Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and threat intelligence analyst. You can find Mauro on X.
From December 20 to 24, 2024, the Quetzal Team identified a phishing campaign targeting the cryptocurrency and fintech sectors. This campaign aimed to distribute a newly discovered stealer malware, which we have named Zhong Stealer, as there were no prior public references to this threat.
The attackers exploited chat support platforms like Zendesk, posing as customers to trick unsuspecting support agents into downloading the malware.
In this article, we’ll use ANY.RUN’s real-time malware analysis capabilities to cover:
- Execution flow: How the malware runs from initial launch to full system infiltration.
- Data exfiltration tactics: How Zhong transmits stolen credentials to a C2 server hosted in Hong Kong.
- Persistence techniques: How it modifies registry keys and scheduled tasks to survive reboots.
A Flood of Phishing Attempts
The attack pattern was simple yet persistent:
- Open a new support ticket from a freshly created, empty account.
- Use broken language and ask for help in Chinese.
- Attach a ZIP file containing screenshots or additional details.
- Insist that support staff open it, growing frustrated when they refused.
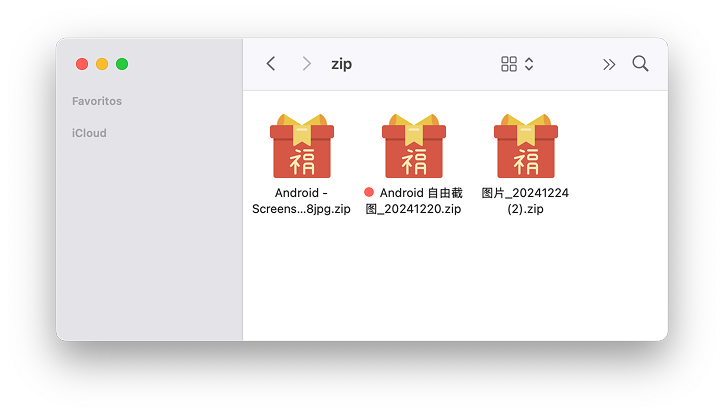
During this period, we managed to collect several suspicious ZIP file samples, all named with Simplified Chinese characters:
- 图片_20241224 (2).zip (Image_20241224 (2).zip).
- Android 自由截图_20241220.zip (Android Free Screenshot_20241220.zip)
- Android – Screenshots2024122288jpg.zip
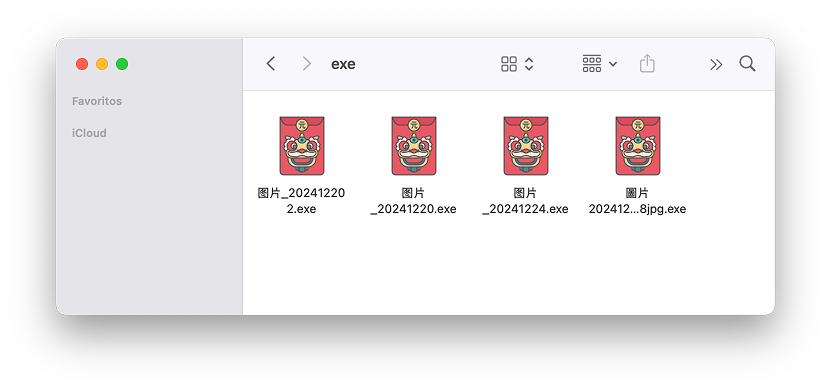
Each ZIP file contained an EXE file inside, which immediately raised red flags:
- 图片_20241224.exe (Image_20241224.exe – Simplified Chinese)
- 圖片2024122288jpg.exe (Image2024122288jpg.exe – Traditional Chinese)
- 图片_20241220.exe (Image_20241220.exe – Simplified Chinese)
The Zhong Stealer Revealed
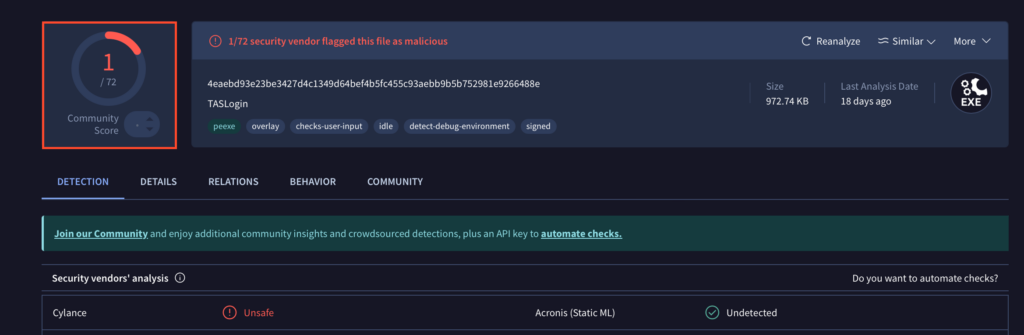
Over four days, we received multiple samples of what appeared to be the same malware. Initially, only one global detection flagged it as “Unsafe,” a vague and generic label.
As time passed, some samples began to receive more global detections, but with a twist: all of them were either generic or driven by heuristic/machine learning/artificial intelligence-powered systems.
However, these detections lacked meaningful naming conventions, making tracking difficult.
