When analyzing malware, it is often necessary to go beyond static analysis techniques and use dynamic analysis. This way helps to understand the malware’s functionality better and find more IOCs, which is often our end goal.
Using a sandbox can automate the dynamic analysis process for you, saving you the time of having to do the process manually. Let’s take a look at two different samples using the sandbox from ANY.RUN, and some of the features this service provides. The focus will be on dynamic analysis, mainly through the network traffic generated by the document. ANY.RUN uses Suricata for its threat detection and will provide the alerts that result from said network traffic.
IcedID malware analysis
During the execution of a task ANY.RUN provides interactive access to the virtual machine. And when the task has been completed, either screenshots or videos are available. So you can view what is happening when the malware becomes active.
The first sample comes from a malicious Office Excel document. In this case, we just see an Excel opening and a prompt to enable editing and content, typical of malicious Office documents. One sign of possible malicious content is poor grammar and spelling mistakes, and here we see that button is misspelled as “bytton.”
The panel on the right side displays a process tree, beginning with the initial process and continuing with all further spawned processes to get an overview of what is happening. In this example, Excel spawns three Rundll32.exe processes, which can be seen in the picture below.
The bottom panel has network information such as HTTP Requests, Connections, DNS Requests, and Threats (IDS alerts). A great feature of ANY.RUN is that network activity is displayed in real-time. You don’t have to wait for malware to finish detonation and a final summary report to be created to begin to see IOCs and other helpful information.
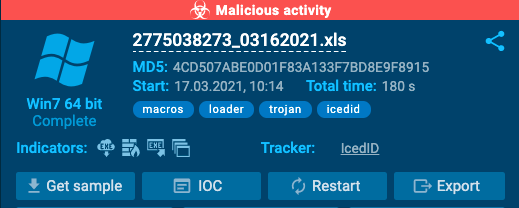
One important IOC is URLs that the malware is attempting to connect to. Under the HTTP Request tab, we can see to whom requests are being made, the location of the address, and the process name and ID. We can see that Excel is making multiple requests for executable files, which is suspicious. The requests are also going to dotted-quad IP addresses instead of a typical web address, like www.google.com, which is uncommon. You can click on the “executable” cell under the Content tab to see the actual request and response data.
You can see summary data as well as hash values. Under the data section, you can clearly see the “magic number” MZ, which indicates that this is a PE file. Looking back at the requests, the newly created processes try to request additional files from hxxp://630mordorebiter[.]website/, which were not successful in this case but are still recognized as malicious sites. Looking under the Threat tab, you can see all the alerts generated by Suricata.
As we noticed earlier, Excel is downloading a PE file, and the request addresses are dotted quads, both of which were detected by Suricata. Also, the two additional rundll32 processes that were spawned were recognized as malware, specifically, IcedID, which were trying to download other content from hxxp://630mordorebiter[.]website/. Looking at the DNS request and Connections tab will give you more detailed network information if you desire.
In the upper right-hand corner of the website, you will find summary information such as file name, hashes, malware type, and environment run-time. Also, you can download the sample and get a list of all the IOCs in one place, which is convenient. All of these services are free. Some, like sample downloads, require an account, but again, all free.
IOCs
Dridex malware analysis
The next sample is another Excel document. It claims to be a “report” but is very small and hard to read, probably done on purpose. Even though a button is intended to incite action from the user, the macros are still executed when the document is opened and content-enabled. These social engineering techniques are used to add more perceived credibility to the document.
The process tree shows Excel launches wmic.exe, which in turn launches rundll32, which is used to run fnb5b.dll.
Under the HTTP Requests tab, we can see that wmic.exe, spawned by the Excel doc, makes a GET request to hxxp://pbotv[.]tv/to presumably download a PHP file, which seems suspicious.
To dig a little deeper, we can click the icon under the “Content” tab of the same request and ANY.RUN will provide the contents of the download.
As you can see, the file is actually identified as a DOS executable, which we can verify in the hex data with the “magic” MZ and the “DOS mode” text. This process then uses rundll32 to execute the downloaded PE file, making two more GET requests. You can click directly on the process in the process tree or under the HTTP Request tab to view more details. ANY.RUN supplies a threat score, which is 100/100 here, and lists specific threats below.
Lastly, under the Threats tab, we are given the specific alerts that were triggered in Suricata. Here, wmlc.exe downloads a PE file via HTTP Get request. Then rundll32 executes a dll which is explicitly recognized as Dridex malware. Again, the Connections and DNS Requests tabs will give more details if desired.
IOCs
http://pbotv.tv/wp-content/plugins/sg-cachepress/vendor/a5hleyrich/y8UzX1Zf0ZWtO.php
pbotv.tv
C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\y8UzX1Zf0ZWtO[1].php
35.214.243.127
77.220.64.140
8.253.204.120
8.4.9.152
sha256 23c625b550dea7fb8847a4c34f931181066e18a97ea40d3018d6a1f77ece9772
sha1 d6be6c4b01e1690923b06253783c79ce3b352e14
Sample 1: https://app.any.run/tasks/e65f0c6d-3754-4a30-a09f-e2ecfbfaeaae/
MD5 4cd507abe0d01f83a133f7bd8e9f8915
Sample 2: https://app.any.run/tasks/7dd4537b-eaf3-4b42-b123-a3c5e3d0316d/
MD5 caf32427ed8b4558c25adbf5c3701594
Conclusion
In-depth manual malware analysis can be very time-consuming and cumbersome. The use of a feature-rich sandbox, like ANY.RUN can streamline your workflow and make your life much easier. This brief analysis of these two samples only highlights some of the site’s features and is intended as a starting point for sample analysis.
