When you investigate suspicious files or potential malware, you need deep visibility into process behavior. ANY.RUN‘s Advanced Process Details provides exactly that – in-depth information about how a specific process interacts with the system.
In this article, we’ll take a high-level look at what information you can find in advanced process details. Let’s get started!
Accessing the Feature
To open advanced process details, find the process you want to investigate in the main process tree view. Then, click to select it and look for the More Info button.
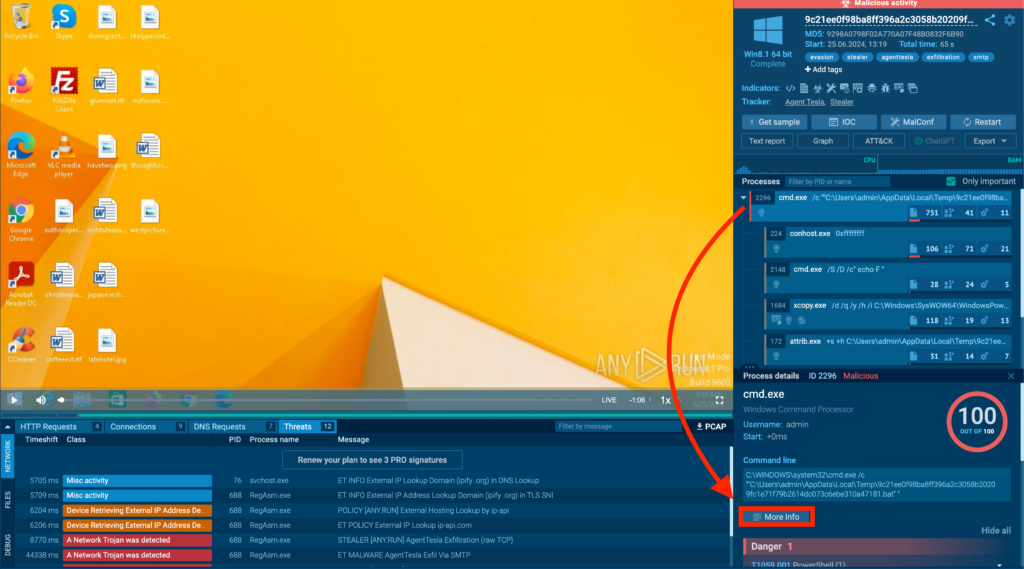
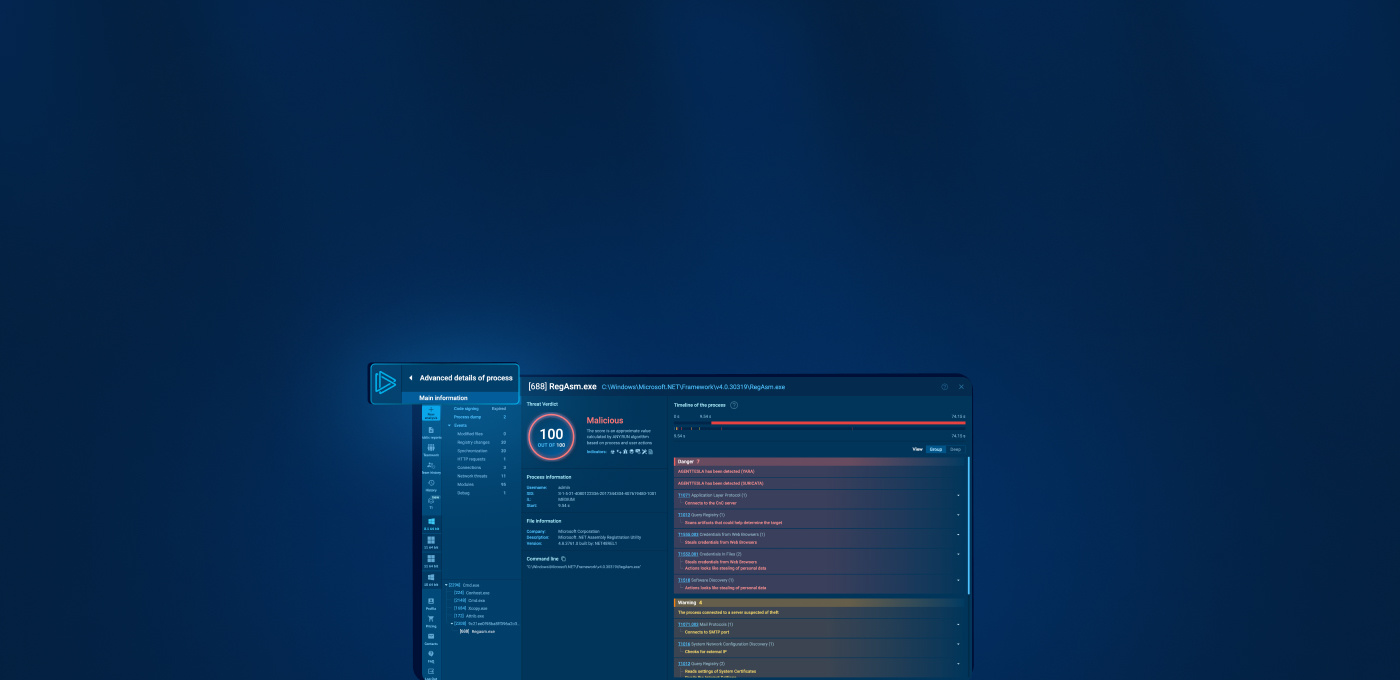
Clicking this button opens up the advanced details interface:
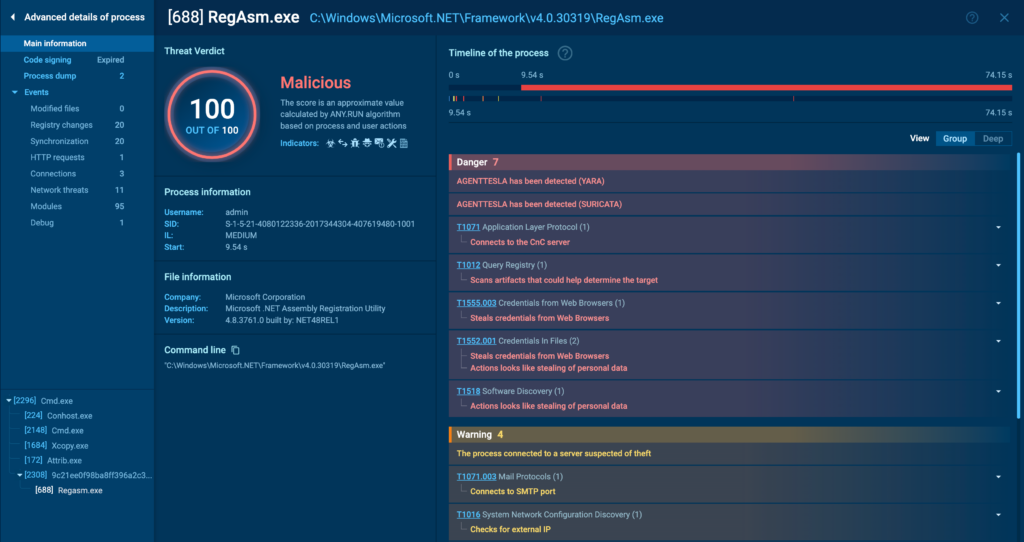
