incredible year it’s been for ANY.RUN. Together, we’ve achieved so much: breaking barriers, improving tools, and working side by side with you, our amazing community of cybersecurity heroes.
From big product launches to small tweaks that make a huge difference, everything we’ve done this year has been with one goal in mind: to make your fight against cyber threats easier, smarter, and faster.
Let’s take a look back at some of the highlights that made this year unforgettable!
Interactive Sandbox
This year, we took significant strides to enhance your experience with the ANY.RUN sandbox, introducing new features and upgrades to help you combat cyber threats more effectively.
Linux OS Support for In-Depth Malware Analysis
For the first time, our sandbox extended its capabilities beyond Windows, making it possible for malware analysts, SOC teams, and DFIR experts to analyze Linux-based samples in a secure and interactive cloud environment.
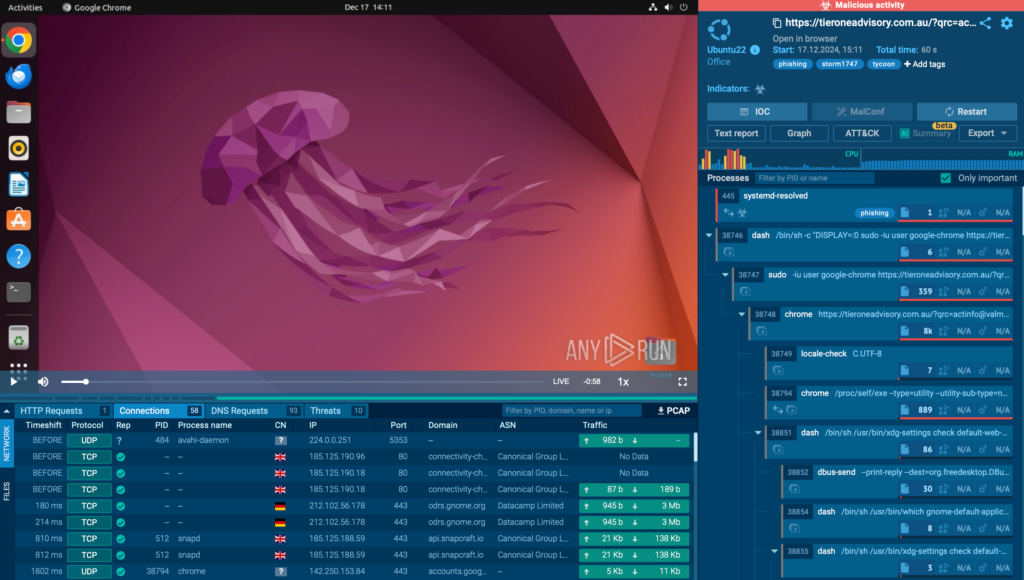
With real-time monitoring of suspicious activities, detailed reports featuring the MITRE ATT&CK Matrix, Process Graphs, and IOCs, you can now uncover threats on Linux systems with the same precision and speed you’ve come to expect from ANY.RUN.
Universal Windows 10 x64 Access
In 2024, we made Windows 10 (64-bit) VMs available to all users, including those on the Community plan!
Everyone can analyze malware and phishing threats in a modern Windows environment, leveling the playing field for cybersecurity investigations.
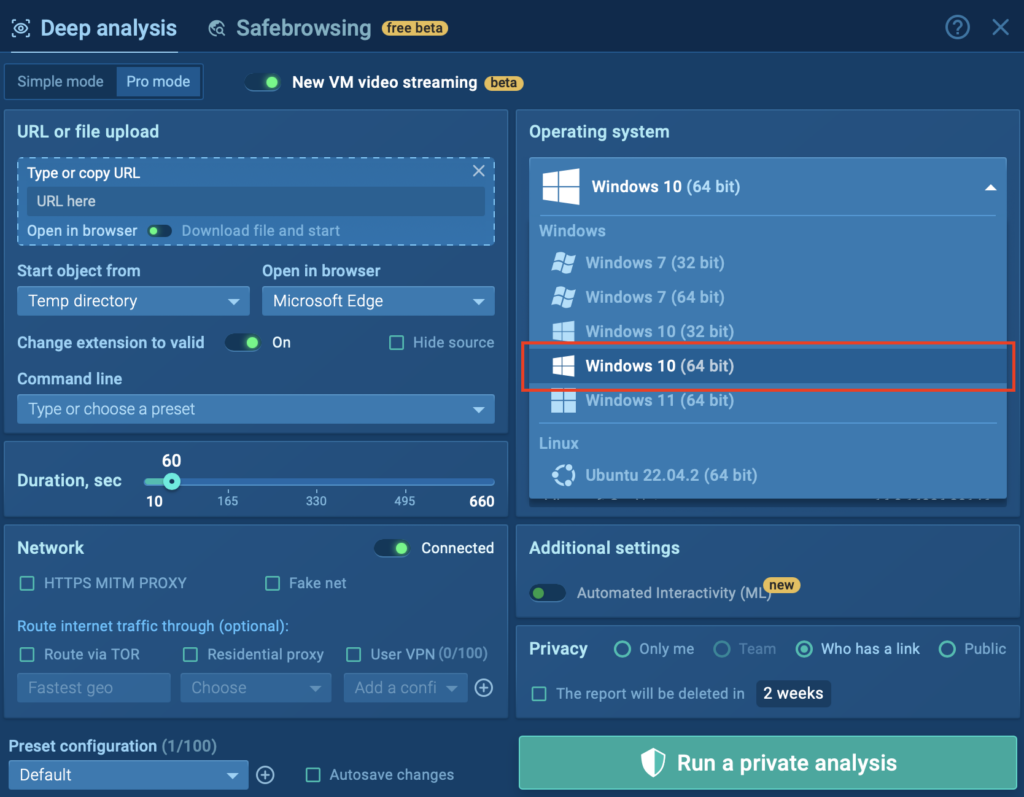
This update ensures everyone can access powerful threat analysis tools and helps improve threat detection for the entire ANY.RUN community.
