In this article, we’re breaking down all updates that took place in ANY.RUN in July: new features, detection rules, and community contributions. We have a lot to unpack, so let’s get started.
Product updates
We had two major releases in July: digital signatures and evidence archive export.
Digital signatures
Digital signature data is now accessible in ANY.RUN both for processes and modules.
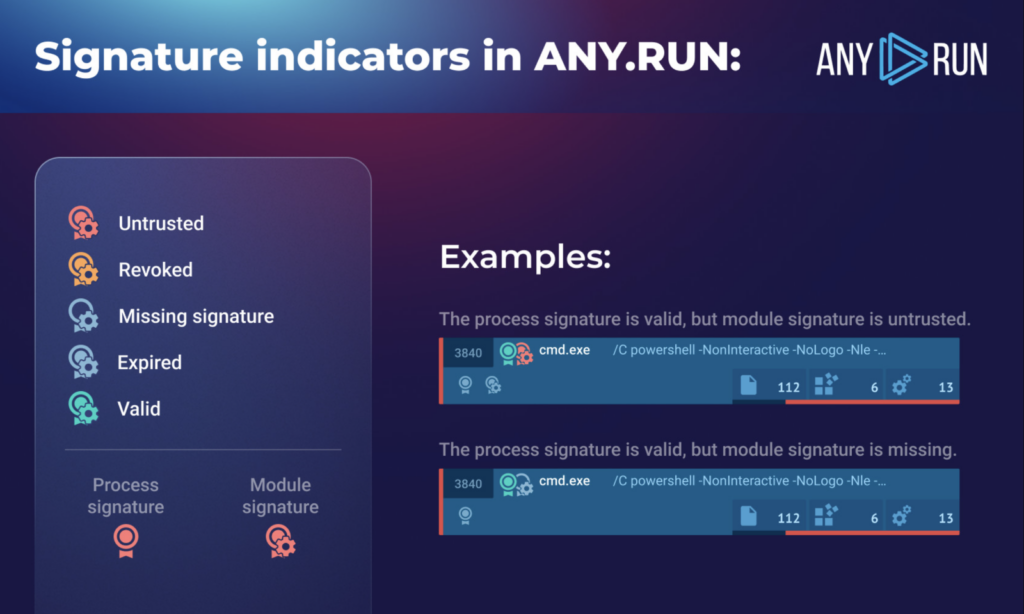
Signature icons appear on the process tree, indicating if a signature is valid, expired, revoked, or untrusted. Clicking on the icon brings up a detailed view.
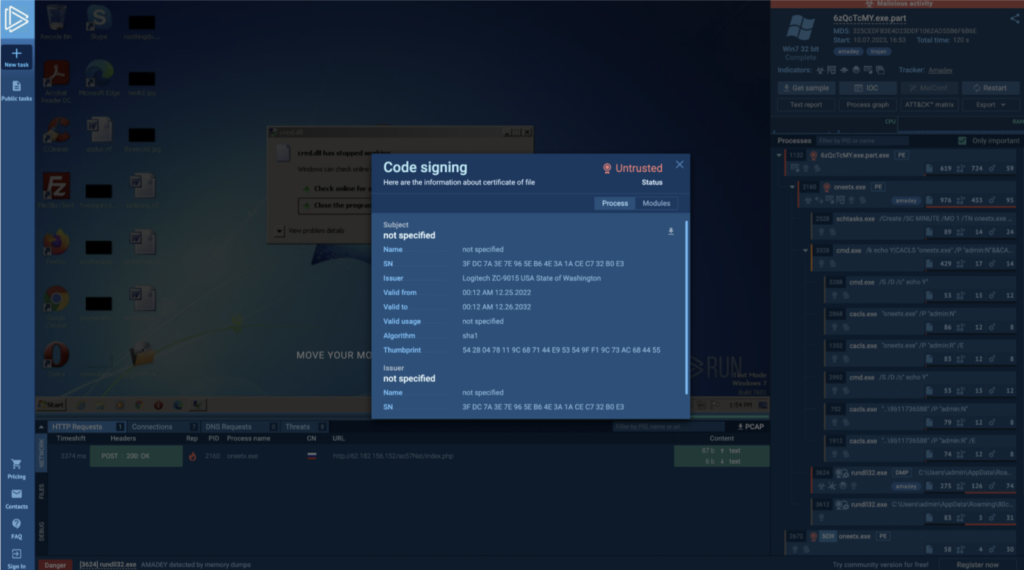
And for even more details, a new section of “advanced process” details is now dedicated to signatures. There, you can download the certificate itself and ASN.1 tree.
New YARA rules and Signatures
We’ve added a signature for lu0bot as well as new YARA rules for the following families:
- PureLoader. A new loader family.
- Revil\Sodinokibi. Ransomware, also known as Sodin.
- BanditStealer: A new strain of information stealer.
- Redosdru: A downloader trojan.
Config extractor additions and fixes
ANY.RUN can automatically extract and decrypt the configuration for over 60 malware families, giving you quick access to encrypted strings. In July, we’ve added 2 extractors:
- Added: Lucastealer extractor
- Fixed: Dcrat extractor
New network and detection rules
In July, we’ve written 74 new network rules in the Suricata format.
- Minimal_PC_Miner, Repl.it Miner coverage added. We’ve investigated GitHub repos in the wild, searching for Duino-Coin miners. As a result, we’ve added a Minimal_PC_Miner, Repl.it Miner coverage. We’ve also created a generic to account for subsequent forks.
