Welcome to the May 2023 edition of our monthly malware analysis news report.
We’ve gathered some of the most important cybersecurity events that transpired over the past month. Read on to make sure you’re not missing any emerging threats.
1. QBot Malware Abuse of Windows WordPad EXE
The QBot malware operation has begun exploiting a DLL hijacking vulnerability in the Windows 10 WordPad program (write.exe) to infiltrate computers.
This technique, known as DLL hijacking, leverages the way Windows applications load DLL files, allowing a malicious DLL to be loaded instead of a legitimate one when the application is launched. QBot is primarily spread through phishing campaigns that include a link to download a file. This file, when downloaded and executed, initiates the infection.
While QBot initially started as a banking Trojan, it has since evolved into a dropper for other types of malware, working with ransomware groups to compromise corporate networks. The malware also steals emails for use in further phishing attacks
2. Batloader Campaign Utilizes AI Ads to Distribute RedLine Stealer
A new campaign involving the Batloader malware is using Google Search advertisements for the ChatGPT and Midjourney generative AI services to distribute the RedLine stealer.
The fraudulent ads misdirect users to webpages, which allow the installation of ChatGPT or Midjourney executables bundled with a PowerShell script. This script facilitates RedLine stealer downloads, while its malicious activity remains undetected due to the binary’s use of Microsoft Edge WebView2.
This new method shows the evolving tactics of cybercriminals. Previous reports identified BATLOADER used in campaigns with ChatGPT lures for Vidar Stealer and Ursnif malware distribution. Furthermore, an increase in ChatGPT-related domain registrations has been noted, highlighting the need for heightened cybersecurity vigilance.
3. SeroXen Remote Access Trojan is rising in popularity
SeroXen, a fileless Remote Access Trojan (RAT), has surged in popularity, especially targeting the gaming community.
SeroXen, which emerged in late 2022, is a blend of Quasar RAT, r77-rootkit, and the command-line NirCmd, offering robust evasion capabilities. This low-cost RAT, touted as a legitimate, undetectable access tool, is primarily used to target video game users. Its growing prevalence and affordability ($30/month or $60/lifetime license).
Stay alert — it’s only a matter of time before businesses encounter this threat as well.
4. RomCom Malware Spread with Google Ads
A new malware campaign, impersonating software such as ChatGPT and GIMP, has been detected distributing the RomCom backdoor malware.
This campaign tricks users into downloading malicious installers by impersonating well-known software websites and distributing them via Google Ads. The malware can cause significant damage and is associated with a Cuba ransomware affiliate.
5. MDBotnet Emerges as a New DDoS Threat
A new strain of malware, called “MDBotnet“, has been discovered by Cyble Research and Intelligence Labs (CRIL). MDBotnet is designed to execute Distributed Denial of Service (DDoS) attacks using HTTP/SYN flood attack techniques.
The service is advertised in a cybercrime forum for 2,500 Rubles (roughly $30), offering lifetime access. The advertisement provides comprehensive details about the features included in the MDBotnet service. It’s critical for organizations to ensure their DDoS mitigation strategies are up-to-date to defend against such threats.
6. npm Packages Found Distributing TurkoRAT Malware
Multiple npm packages have been found to contain a trojan named TurkoRAT, disguised as NodeJS libraries.
These packages have been present on npm for over two months before detection, with a very low detection rate contributing to their prolonged presence.
The three packages — nodejs-encrypt-agent, nodejs-cookie-proxy-agent, and axios-proxy — were downloaded over 1,200 times in total. They contained a Windows executable file that mimics NodeJS but is malicious in nature. This executable runs the TurkoRAT infostealer, a customizable “grabber” and credential stealer that is difficult to detect.
These packages were removed from the npm registry upon detection, but their prolonged presence highlights the ongoing risk unvetted open source packages pose to software supply chain security.
7. Water Orthrus Launches Rootkit and Phishing Campaigns
Water Orthrus, a known threat actor, has been identified as the source of two new malware campaigns: CopperStealth and CopperPhish.
CopperStealth uses a rootkit to install malware onto systems, while CopperPhish targets credit card information. The group has been observed distributing CopperStealer malware through pay-per-install networks since 2021, modifying it multiple times for different purposes such as injecting network ads, gathering personal information, and cryptocurrency theft.
The new campaigns resemble CopperStealer in several ways, suggesting they may be from the same author. CopperStealth was first distributed in March 2023, targeting users via a popular Chinese software sharing website.
8. DarkWatchMan RAT Spreads Via Phishing Sites, Hides in Windows Registry
Cyble Research and Intelligence Labs (CRIL) have identified a phishing site distributing the DarkWatchMan Remote Access Trojan (RAT).