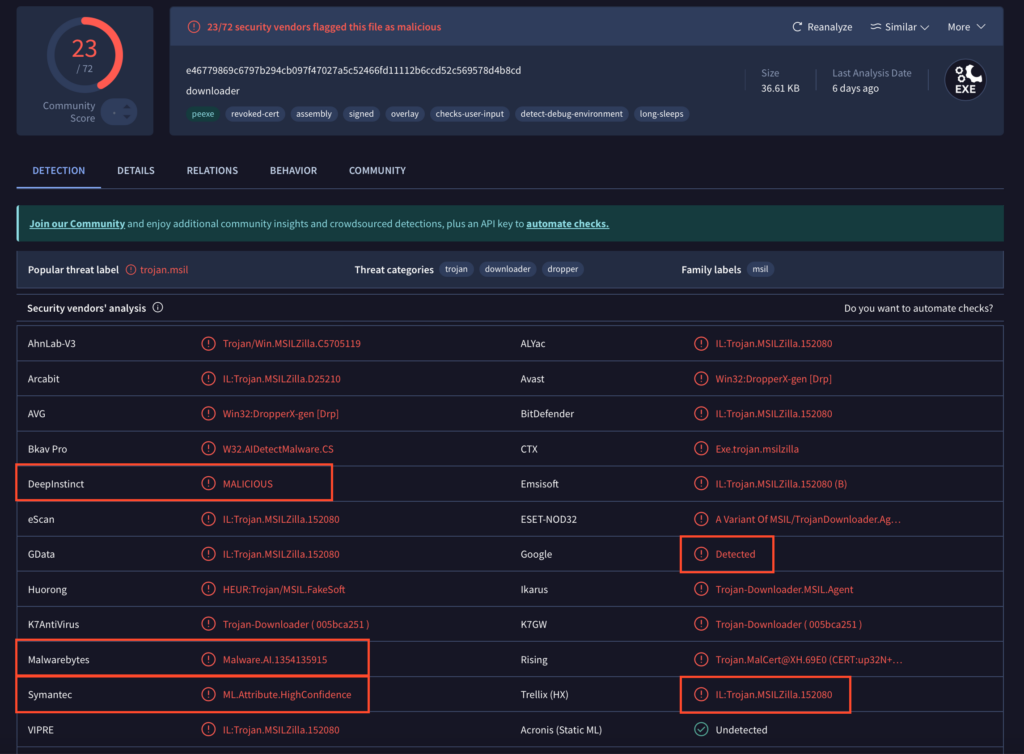
Generic conventions (such as “Win.MSIL”, “Detected”, or “Unsafe”) and AI-generated names (like “AIDetectMalware”, “Malware.AI”, “ML.Attribute.HighConfidence”, “malicious_confidence_90%”, “Static AI”) may be useful for internal classification or as temporary indicators but their lack of specificity makes it difficult to track malware over time or correlate research findings.
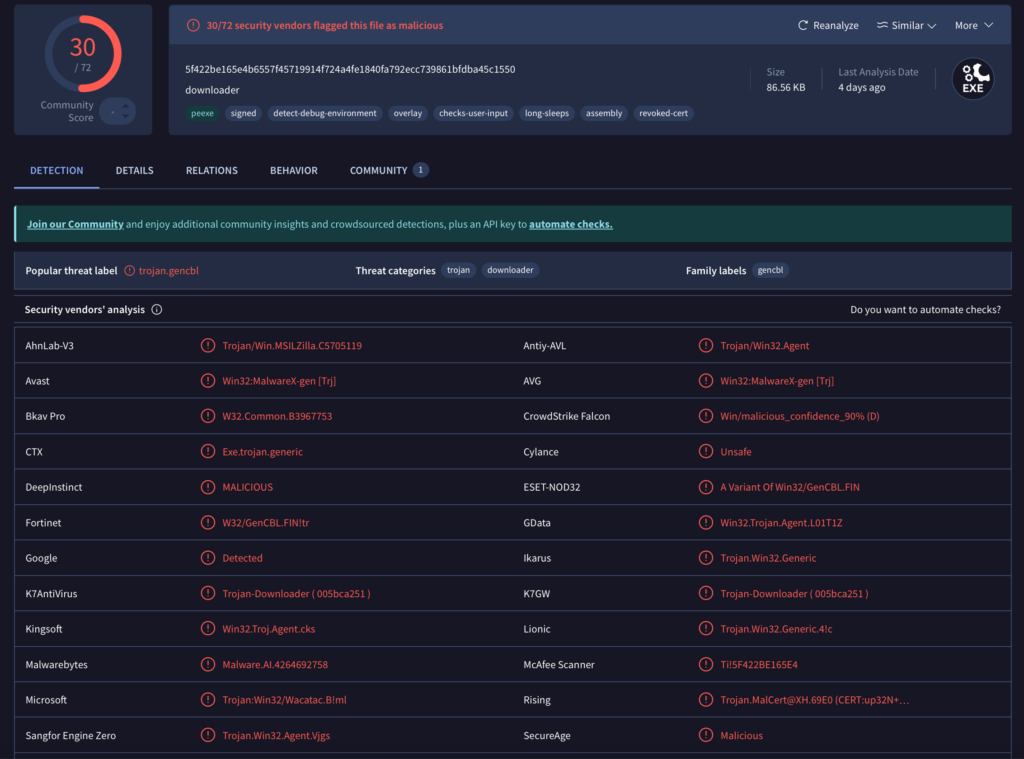
To solve this, we decided to give this malware a proper name: Zhong Stealer, inspired by the email address of the first submitter to hit the ticketing system. From now on, we’ll track all these strains under this family name.
Now that we’ve made a new “friend”, let’s play with it a little bit.
Dissecting Zhong
Running Zhong Stealer in ANY.RUN revealed its behavior almost immediately. Upon execution, it queried a C2 server based in Hong Kong, hosted by Alibaba Cloud.
