Malware is evolving faster than ever. As security measures improve, so do the techniques used to bypass them. This ongoing arms race has led to increasingly sophisticated obfuscation methods that challenge even seasoned analysts.
This blog post will explore some of the cutting-edge obfuscation tactics we’re seeing in the wild. We’ll break down how they work and discuss strategies for detection and mitigation. Whether you’re a security professional or simply interested in the latest cybersecurity trends, understanding these techniques is crucial in today’s digital landscape.
What is obfuscation
Obfuscation in malware is the practice of disguising code to make it difficult to understand or detect. It’s like digital camouflage, helping malicious software blend in with legitimate processes and files.
Obfuscation techniques range from simple to very complex. At its most basic, it might involve renaming variables to nonsensical strings. More advanced methods can include:
- Packing: Compressing the malware and including a small unpacking routine.
- Encryption: Encoding portions of the code, only decrypting them at runtime.
- Polymorphism: Constantly changing the malware’s code structure while maintaining its core functionality.
These techniques serve multiple purposes. They slow down analysis, helping malware stay undetected longer. They can also make it harder for security tools to recognize known threats.
Common Malware Obfuscation Techniques
1. XOR
XOR (exclusive or) encryption is a classic obfuscation technique that’s still widely used due to its simplicity and effectiveness. It works by performing a bitwise XOR operation between each byte of the original code and a key (or a repeating key pattern). Here’s the truth table for XOR:
| A | B | A XOR B –|–|——– 0 | 0 | 0 0 | 1 | 1 1 | 0 | 1 1 | 1 | 0 |
What makes XOR interesting is its symmetry — applying the same operation twice returns the original data. This means the same routine can be used for both encryption and decryption, simplifying the malware code.
Bypassing:
- Brute-force: For single-byte keys, try all 256 possibilities.
- Frequency analysis: In larger samples, the most common byte often represents XOR(space, key).
- Known-plaintext attack: If you can guess part of the original content (like common headers), you can derive the key.
- Entropy analysis: XORed data often has high entropy, helping to identify obfuscated sections.
Which of the following tools can be used to obfuscate malware code? We’ll mention a number of them. In this case, tools like XORSearch can automate much of the process. For more complex cases, try writing a custom IDA or Ghidra script to deobfuscate on-the-fly.
2. Subroutine Reordering
This technique shuffles the order of functions in the code, breaking the logical flow that analysts expect to see. It’s often combined with control flow obfuscation to create a confusing maze of jumps between subroutines.
Malware might take this to the extreme, splitting functions into tiny chunks and scattering them throughout the code. Each chunk ends with a jump to the next part, creating a “spaghetti code” effect that’s maddening to follow manually.
Bypassing:
- Control flow graph analysis: Tools like IDA Pro can visualize the program’s flow, helping to reconstruct the logical order.
- Dynamic analysis: Running the code in a debugger reveals the true execution path.
- Symbolic execution: Advanced techniques can explore multiple code paths simultaneously, helping to map out the program’s behavior.
3. Code Transposition
Code transposition takes reordering to the instruction level. Individual instructions or small code blocks are shuffled, with jump instructions added to maintain the correct execution order. This can make static analysis extremely difficult, as the code appears nonsensical when viewed sequentially.
Bypassing:
- Dynamic binary instrumentation: Tools like Intel Pin can help you trace the actual execution path.
- Emulation: Running the code in an emulator allows you to record and reorder the instructions as they’re executed.
- Custom disassemblers: For extreme cases, writing a custom disassembler that understands the obfuscation scheme can be necessary.
4. Code Integration
Code integration involves mixing malicious code with benign code, often by inserting it into legitimate programs or libraries. This technique leverages trust in known software to slip past defenses.
The malware might inserted into a legitimate software update, with malicious functions carefully woven into existing code and use existing variable names and mimicked the coding style, making it incredibly difficult to spot.
Bypassing:
- Diff analysis: Compare suspicious files with known clean versions to identify modifications.
- Behavior analysis: Look for unexpected network connections, file operations, or API calls.
- Code flow analysis: Identify unusual branches or calls to injected functions.
- Memory forensics: Analyze memory dumps to find hidden or injected code.
