Cyber threat intelligence is all about data: its collection, exploration and research, extracting actionable insight. If you employ any intelligence solution, it is vital to understand what data sources it relies on and what kind of information they deliver.
In ANY.RUN’s Threat Intelligence Lookup and TI Feeds, we leverage fresh data from millions of sandbox analyses performed by thousands of organizations and hundreds of thousands of researchers.
Here is how it works.
Where Threat Intelligence Comes From
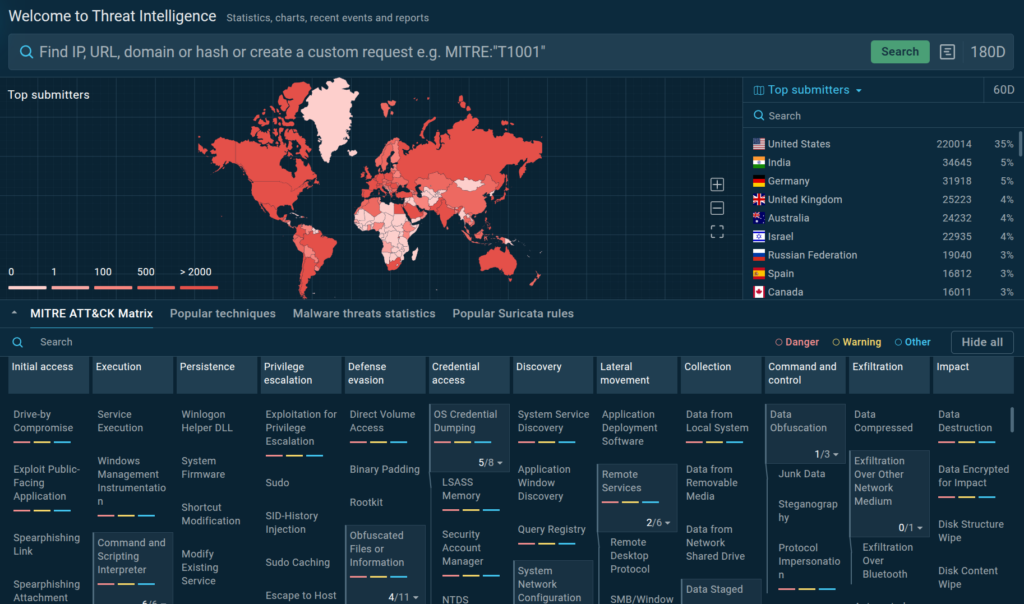
Over 500,000 security professionals worldwide, including SOC teams from 15,000 companies, use ANY.RUN’s Interactive Sandbox daily to analyze suspicious links and files related to the latest cyber attacks. They check alleged phishing emails, explore potential breach attempts, investigate incidents, and collect critical insights into malicious behavior.
Thanks to ANY.RUN’s proprietary technology, we extract IOCs, IOAs, IOBs, and TTPs from the analyzed samples and enrich Threat Intelligence Lookup and TI Feeds with a continuous inflow of threat data which is:
- Real and Exclusive: Companies submit files and URLs related to actual attacks on their infrastructure. The data extracted from these submissions is often unique and cannot be found in any other sources.
- Up-to-date: The data belongs to recent or ongoing cyber attacks, including active campaigns and emerging malware.
- Actionable: SOC teams often submit samples as part of proactive threat hunting or incident response, contributing to a dataset that helps you predict and prevent future attacks.