- A new rule created to mark Hydrochasma reverse proxy. A traffic proxy tool called Hydrochasma, which poses a threat to medical and shipping companies in Asia, has been marked by our rule. The rule, named Hydrochasma Fast Reverse Proxy, was shared with the ET community.
- Improved Danabot coverage. We’ve improved the coverage for Danabot by adding a new rule which targets the message structure related to this threat’s activity.
- Two new phishing rules added. Phishing is one of the most pressing threats and a common vector of attack. Our HTMLPhisher page collection has been updated with two new rules.
- New rule for loading shellcode. Shellcode is a binary executable code that usually transfers control to the command processor. Our arsenal has been updated with a rule for loading shellcode, as well as a tag for similar content. Enter ‘shellcode’ into the search bar and see the result here.
- Even more new rules. Fabookie, Stealc, Formbook, and GuLoader have also received additional rules for detecting network activity. We constantly monitor non-detectable connections of already known malware with the aim of achieving the most comprehensive threat coverage.
Better Coverage and Detection of New Threats
Menorah, a new backdoor found. The backdoor that we’ve named Menorah, after the name of the executable file, caught our attention with a lure in the form of a Microsoft Word document containing a vehicle registration form under the jurisdiction of the Seychelles. The document incorrectly stated the address of the Seychelles Licensing Authority and also contained a malicious macro.
Implemented detection of Mystic Stealer. Mystic Stealer is a relatively new threat, the network traffic of which was described in this article. We’ve added our signature and have also contributed to the community.
Created a rule for Hydrogene — a new backdoor. The previously unexamined public Java backdoor Hydrogene was active as of July 16th, drawing our attention. It received the rule BACKDOOR [ANY.RUN] Hydrogene (Java.Agent).
New MQsTTubo malware found. The Internet of Things (IoT) is all around us, and it has its own lightweight protocols, such as MQTT. Malicious actors decided to exploit this and have created yet another malware based on MQTT. This previously unexplored malware publicly accessible has been named MQsTTubo and has a series of rules for detecting network activity. Note, that reproducing the threat is quite complicated. The link to the primary analysis in ANY.RUN can be found here.
A new GO-based stealer detected. The previously unexplored stealer written in the GO language and distributed via discord links was named SorryGoMaster and received detection rules.
Increased activity of APT groups detected in July
This month, we observed a surge in activity from APT groups such as APT37, Storm-0978, and Lazarus.
Storm-0978 exploited the zero-day vulnerability CVE-2023-36884 with a CVSS v3.1 score of 8.3/8.1. The first sample appeared in our sandbox on July 3rd, 2023. To proactively track exploitation, we added several policy class rules.
Konni is a tool used by the North Korean APT37 group designed to steal victim data. Notably, it checked for a kill switch file that would halt the stealer’s operation. In the case we examined, the lure came with several documents in Korean:
- 소명자료 목록(국세징수법 시행규칙).hwp.lnk – List of explanatory materials (Execution Rules of the Tax Collection Law).hwp.lnk
- 인지세 조사 보고서(인지세 사무처리규정).hwp – Report on stamp duty investigation (Stamp Duty Administration Rules).hwp
- 자금출처명세서(부가가치세법 시행규칙).hwp – Statement of source of funds (Implementation Rules of the Value-Added Tax Law).hwp
You can find the analysis in ANY.RUN here. We’ve also published the rules for detecting these illegal online activities.
Lazarus, another North Korean group, used an unidentified backdoor tool. Based on preliminary research, the DTrack tool is suspected at the initial stage, with a lure named ‘Multi National Recruitment System Templete.pdf.lnk’ within a Korean archive – \미군 구인공고 웹사이트 주소 및 사용방법 안내\ (US Army job posting website address and how to use it). As in the previous case, we informed the community with a new rule.
The HZRAT threat remains active and has a functioning command and control server. We had to add another rule to our set due to the lack of detection in this sample.
Previously flagged as the STEALER [ANY.RUN] Win32/Clipbanker, the backdoor received its name BACKDOOR [ANY.RUN] KillRun PowerShell.Backdoor due to the presence of only two commands — kill and run. We relied on the research conducted in SANS (Internet Storm Center) Diary by Xavier Mertens.
VanillaRAT is an advanced remote administration tool coded in C#, according to a 4-year-old description on GitHub. Vanilla itself is not something new and was already on the radar back in 2019. We still note its network activity, which received the rule REMOTE [ANY.RUN] VanillaRAT.
DNS Error found that can lead to vulnerabilities
An amazing case of negligence in programming DNS addresses occurred in a report. It claims that Cisco OpenDNS with the address 208.67.222.222 is read by the malicious tool Deed RAT in reverse order, i.e., as 222.222.67.208. This leads to an erroneous connection to a server with a missing DNS resolver. This incident was reflected in our rule SUSPICIOUS [ANY.RUN] Misspelled OpenDNS IP (CosmicStrand or Deed RAT). Thanks to our colleagues for the report. We noticed the same error in the CosmicStrand rootkit.
LucaStealer changes tactics
Network activity for LucaStealer has been detected, based on HTTP POST requests. Previously, the preferred exfiltration channel for this malware was considered to be Telegram.
Try ANY.RUN for free for 14 days
ANY.RUN is an interactive malware sandbox that streamlines behavioral analysis and accelerates access to knowledge. Our detection capabilities are already industry-leading, but we’re working hard to make them even more robust. See how ANY.RUN can help you catch emerging threats.








0 comments