Welcome to ANY.RUN‘s monthly updates, where we share what our team has been working on over the past month.
In May, we updated the sandbox homepage, introduced a dedicated page for TI Feeds in the Intelligence section of the app, and added several new YARA rules, signatures, and config extractors. We also updated some existing rules.
Here’s a closer look at what we’ve done.
New features
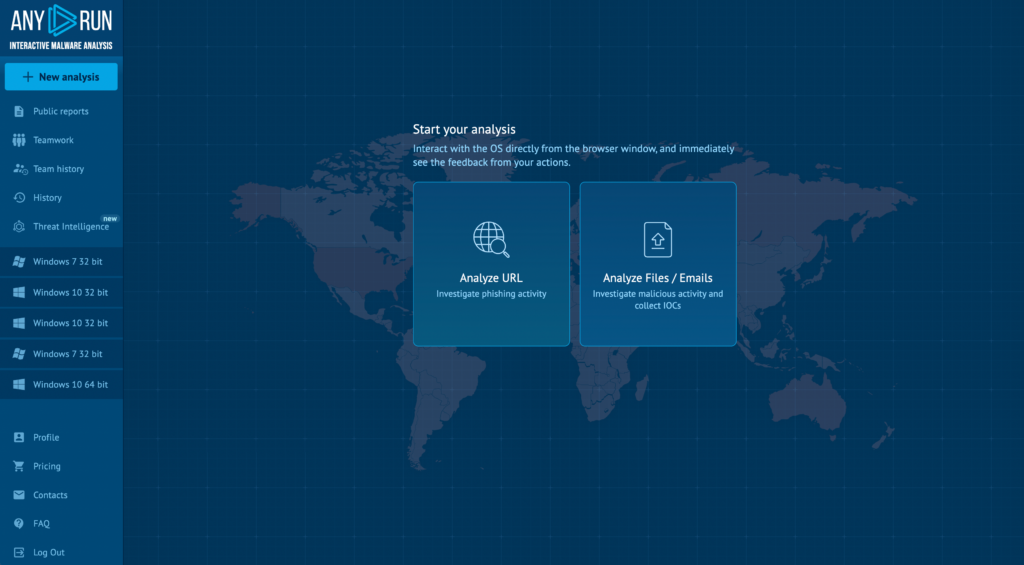
1. New sandbox home screen: We’ve added handy shortcut buttons to launch a new analysis session on ANY.RUN’s sandbox homepage. This replaces the old map, which has lives only in the Threat Intelligence section of the app.
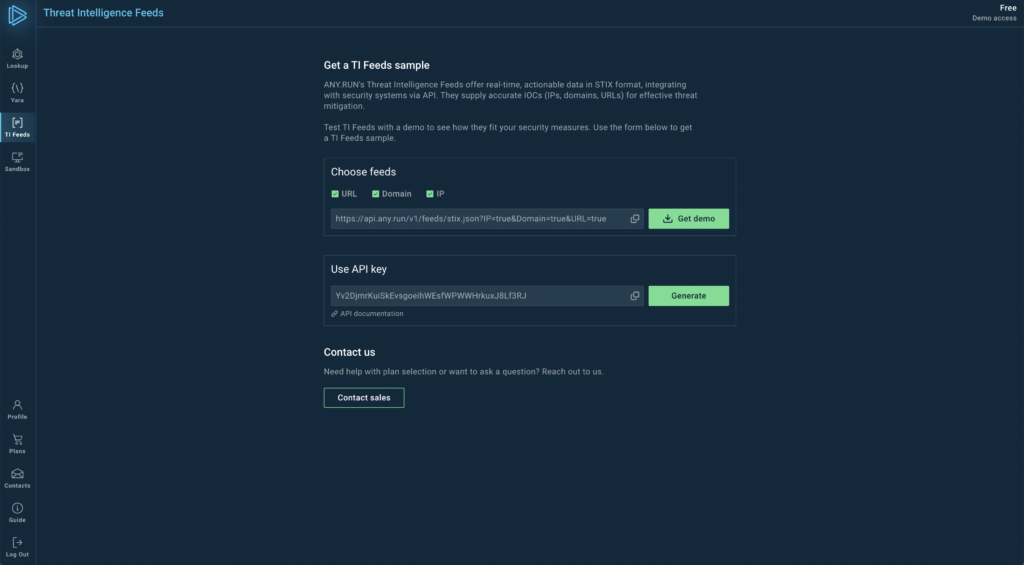
2. TI Feeds demo page: We’ve created a page in ANY.RUN’s Intelligence section where you can request a demo of our TI Feeds. There’s also a corresponding menu item for easy access.
New YARA and network rules
We’ve added YARA rules for Sliver, Growtopia, Phobos and PureHVNC (though, currently it doesn’t detect all samples).
Additionally, we’ve introduced network rules for BlackMoon, CoinIMP Miner, and a new phishing rule.
New extractors and updates
In May, we added new config extractors and updated many existing ones. Here’s a detailed breakdown:
- Added a new extractor for DarkCrystal RAT, the config and its plugins, and made a small overhaul of the old config.
- Added two new extractors for RisePro: extractor one and extractor two.
We’ve also updated the following config extractors and rules:
Signatures
In May, we added a total of 25 new signatures. Here are some highlights:
- NewBot.
- Beast.
- RokRat.
- Cash.
- INC.
- Trinity.
- BlackBasta.
- Zeus.
- Latrodectus.
- BerBew.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.
Try the full power of ANY.RUN for free








0 comments