Interface Breakdown
Let’s start by breaking down the main interface, beginning with the general information on the right. This section mostly shows the same details as the process tree, but in a more expanded and easier-to-read format.
You can immediately see the malicious score and signatures, along with their descriptions. Unlike the tree view, here you can switch between Group view, which filters only the most important events, and Deep view, which lists all the process interactions with the system in sequence. Here’s how that looks:
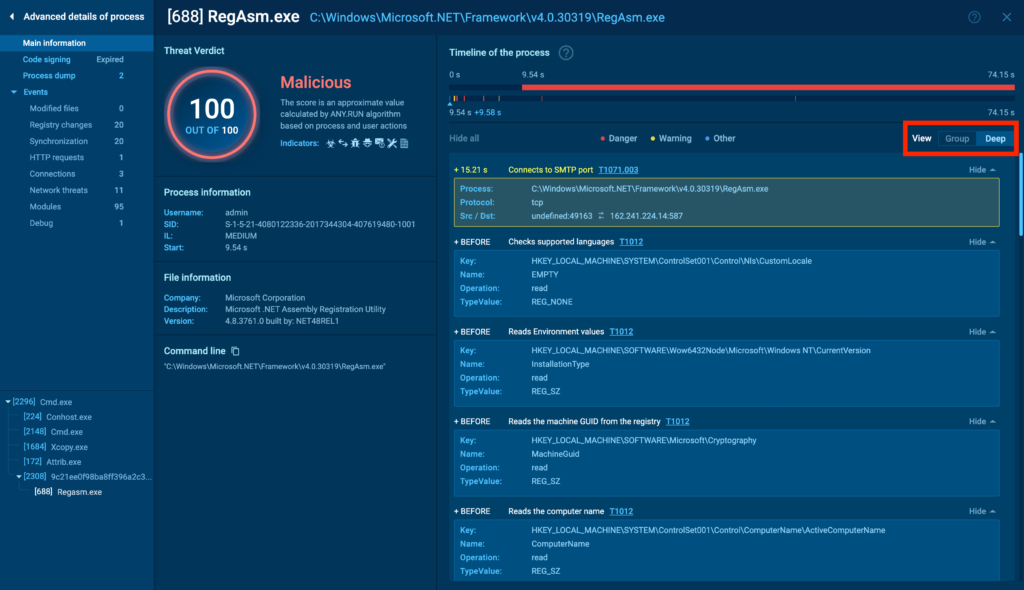
Another feature unique to advanced process details is the timeline. You can drag the pointer along it to adjust the displayed events based on the execution timeline.
