This is the July 2023 edition of ANY.RUN’s monthly malware analysis news report, where we share key cybersecurity incidents from the last 30 days.
In July, cybercriminals deploy FraudGPT, an AI bot for offensive cyber activities. The success of the “Barbie” movie leads to malware-laden scams, including RedLine Stealer. A trojanized MS Visual Studio installer triggers a Cookie Stealer. AMI MegaRAC BMC software is found vulnerable to remote attacks, and more.
1. FraudGPT: A New AI Weapon in Cybercriminals” Arsenal
Cybercriminals have a new tool at their disposal, an AI bot named FraudGPT, which is being promoted across dark web marketplaces and Telegram channels.
Netenrich”s report reveals that this AI bot is specifically designed for offensive cyber activities, such as generating spear phishing emails, creating cracking tools, and carding. The tool has been in circulation since July 22, 2023, and is available for a monthly subscription fee of $200.
The capabilities of FraudGPT extend to writing malicious code, crafting undetectable malware, and identifying leaks and vulnerabilities. The creator of the tool, who goes by the alias CanadianKingpin, claims that the tool has already been sold and reviewed over 3,000 times. The exact large language model used to develop FraudGPT remains undisclosed.
2. WormGPT: A Malicious Spin-off of ChatGPT
Another malicious AI tool named WormGPT is being advertised in hacker forums, according to cybersecurity firm SlashNext.
This tool, inspired by OpenAI”s ChatGPT, is designed for illicit activities, potentially including generating malicious code and crafting convincing phishing emails.
WormGPT, unlike ChatGPT, lacks ethical boundaries and limitations. It was able to generate a persuasive email pressuring an account manager into paying a fraudulent invoice. The tool is being promoted via a subscription model, with prices ranging from $60 to $700.
3. Barbie Movie Success Leads to Malware-Laden Scams
The recent success of the “Barbie” movie, which grossed $162 million in its opening weekend, has attracted the attention of online fraudsters.
According to McAfee, these scammers are exploiting the movie”s popularity with a range of social-engineering scams, from fake movie downloads designed to deliver malware to bogus videos promising free tickets but aimed at stealing victims” personal information.
In the three weeks leading up to the movie”s release, researchers saw 100 new instances of malware with Barbie-related filenames. The United States accounted for 37% of the malware received, followed by Australia at 6% and Spain, the UK, India, and Brazil, all at 5%.
Among the malware detected was RedLine, a strain that steals information from browsers, cryptocurrency wallets, and other apps.
4. Trojanized MS Visual Studio Installer Targets Developers
Cybercriminals have created a fake Microsoft”s Visual Studio installer that also triggers a Cookie Stealer, according to Cyble Research and Intelligence Labs (CRIL).
The installer, named “VisualStudio.exe”, extracts sensitive information from browser cookies, specifically targeting popular social media sites.
After extraction, the stolen data is compressed into a zip file and sent to a designated Telegram bot. The stealer then executes the legitimate Visual Studio application, deletes the temporary folder containing the stolen data, and terminates itself to avoid detection. This highlights the importance of caution when downloading files and regularly clearing browsing history.
5. Trojanized TeamViewer Application Distributes njRAT
Cyble Research & Intelligence Labs (CRIL) has discovered a trojanized version of the TeamViewer application that is being used to distribute the njRAT malware.
The deceptive application, which is being spread through compromised WordPress sites, installs a legitimate version of TeamViewer while simultaneously executing the njRAT malware.
The njRAT malware is capable of logging keystrokes, taking screenshots, stealing passwords, and exfiltrating data. It also connects to a command-and-control server, awaiting further instructions.
You can find the latest njRAT samples analyzed by our community in ANY.RUN’s public submissions malware database.
