The human factor contributes at least a little to every successful cyberattack. In many cases, it is even the main cause of the breach. You’ve probably seen a lot of similar headlines on the news recently:
Here’s another one:
And another one:
Despite all the super-sophisticated technology that attackers now have at their disposal, social engineering attacks are still an integral — and arguably the most reliable — driver behind hacking.
In fact, CISCO has found that about 90% of breaches happen because of social engineering. Approximately 70% of all attacks are a combination of phishing and hacking. And the number of phishing attacks worldwide is growing by as much as 400% year-over-year.
But what does social engineering mean, exactly, and why do hackers prefer this approach over purely software-based attack vectors?
What is social engineering?
Social engineering can be defined as a way of psychologically manipulating people to perform certain actions. Usually, to disclose confidential information or install malware. Here are some quick examples of social engineering attacks:
- A fraudulent email containing a malicious attachment imitating an invoice
- An SMS from a bank about an ostensibly compromised account
- A fake login webpage that steals credentials
By exploiting our cognitive biases like fear, familiarity or sense of urgency, attackers disarm us and lower our guard. Social engineering attempts are carefully designed to exploit built-in human biases, including but not limited to:
- Authority. Research showed that we are more likely to believe an authority figure, regardless of the context. This is why scammers so often pose as regulators.
- Friendship We usually trust people we like or know well. To take advantage of this, attackers may try to impersonate our acquaintances.
- Fear of Missing Out. We tend to feel apprehensive when we think we are about to miss something that could make our life better. The scammers use this to create a sense of urgency and scarcity.
- Intimidation. Attackers may use intimidation to control the victim. Techniques range from threatening to report wrongdoing to the manager to much nastier things.
But there is another trait that often leads to security breaches. And in a corporate IT environment, it’s more common among people on certain teams: a lack of knowledge. Specifically — being a bit computer illiterate.
If you are not aware that what you are doing is dangerous, it can create a false sense of security that will make you more gullible. That is why HR professionals and accountants are more likely to be spear-phishing victims than programmers.
We are remarkably bad at detecting well-designed phishing attempts. One study showed that 97% of people can’t tell a well-planned phishing email from a real one.
The idea of using psychological manipulation to exploit heightened emotions is probably as old as crime itself. ILOVEYOU malware was one of the first malicious programs to use social engineering and massive email spam campaigns. Unfortunately, we’ve never learned how to avoid scams that great, especially on the internet.
About 30% of recipients open phishing emails, one study claims, and roughly 40% of employees admit to engaging in unsafe online behavior, such as clicking on suspicious links from their workstation or downloading questionable files.
Here’s how social engineering can impact your business
Security breaches have devastating consequences, especially in healthcare, where the cost of remediation has been the highest for any industry for several years in a row. Here are a few quick facts based on statistics that illustrate why social engineering is such a big threat:
Email may be the most used attack vector, but it’s not the only one. Here are 12 techniques that hackers use:
12 types of social engineering attacks
You are probably familiar with phishing and spear phishing, but that’s just the tip of the social engineering toolkit. Here are some more attack vectors that hackers use:
12 Social Engineering Types
| Spam Phishing A widespread attack that cajoles users into disclosing sensitive info | Spear Phishing A targeted social engineering attack which is planned meticulously around one user | Whaling A Spear Phishing attack aimed at a celebrity or a high government official |
| Angler phishing Attackers impersonate a brand on social media in a DM conversation. | Search engine phishing A fake website is placed at the top of the search results through ads or genuine SEO | In-session phishing Website pop-ups attempt to deceive or scare users into performing an action |
| Baiting A “too good to be true” offer directing to a fake or infected webpage | Physical breaches Crooks infiltrate unauthorized areas by posing as someone with access rights | Pretexting Bad actors impersonate a brand or an authority figure to gain trust |
Vishing and Smishing The same as phishing, but done in voice calls or SMS messages respectively | Scareware A malware that uses scare tactics to make you install other malware | URL phishing Links to compromised websites are delivered by email or with malicious ads |
How to protect your business against social engineering?
While it’s true that some attacks are so well thought out that they’re nearly impossible to catch, most of them are actually pretty primitive. And attempts at social engineering hacks can be spotted from afar if you know what to look for. The problem is that many people don’t.
According to one study, 90% of organizations do not provide cybersecurity training to their employees, and this is exactly the type of ignorance that attackers thrive on.
By extension, holding security training seminars and raising awareness of the signs of phishing is the best countermeasure. But here are a few more ways organizations can boost security. You can reduce potential exposure with spam filters, manage risk by restricting employee access to information, and drastically reduce the chance of malware infection by checking suspicious files and links with ANY.RUN malware sandbox.
- Spam filters. About 1 in every 99 emails is a phishing attack. It’s impossible to stop them all, but spam filters can reduce the number of phishing messages reaching your inboxes by about 85%.
- 2FA. Scammers love to hunt for login credentials to gain unauthorized access. Having two-step verification on multiple devices will stop them, unless they somehow manage to get hold of the secondary authentication gadget.
- Restricting access to information. Establish and enforce policies around accessing data. Make sure your user base isn’t just floating around in some analytics software, where anyone can view it.
- Cross referencing information. For example, if you receive an email with an unexpected invoice, verify its authenticity by calling the company that supposedly sent it.
- Using ANY.RUN to rule out phishing attempts. The ANY.RUN interactive malware sandbox can automatically analyze any file or link and tell you if it’s malicious. Also, you can use it to view network traffic and find out what information hackers are after and where they’re transmitting it to.
Using ANY.RUN to stop social engineering attempts
Let’s look at how we can use ANY.RUN to detect malicious emails and URLs, illustrated with a couple of real-life examples of social engineering attacks.