Automated Interactivity: Smarter and Faster Malware Detonation
With Stage 2 Automated Interactivity, ANY.RUN’s Interactive Sandbox now handles even more complex malware and phishing scenarios automatically. From extracting URLs in QR codes to detonating payloads in email attachments and navigating long redirect chains, it’s all done without user input.
Our analyst team continuously adds new attack scenarios, ensuring your sandbox stays one step ahead of evolving threats!
A New Look at Network Threats: Redesigned Details Window
IIn 2024, we revamped the Threat details window to give you a clearer view of malware activity. Now, you can access all key intel, like source data, IP addresses, ports, and protocols, in one streamlined view.
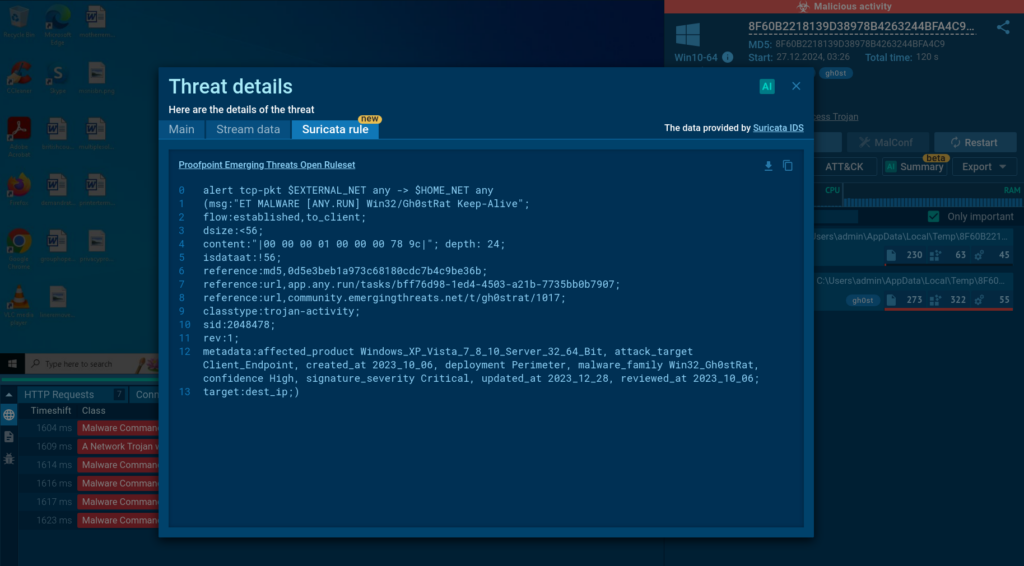
And for Hunter and Enterprise users, the new Suricata rule tab opens the door to the signatures behind the detections.
PowerShell Support in Script Tracer
This year, we supercharged our Script Tracer by adding PowerShell support to its arsenal, alongside JScript, VB Script, VBA, and Macro 4.0.
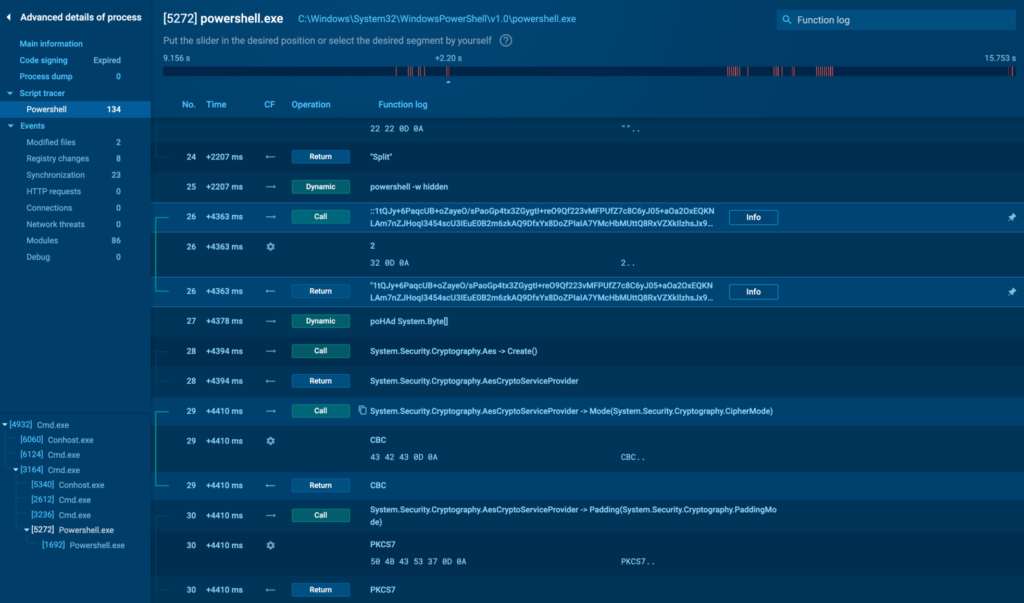
Now, you can follow PowerShell scripts step by step, making it easier to analyze and counter malware leveraging persistence, lateral movement, or payload execution.
Your Private AI Assistant: Smarter, Safer, and Always There to Help
This year, we introduced a private AI model inside ANY.RUN’s sandbox.