How Data From 15,000 Businesses Helps Yours
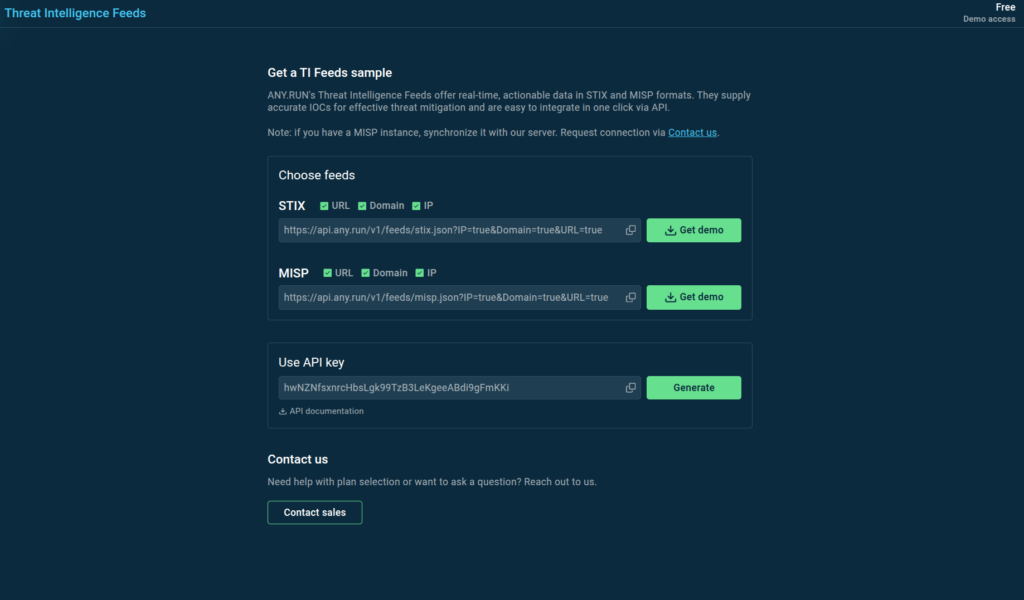
The wealth of data on the latest cyber threats available in Threat Intelligence Lookup and TI Feeds enables organizations like yours to:
- Quickly Detect and Prevent Attacks avoiding operational disruption and further damage.
- Enhance SOC Efficiency providing teams with access to current and relevant data and enabling them to defend company’s assets and infrastructure proactively.
- Boost Mitigation and Response minimizing the cost of incident, financial and reputational losses.
You can investigate, search, and get a direct stream of IOCs, IOAs, and IOBs in your company to strengthen your proactive defenses against ongoing malware and phishing attacks.
Examples of Unique Threat Intelligence on Active Cyber Attacks
One of the scenarios where threat data from companies serves other companies through the agency of ANY.RUN’s tools is industry-wide malware campaigns. Organizations that were the first to face incidents help others to anticipate and prevent them.
1. Interlock Ransomware Attacks on US Healthcare
