Cybersecurity is not just about defense, it is about protecting profits. Organizations without modern threat intelligence (TI) face escalating breach costs, wasted resources, and operational inefficiencies that hit the bottom line.
Here is how actionable intel can help businesses cut costs, optimize workflows, and neutralize risks before they escalate.
Key Takeaways
- TI turns security into a cost-saving engine by preventing breaches that could otherwise drain millions in recovery and reputational damage.
- Automation eliminates labor waste, allowing SOC teams to focus on high-value tasks instead of drowning in false positives.
- TI drives faster response which minimizes disruptions, reducing downtime and the cascading financial losses that follow.
- Continuous intelligence future-proofs defenses, keeping organizations ahead of evolving threats without constant manual updates.
- Seamless integration protects existing investments, embedding TI into current workflows without costly overhauls.
3 Hidden Costs of Ignoring Threat Intelligence
1. SOC Inefficiency and Burnout
When SOC analysts lack high-fidelity, context-rich threat intelligence, they are forced to manually investigate thousands of alerts, many of which turn out to be false positives. This relentless cycle wastes time, drains budgets, increases turnover, and leaves critical threats unaddressed.
Without automation and precise data, teams operate in a constant state of reactive chaos, where even minor incidents consume disproportionate resources.
- False positives cost enterprises $1.3M annually in wasted labor.
- Analyst burnout makes people over two times more likely to look for a new job.
2. Undetected Threats Escalate into Financial Disasters

Cyberattacks exploit gaps in visibility and slow response times. Organizations relying on outdated or generic TI feeds often miss targeted, evasive threats until it is too late. By the time a breach is detected, the damage in terms of downtime, regulatory fines, and lost customer trust has already begun. The financial effects of a single incident can cripple budgets and erode market position for years.
- $4.4M is the average breach cost for companies today.
- 60% of SMBs close within 6 months of a breach.
3. Compliance Gaps Trigger Fines and Legal Risks
Regulatory bodies do not accept “we didn’t see it coming” as an excuse. Without real-time, comprehensive TI, organizations struggle to detect, document, and mitigate threats in ways that satisfy auditors. The result is hefty fines, legal battles, and mandatory security overhauls that could have been avoided with proactive intelligence.
- GDPR fines may constitute up to 4% of global revenue or €20M.
- HIPAA violations may reach $1.5M+ per incident.
5 Ways Threat Intelligence Saves Money and Resources
1. Helps Stop Breaches Before They Start
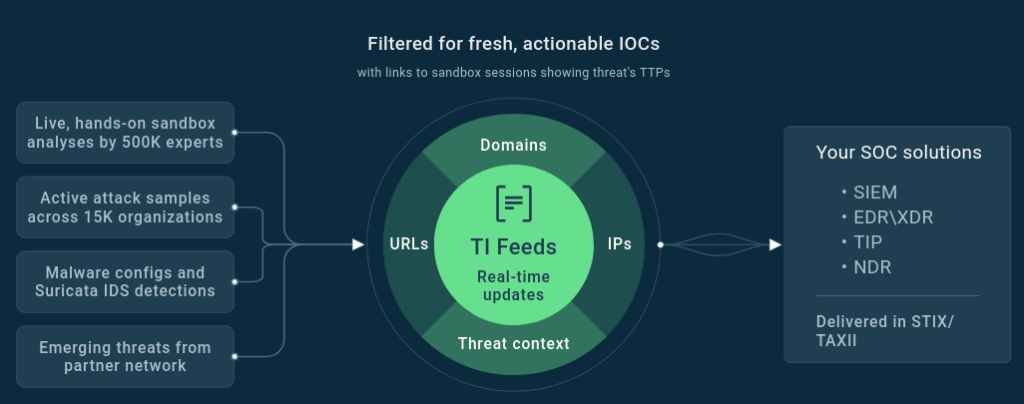
The financial impact of a cyberattack extends far beyond the immediate incident. Downtime, regulatory penalties, and reputational harm can accumulate into millions in losses even for a single event. Most organizations do not realize how many attacks slip through their defenses until it’s too late. The difference between a near-miss and a full-blown crisis often comes down to how quickly and accurately threats are identified.
ANY.RUN’s Threat Intelligence Feeds provide actionable, real-time intelligence needed to block threats at the earliest stage. Instead of reacting to breaches after the fact, teams can neutralize risks before they execute, turning potential disasters into routine intercepts.
How ANY.RUN Helps:
- TI Feeds and Threat Intelligence Lookup deliver 24× more IOCs per incident from 15,000+ SOCs’ real-world investigations, offering instant, deep context on emerging threats, so analysts confirm and contain attacks in seconds.
2. Eliminates Wasteful Spending on False Positives
SOC teams are overwhelmed by alert fatigue, with analysts spending hours each day chasing down irrelevant or duplicate threats. This becomes both a productivity issue and a financial drain, as organizations pay for overtime, burnout, and unnecessary tooling that does not address real risks. The problem compounds when teams lack the context to prioritize threats effectively, leading to misallocated resources and missed critical alerts.
