Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


DarkCloud is an infostealer that focuses on collecting and exfiltrating browser data from the infected device. The malware is also capable of keylogging and crypto address swapping. DarkCloud is typically delivered to victims’ computers via phishing emails.
|
Stealer
Type
:
|
Unknown
Origin
:
|
|
1 November, 2022
First seen
:
|
7 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 November, 2022
First seen
:
|
7 February, 2026
Last seen
:
|

 440
440
 0
0

 2304
2304
 0
0

 4466
4466
 0
0
DarkCloud is a stealer malware written in Visual Basic. The core functionality of the malicious software is collecting and exfiltrating sensitive information from infected machines. The type of data stolen by DarkCloud ranges from user credentials to credit card details in browsers.
The malware has been active since the end of 2022 and has been widely used in attacks in 2023. DarkCloud is sold by its creators on DarkNet forums who also provide customization options, including the additional clipper module, allowing the malware to monitor the content saved by victims to the clipboard.
The most common infection chain for DarkCloud is spam emails, targeting a variety of users. The malware is usually distributed in the form of a malicious attachment. Once downloaded and launched by the user, the malware gets installed on the device and begins its malicious activities.
DarkCloud can engage in the following operations on the infected system:
Additionally, similar to LaplasClipper, DarkCloud is equipped with a crypto swapper, enabling it to replace the user’s crypto wallet addresses with those of the attacker.
The malware can create a Task Scheduler entry in order to gain persistence on the system.
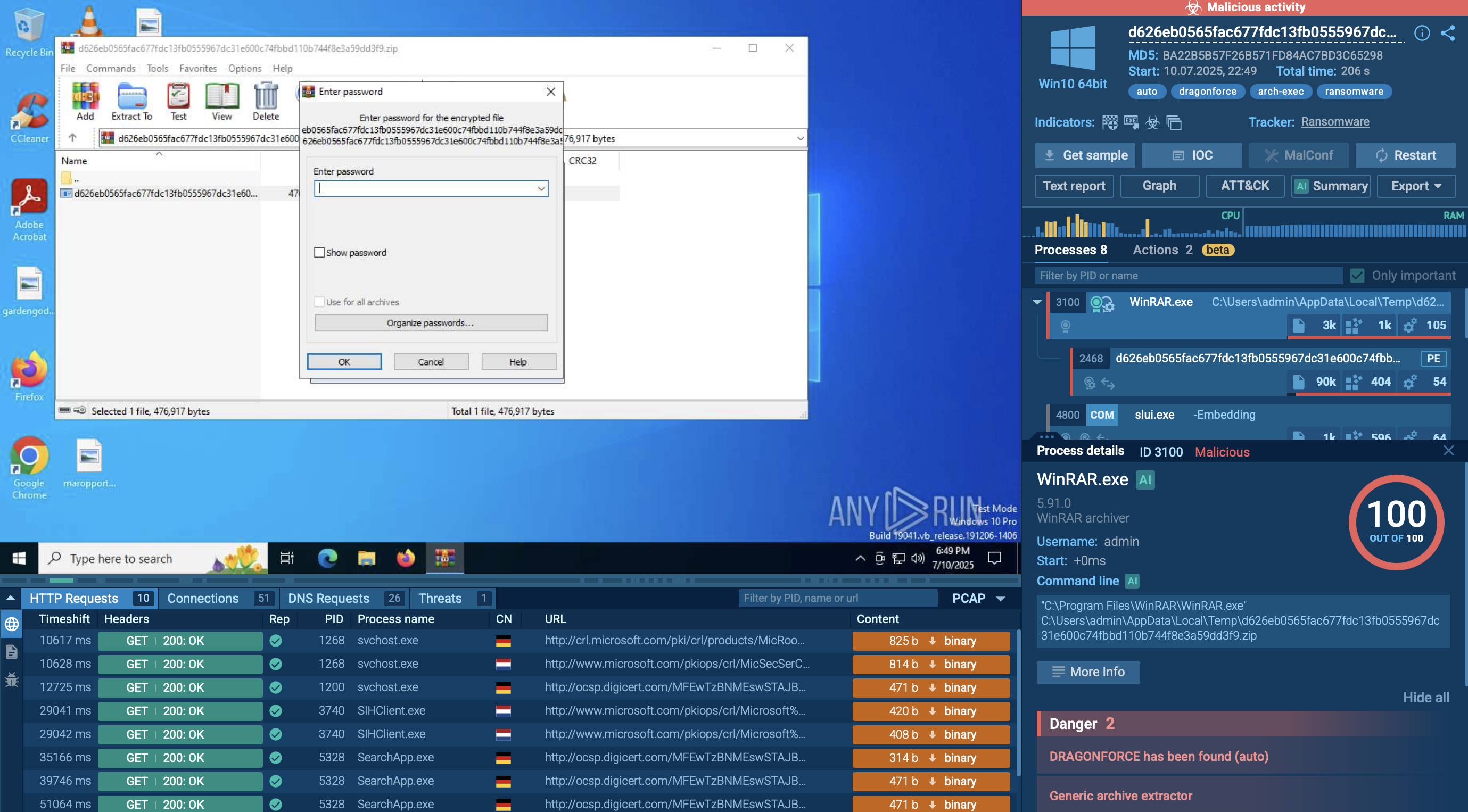
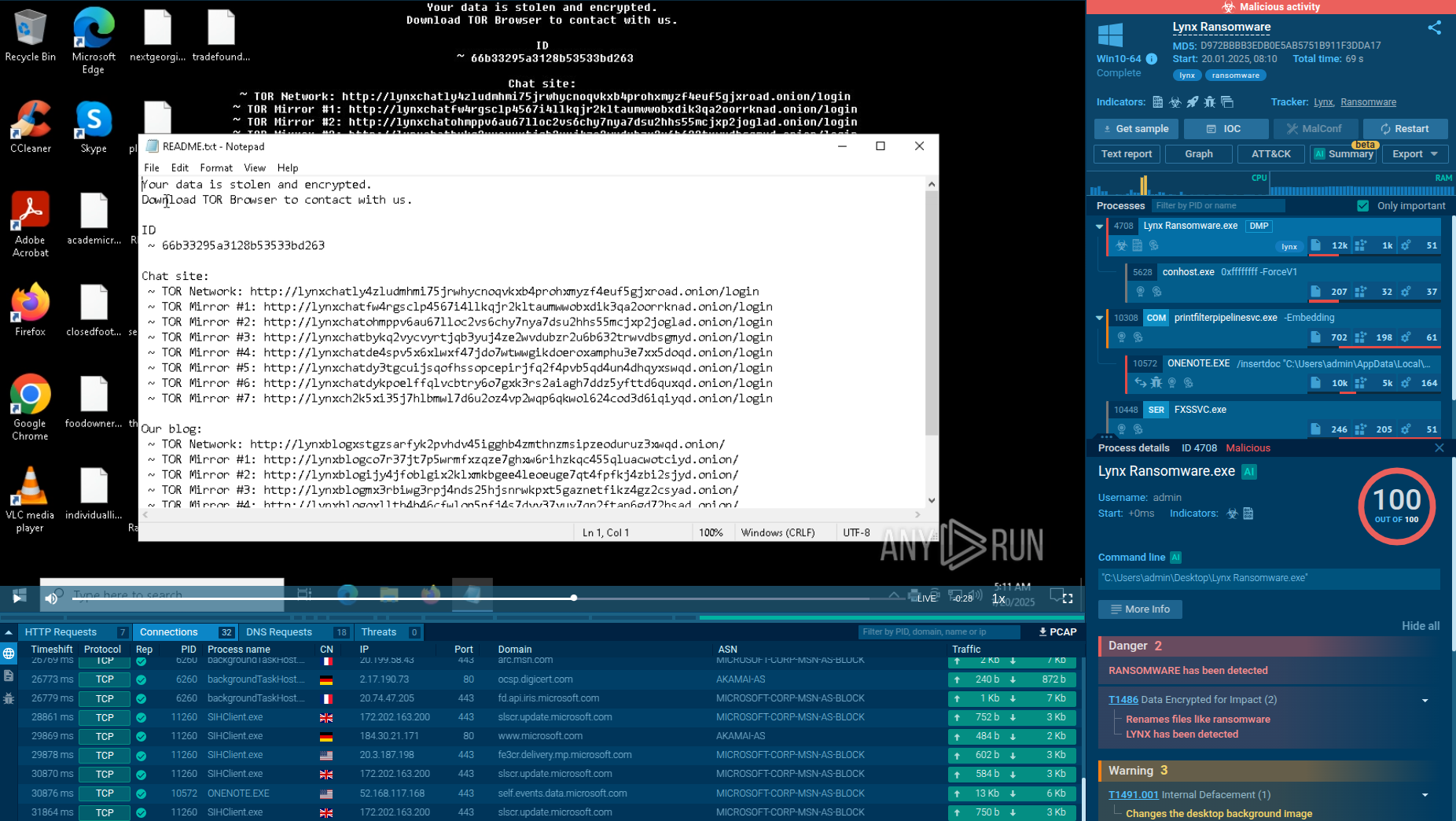
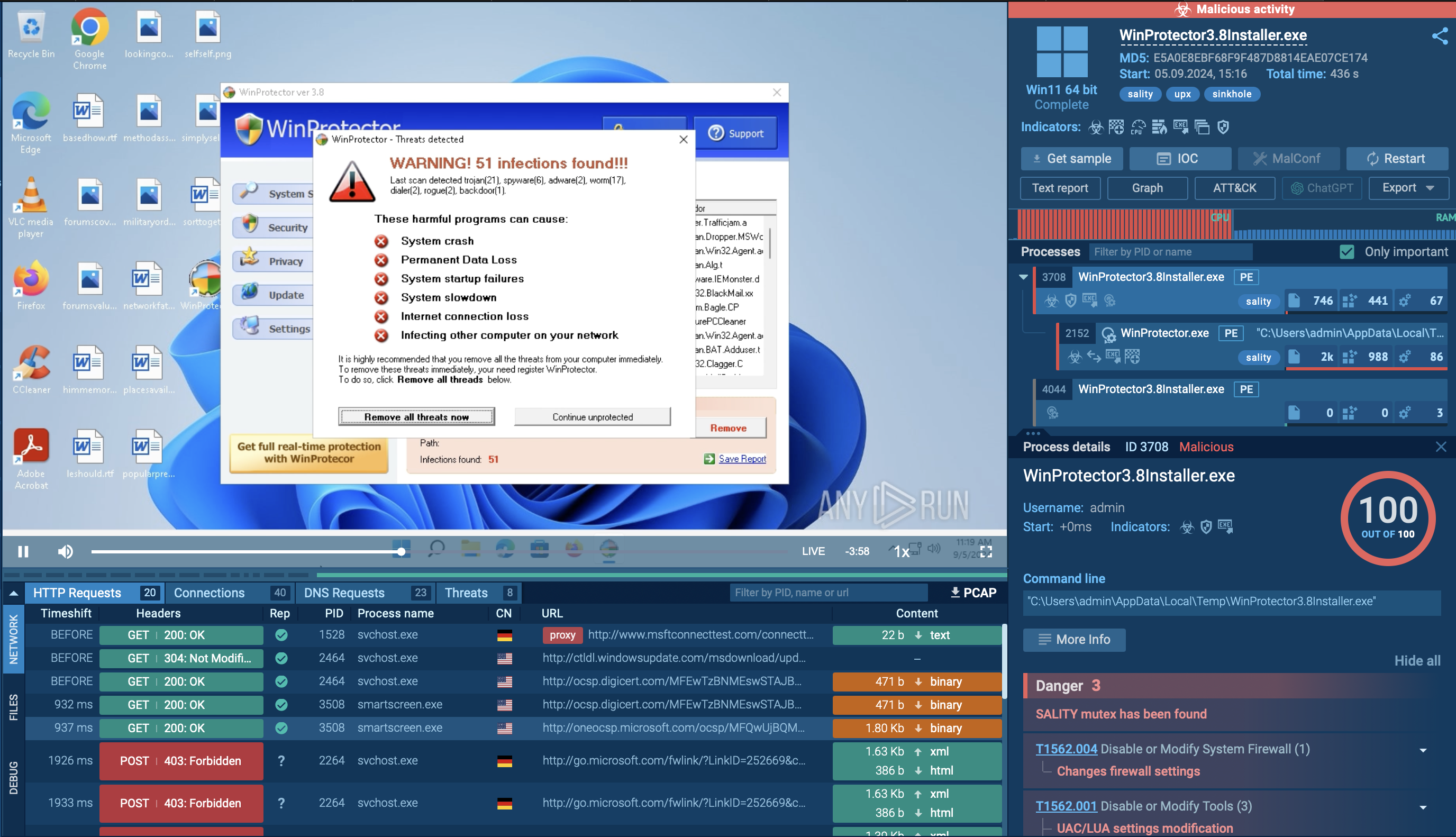
In order to examine the entire execution chain of DarkCloud in more detail, we can upload its sample to the ANY.RUN sandbox.
