On the 4th of May 2000, a new malicious program was released into the wild — ILOVEYOU, also known as Loveletter and Lovebug. We didn’t know it then, but this worm would forever change how we view malware, causing devastating damage.
Twenty years ago the internet was different. Then, people were not used to receiving tons of spam emails. It is not surprising then, that one of the first malware to use social engineering and massive email spam campaigns would cause nothing short of a malware pandemic.
In the end, the world has suffered billions of dollars in losses, up to 80% of computer networks in select countries become infected and the malware itself has acquired a Guinness book record for causing the most damage.
ILOVEYOU behavior
ILOVEYOU was a computer worm designed to spread through emails of Microsoft Outlook users. First victims of this malware received an email with a subject reading “ILOVEYOU”. An email like this was hard to miss in an uncluttered mailbox. Attached was a file, named LOVE-LETTER-FOR-YOU.TXT.vbs.
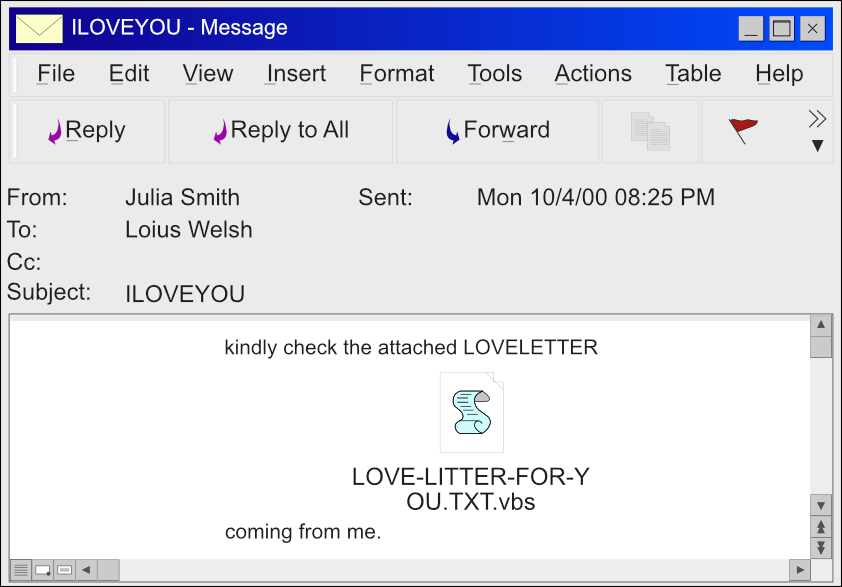
The malware would run after the unsuspecting victim downloaded the infected file. Once opened, ILOVEYOU would overwrite or hide a lot of the files on the infected machine. Usually JPGs MP2, MP3, and various document files. Replacing most of the files would render a machine unbootable. Then, having gained access to the Microsoft Outlook of the victim, the malware would send itself to all addresses found in the Outlook address book.
The worm usually makes its way into machines with an infected VBS file, that victims download from emails. When the ILOVEYOU execution begins, the malware first copies itself in the Windows directory. Then, the worm creates a registry key MSKernel32. Additionally, the worm generates a new Local Machine RunServices key Win32DLL, which causes it to launch at system boot before the user is even logged into the system. Then, ILOVEOYOU downloads a trojan and creates a registry key for it as well. Finally, the worm begins looking for files to modify, overwriting them, and copying itself. The malware keeps the original file names but adds a .VBS file extension to all compromised files.
ILOVEYOU Distribution
The damage from the Loveletter was first felt in South-East Asia. Then, it scaled over to Europe and the USA. Data varies on how many victims were infected but based on different evaluations ILOVEYOU compromised from 30 to 80 percent of computer networks in specific countries.
As the worm was spreading, security companies began making cures. Unfortunately, most were ineffective. Writing in VBScript gave the attackers a way to easily introduce changes to the malware code. Soon after launch, multiple versions of ILOVEYOU circulated in the wild. Each targeted different files and exhibited modified behavior, such as changed email subject lines.
Some of the subjects used included:
- fwd: Joke;
- Important! Read Carefully!!;
- FRIEND MESSAGE.