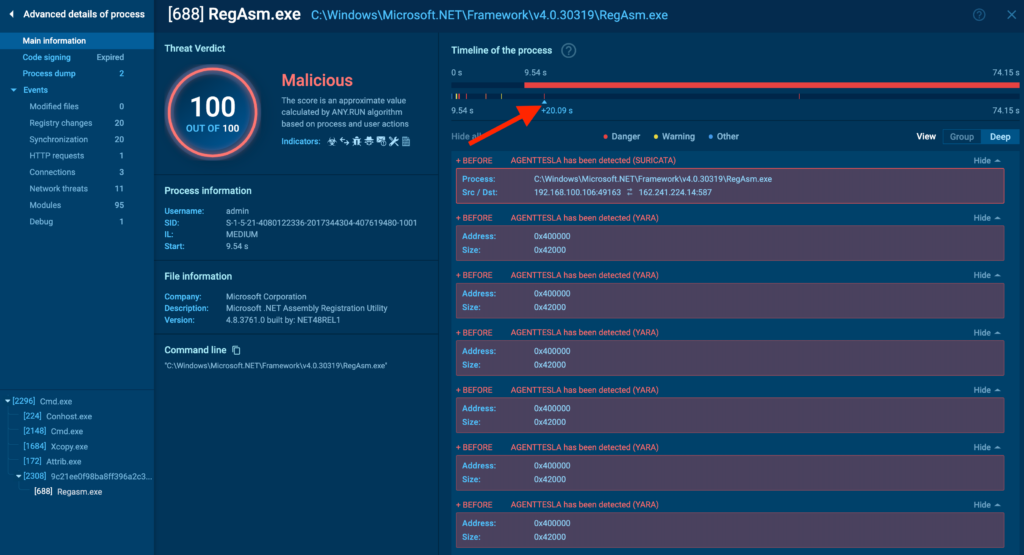
Now, let’s turn our attention to the menu on the left. The vertical menu is divided into two sections:
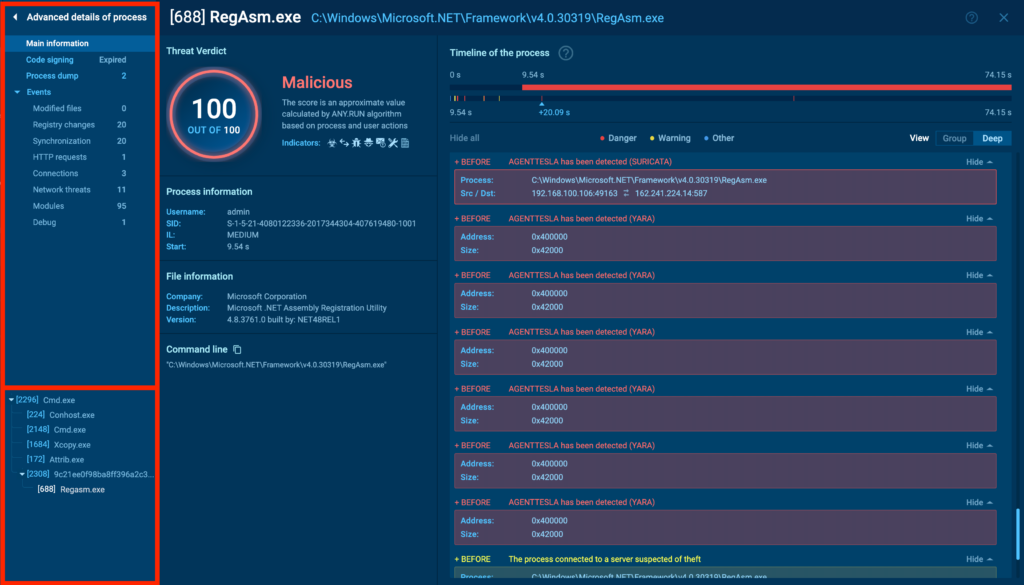
- The top section contains tabs with more in-depth information about the process.