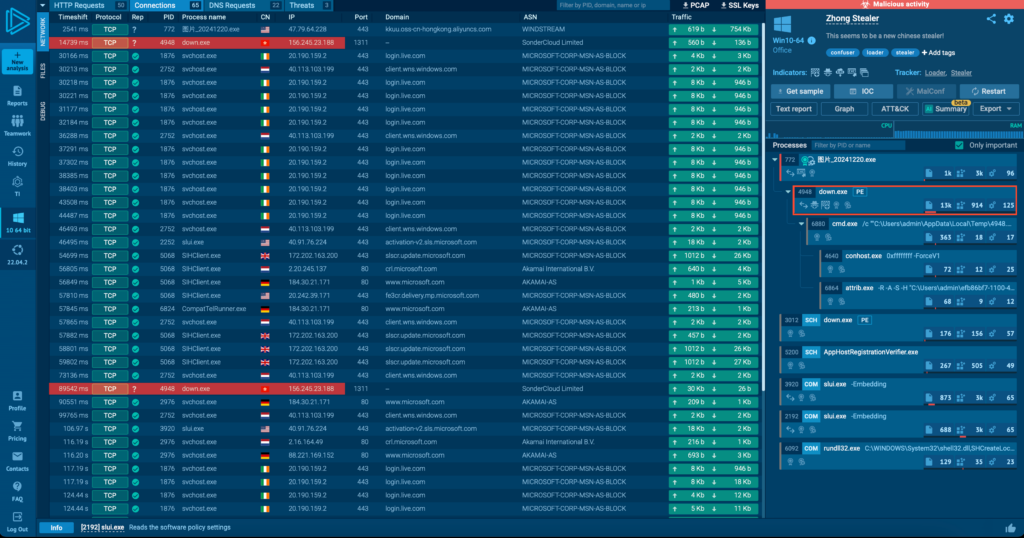
Stage 1: Initial Contact
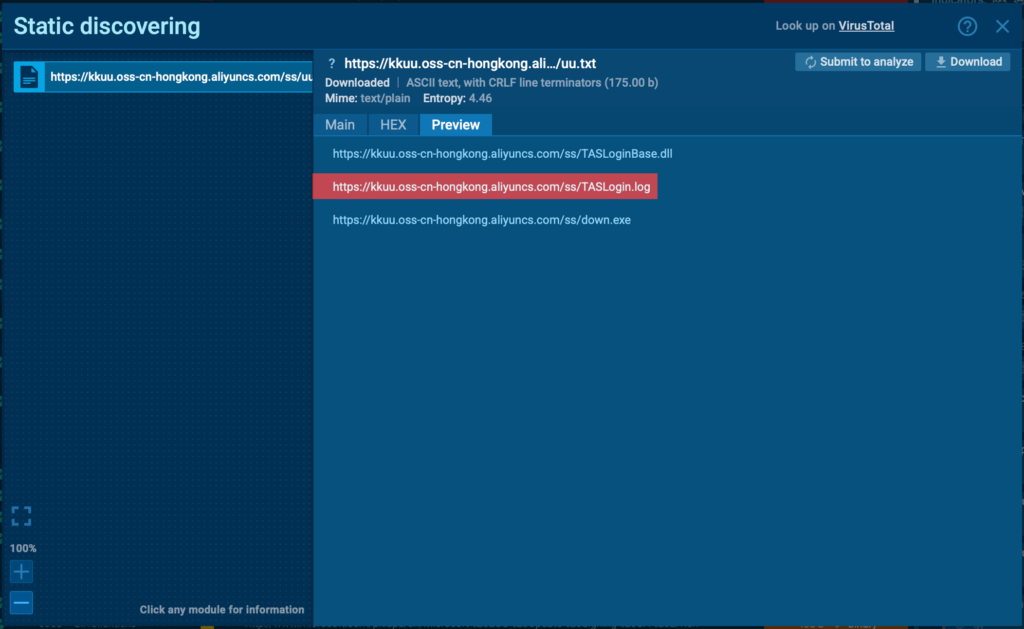
The first action involves reading a TXT file, which serves as an inventory. This file contains links to itself and other components that need to be downloaded.
Stage 2: Downloader Execution
Next, another stage is downloaded: down.exe, a file signed with a previously valid but now revoked certificate from Morning Leap & Cazo Electronics Technology Co., suggesting it was likely stolen. Notably, the file masquerades as a BitDefender Security updater, a deliberate choice that adds an extra layer of deception to evade suspicion.
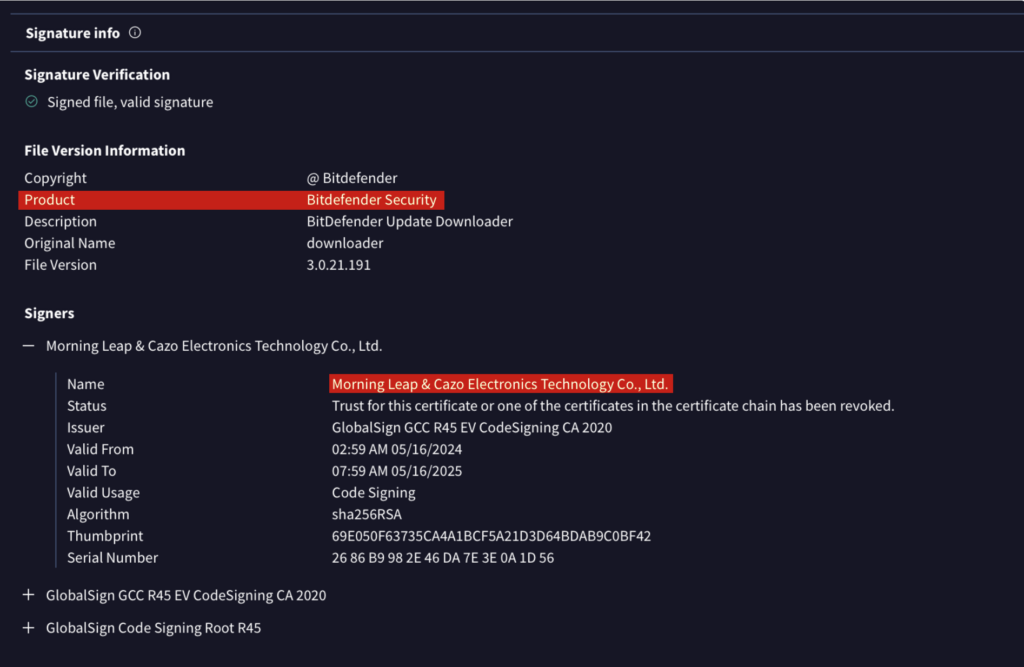
Alongside this stage, Zhong downloaded additional components:
- TASLogin.log (a log file)
- TASLoginBase.dll (a dynamic-link library)
These components helped facilitate execution of the next stage.