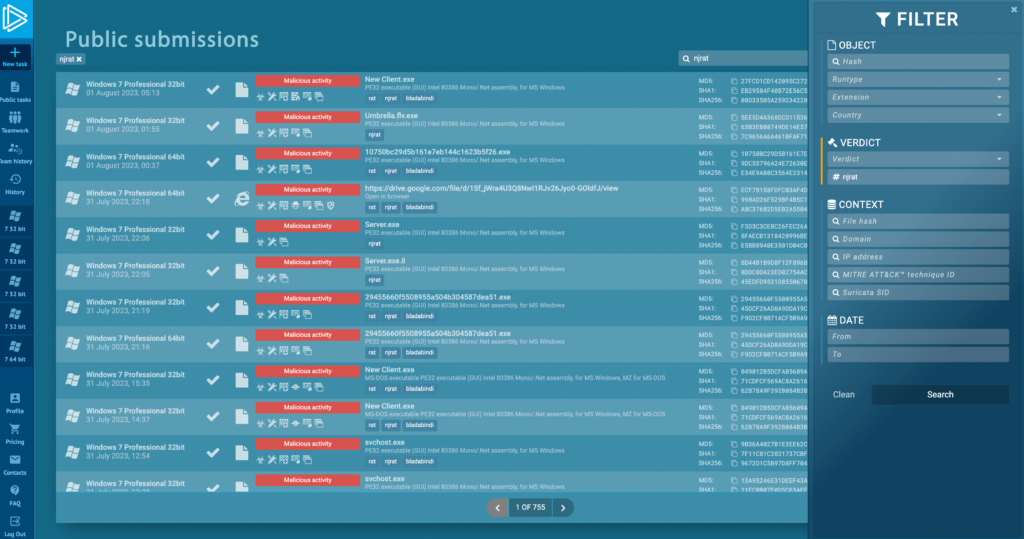
Search for njRAT using the search far or verdict fileds. You can also searc by IOCs and filter results geographically or by submission date.
6. AMI MegaRAC BMC Software Vulnerable to Remote Attacks
Two critical security flaws have been identified in AMI MegaRAC Baseboard Management Controller (BMC) software.
The vulnerabilities, named CVE-2023-34329 and CVE-2023-34330, could allow an attacker to bypass Redfish authentication and remotely execute arbitrary code on the BMC chip with the highest privileges. The popularity of MegaRAC BMC, a critical component found in millions of devices, makes it a potential target for threat actors aiming to control every aspect of a targeted system.
7. FakeSG Campaign Delivers NetSupport RAT via Fake Updates
A new campaign, dubbed FakeSG, has been discovered that uses compromised WordPress sites to deliver the NetSupport Remote Access Tool (RAT) via fake browser updates.
The campaign, which closely resembles the tactics of the known SocGholish campaign, uses a URL shortcut to download a heavily obfuscated script that triggers the execution of PowerShell, leading to the final malware payload.
The NetSupport RAT files are hosted on the same compromised WordPress site used to download the Internet shortcut. Once installed, the RAT communicates with a command-and-control server, potentially allowing attackers to gain remote access and deliver additional payloads.
8. “Sophos” Impersonated by New Ransomware Variant
Sophos has identified a new ransomware that misuses the “Sophos” name in its user interface and encrypted file extensions.
Unlike typical ransomware, this variant exhibits additional capabilities, including keystroke logging and system profiling. It also checks for Russian language settings and refrains from executing if detected.
The ransomware operates via the Windows command line, prompting user input to configure its behavior and ransom note content. Despite referencing a Tor dark web address, it doesn”t establish a Tor connection.
9. PUBG Players Targeted by “Legion Stealer” via Fake GitHub Repo
Cyble Research and Intelligence Labs (CRIL) has discovered a GitHub page posing as a PUBG bypass hack project, but instead, it distributes the “Legion Stealer” malware.
When users download the project and execute the solution file, it deploys the information stealer onto their systems.
The “Legion Stealer” malware is capable of manipulating Windows Defender settings, extracting information from the registry, and gathering system details. It also steals browser passwords, cookies, and data associated with cryptocurrency wallets. The malware then sends the collected data to a Discord server. This incident highlights the risks of downloading files from untrusted sources and the importance of regular password changes and software updates.
10. ARCrypt Ransomware Enhances Anonymity with Multiple TOR Channels
The ARCrypt ransomware, also known as ChileLocker, has evolved to use multiple TOR communication channels, according to Cyble Research and Intelligence Labs (CRIL). The updated variant targets both Windows and Linux operating systems, and uniquely uses a different TOR site for each victim, increasing the attacker”s anonymity.
The ransomware also introduces a new ransom note and a new file extension, “.crYpt”, for encrypted files. It offers a discount for ransom payments made in Monero, a cryptocurrency that is harder to trace than Bitcoin. This evolution of ARCrypt ransomware highlights the continuous adaptation of cyber threats and the need for robust cybersecurity measures.
New in ANY.RUN blog
In July, we”ve published an analysis of a new .NET variant of LaplasClipper, shared a report about the most popular malware types and families in Q2 2023, and written about digital signatures— a new ANY.RUN feature that adds another useful tool into the malware researcher”s toolbox.
This report is brought to you by ANY.RUN, developer of a cloud malware sandbox that handles the heavy lifting of malware analysis for researchers, SOC and DFIR teams.
Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis. Request a demo today and enjoy 14 days of free access to our Enterprise plan.







0 comments