- The bottom section features a list of processes, allowing you to switch between them without having to close out of the detailed view. Super convenient!
Breaking Down the Different Tabs
We’ll look at Main Information sub-menu first.
Code Signing
The Code Signing tab provides crucial insights into the authenticity of the process. It shows whether the process has a valid digital signature, which is often used to verify the legitimacy of software.
In this tab, you can see the certificate details, including the issuer, status, validity, and in-depth information about the signature.
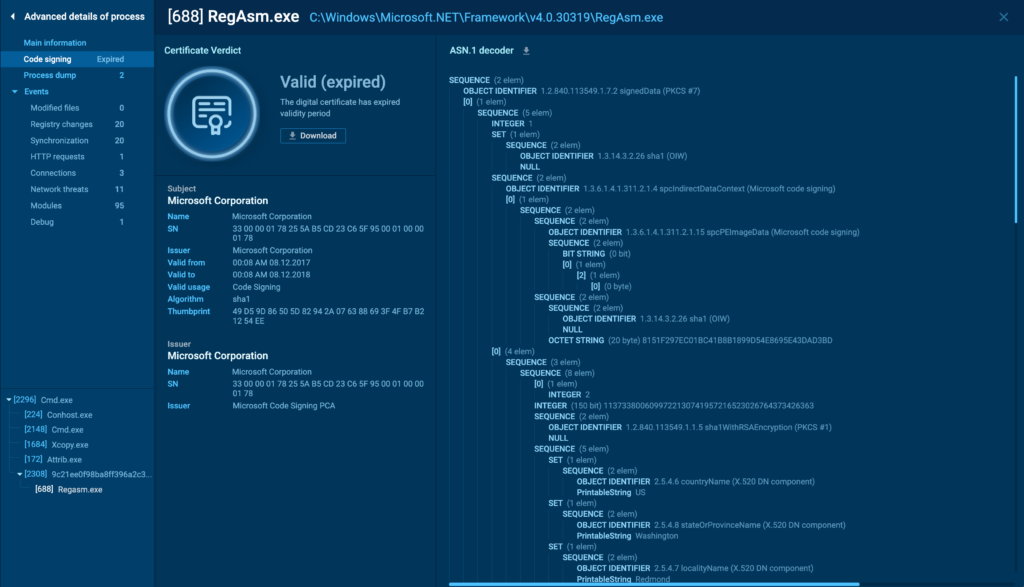
When using this tab, focus on verifying the legitimacy of the digital signature. A valid signature from a trusted issuer usually indicates that the process is safe. However, be cautious of expired or self-signed certificates, as these can be signs of potentially malicious activity.
Process Dump
The Process Dump tab allows you to download a full memory dump of the selected process. This is a powerful tool for in-depth forensic analysis. Memory dumps can contain vital information, such as encryption keys, passwords, and other sensitive data that the process was handling at the time of the dump.
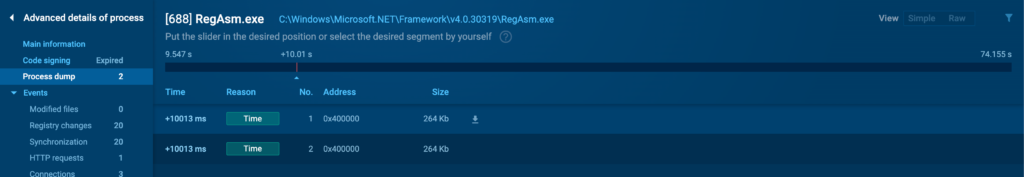
To download a dump, hower over it and click on the download icon which will appear next to the Size field.
Script Tracer
If the malware or process in question uses a scripting language, such as PowerShell, JavaScript, or VBScript, you will see a Script Tracer tab. It provides a detailed trace of the script execution, allowing you to see the exact commands and scripts being run by the process.