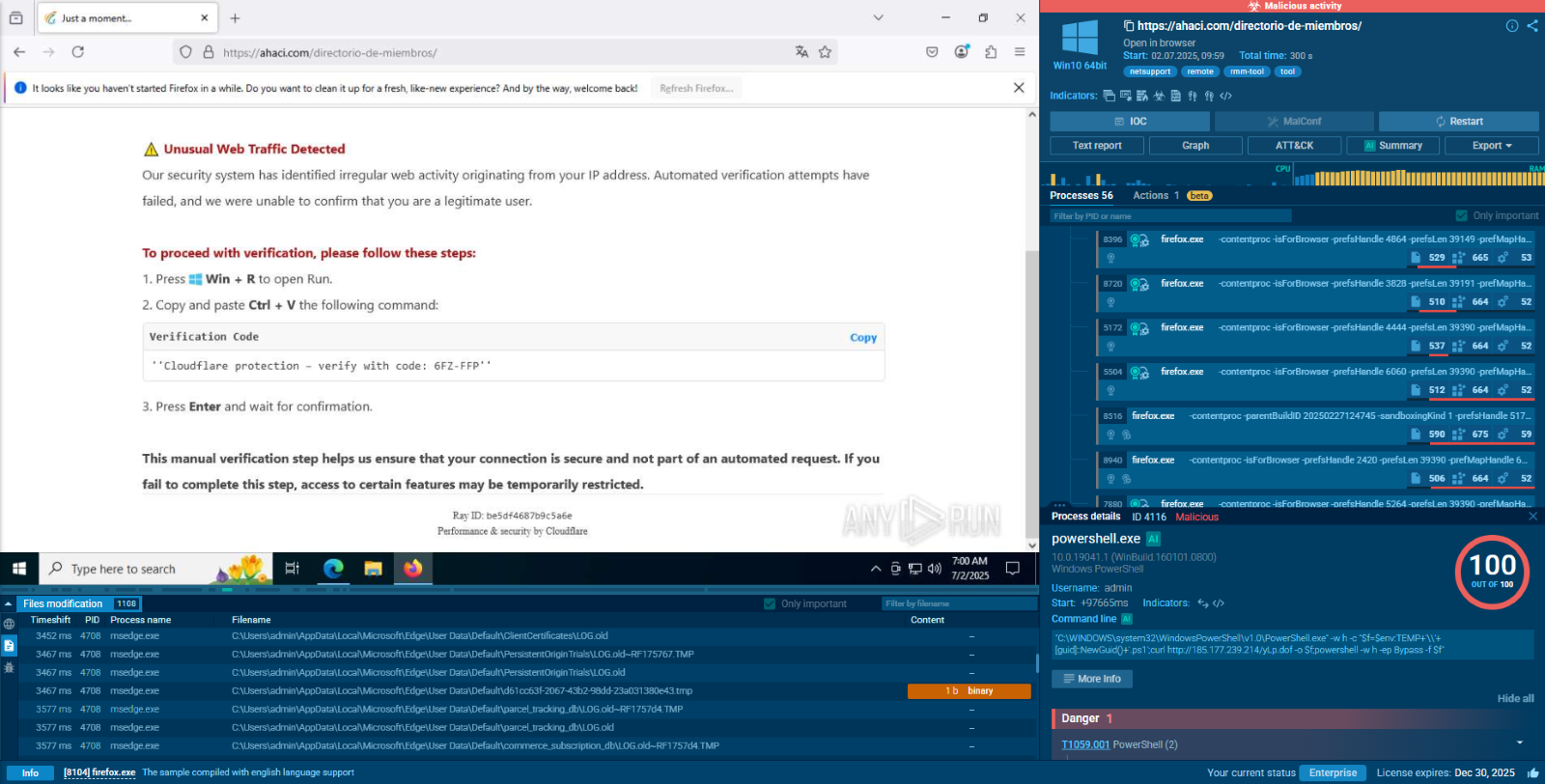
As stealers strive to conceal their activities, the DarkCloud stealer employs a deliberately straightforward execution chain to minimize visibility. Consequently, the infected operating system experiences a limited number of processes, and the malware refrains from utilizing system tools. Once the payload infiltrates the compromised system, it promptly initiates its execution.