Ryan Blevins
My name is Ryan Blevins, and I live in the Pacific North West, where I love spending time out in the wild to recharge myself. I earned a BS in Cyber Operations from Dakota State University. My professional interests include cyber-security, especially reverse engineering and all things malware-related.
41 comments










Will the Excel file infect or execute the malware if I run a Linux Ubuntu with LibreOffice?
No, Portable Executable file format won’t run inside Linux system without additional steps such as Wine.
Thanks for finally writing about it. Loved it!
I like the helpful information you provide in your articles.
I’ll bookmark your weblog and check again here frequently.
I am quite certain I will learn many new stuff right here!
Good luck for the next!
Hi, I do think this is an excellent website. I stumbledupon it ;
) I will come back yet again since I book-marked it.
Money and freedom is the greatest way to change, may you be rich
and continue to guide others.
I think this is one of the most significant information for me.
And i’m glad reading your article. But want to remark
on some general things, The website style is great, the articles is really great : D.
Good job, cheers
I was able to find good information from your blog articles.
Thanks for sharing your thoughts.
Regards
Hi, after reading this awesome piece of writing i am as well cheerful to share my experience here with colleagues.
I do accept as true with all the ideas you’ve introduced for your
post. They are very convincing and will certainly work.
Still, the posts are too brief for newbies. Could you please
extend them a little from next time? Thanks for the post.
This excellent website certainly has all of the information I needed
concerning this subject and didn’t know who to ask.
This is my first time go to see at here and i am genuinely happy to read all at one place.
Peculiar article, just what I was looking for.
Hi, the whole thing is going well here and ofcourse every one is sharing information, that’s in fact
good, keep up writing.
Spot on with this write-up, I absolutely think this site needs far more attention.
I’ll probably be back again to see more, thanks for the
information!
Hello, Neat post.
Good info. Lucky me I recently found your website by accident.
I’ve saved it for later!
Your style is so unique in comparison to other folks I have read stuff from.
Thank you for posting when you’ve got the opportunity, Guess
I’ll just book mark this blog.
An intriguing discussion is definitely worth comment.
I think that you ought to publish more on this subject matter, it might not be a taboo
matter but usually people do not speak about such subjects.
To the next! All the best!!
hello!I love your writing so so much!
Excellent, what a blog it is! This website gives valuable facts to
us, keep it up.
You’re so interesting! I do not think I have read a single thing like this
before. So good to find another person with a few genuine thoughts on this subject matter.
Really.. thanks for starting this up. This site is something that is needed on the web,
someone with some originality!
Useful info. Lucky me I discovered your website unintentionally, and I’m shocked why this accident did not came about in advance!
I bookmarked it.
Thank you for sharing your thoughts. I really appreciate your efforts and I will be
waiting for your further post thank you once again.
This is a topic which is near to my heart…
I think this is among the most significant information for me.
And i’m glad reading your article. But should remark on some general things,
The web site style is great, the articles is really nice : D.
Good job, cheers
I’m extremely pleased to uncover this page. I want
to to thank you for your time for this particularly wonderful
read!! I definitely liked every part of it
and i also have you saved to fav to check out new stuff on your website.
Hello to every one, it’s really a nice for me to pay a quick visit
this site, it contains precious Information.
You can definitely see your skills within the work you write.
The arena hopes for even more passionate writers such as you who are not afraid
to mention how they believe. At all times go after your heart.
Howdy! I simply wish to give you a big thumbs up for your great info you have right here
on this post. I will be coming back to your website for more
soon.
Simply desire to say your article is as astonishing.
The clarity in your submit is simply nice and i could think you are a professional in this subject.
Fine with your permission let me to grab your RSS feed
to keep updated with imminent post. Thanks 1,000,000
and please carry on the rewarding work.
Pretty! This has been an extremely wonderful post.
Thank you for providing this info.
Pretty nice post. I just stumbled upon your weblog and wanted to say that I have truly enjoyed browsing your blog posts.
After all I’ll be subscribing to your rss feed and I hope you
write again soon!
Do you have any video of that? I’d like to find out some additional information.
Hi! Sure, please check out our YouTube channel.
Hello There. I found your blog using msn. This is a very well written article.
I will make sure to bookmark it and return to read more of your useful information. Thanks for the
post. I’ll certainly return.
Good article. I will be going through some of these issues as well..
Informative article, just what I needed.
Appreciate the recommendation. Let me try it out.
Hi, I do think this is a great blog. I stumbledupon it 😉 I’m going
to return once again since i have book marked it.
The contents are masterpiece. you have done a wonderful task on this topic!