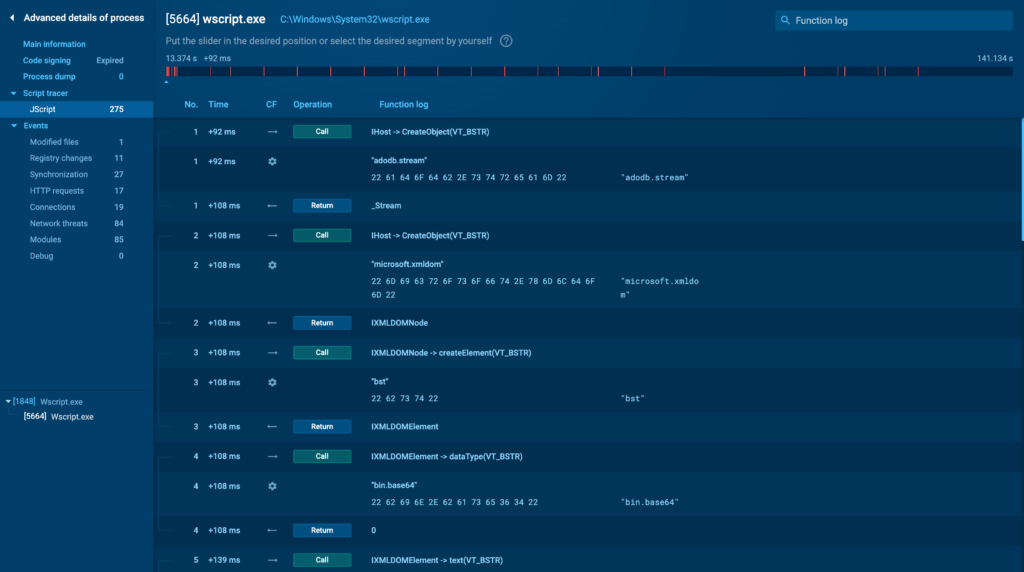
This tab is particularly useful when dealing with fileless malware or other threats that rely on scripts to perform malicious actions.
Next, let’s look at the various events ANY.RUN captures during analysis.
Modified Files
The Modified Files tab tracks all changes made to the file system by the process.
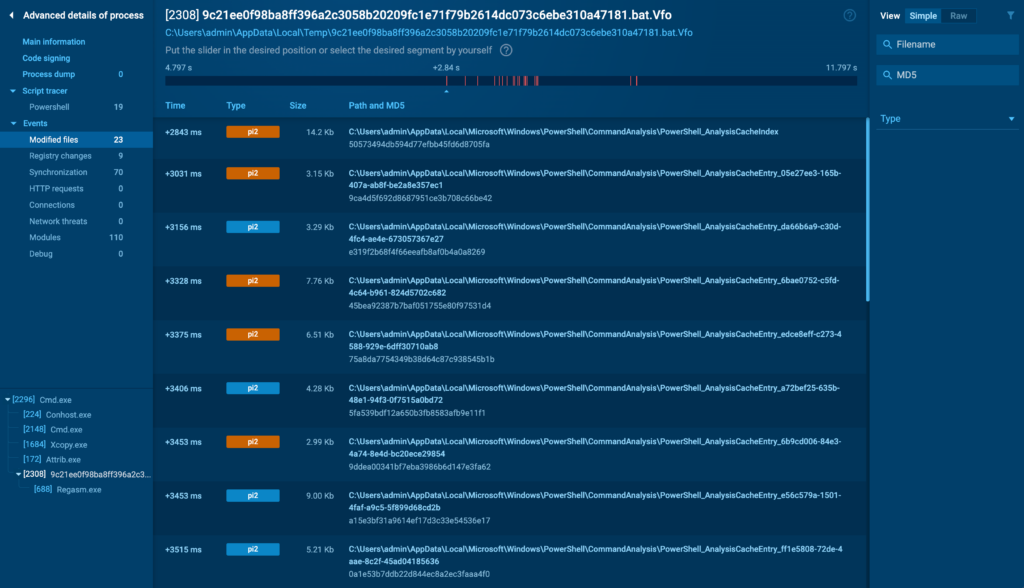
This includes file creation, modification, and deletion events. For malware analysts, this tab is invaluable, as it can quickly reveal if a process is attempting to drop or modify files in sensitive areas, such as system directories or startup folders.
Registry Changes
The Registry Changes tab logs any modifications the process makes to the Windows Registry. The registry is a common target for malware seeking persistence, as it can be used to run malicious code on startup or alter system behavior.