Identifying a fake Microsoft login page
Creating a fake website that masquerades as a login portal of an established brand is an effective way to steal credentials. Forget to cross-check authenticity, and your details are already in the hands of the crooks.
In this sampe, attackers have copied a Microsoft Office login page. After the user fills out the form and submits the login and password, thinking they’re about to sign into their Microsoft account, what really ends up happening is that the data is sent over to the hackers. To make sure no tracks are left, the fake portal then redirects to the real Microsoft website. This scheme is extremely easy to fall for.
But it’s also easily avoidable if you’re using ANY.RUN. Because our service is interactive, you can fire up a new sandbox and complete the suspicious form, as if you were using a real PC. Just make sure to type some gibberish into the fields. After clicking on the ‘Next’ button, the sandbox detects an outgoing request that passes login information to a shady server. Then a warning about “malicious activity” appears in the upper right corner. And by enabling the MITM Proxy, we can even see what information the attackers were trying to steal.
Checking malicious email attachments
About 90% of hacks use malicious emails to breach the system. This is the phishing attack vector that you will have to deal with most often. Luckily, it’s easy to defend against it by checking attachments with ANY.RUN.
In this example, we’ve received a spear phishing email which contains an infected archive. Download it without checking, and our system will be compromised with an Agent Tesla trojan the moment we click on it. So, let’s run it through ANY.RUN instead.
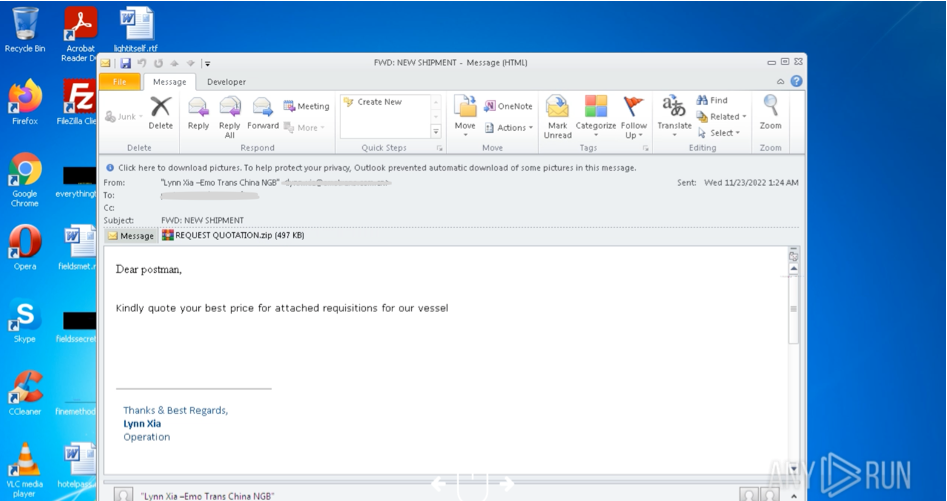
With ANY.RUN malware sandbox, we can open the letter, and interact with its attachments, which contain executable files of the trojan. We can also view the config file, and see the nested malware. A free account allows us to complete all analysis steps, and collect MITRE ATT&CK indicators. The analyst can safely execute the malware in the virtual sandbox and the whole process only takes a couple of minutes. And once the malware runs, ANY.RUN automatically flags it as Agent Tesla.
In both examples, we checked suspicious content before trusting it and interacting with it on the main system. This is a crucial habit to adopt. But it’s still not realistic to clear every file you receive or analyze every existing URL for fraud. So how do we know what’s worth scrutinizing and what isn’t?
Here are a few pointers:
- Bad grammar. Poorly executed phishing campaigns will be laden with spelling errors and botched grammar.
- Unexpected correspondence. Did you receive an invoice that you didn’t expect at all? There’s a good chance it’s fraudulent.
- Heightened emotions. Check yourself for signs of FOMO or fear. Attackers usually play on urgency and intimidation to get you to lower your guard.
- Is it too good to be true? Then it probably is. Check before proceeding with it further.
Wrapping up
Social engineering is unlikely to ever stop working. As honest people, we all tend to trust what we see rather than suspect something is wrong around every corner. Attackers know this too, and take advantage of our decency in elaborate phishing campaigns.
That said, there are many ways to reduce the risk of falling victim to such scams — proper online hygiene is at the top of the list, as is making sure the content we interact with is safe before trusting it completely.
Be vigilant on the web, clear suspicious links and files with ANY.RUN, and, most importantly, stay safe online!
Questions and answers (Q&A)
- What is social engineering attack?
In cybersecurity, a social engineering attack is an attempt to use psychological manipulation to breach a secure system or perform a malicious action.
- What is the best countermeasure against social engineering?
People with limited computer knowledge fall victim to social engineering most often, so raising awareness about types and dangers of phishing is the best countermeasure. Another important defense line is creating a policy of checking suspicious content you engage with it.
- How do social engineering attacks happen?
Having studied the victim, attackers make contact and gain trust. They then coax the victim into committing a compromising act. Finally, they back off and cover their tracks. The entire process can take months or happen in a single email.
- What social engineering principle frightens and coerces a victim by using threats?
Intimidation. Attackers can intimidate the victim by threatening to lose their job or using incriminating data that they may have previously collected using spyware.
- How to protect against social engineering attacks?
You can protect yourself against social engineering by staying vigilant, double-checking information before trusting it, using antivirus software, and sandboxing suspicious files or links.
1 comments







Social Engineering is the main vulnerability of all cyberattacks. People cannot be protected by anyone except themselves.