In late 2024, the Interlock ransomware group launched targeted attacks against multiple healthcare facilities in the United States, causing significant disruptions and exposing sensitive patient data.
Threat Intelligence Lookup had data on the threat almost one month before the first reports emerged. This helped our users take preventative measures long before public alerts were raised. For example, one of the malicious domains that distributed the ransomware appeared in submitted samples in September.
domainName:”apple-online.shop$”
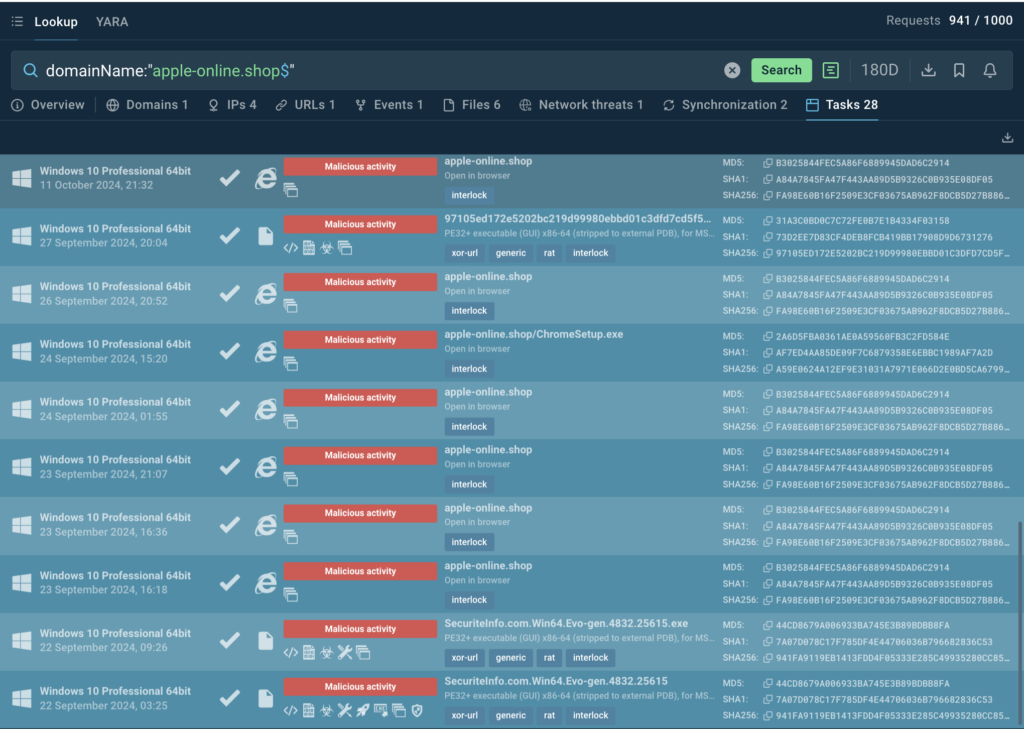
Beside gathering IOCs for monitoring, detection and alerts, the security teams were able to see inside sandbox emulations how malicious websites and pages looked like and train employees to recognize and avoid similar threats in the future.
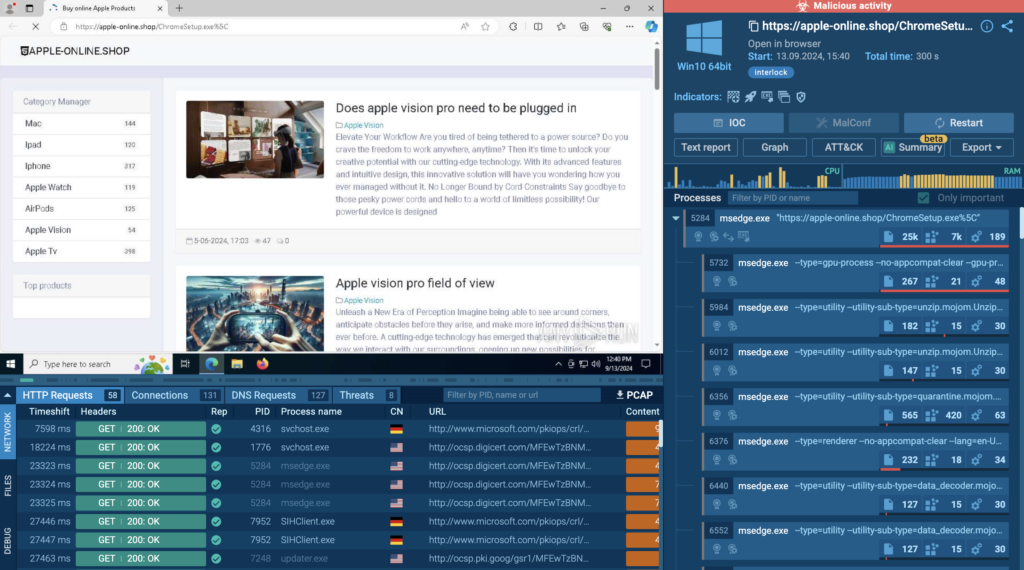
Finally, ANY.RUN’s data managed to enrich the understanding of attacks and their evolution.
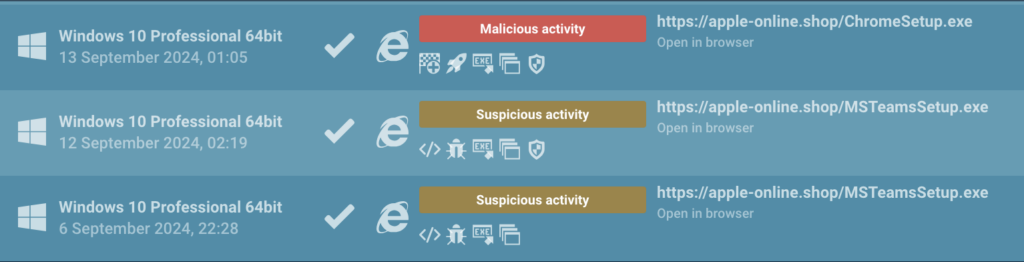
While reports stated that the attackers used malware disguised as a Google Chrome updater, ANY.RUN uncovered additional tactics, such as mimicking MSTeams and MicrosoftEdge updates (evident in filenames like MSTeamsSetup.exe and MicrosoftEdgeSetup.exe).

