Editor’s note: The current article is authored by Clandestine, threat researcher and threat hunter. You can find Clandestine on X.
ANY.RUN’s Threat Intelligence (TI) Lookup is a powerful service for Open Source Intelligence (OSINT) and Threat Intelligence investigations. In this research, we shall analyze 5 specific queries, each targeting different aspects of the threat landscape, to better understand the nature of modern threats as well as defense and response strategies.
Key Findings
- JA3S Fingerprinting underscores the value of behavioral indicators in hunting advanced threats allowing analysts to track Command and Control infrastructure even when attackers rotate IP addresses and domains
- Massive abuse of legitimate infrastructure (AWS, Google Cloud, Cloudflare, Microsoft services) complicates detection, as malicious traffic blends with legitimate services.
- Locally targeted phishing operations demonstrate that attackers tailor their strategies by geography. This highlights the importance of localized cyber threat intelligence.
- By combining sandbox detonation with TI Lookup queries, analysts uncover trojan traffic disguised within HTTPS (port 443). This methodology proves the benefit of correlating behavioral analysis with IOC-based searches.
- The .top domain extension serves as a thriving ecosystem for cybercrime, with randomly-generated DGA domains used for malware delivery, often leveraging WinRAR for payload extraction.
Exploring Beyond IOCs: Malicious Pattern Case Studies
ANY.RUN’s Threat Intelligence (TI) Lookup is a dynamic, searchable database that equips security analysts with immediate access to over 50 million Indicators of Compromise (IOCs), Behavior (IOBs), and Attack (IOAs) and threat events extracted from real-time malware sandbox analyses conducted by a global community of over 500,000 analysts and 15,000 companies.
Tailored for threat hunting, alert triage, and incident response, it allows analysts to query the database using more than 40 parameters – including hashes, IPs, registry keys, processes, and TTPs. It supports search operators, wildcards, YARA and Suricata rules, and notifies on updates on saved searches.
Let’s see how analysts can use it as part of their OSINT investigation.
Case 1: Investigating Regionalized Phishing Campaigns
Query: threatName:”Phishing” AND submissionCountry:”br” and domainName:””
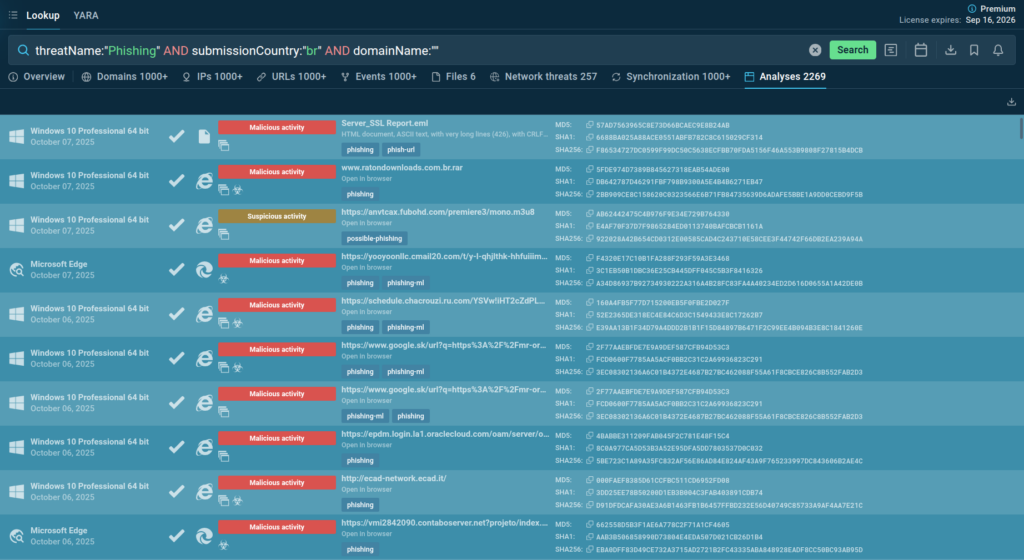
We can start by checking for active phishing campaigns targeting organizations in our region. Even with a free plan, TI Lookup provides us with lots of sandbox analyses of the latest malicious domains and emails sent to companies in Brazil.