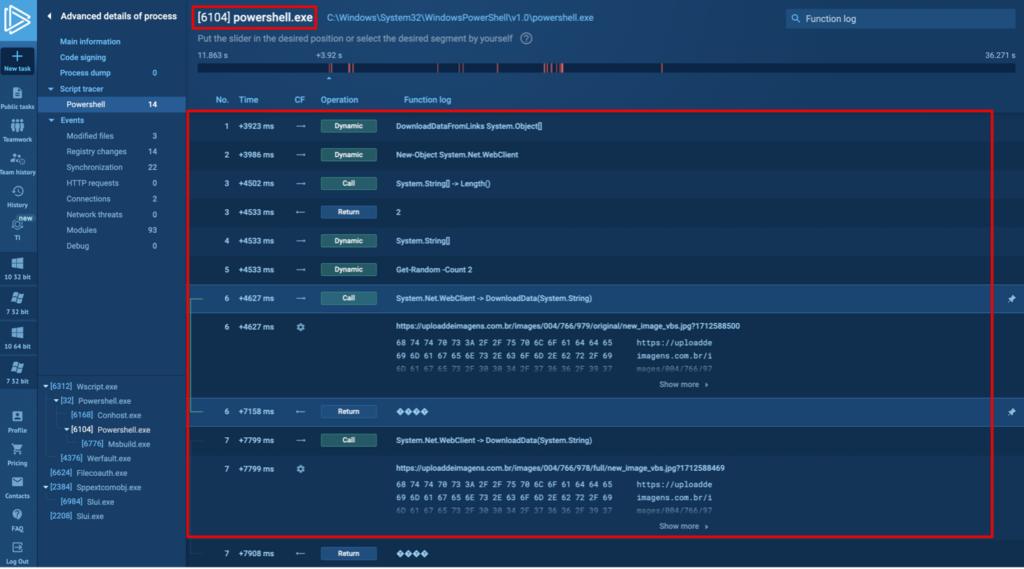
Tools like Bindiff can automate the comparison process. For runtime analysis, using a sandbox environment with detailed API call tracking (like ANY.RUN) can reveal malicious behavior that’s not apparent in static analysis.
5. Packers
Packers compress and encrypt the original code, with a small stub to unpack it at runtime. This not only obfuscates the code but also reduces file size, potentially helping the malware evade size-based detection.
Modern packers often employ anti-debugging, anti-VM, and other evasion techniques. Sometimes hackers use custom packers with advanced malware obfuscation techniques, like Clever Hans-style detection — they behave differently if they detect a try to analyze them, subtly altering the unpacking routine to produce benign code instead of the actual malware.
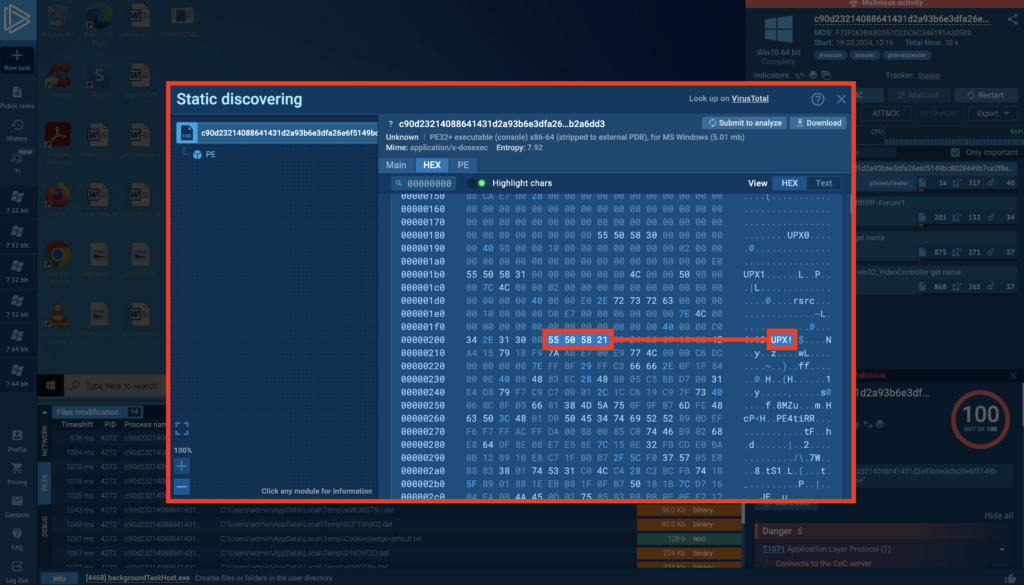
Bypassing:
- Static unpacking: Identify the packer (tools like DIE can help) and use a specific unpacker if available.
- Dynamic unpacking: Allow the packed program to run in a controlled environment, then dump the unpacked code from memory.
- Manual unpacking: For custom or heavily obfuscated packers, manually tracing the unpacking routine might be necessary.
ANY.RUN’s memory dumps can handle many common packers automatically. For custom packers, using a debugger can be effective.
Wrapping up
Remember, these techniques are often used in combination, creating layers of obfuscation. Patience, creativity, and a well-stocked toolkit are key to unraveling modern malware.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Try the full power of ANY.RUN for free









0 comments