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
2. Nitrogen Ransomware Attacks on Fintech
Financial services have been one of cybercriminals’ most targeted sectors in recent years. The case with the Nitrogen ransomware group is pretty much similar to that with Interlock in healthcare. Thanks to thousands of companies using ANY.RUN, the information on the new threat appeared quickly in our services, and more companies had the opportunity to protect themselves, set up detection and alerts.
The group was first reported about half a year ago, months after the attack unfolded, and the information about it is still scarce. The more valuable is this data from Threat Intelligence Lookup, which allows users to interconnect, contextualize, and further explore it.
For example, the first analytic report on Nitrogen group from StreamScan mentions the file truesight.sys in their attack dissection. This is a legitimate driver, one of those that are often abused by malefactors to bypass detection. The StreamScan report, however, does not contain or link to any malware samples and analyses that feature the abuse of this driver.
We can use the following query in TI Lookup to find relevant samples:
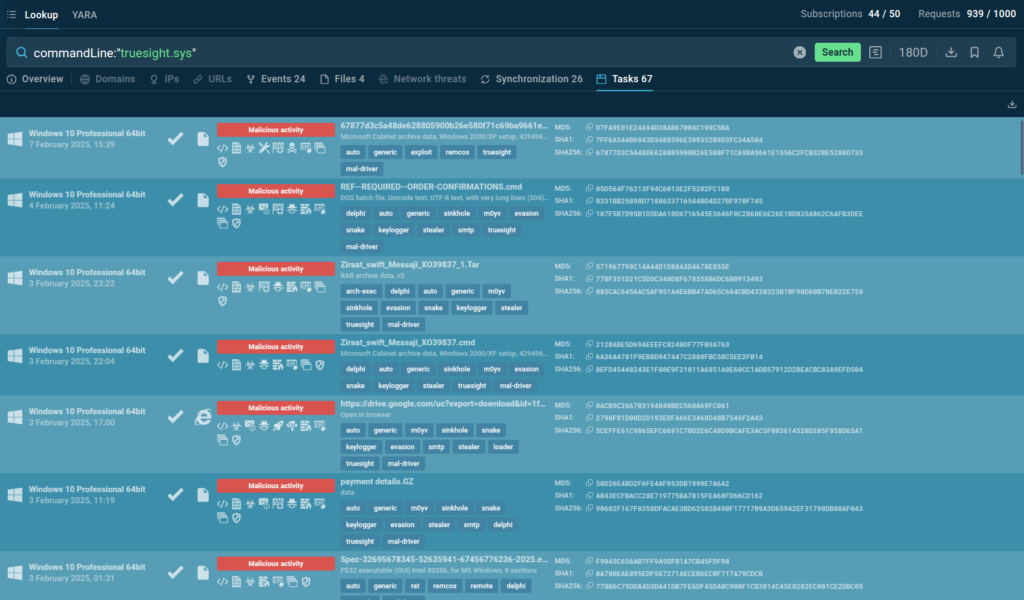
We can search for this file via TI Lookup, find dozens of analysis tasks where the driver was spotted, see how the malware behaves, and what IOCs are associated with truesight.sys abuse. And of course we can find other malware with similar mechanics.
Conclusion
Threat Intelligence Lookup and TI Feeds offer a wealth of threat data on the latest cyber attacks. From IOCs, IOAs, IOBs to TTPs, you can easily gain valuable context on any piece of intelligence and get a constant stream of up-to-date indicators directly to your detection systems. With ANY.RUN, you get actionable threat intelligence to help your businesses build strong, scalable, and efficient protection against ongoing and emerging threats.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request trial of ANY.RUN’s services to test them in your organization →








0 comments