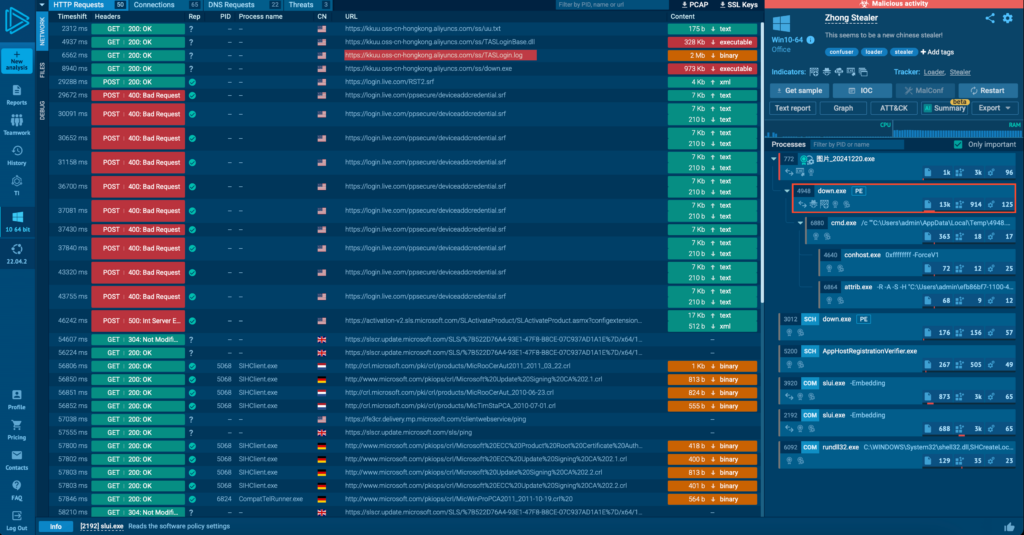
Stage 3: Persistence & Reconnaissance
Once active, down.exe creates a BAT file with a random 4-digit name in the user’s temporary folder (e.g., 4948.bat on my setup). This script sets up the environment by invoking system utilities like Conhost.exe and Attrib.exe to unhide and grant execution permissions to the next step.
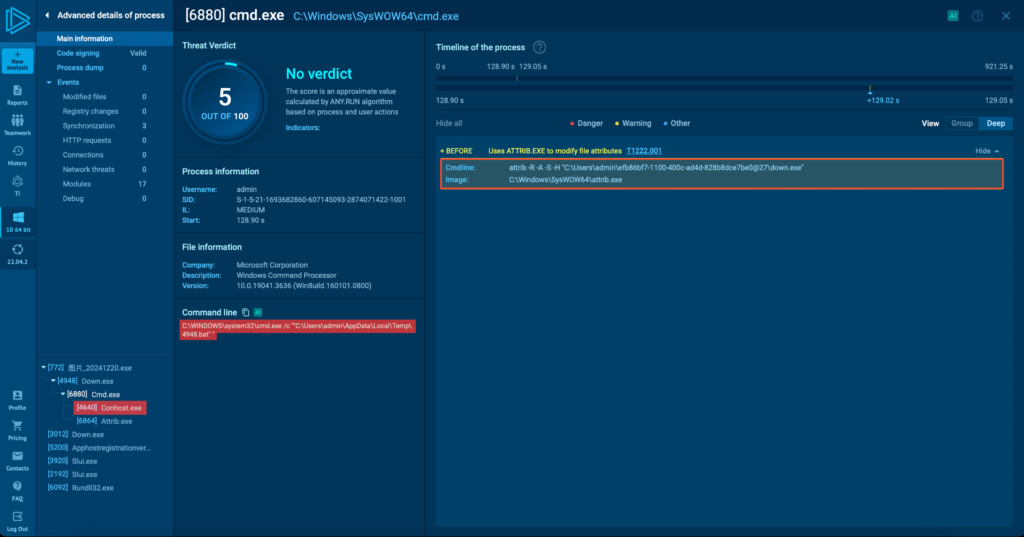
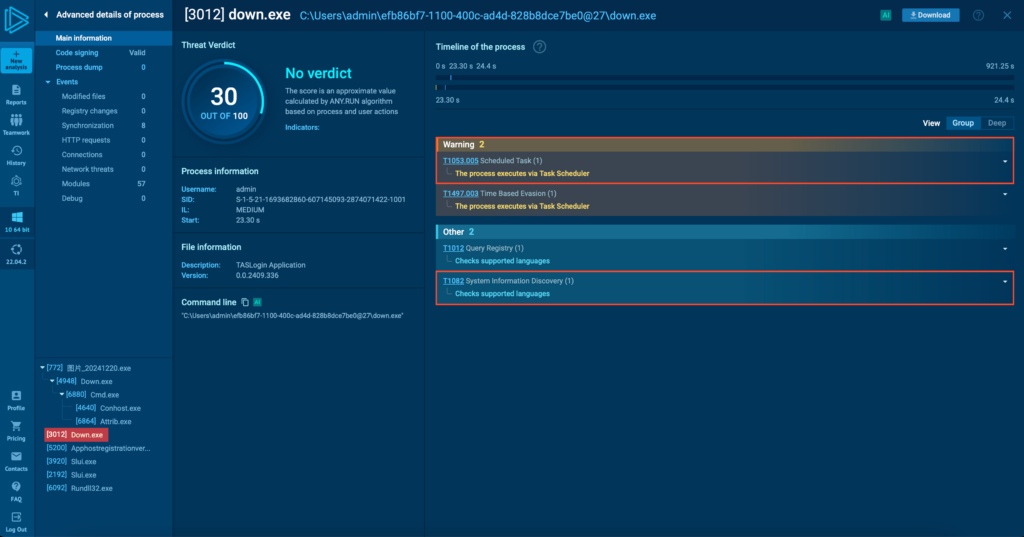
The stealer then queries the system’s supported languages, a tactic often seen in ransomware. It is used to avoid targeting specific regions. It also schedules itself to run periodically via Task Scheduler, which serves as a fallback persistence method, though not its primary one (more on this later).