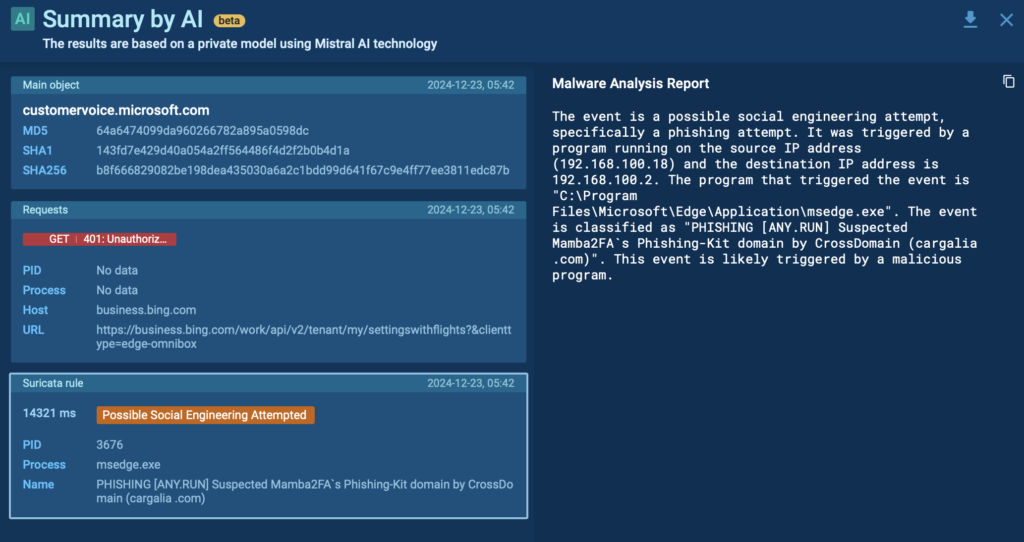
Now, you can get fast, AI-powered explanations in both public and private sessions, without worrying about data leaving your hands.
Phishing Detection with RSPAMD
In 2024, we leveled up our phishing detection game with the integration of RSPAMD, an open-source email filtering system, into ANY.RUN’s Static Discovering module.
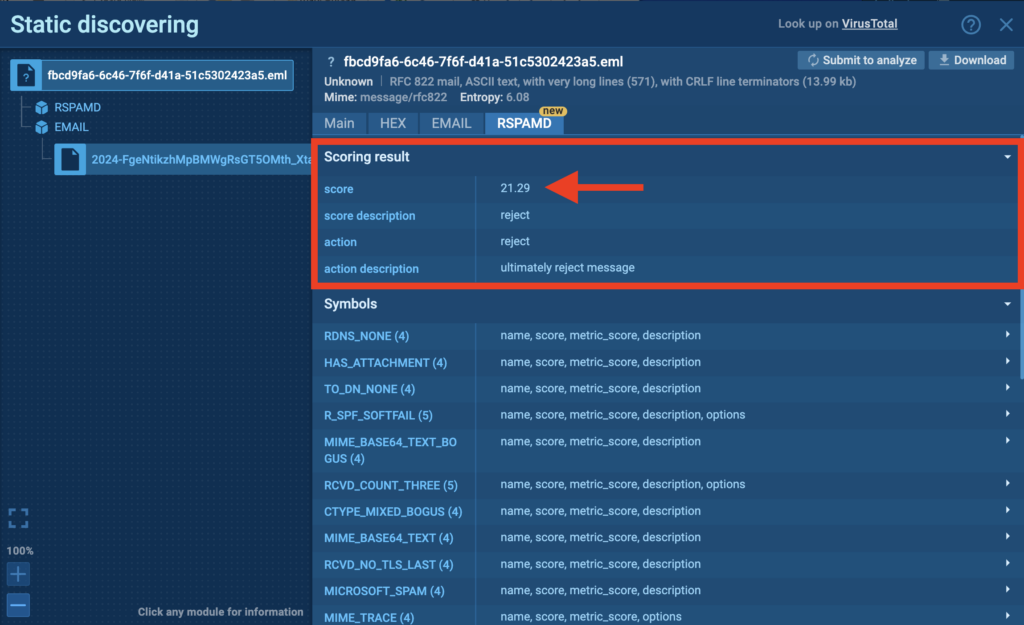
With features like Score, Content, and Header Descriptions, you can dive deep into email analysis.
