Gathering Indicators of Compromise (IOCs) is key to identifying and responding to threats. IOCs are pieces of forensic data that point to potential malicious activity, helping you detect, investigate, and prevent cyberattacks.
With ANY.RUN, you can collect a wide variety of IOCs, giving you a complete picture of any threat.
Let’s dive into the types of IOCs you can collect in ANY.RUN’s Interactive Sandbox and where to find them.
File System Indicators
Main Objects
The Main Object is one of the most critical components when analyzing malware inside the ANY.RUN sandbox. This refers to the primary file that was loaded for analysis.
Once you’ve initiated a sandbox analysis session, simply click on the file name located in the upper-right corner of the screen.
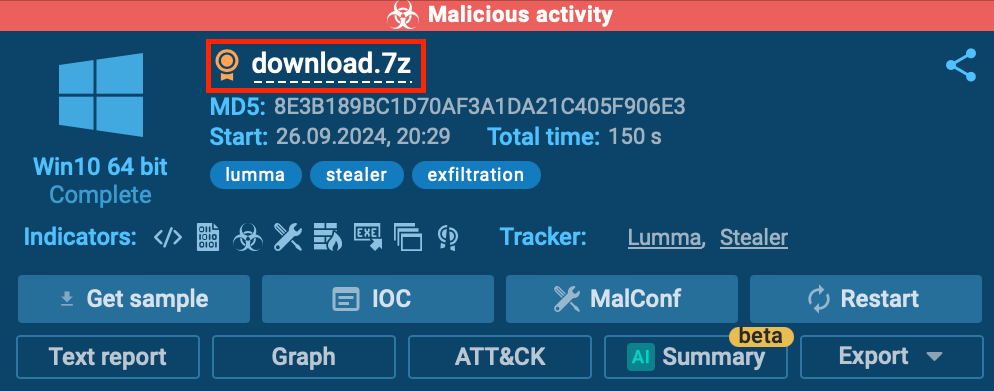
This action will give you quick access to the Main Object IOCs, which include basic details such as file paths, hashes, and more.
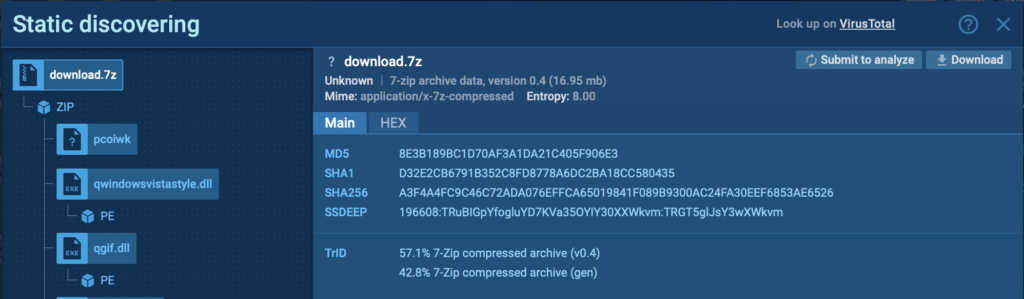
Dropped Executable Files
All files dropped during the malware’s execution are shown in the bottom panel under Files. This area demonstrates exactly what files the malware generated or modified, helping you track its propagation across the system.
Network Indicators
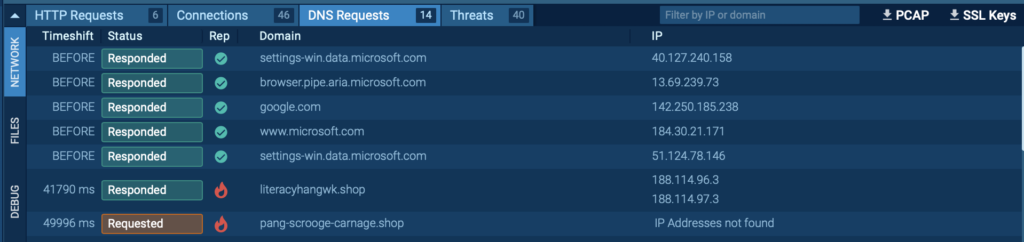
Domains (DNS Requests)
Domains that the malware attempts to access can help you trace its communication with external servers, such as command-and-control (C2) infrastructure.