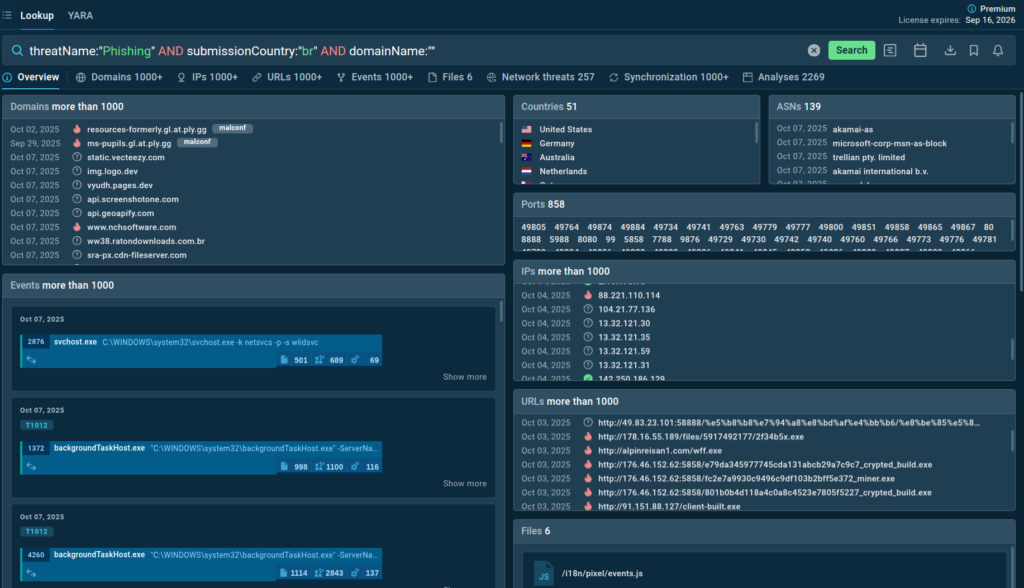
We can also observe legitimate infrastructure abuse as a number of known service subdomains are linked to the campaigns along with malicious domains. Globally hosted infrastructure is leveraged to hinder takedown.
Actionable Intelligence: Organizations in Brazil should be especially alert to emails containing links to subdomains of popular services. Security teams can use the identified domains and IPs to create proactive defense using detection and blocking rules.
Case 2: Tracking C2 Infrastructure with JA3S
Query: ja3s:”1af33e1657631357c73119488045302c”
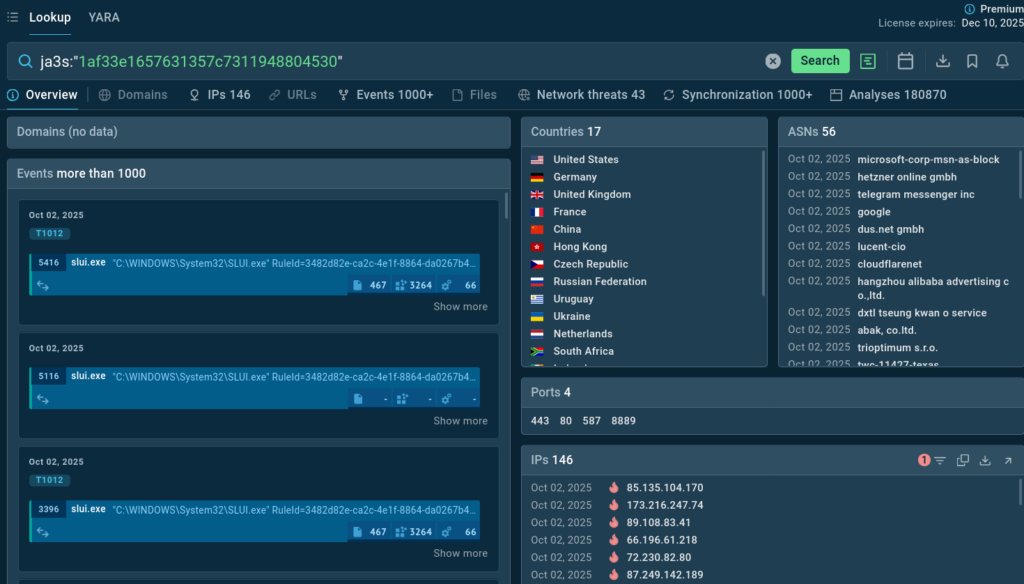
The JA3S hash is a fingerprint of how a TLS client communicates. Different malware or attack tools may have unique JA3S signatures, allowing analysts to track their Command and Control (C2) infrastructure even when IP addresses and domains change. Hash “1af33e1657631357c73119488045302c” is commonly associated with Cobalt Strike.
What do we capture from the search results?