STIX Reports
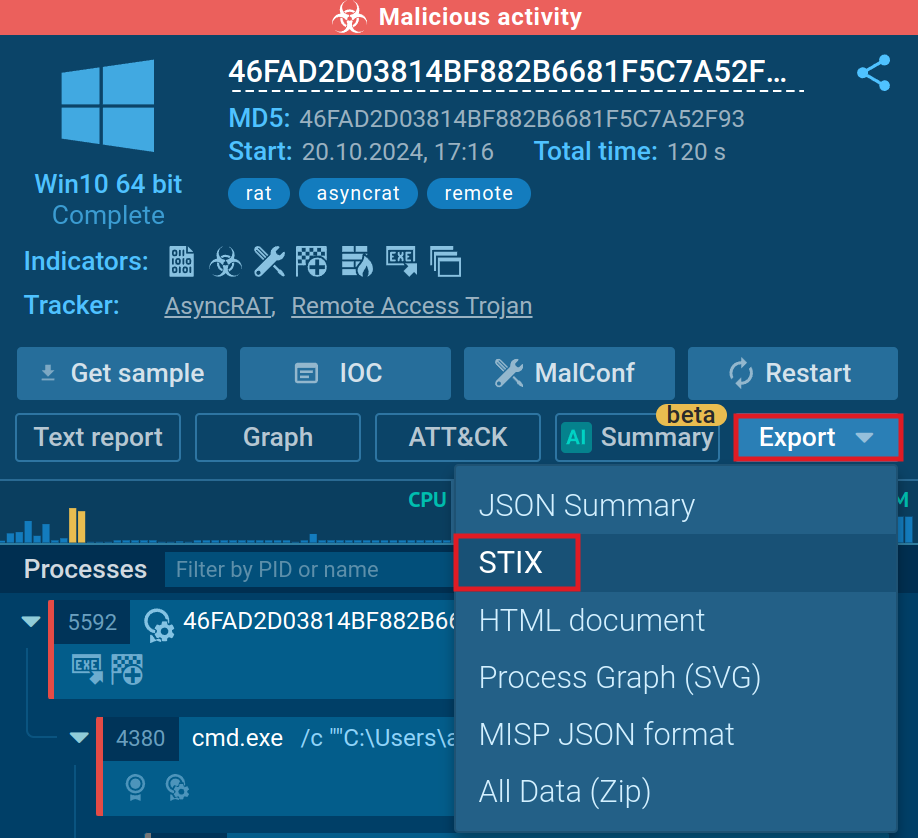
We added the ability to export threat data in the STIX format, a standardized language for sharing cyber threat intelligence. The report contains the link to the sandbox session, hashes, network traffic details, file system modifications, TTPs, and more.
A Fresh Look for Faster Analysis: Sandbox Home Screen Redesign
We gave the ANY.RUN Sandbox home screen a sleek makeover to make navigation easier and faster.
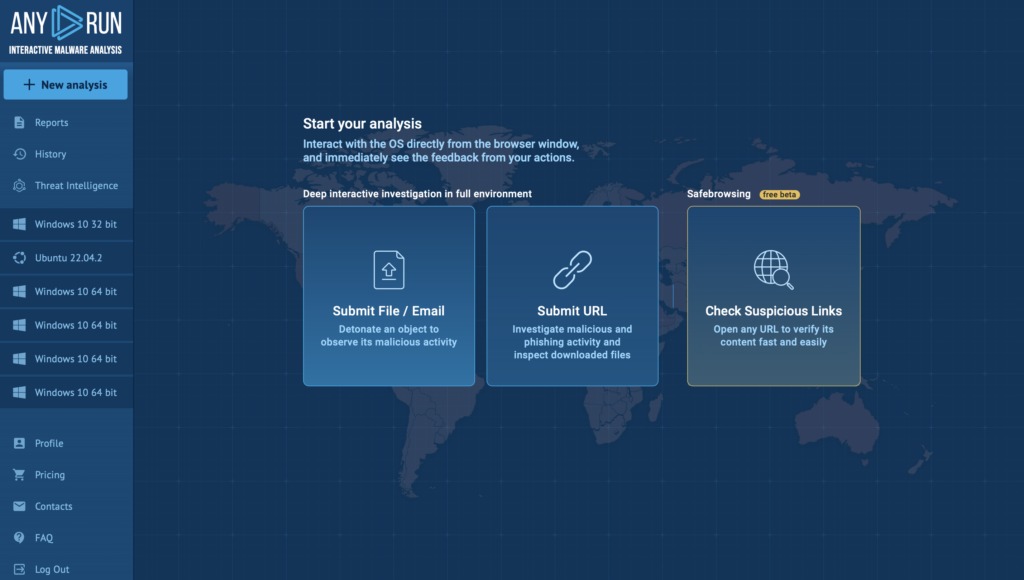
New shortcut buttons let you launch analysis sessions in just a click
Tag It Your Way: Custom Tags via API
Now you can set custom tags to sandbox sessions directly through the API, adding to the flexibility of the web interface. Organize and categorize your analyses your way, with more control than ever before!
Teamwork Upgrades
This year, we made significant upgrades to the Teamwork functionality of the ANY.RUN sandbox. Some of the key changes include:
- Single Sign-On (SSO): We’ve tackled key issues like fixing the logout process and resolving setup problems. Plus, you now can log in not just through our authorization window but also using third-party services.
- Exporting team history: Enterprise users can now export structured lists of their team’s sandbox sessions in JSON format.
- Mutli-admin support: Team owners can now appoint multiple admins to manage their teams more effectively. Admins have the ability to enable and disable SSO, invite or remove team members, and manage licenses, including Threat Intelligence (TI) licenses.
Threat Intelligence Lookup
In 2024, we introduced Threat Intelligence Lookup, a tool designed to give you access to a centralized repository of millions of Indicators of Compromise (IOCs), Indicators of Attack (IOAs), and Indicators of Behavior (IOBs).