You can find these IOCs under Network → DNS Requests in the bottom panel of the sandbox interface.
By analyzing the DNS requests, you’ll get a clearer view of how the malware interacts with remote hosts, often revealing malicious infrastructure or other indicators that can assist in further threat investigation.
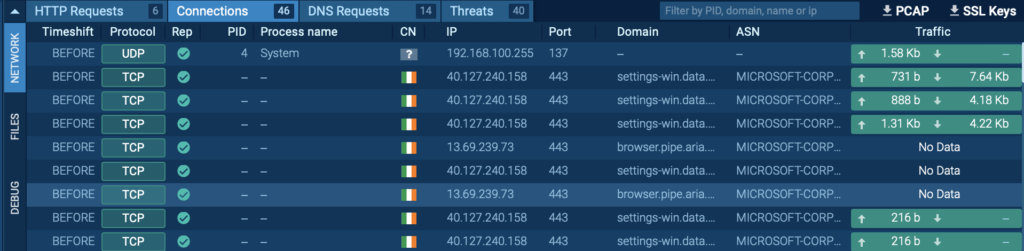
Connections
The malware’s active connections can be observed under Network → Connections.
This feature allows you to monitor the malware’s communication channels, tracking its interactions with command-and-control (C2) servers or other suspicious IP addresses.
Analyzing these connections enables you to identify data exfiltration routes or pinpoint where the malware is sending information.
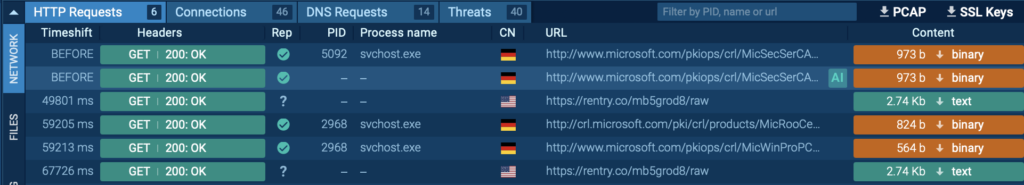
HTTP/HTTPS Requests
HTTP and HTTPS requests initiated by the malware are logged under Network → HTTP Requests. This is crucial for identifying malicious websites or external servers the malware connects to.
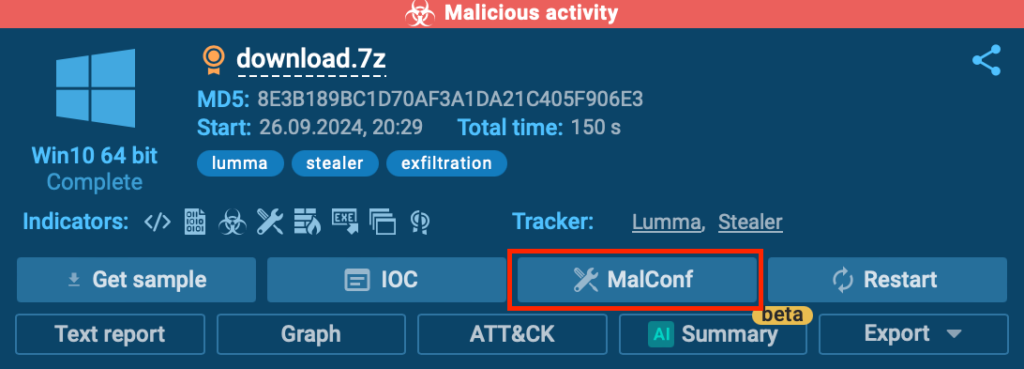
Malware Configurations
In the ANY.RUN sandbox, you can gather IOCs specifically associated with malware configurations by clicking the MalConf button located in the upper right corner of the screen.