ANY.RUN’s solutions filter out the noise, ensuring teams focus only on verified, high-impact threats. This shift saves time and redirects budgets from wasteful investigations to proactive and fast incident handling.
How ANY.RUN Helps:
- TI Feeds cut through irrelevant alerts, delivering only filtered, malicious IOCs, which saves hours of work and speeds up response.
- TI Lookup enriches alerts with threat context, including TTPs and additional indicators so teams prioritize based on actual risk.
3. Cuts Labor Costs with Automated Triage
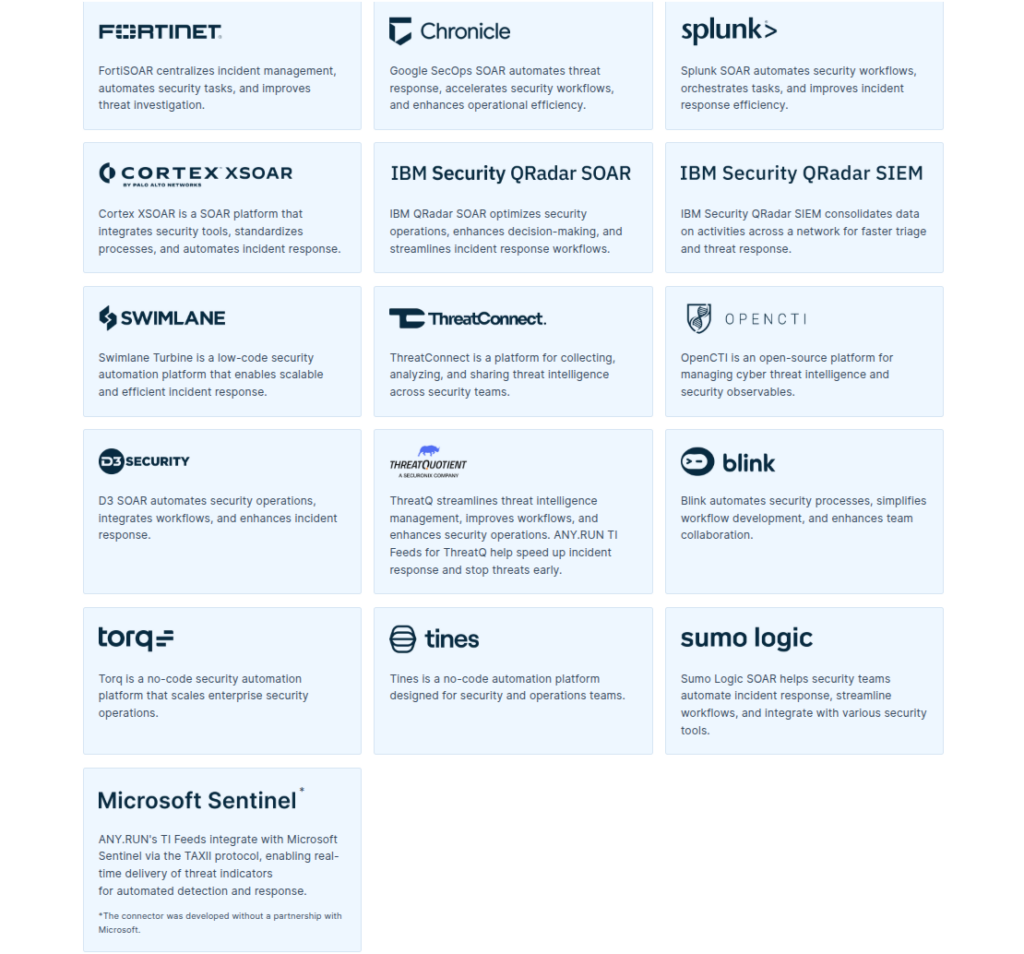
Manual threat triage is one of the biggest hidden expenses in cybersecurity. Analysts stuck in repetitive, low-value tasks burn out and cost more in overtime and turnover. Delayed responses increase breach risks and force costly retraining.
Thanks to plug-and-play integrations and API/SDK support, ANY.RUN’s TI solutions connect seamlessly with SOCs’ current software and enhance existing workflows. This reduces unnecessary escalations from Tier 1 to Tier 2 analysts, cutting labor costs and increasing the alert handling capacity without extra hiring.
How ANY.RUN Helps:
- TI Lookup can be used to automatically enrich alerts and artifacts, reducing triage time to seconds and giving analysts the context they need to act independently.
- TI Feeds stream live IOCs via STIX/TAXII directly into SIEM/SOAR/firewall/EDR and other solutions, eliminating manual data entry.