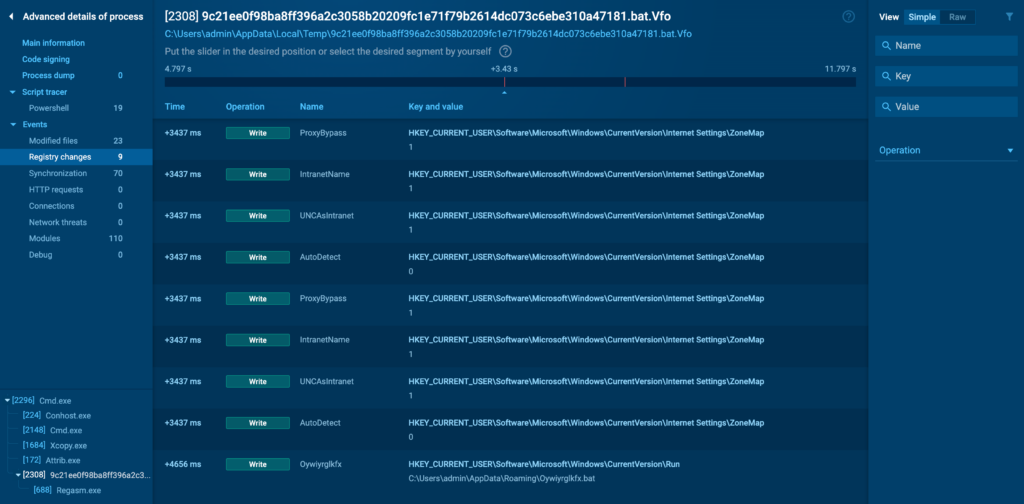
Key areas to monitor include startup entries, which are often manipulated by malware to ensure it runs automatically after a reboot.
Synchronization
The Synchronization tab provides details on any synchronization events, such as process waiting times or signals. These events can indicate coordination between different processes or threads, which is a common behavior in sophisticated malware.
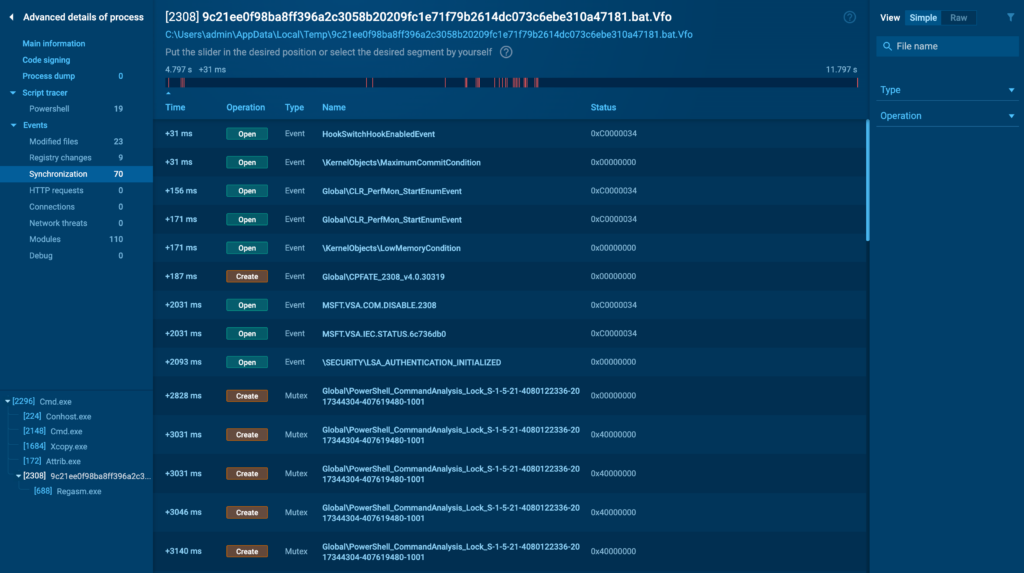
While less common in basic malware, synchronization events are more likely in advanced threats where multiple components must work together seamlessly. Monitoring these events can help identify complex malware that relies on inter-process communication.
HTTP Requests
The HTTP Requests tab logs all HTTP requests made by the process. This is critical for identifying whether a process is attempting to communicate with a remote server, which is a common behavior in malware that exfiltrates data or receives commands from a C2 server.