- 1,000+ system events mostly involving slui.exe (System License User Interface), svchost.exe, and PowerShell.
- Predominant communication on port 443 (HTTPS) exposes evasion techniques exploiting LOLBins.
- Abuse of major cloud providers to host C2 infrastructure (Microsoft, GitHub, Google, Amazon, CloudFlare).
- Techniques: Use of legitimate system tools for malicious execution.
Actionable Intelligence: Detection of this JA3S hash on the network is a strong indicator of Cobalt Strike infection or an abuse of a similar tool. Security teams should correlate these alerts with other endpoint and network events to identify compromised systems and initiate incident response.
TI Lookup’s “Analyses” tab contains links to sandbox analyses of malware samples featuring the hash in question. We can sort out samples tagged as “malicious” and study various attack scenarios leveraging similar TTPs:
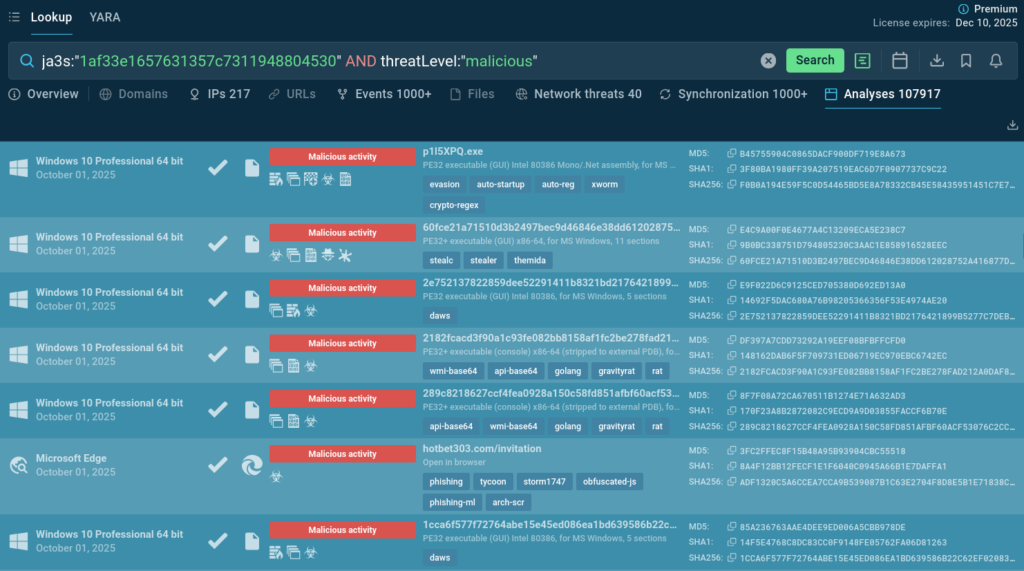
For example, one can view a Cerber ransomware attack and see how it abuses system tools and cloud services.
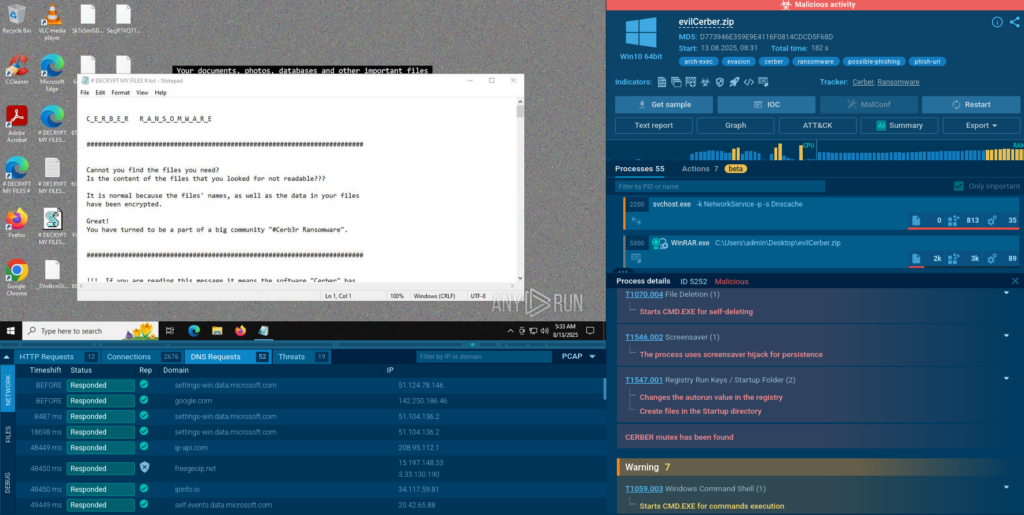
Case 3: Hunting Trojan Traffic Camouflaged in HTTPS
Query: destinationIPgeo:”ru” AND suricataClass:”trojan” AND destinationPort:”443″
This query is a classic example of threat hunting. It doesn’t look up a specific IOC but rather searches for a suspicious behavior pattern: traffic classified as trojan by the Suricata engine, destined for IPs in Russia and using port 443 (HTTPS).