The site mimics a legitimate website, CryptoPro CSP, and offers a malicious file for download. DarkWatchMan, first detected in 2021 primarily targeting users in ex-USSR territories, allows attackers remote control over compromised systems to extract sensitive data. Notably, DarkWatchMan stores captured data in the registry rather than writing it to the files, reducing the likelihood of detection. The malware is spotted being delivered via a file called “CSPSetup.rar” available for download on the phishing site.
Wrapping Up May with ANY.RUN
Throughout May, the dedicated team of analysts at ANY.RUN has been busy analyzing malware, adding new config extractors and signatures. In case you haven’t caught up with our May releases, here’s a quick recap.
New signatures and extractors
We’ve added automatic configuration extractors for StealC, RevengeRAT, LucaStealer, SolarMarker, and DBatLoader.
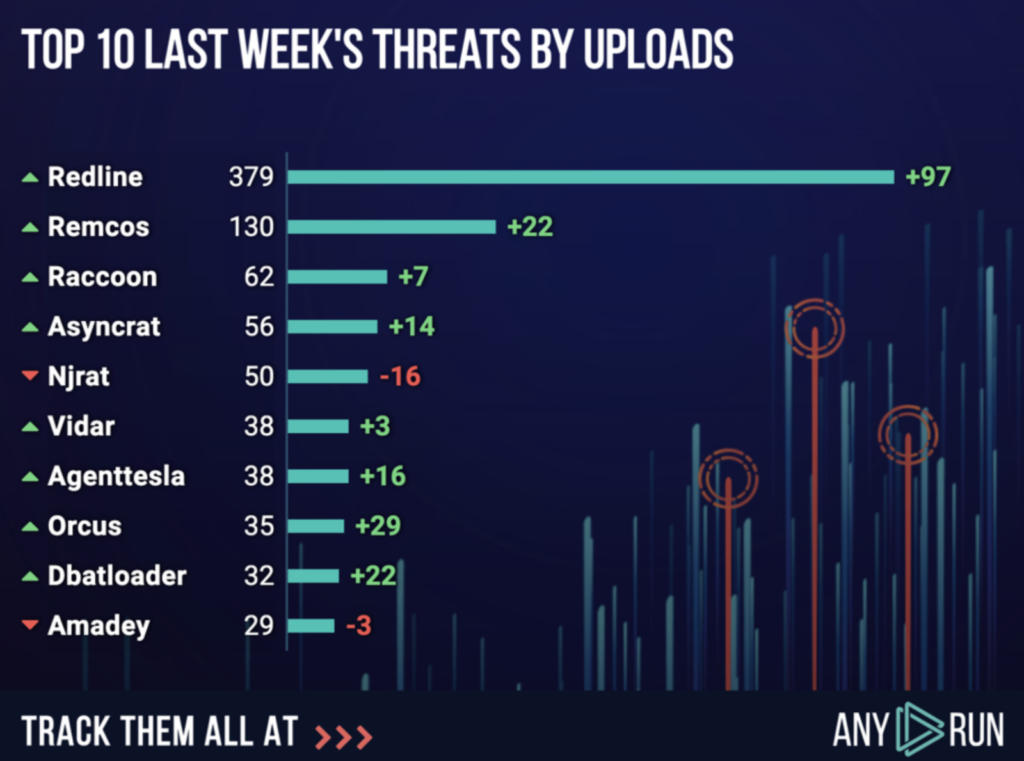
DBatLoader briefly entered our weekly top 10 most uploaded malware chart. Keep an eye on this one.
New Rules for Emerging Threats
We’ve written 5 detection rules which were added by the Emerging Threats community. Here’s the full list, and you can use them in ANY.RUN directly, too.
- ET MALWARE [ANY.RUN] LgoogLoader Retrieving Config File
- ET MALWARE [ANY.RUN] PikaBot Related Activity (GET)
- ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization)
- ET MALWARE [ANY.RUN] WhiteSnake Stealer Reporting Request (Outbound)
- ET MALWARE [ANY.RUN] RCRU64 Ransomware Variant CnC Activity
108 Suricata rules added to ANY.RUN
108 network rules in the Suricata format have been created for detection in ANY.RUN. These include the detection of the following threats:
- PennyWise
- Vice Society
- GootLoader
- Banditstealer
- Ducktail
- ViperSoftX
- Arkei
- DarkVision
- ZgRat
- PrivateLoader
- Mekotio
- Gh0st
- AsyncRat
- NetSupport RAT
Blog updates
We’ve delved into automating GuLoader analysis, explored how malware analysts can leverage ChatGPT, and, last but not least, released a useful step-by-step guide on setting up a new task in ANY.RUN cloud malware sandbox.
New Malware Overviews
We’ve also added several new malware overviews to our Trends Tracker, where we post information about different malware families along with IOCs and samples — updated in real time. In May, we’ve added:








0 comments