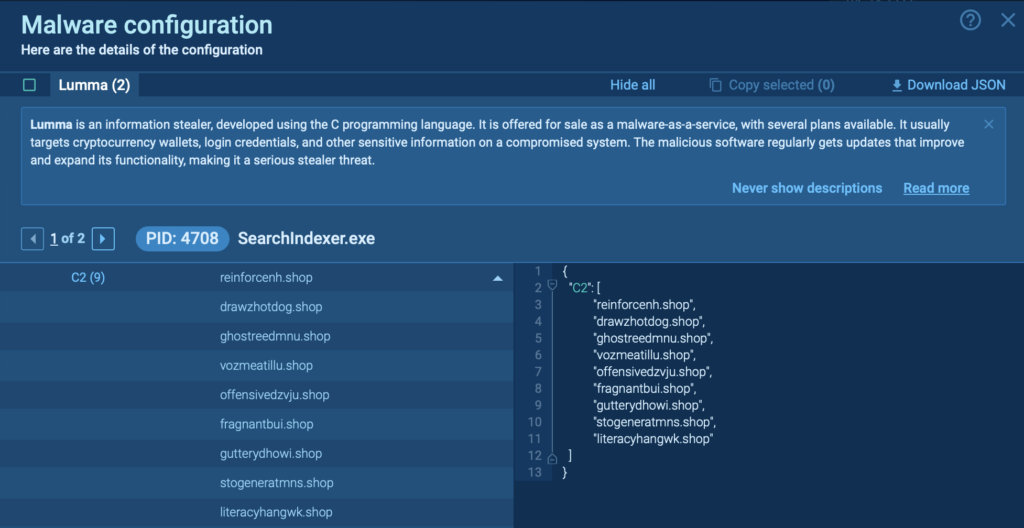
The feature specifically pulls IOCs from to the malware’s configurations, such as URLs, file hashes, and domains, providing key insights that are crucial for further in-depth investigation and reporting.
Centralized IOC Window
You can easily access all the important indicators in the IOC window.
Simply hit the IOC button located in the top-right corner, and you’ll instantly gain access to the most critical IOCs collected throughout the analysis—whether they come from Static Analysis or Malware Configurations.
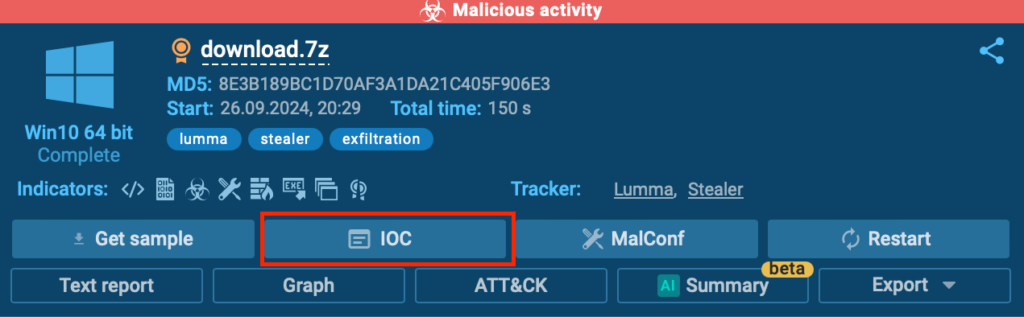
This window saves time and ensures that all critical data is conveniently organized in one place for easier review.