Other subject matters were:
- An airline ticket receipt from Arab Airlines;
- A rage email, presumably from a friend;
- An antivirus designed to protect from ILOVEYOU;
- A present for Mother’s day, a holiday celebrated in the US.
When security professionals began creating cures for the malware, many targeted an older version, rendering their efforts near useless.
What resulted, was a cyberattack we simply weren’t prepared for. ILOVEYOU proceeded to infect millions of machines.
Not only could the malware spread further and further after each victim, but consequent emails were distributed from familiar addresses. People began receiving letters from their acquaintances. Most would presume them to be safe and open the love letter. At the time, an ingenious way to make users drop their guard.
According to data from the Trend Micro company, ILOVEYOU infected over 3.5 million devices around the world, including the network of the US Department of Defense. The malware caused about $15 million worth of damage.
ILOVEYOU Creator
Soon after launch, researchers learned that ILOVEYOU originated in the Philippines. Authorities began investigating two local programmers, Reonel Ramones and Onel de Guzman.
By tracing messages from European users to a Filipino internet provider, the investigation was found conclusive and Ramones was put into custody. De Guzman, however, at the time escaped the arrest.
The evidence was pointing at the programmers, but neither was charged. In 2000 there simply aren’t any laws related to hacking in the Philippines. First, authorities wanted to use credit card fraud as a substitute, then malicious mischief. But neither could apply completely.
In addition, de Guzman who just graduated from a programming class with a project extremely similar to ILOVEYOU claimed that he could have released the malware by accident. He never admitted to being responsible. When asked if he created ILOVEYOU, he would reply “maybe” and “I could have done it without realizing the consequences” through his lawyer.
Only 20 years after, when Geoff White of the BBC News tracked down de Guzman, the hacker admitted to being behind the ILOVEYOU attacks. Allegedly, all the students wanted to do was steal internet passwords, as he wasn’t able to afford his own connection. According to de Guzman’s words, he had no idea about the mayhem his creation could cause.
According to his words, after launching the worm de Guzman left to hang out with friends, soon forgetting about his actions. He only discovered the chaos he caused, by learning from his mother that the Police are looking for a dangerous hacker in Manila.
Conclusion
A lot has changed since the year 2000. At the time, creating malware was more of a hobby. A way to prove programming skills to co-workers and friends. But ILOVEYOU showed the world just how effective and devastating malicious programs can be. In doing so, it helped shape the cybercrime landscape into what it is today.
Twenty years later nobody takes malicious programs for granted. Today, they are highly specialized and sophisticated tools designed to cause damage. They target businesses and sometimes private users with one goal — stealing money or information that leads to money. Now, there are people who develop and operate these programs professionally.
In the last 20 years, the malware was evolving. Despite better modern cyber defenses and anti-viruses, some programs can spread even faster than ILOVEYOU, causing even greater damage.
We are likely to see a lot of attacks utilizing botnets. They will be more automated and more complex. Many are likely to resemble WannaCry, attacking in multiple stages.
Users can trigger a massive outburst of malware by simply opening a phishing email or following a phishing URL. In some instances, simply clicking on a malicious link can compromise the network router, opening even more backdoors, and enabling the attackers to redirect network traffic to malicious websites.
That’s why today more than ever we must be extremely cautious when working with emails. Especially when they contain links or attached files. Even if an email is from somebody you know — it is not a guarantee that it is safe. Vigorously checking all suspicious content is a vital step in building an effective security perimeter. Luckily, with ANY.RUN it is extremely easy.
Test everything; don’t risk infection of the entire network. Take care of yourself and your data!
3 comments







Fantastic goods from you, man. I have understand your stuff previous to and you are just too great. I actually like what you’ve acquired here, really like what you are stating and the way in which you say it. You make it entertaining and you still take care of to keep it wise. I cant wait to read much more from you. This is actually a great web site. Real nice pattern and wonderful articles , practically nothing else we require : D
I do accept as true with all the ideas you’ve presented to your post. They’re very convincing and will definitely work. Still, the posts are very brief for starters. Could you please extend them a bit from next time? Thanks for the post.
Hi my family member! I want to say that this post is awesome, nice written and come with approximately all significant infos. I would like to see more posts like this.