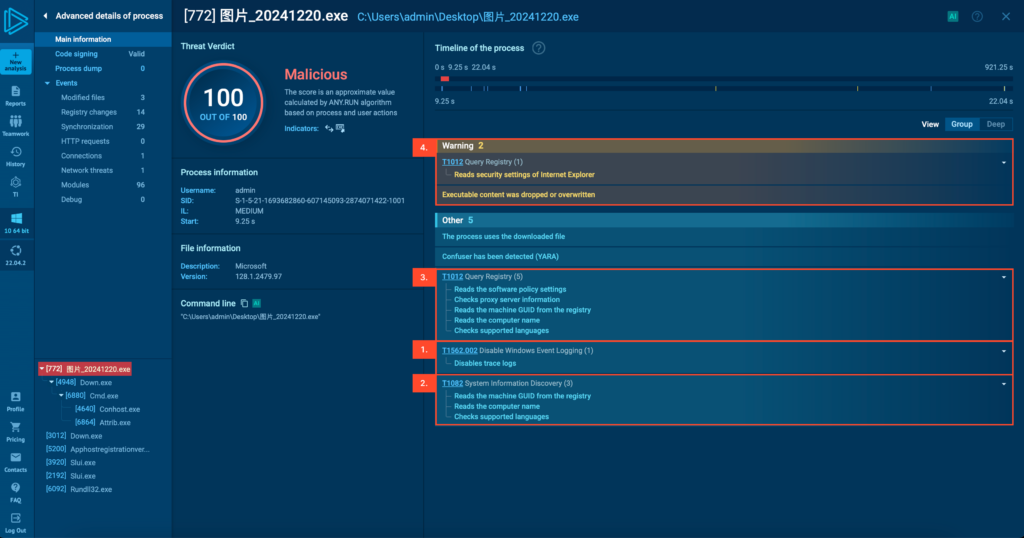
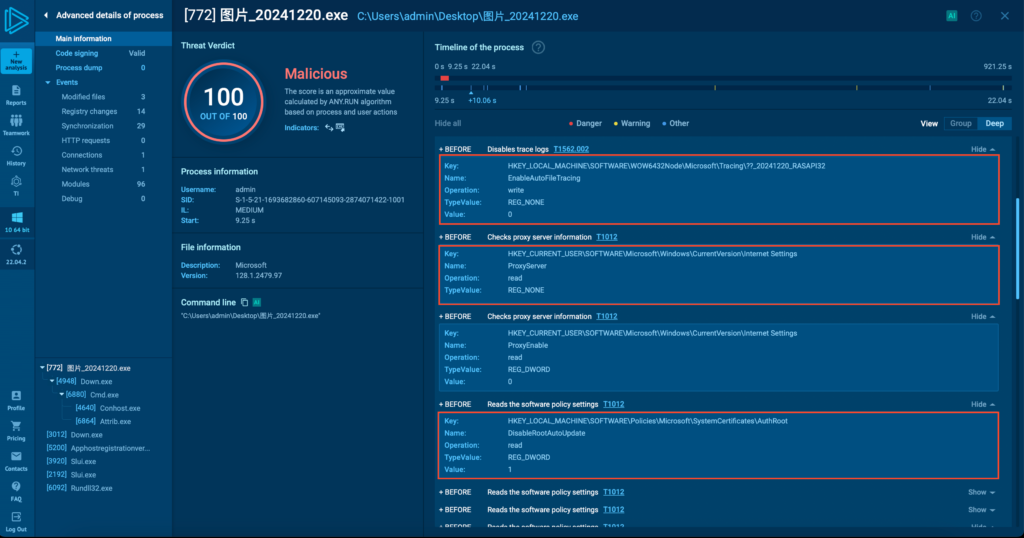
Next, Zhong disables trace logs (point 1 in the image below) and initiates reconnaissance routines.
This includes reading registry keys to collect details such as the machine hostname, GUID, proxies, software policies, and supported languages (points 2 and 3). It also evaluates Internet Explorer/Edge security settings (point 4).

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Stage 4: Credential Theft & Data Exfiltration
With the preparation complete, Zhong moves to its final stage, where it aims to execute a clean attack.