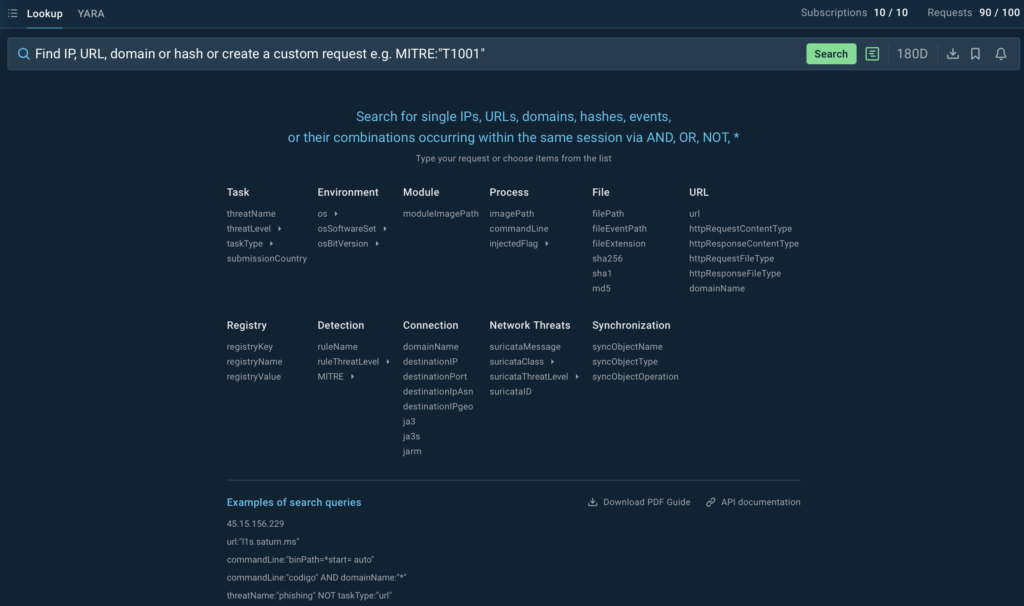
This powerful service allows you to build precise queries, use them to search across threat data from sandbox sessions, and enrich your threat intelligence with additional context, connecting isolated IOCs to broader malware campaigns, all in one place.
But we didn’t stop there!
Throughout the year, we worked hard to refine TI Lookup, adding new features and capabilities to make it even better for security teams and professionals.
Here’s how we’ve enhanced it:
YARA Search: Your Custom Threat-Hunting Tool
This year, we expanded our Threat Intelligence suite with YARA Search, giving users the power to scan ANY.RUN’s extensive database using custom YARA rules.
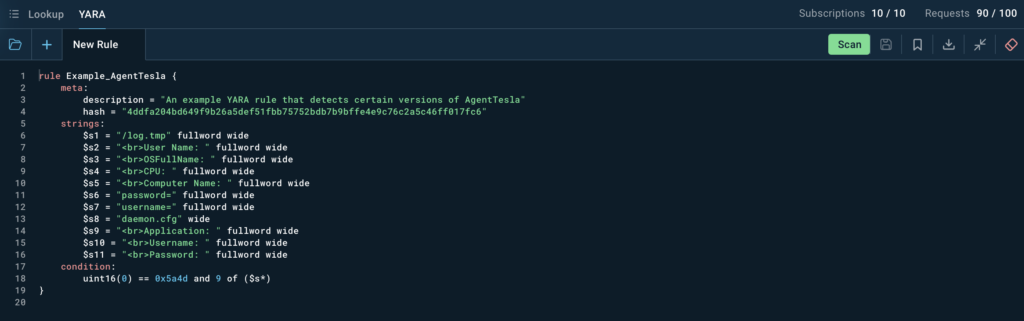
With a built-in editor, you can easily write, edit, test, and manage your rules. Once matching malicious files are identified, dive deeper by analyzing their behavior directly in the sandbox.
Mutex Search: Precision Meets Speed in TI Lookup
We’ve enhanced Threat Intelligence Lookup with a powerful Mutex Search feature, designed to make your investigations faster and more precise.
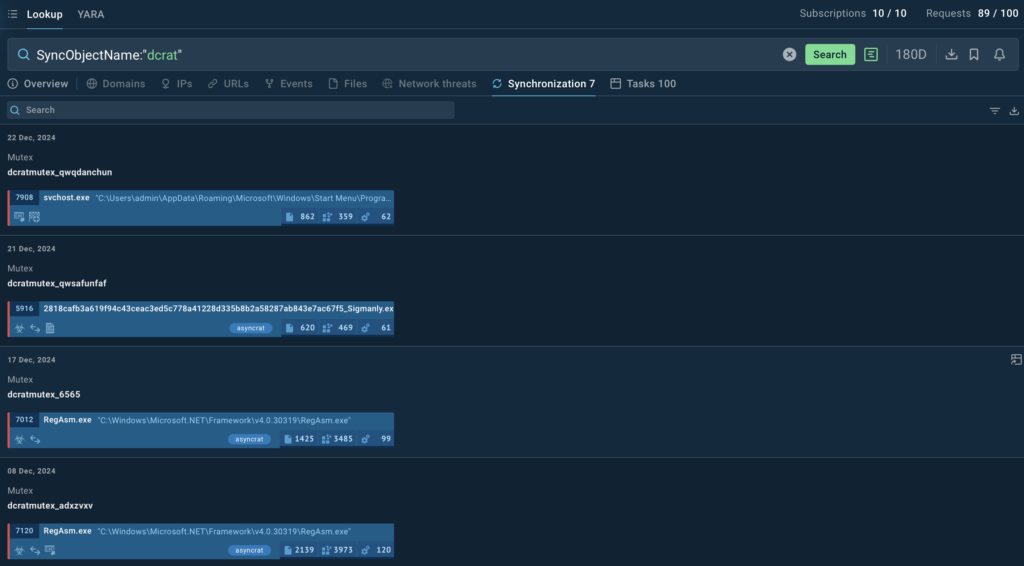
Using queries like SyncObjectName:”[name of the malware]”, you can quickly locate relevant sandbox analysis sessions tied to specific mutexes.
Suricata Search: Deeper Dive into Network Threats
The Threat Intelligence Lookup now includes Suricata search fields, making it easier to pinpoint specific network threats.