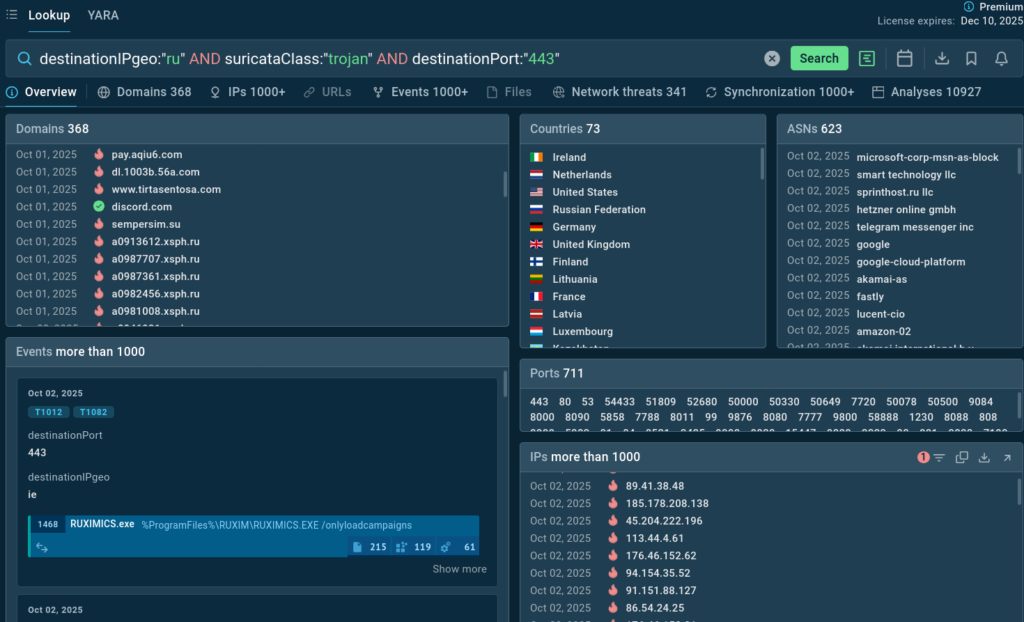
Russia is generally a suspicious communication destination, and port 443 is used to camouflage malicious traffic. The attack strategy includes threat diversity: multiple services and legitimate domains are abused; various ports are employed for communication and fallback.
Actionable Intelligence: This query provides a list of high-risk IPs and domains for enriching perimeter defenses. The combination of destination geolocation, threat classification, and communication port is a powerful hunting methodology.
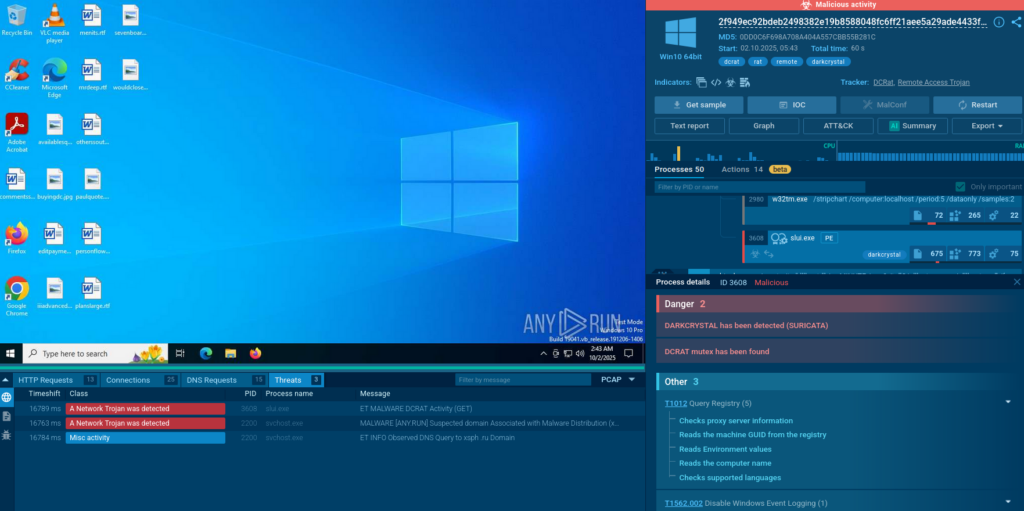
TI Lookup has found a number of analysis sessions demonstrating this behavior pattern.