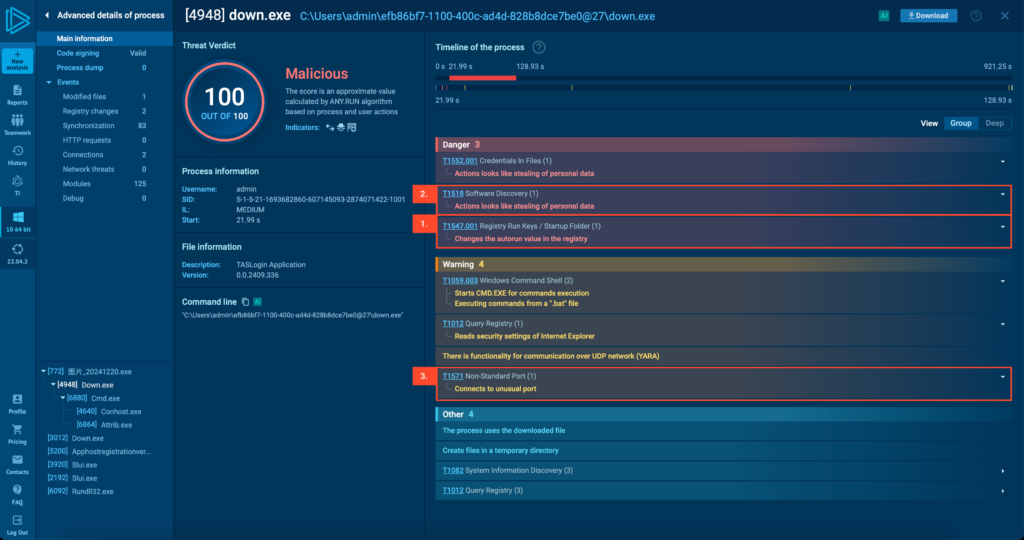
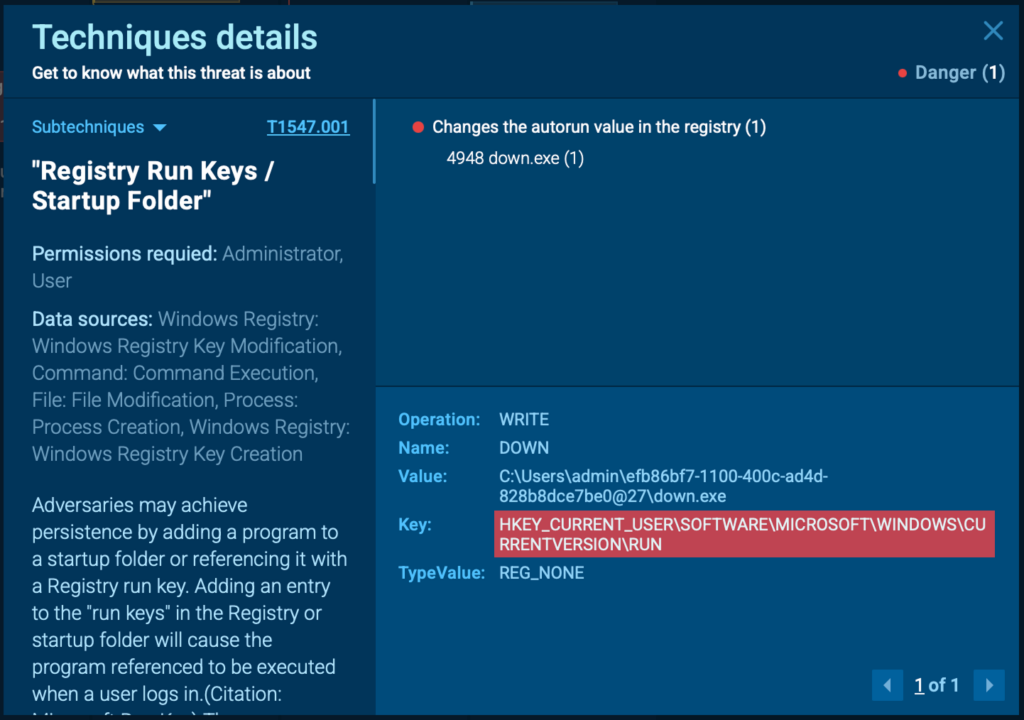
Now, the real action starts. Zhong establishes persistence by adding a registry key (point 1 in the image below) at:
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
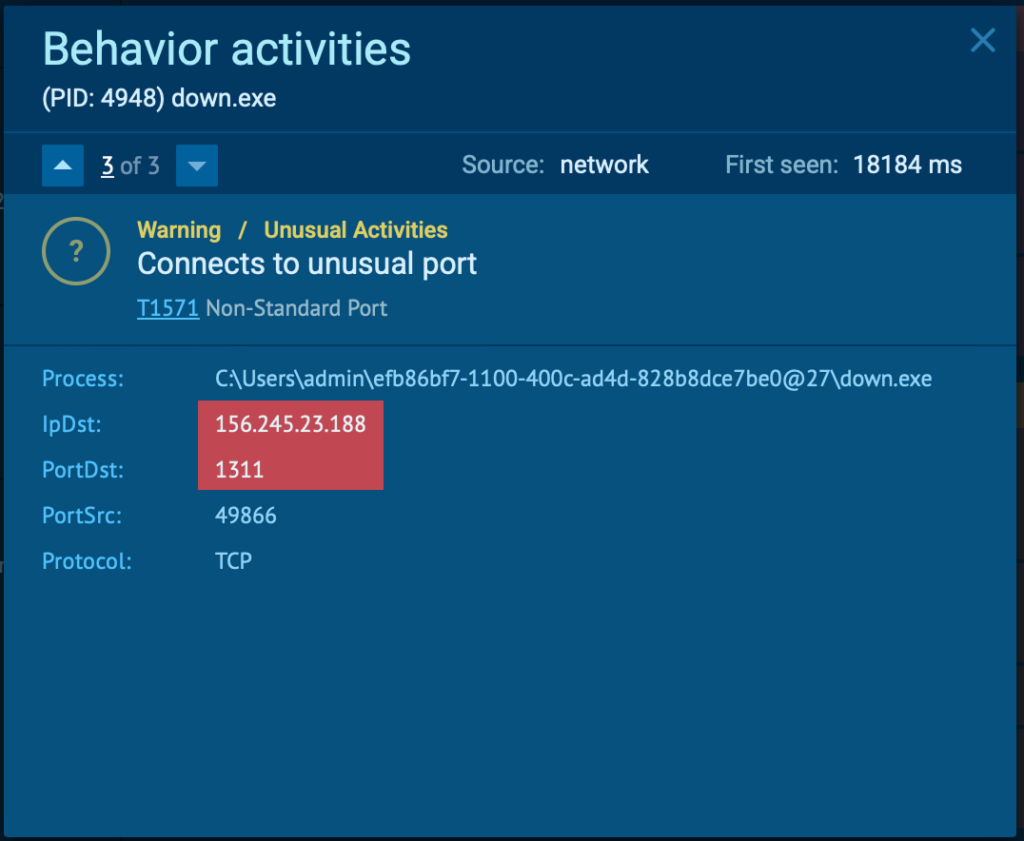
Next, it harvests browser credentials and extension data (point 2) before connecting to its C2 server on port 1311(point 3) to exfiltrate the stolen information.