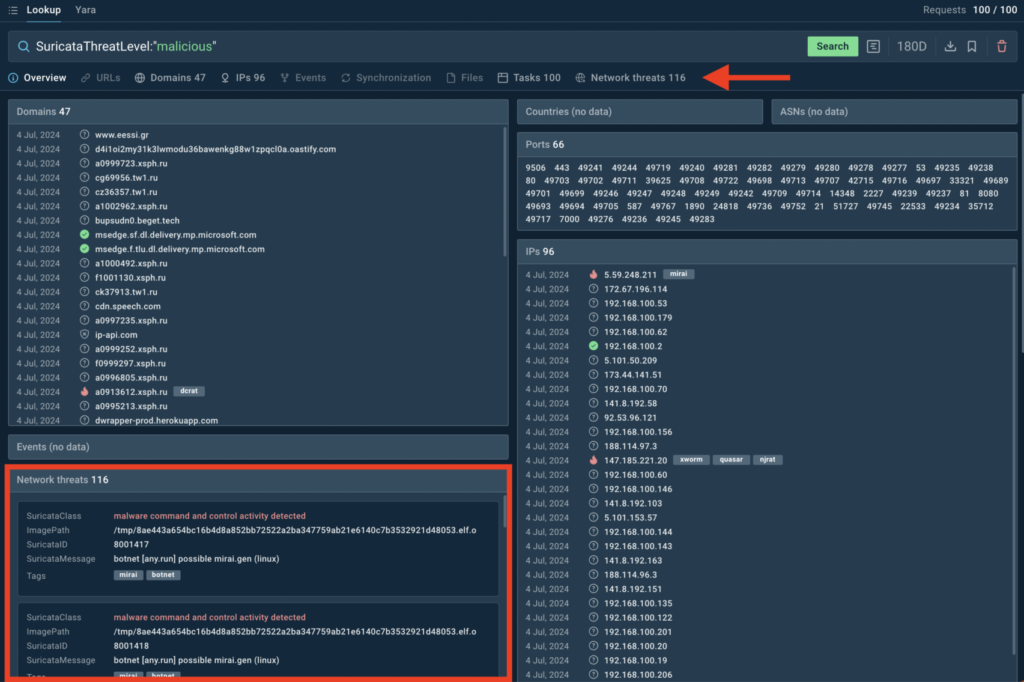
Search using fields like SuricataClass, SuricataMessage, SuricataThreatLevel, and SuricataID to uncover detailed information about network activity.
Malware Config Insights: Unlocking Hidden IOCs
We’ve expanded Threat Intelligence Lookup to include IOCs from malware configurations, manually extracted from reverse-engineered samples.
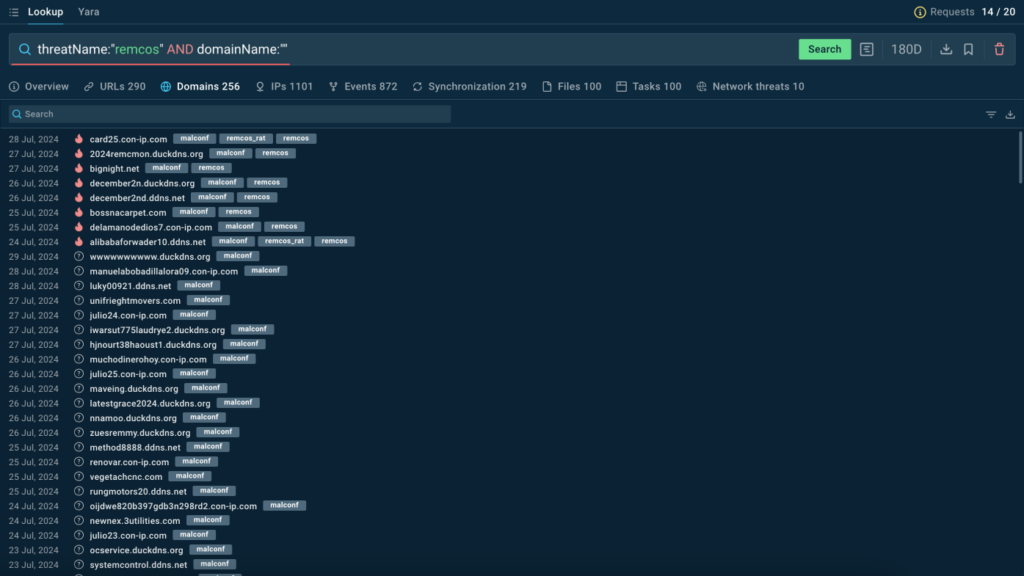
Currently covering 79 malware families, these config-based IOCs are tagged with “malconf” for easy identification. This feature gives you a clearer understanding of malware behavior and helps you uncover actionable insights faster than ever.
Notifications
Threat Intelligence Lookup has also been upgraded with the new Notifications feature.
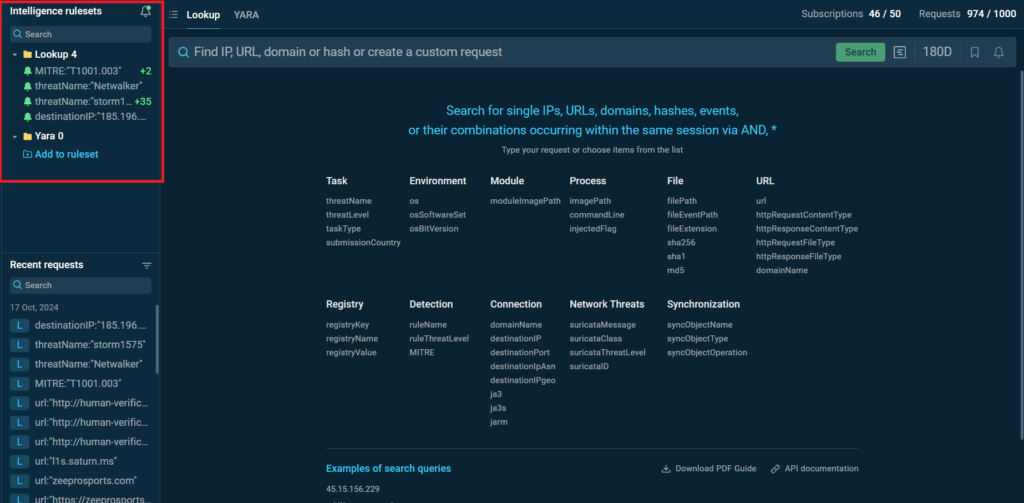
Subscribe to specific search queries and receive alerts on new IOCs, IOAs, and IOBs directly in your dashboard. New results are clearly highlighted, making it easier to stay on top of emerging threats and act quickly.