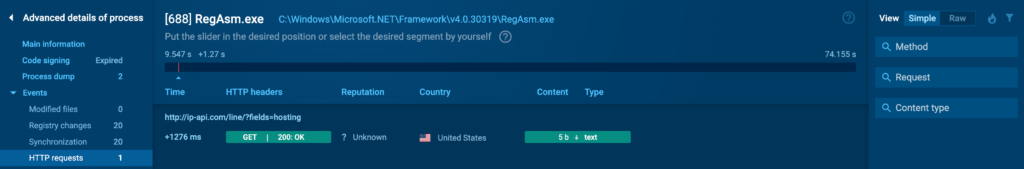
You can click on the colored buttons to access additional information about each request:
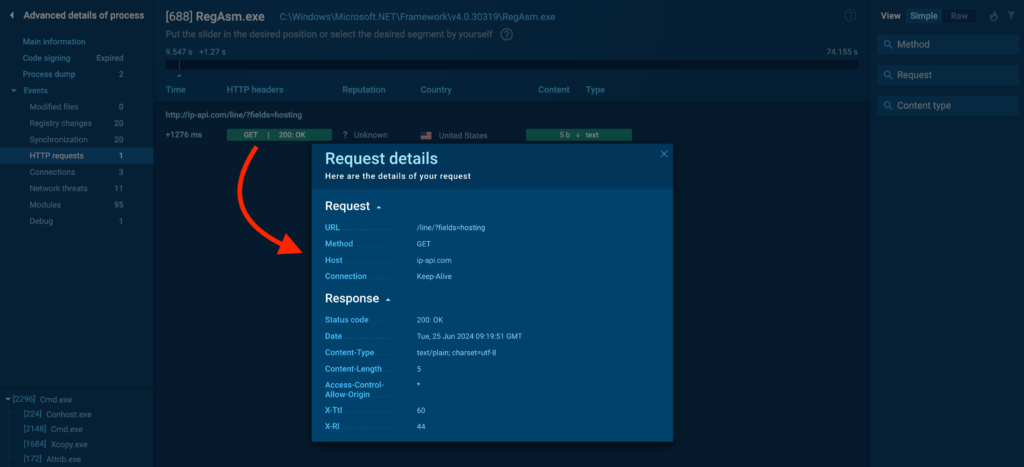
Connections
The Connections tab provides a detailed view of all network connections established by the process.
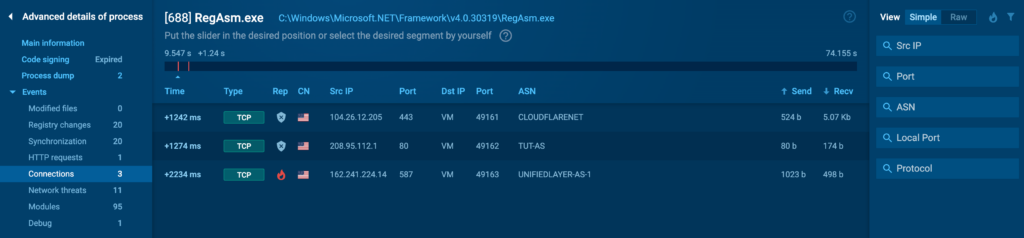
This includes both incoming and outgoing connections, along with information such as:
- IP addresses.
- Protocols.
- Ports.
- Reputation.
- ASN.
- Geolocation.
- Payload size.
Network Threats
The Network Threats tab is dedicated to identifying potential network-based threats associated with the process. It provides a high-level overview of any suspicious activities detected during the analysis, such as attempts to contact blacklisted IP addresses or domains. We use Suricata rules to detect these threats.
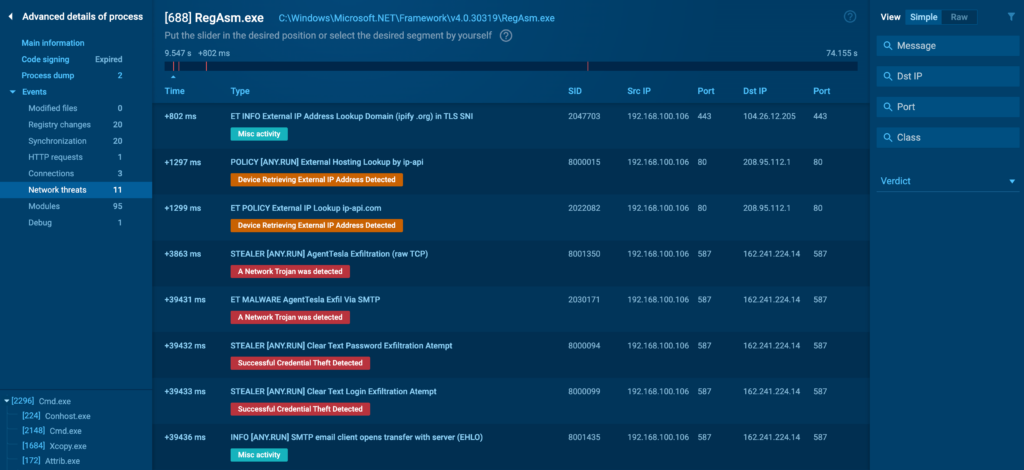
You can click on each identified threat to view the full Suricata rule that triggered the alert.