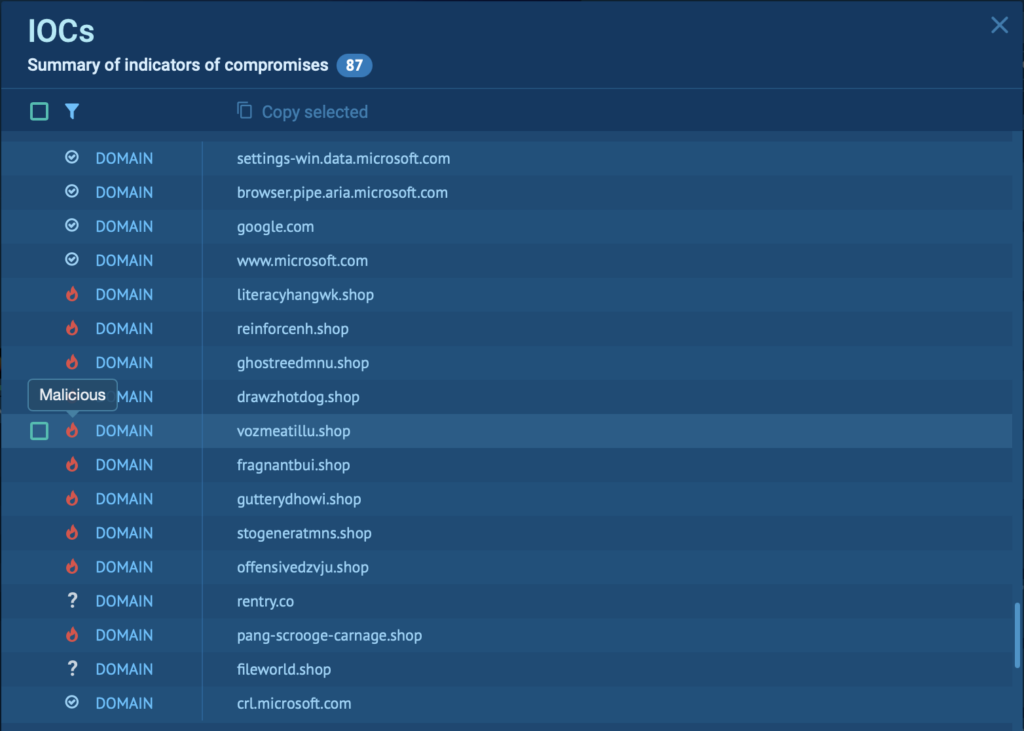
The IOC window is easy to navigate thanks to the simple dropdown menu.
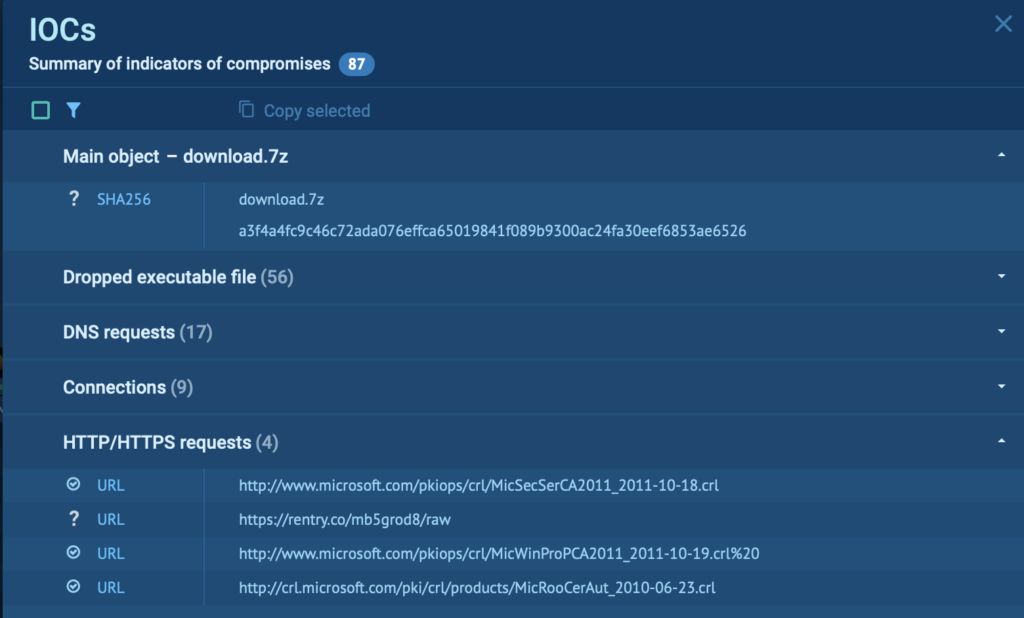
You can quickly filter and organize IOCs. Plus, copying the selected indicators for your reports or further analysis is just a click away, making the whole process smooth and efficient.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need







0 comments