The analyzed sample injects the system binary "AppLaunch" and subsequently executes it. After initiating, DarkCloud employs time-based evasion techniques in an attempt to conceal itself from sandboxes. However, it was detected, and the configuration was successfully extracted. It then starts a process executing all malicious activities, encompassing data theft and communication with the Command and Control (C&C) server.
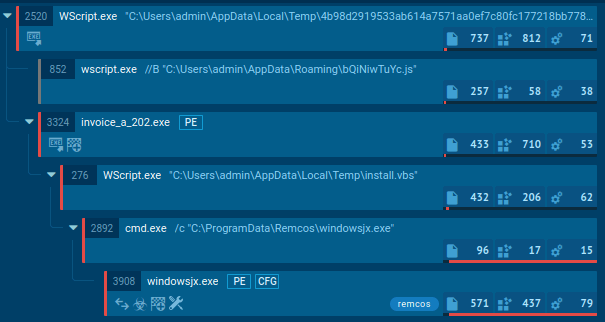
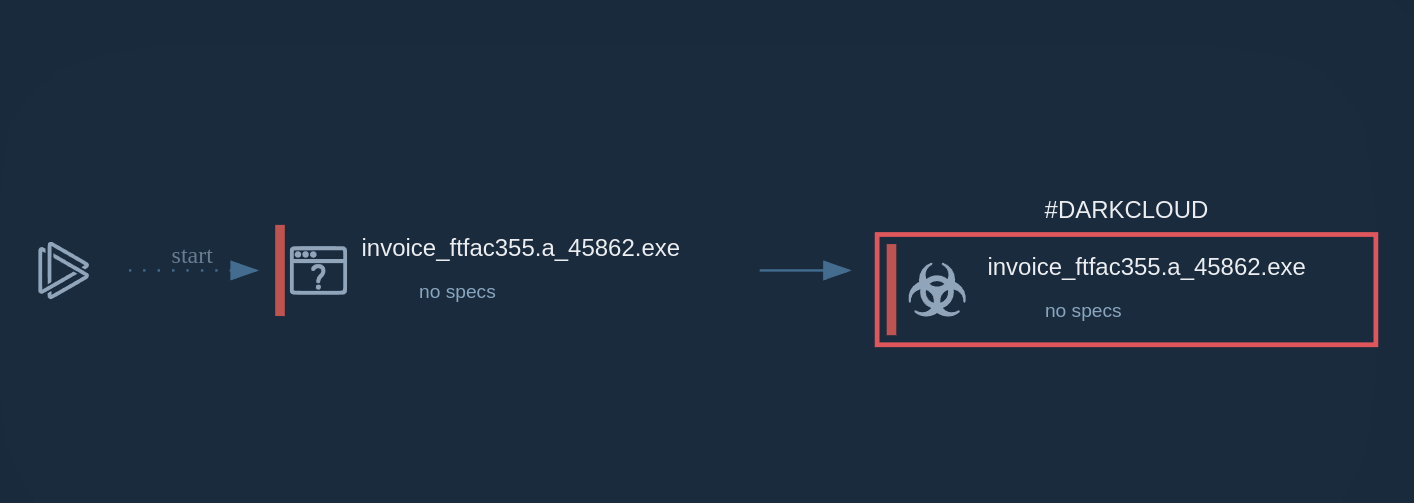 DarkCloud's process graph demonstrated in ANY.RUN
DarkCloud's process graph demonstrated in ANY.RUN
Just like in the case of other stealer malware, such as Formbook and Lokibot, the most common way used by attackers to distribute DarkCloud is via emails. In most cases, criminals employ social engineering and craft their messages to look legitimate. This is why victims often receive fake invoice payment requests and similar emails with files attached to them. Users who fail to recognize a scam end up downloading the malicious attachment and running it on their system, thus triggering the infection process.
In order to avoid falling victim to DarkCloud, it is vital to follow strict security practices. One of them is analyzing suspicious files and links in a malware sandbox. ANY.RUN is a cloud-based service that lets you investigate any email attachment or URL sent to you by an unknown sender and determine whether it poses any risk.
ANY.RUN’s interactive approach to malware analysis enables you to engage with the files and the system just like on your own computer, performing all the necessary actions to execute malicious software fully. The service provides you with comprehensive threat reports that contain details about the attack, indicators of compromise (IOCs), and other relevant information.
Try ANY.RUN for free – request a demo!