View an example in the Sandbox
Case 4: Unmasking BEC Campaigns Focused on Invoices
Query: filePath:”invoice.pdf” OR filePath:”pagamento.pdf”
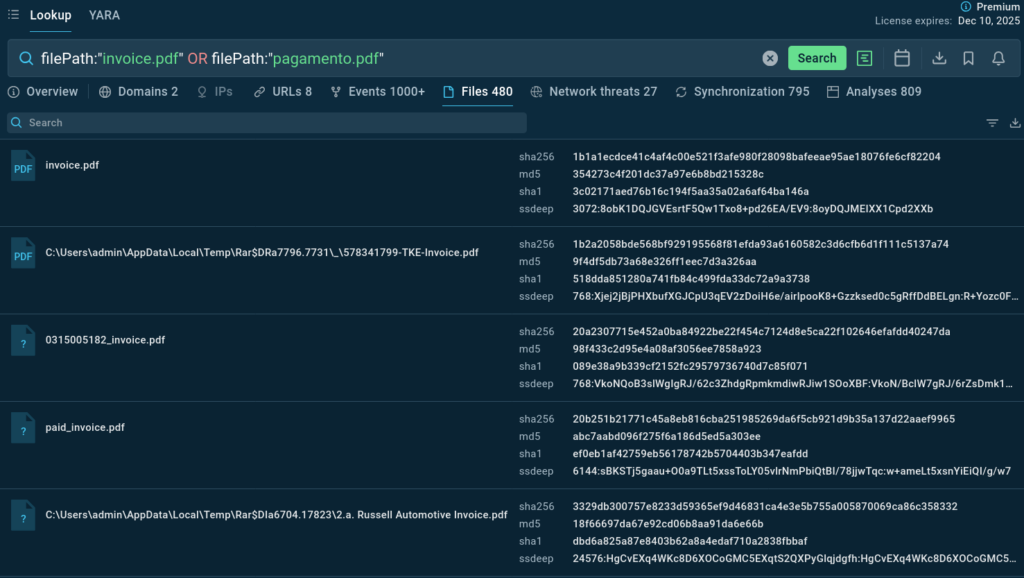
Business Email Compromise (BEC) frauds continue to be one of the most lucrative threats. This query searches for PDF files containing the words “invoice” or “pagamento” (payment) in their name, an extremely common infection vector in BEC schemes.
The malicious files are often hosted on Amazon S3 Buckets and named to appear legitimate. Exploring such attacks delivers file hashes to use as IOCs for detection.
Actionable Intelligence: Organizations should implement email attachment verification and educate employees about fake invoice risks. The IOCs should be added to block lists, and monitoring downloads from unknown S3 buckets can be effective.
Case 5: Identifying Malicious Activity Hotspots with TLDs
Query: domainName:”*.top” AND threatLevel:”malicious”
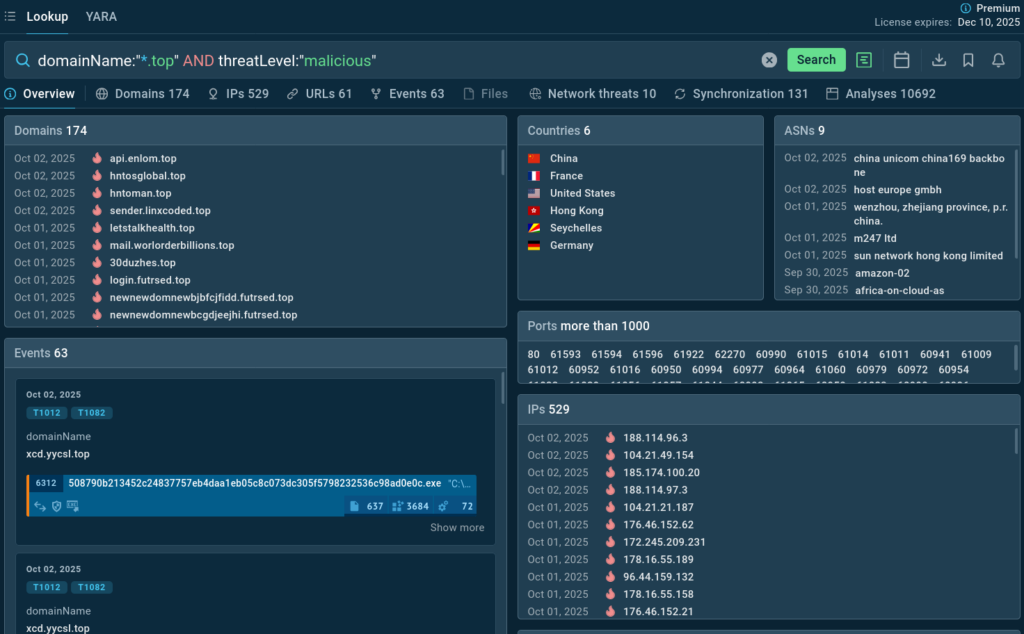
Certain Top-Level Domains (TLDs) are notoriously abused by cybercriminals due to low cost and loose regulation. The .top TLD is one of these. This query searches for all domains ending in .top that have been classified as malicious.