Redesigned Home Screen with Interactive MITRE ATT&CK Matrix
In 2024, we took the time to give the Threat Intelligence home screen a thoughtful upgrade, making it more user-friendly and packed with valuable features.
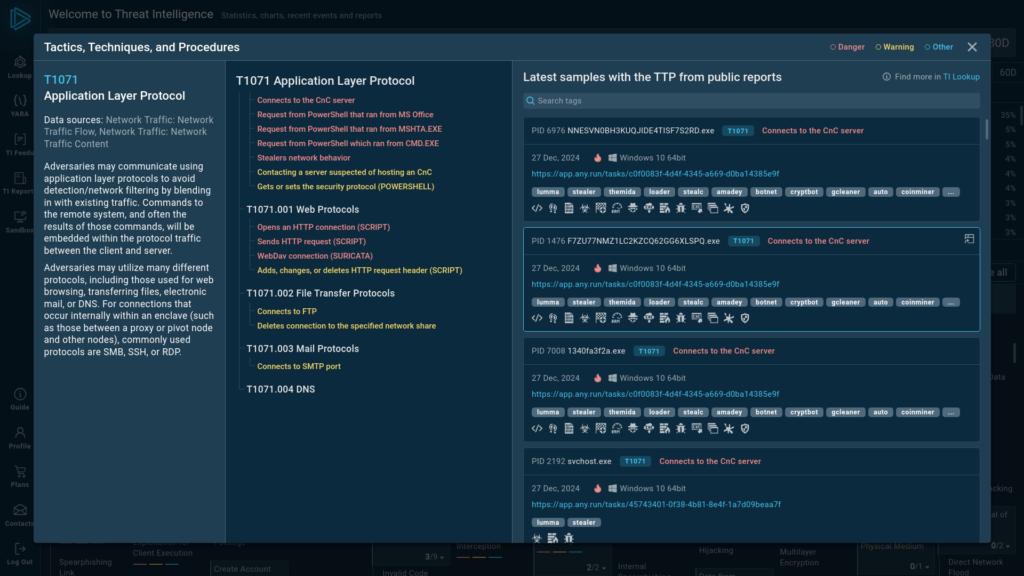
The new design offers a clearer, more intuitive view of the threat landscape. We’ve added a MITRE ATT&CK matrix with refined techniques and tactics, along with real-world examples of malware and phishing threats analyzed in the ANY.RUN sandbox.
TI Feeds
Our Threat Intelligence Feeds provide actionable data on malicious IPs, URLs, and domains, collected from analysis sessions created by over 500,000 researchers in the ANY.RUN sandbox.
This year, we further improved TI Feeds by introducing STIX and MISP formats.
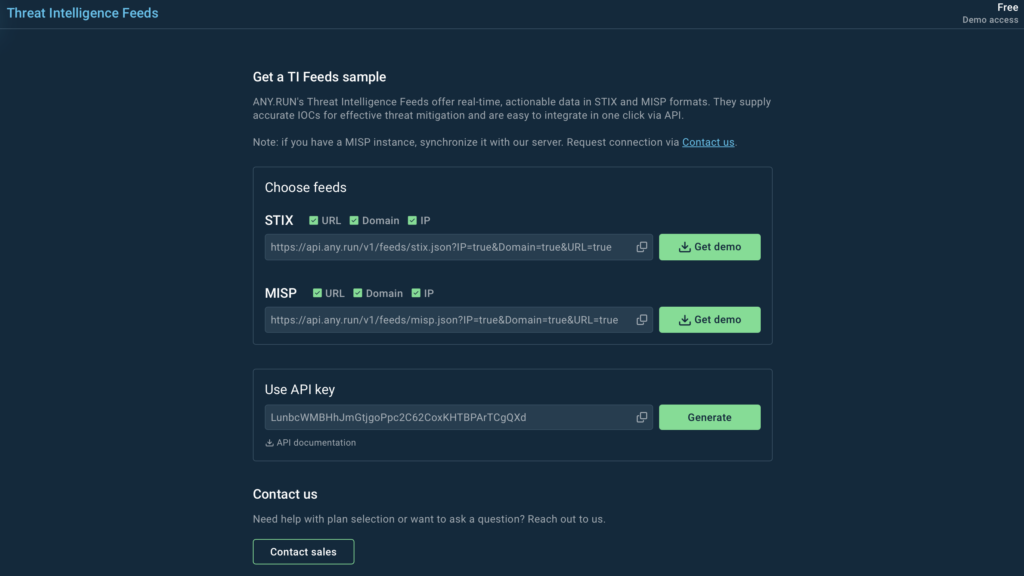
We also introduced demo samples of our feeds that any user can try for free via API.
Safebrowsing
In 2024, we brought you Safebrowsing, a new tool designed for faster and simpler threat analysis.