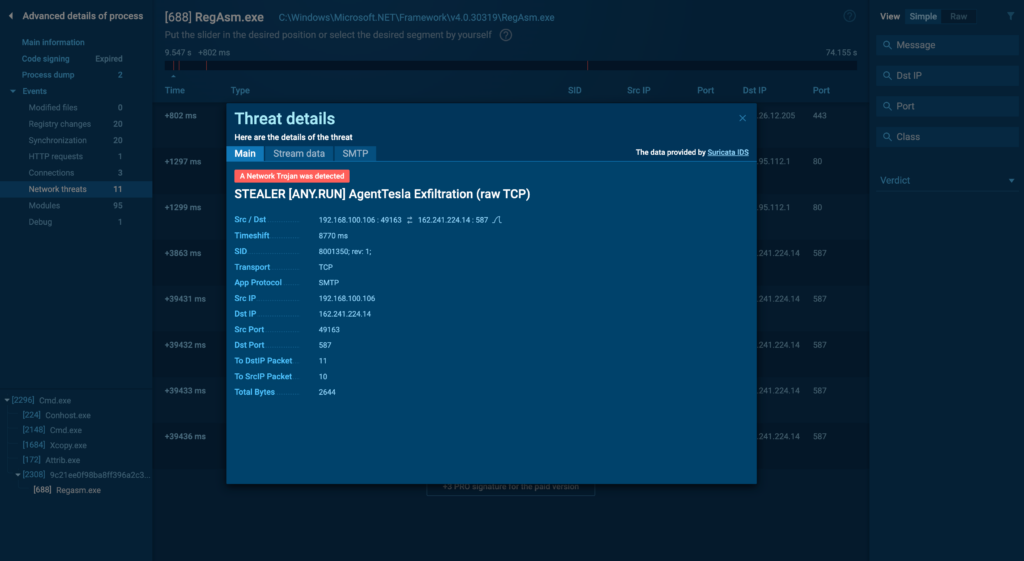
While most of these rules are available for free, some are exclusive to our paid subscribers. This allows for deeper insights into the detected threat, helping you understand the specific network behavior that was flagged.
Let us show you how ANY.RUN can help your SOC team – book a call with us ⬇️
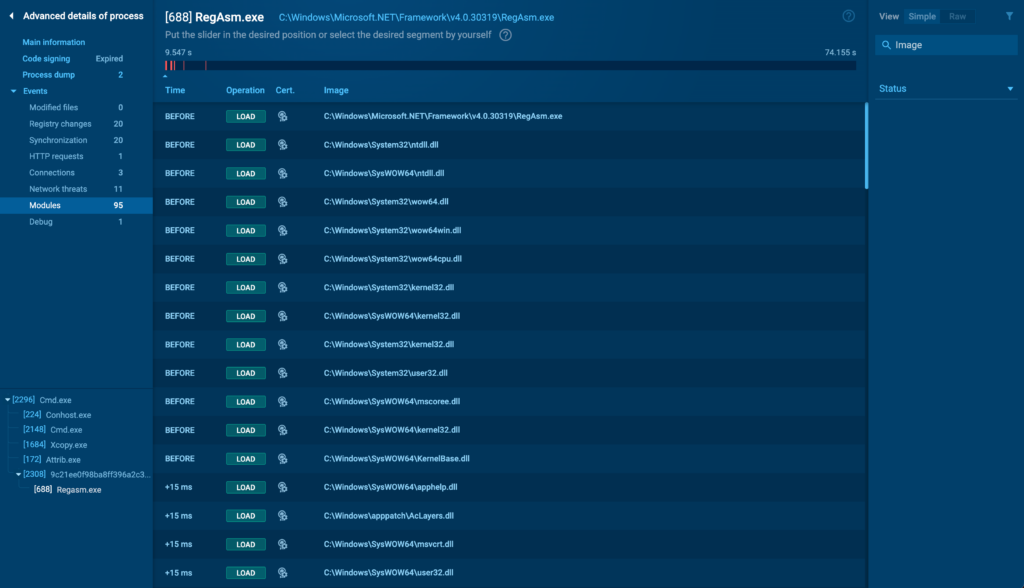
Modules
The Modules tab shows all modules loaded by the process. Malware often uses module injection to hide its presence or to leverage the capabilities of legitimate software components. This tab lists each module, along with its path and other relevant details.
Debug
The Debug tab provides additional information like exceptions, or other debugging information that can help in understanding complex malware behavior.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.









0 comments