Let’s break down these actions step by step.
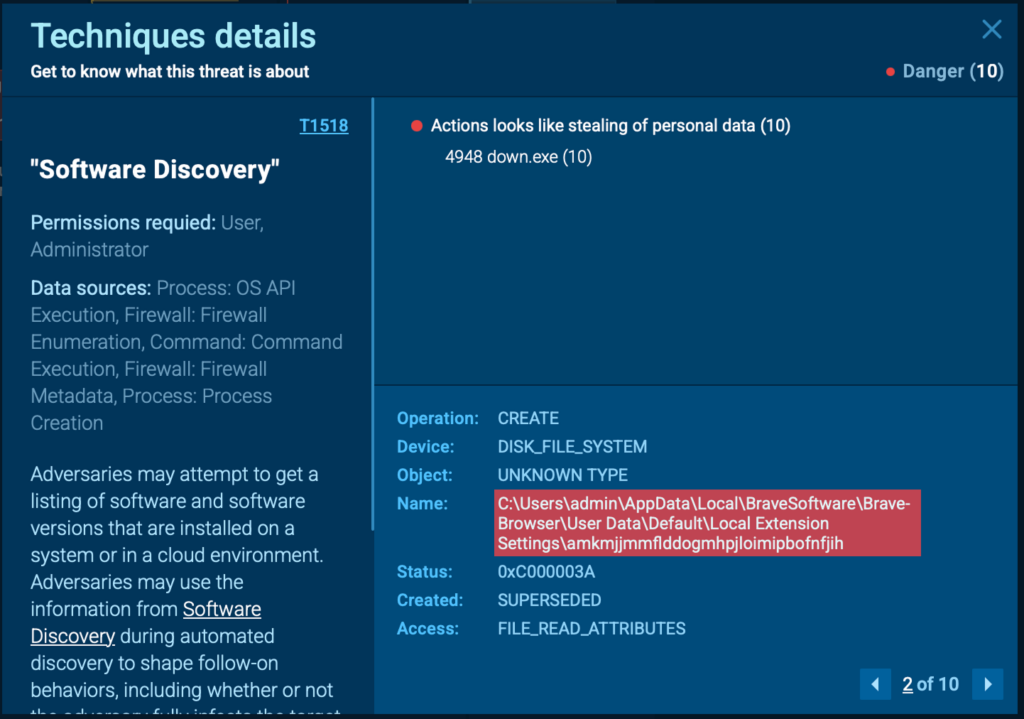
The registry key serves as Zhong’s primary persistence mechanism, with the scheduled task acting as a fallback in case the registry entry is removed. Once persistence is secured, Zhong shifts its focus to harvesting credentials and browser extension data.
Next, Zhong scans browser extensions and credentials, starting with Brave Browser on this setup.
It then moves on to Edge/Internet Explorer, which comes pre-installed on most Windows systems, making them valuable targets for data theft.
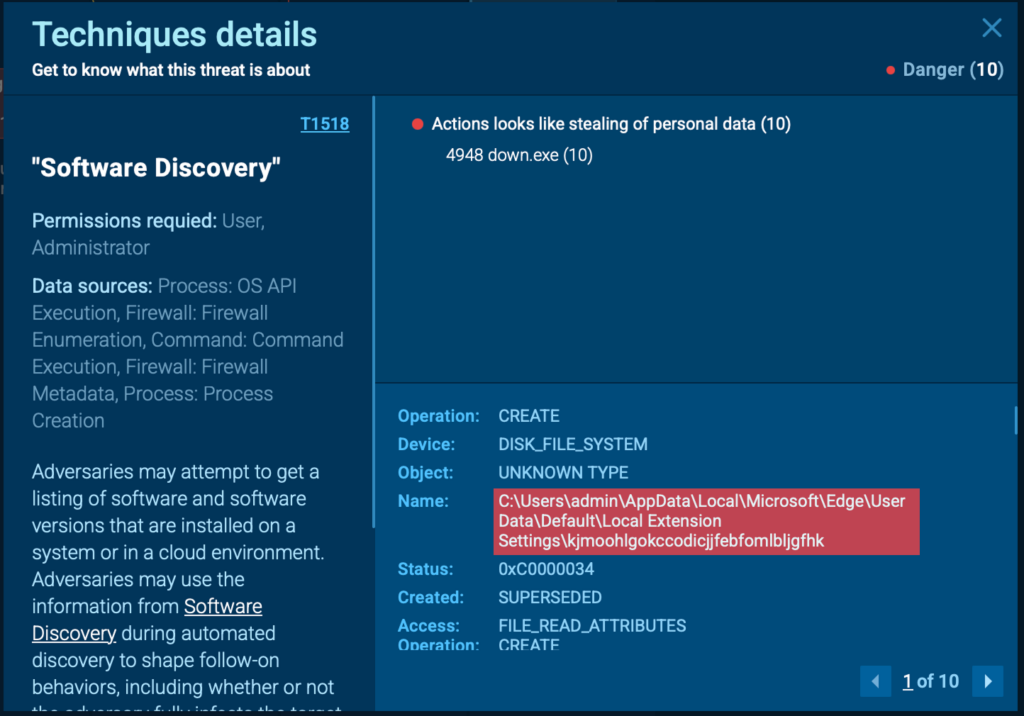
After collecting sensitive data, Zhong contacts its Hong Kong-based C2 server on port 1311 to exfiltrate relevant information.
At this point, the outcome is predictable—Zhong evolves from a mere nuisance into a full-fledged data thief.