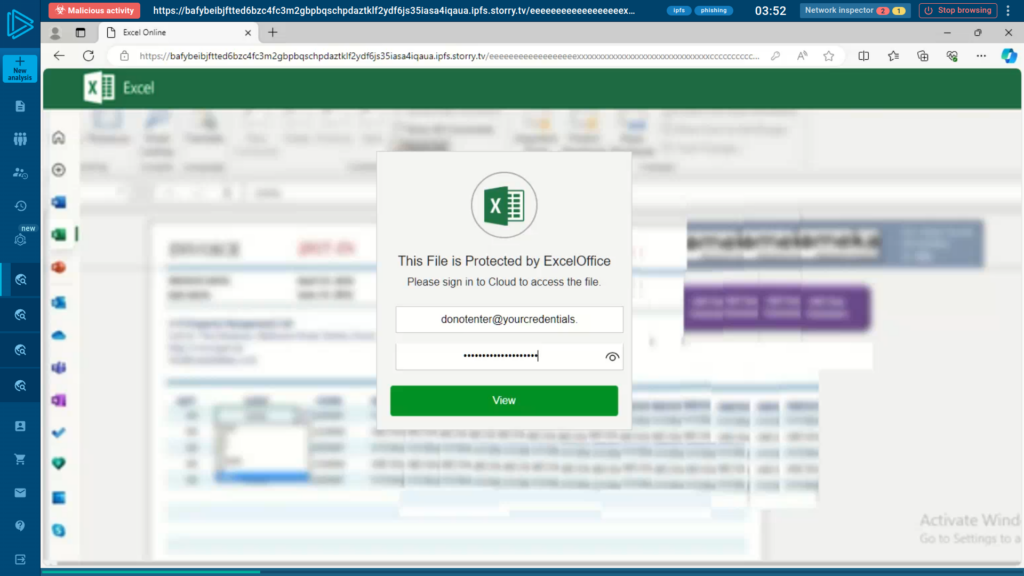
With Safebrowsing, you can safely analyze suspicious URLs in a fully interactive, isolated browser environment. It’s a quick and secure way to explore websites, verify malicious content, and protect your local system from risk.
Browser Extension
We made malware analysis even easier with the launch of the ANY.RUN Browser Extension for Chromium-based browsers.
With this extension, you can start analysis sessions directly from your browser and view results instantly, either in the extension or in the sandbox for deeper investigation. It’s fast, simple, and designed to save you valuable time.
Integrations
At ANY.RUN, we know how important integrations are for streamlining your threat analysis workflows.
That’s why in 2024 we focused on expanding our connectivity with industry-leading platforms to make your investigations faster and more efficient.
Integration with OpenCTI
We integrated with OpenCTI, allowing users to enrich their threat intelligence with data from ANY.RUN. Malware labels, malicious scores, TTPs, file hashes, and IP addresses are now transferred into OpenCTI, eliminating manual work and centralizing your analysis.
Integration with Splunk
We also launched an integration with Splunk, bringing our Interactive Sandbox and Threat Intelligence Lookup directly into the Splunk SOAR environment.
It lets you analyze malicious files and URLs, and enrich your investigations with comprehensive threat intelligence, all without leaving your familiar Splunk environment.
Cyber Threat Research from ANY.RUN Team
In 2024, ANY.RUN’s team of malware analysts continued to share their research on new and emerging threats, helping the cybersecurity community stay informed. Take a look at some of the article published by our team throughout the year:
- Zero-day Attack Uses Corrupted Files to Bypass Detection: Technical Analysis
- PSLoramyra: Technical Analysis of Fileless Malware Loader
- New PhantomLoader Malware Distributes SSLoad: Technical Analysis
- Brief Overview of the DeerStealer Distribution Campaign
Make sure to subscribe to us on X and other social media to get quick rundowns on active malware and phishing campaigns.
ANY.RUN’s Top Awards in 2024

In 2024, ANY.RUN’s commitment to innovation and excellence in cybersecurity was recognized with prestigious industry awards. They reflect the hard work of our team and the impact of our tools on the global cybersecurity community:
- Cybersecurity excellence awards– Winner in the Threat Hunting category, highlighting our impact and commitment to excellence.
- Best security solution– Our platform was named the Best Threat Intelligence & Interactive Malware Analysis Platform, praised for its innovation and user-friendly design.
- Top 150 cybersecurity vendors– ANY.RUN earned a spot on IT-Harvest’s Top 150 Vendors, a global benchmark in the cybersecurity field.
- Best in behavior analytics– The CyberSecurity Breakthrough Awards recognized our behavior analytics and the advanced Automated Interactivity feature.
We’re proud of these achievements and look forward to raising the bar even higher in 2025!
Stronger Together: Collaboration with the ANY.RUN Community
We were closer than ever with the incredible ANY.RUN community. Together, we uncovered new threats, presented cutting-edge technical analyses, and pushed the boundaries of what’s possible in malware research.
Your active engagement has been at the heart of our success. We can’t thank you enough for your support and collaboration throughout the year.
As we look ahead to 2025, we’re excited to bring even more opportunities for mutual collaboration.
Let’s continue to grow, learn, and tackle cyber threats together!
More to Come in 2025
As we celebrate these milestones, we’re already looking ahead to 2025. With exciting projects on the horizon, new features in development, and your continued support, we’re confident that the best is yet to come.
To every researcher, analyst, and team who trusted ANY.RUN this year: thank you. You are the reason we do what we do. Here’s to another year of fighting cybercrime.
Happy New Year,
The ANY.RUN Team
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.








0 comments