Such domains, mostly generated by algorithms, support a thriving ecosystem for malicious activities. They are often used for delivering payload packed in WinRAR archives. Cloudflare services are engaged for concealing true server locations.
Actionable Intelligence: Aware of extremely high malicious activity volume, many organizations block the .top TLD completely. The appearances of .top domains in network logs should be treated as high-priority events.
Alltogether, these searches provide insight into the broader threat landscape and recent query patterns, showing the diversity of investigation approaches used in threat hunting. Threat intelligence lookups can be focused on a topical threat type (for example, phishing), legitimate tools abuse, registry modifications: queries can target both IOCs and behavioral patterns.
Lessons Learned: Security Recommendations
Here’s how SOC teams and threat hunters can perform an effective OSINT investigation.
For Analysts
- Implement multi-parameter hunting queries combining JA3S fingerprints, destination geolocation, and Suricata classifications rather than relying solely on hash or domain lookups.
- Create detection rules for the identified JA3S hash and monitor for similar TLS fingerprinting patterns indicating Cobalt Strike or similar frameworks.
- Monitor for traffic to non-standard ports and HTTPS-based C2 activity; correlate with TI Lookup results for stronger detection.
- Integrate sandbox detonations into investigations to validate suspicious files, uncover hidden payloads, and gather fresh IOCs.
For SOC and MSSP Leaders
- Adopt proactive hunting playbooks that leverage behavior-based patterns (e.g., phishing, malicious PDFs, LOLBins) instead of relying solely on static IOCs.
- Automate ingestion of ANY.RUN TI Feeds and Lookup results into SIEM/SOAR platforms to strengthen correlation and reduce analyst workload.
- Establish rules and alerts around high-risk TLDs (.top, .shop, .cc) and cloud-hosted infrastructures commonly abused by attackers.
- Adopt a Zero Trust security model: The extensive abuse of trusted infrastructure (Microsoft, Google, Amazon domains) demonstrates that brand reputation no longer guarantees safety
For Business Decision Makers
- Support employee awareness campaigns, especially for financial teams, to counter phishing and BEC attempts.
- Recognize that cloud service abuse is now the norm in modern campaigns, so budgeting for advanced detection and monitoring is critical to maintaining resilience.
- Budget for cyber threat intelligence solutions that provide both sandboxing and lookup capabilities—the ROI comes from preventing successful breaches through proactive threat hunting rather than reactive incident response.
Conclusion
This investigation highlights how modern cyber threats are increasingly sophisticated, regionalized, and reliant on abusing legitimate infrastructure to evade detection. Static IOCs alone are insufficient for defense. Security teams must embrace behavior-based detection and proactive hunting strategies.
ANY.RUN’s TI Lookup and Sandbox provide the intelligence depth and investigative flexibility needed to uncover hidden connections, expose attacker TTPs, and accelerate incident response. Organizations that combine advanced threat intelligence solutions with strong security culture and well-trained teams will be better positioned to withstand evolving threats and reduce the cost and impact of cyber incidents.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN to streamline malware investigations worldwide.
Speed up triage and response by detonating suspicious files in ANY.RUN’s Interactive Sandbox, observing malicious behavior in real time, and gathering insights for faster, more confident security decisions. Paired with Threat Intelligence Lookup and Threat Intelligence Feeds, it provides actionable data on cyberattacks to improve detection and deepen your understanding of evolving threats.








0 comments