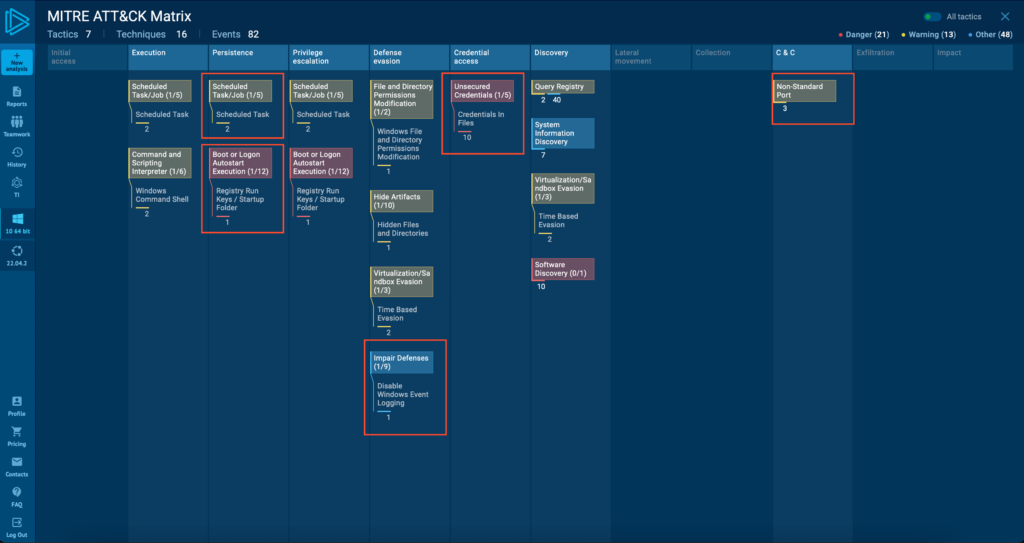
Now, let’s break down its techniques into a clear and structured MITRE ATT&CK Matrix to visualize its full attack chain.
Fortunately, ANY.RUN simplifies this process, mapping out the malware’s behavior step by step for better analysis and threat tracking.
Zhong Stealer’s Tactics & Techniques
This particular piece of malware employs a variety of TTPs which are common, simple, and yet, highly effective:
- Disabling Event Logging (T1562) – Prevents security tools from recording malicious activity, making detection and forensic analysis more difficult.
- Gaining Persistence via Registry Keys (T1547) – Modifies Windows registry settings to ensure the malware automatically runs at startup.
- Harvesting Credentials (T1552) – Extracts saved passwords, browser session data, and authentication tokens from compromised systems.
- Scheduling Tasks (T1053) – Creates scheduled tasks to maintain persistence, ensuring the malware executes even after a system reboot.
- Communicating via Non-Standard Ports (T1571) – Uses uncommon network ports, such as port 1311, to avoid detection and transmit stolen data to a command-and-control server.
You can find more TTPs used by Zhong Stealer in the screenshot below:
How to Protect Against Zhong Stealer
To combat Zhong Stealer and similar social engineering-based malware, security teams must adopt proactive detection and analysis strategies. Traditional antivirus solutions often fail to recognize stealthy threats, but with ANY.RUN’s Interactive Sandbox, organizations can identify, analyze, and block malicious activity in real time before it causes harm.
Here’s how to protect your organization from Zhong Stealer:
- Train customer support teams to recognize phishing tactics and avoid opening suspicious file attachments in support chats.
- Restrict ZIP file execution from unverified sources and enforce zero-trust security policies to prevent unauthorized file access.
- Monitor outbound network traffic for suspicious C2 connections, especially to non-standard ports like 1311, a key indicator of Zhong Stealer’s activity.
- Use ANY.RUN’s real-time analysis to safely detonate unknown executables, observe their behavior step by step, and extract critical IOCs before the malware can spread.
With ANY.RUN’s in-depth behavioral analysis, security teams can stay ahead of evolving threats like Zhong Stealer and prevent cybercriminals from using social engineering to bypass traditional defenses.
Final Thoughts
Zhong Stealer’s campaign is a prime example of how social engineering and persistent phishing tactics can be used to distribute malware. By targeting customer support teams, the attackers attempted to bypass traditional security measures and exploit human trust.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
IOCs
FileHash-MD5:778b6521dd2b07d7db0eaeaab9a2f86b
FileHash-SHA1:ce120e922ed4156dbd07de8335c5a632974ec527
FileHash-SHA256:02244934046333f45bc22abe6185e6ddda033342836062afb681a583aa7d827f
FileHash-SHA256:1abffe97aafe9916b366da57458a78338598cab9742c2d9e03e4ad0ba11f29bf
FileHash-SHA256:4eaebd93e23be3427d4c1349d64bef4b5fc455c93aebb9b5b752981e9266488e
FileHash-SHA256:dd44dabff536a1aa9b845dd891ad483162d4f28913344c93e5d59f648a186098
FileHash-SHA256:e46779869c6797b294cb097f47027a5c52466fd11112b6ccd52c569578d4b8cd
FileHash-SHA256:5f422be165e4b6557f45719914f724a4fe1840fa792ecc739861bfdba45c1550
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/TASLogin.log
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/TASLoginBase.dll
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/down.exe
URL:hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/uu.txt
email:zhongmaziil992@outlook.com
hostname:kkuu.oss-cn-hongkong.aliyuncs[.]com
IPv4:156.245.23.188
IPv4:47.79.64.228
Mauro Eldritch
Mauro Eldritch is an Argentinian-Uruguayan hacker, founder of BCA LTD and DC5411 (Argentina / Uruguay). He has spoken at various events, including DEF CON (12 times). He is passionate about Threat Intelligence and Biohacking. He currently leads Bitso’s Quetzal Team, the first in Latin America dedicated to Web3 Threat Research.
2 comments










some IOC sha256 is only 64 characters, it should be 65 right?
Hi Christopher,
You are absolutely correct. Thank you for pointing it out. The error should be fixed now.
Best,
The ANY.RUN team