4. Accelerates Response to Minimize Financial Fallout
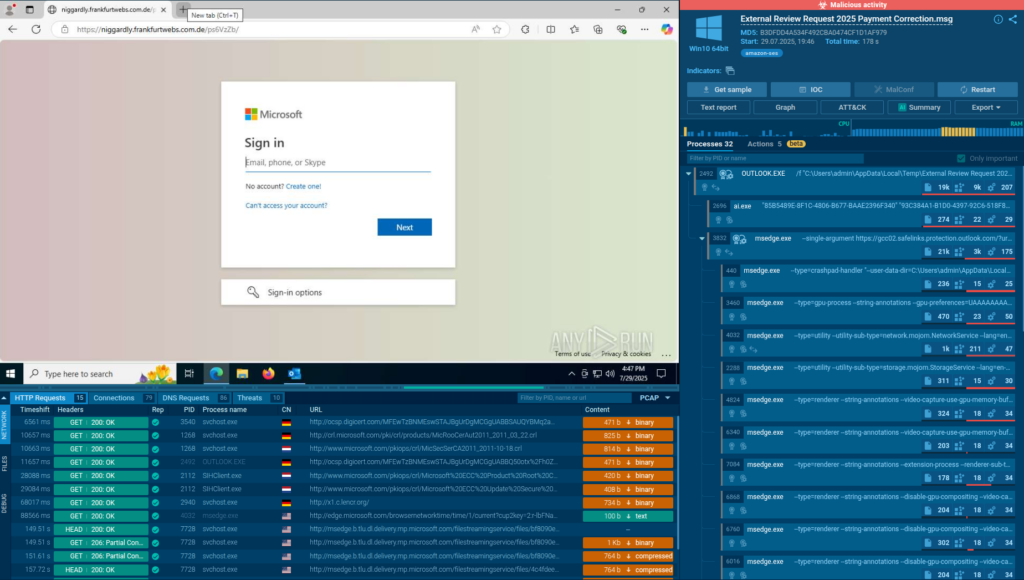
Every minute counts during a cyber incident. Slow detection and response prolong downtime and amplify financial losses, from regulatory fines to customer churn. Organizations without real-time, context-rich TI often struggle to collect actionable insights, delaying critical decisions and letting attacks spread unchecked.
ANY.RUN’s TI Lookup provides instant, deep context, including a full attack view based on a single indicator, so teams can quickly understand the threat they are dealing with and respond decisively without guesswork. Faster responses limit damage, preserve revenue, and protect customer trust, turning potential crises into manageable events.
How ANY.RUN Helps:
- TI Lookup provides sandbox detonation context for threats, so SOCs can see how malware acts on a real system and use the findings to contain it in their infrastructure.
- TI Feeds supply links to sandbox reports for each indicator, which immediately provides security teams with full visibility into the detected threat’s actions.
5. Keeps SOCs Up-to-date on Evolving Threats without Manual Work
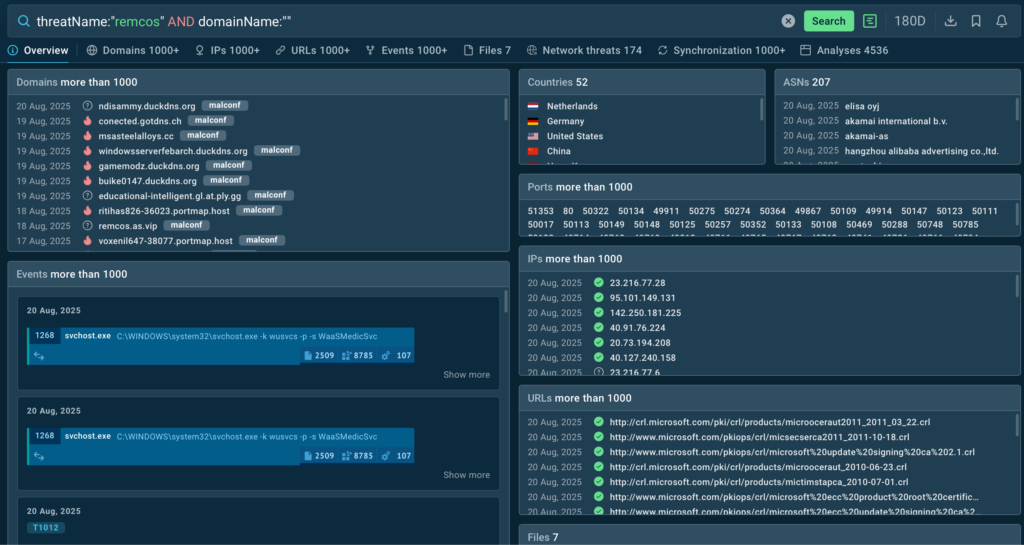
Cyber threats evolve daily, but most TI feeds update weekly or monthly, leaving gaps that attackers exploit. Organizations stuck with static, generic IOCs are forced into reactive, costly fixes every time a new attack emerges. This approach poses a direct financial risk, increasing the likelihood of malware slipping through outdated defenses.
ANY.RUN’s TI Feeds update continuously with data from live investigations by 500,000 security analysts, ensuring defenses adapt automatically to new threats. TI Lookup’s MITRE ATT&CK integration helps teams anticipate attacker moves, turning security from a cost center into a strategic advantage.
How ANY.RUN Helps:
- TI Feeds are continuously updated in real time, delivering 99% unique IOCs, so SOCs can stay ahead of emerging threats and detect attacks that are missed by other tools.
- TI Lookup’s Query Updates help SOCs to get new indicators and samples for threats of their interest to keep up with evolving infrastructure and enrich proactive defense.
Success Story: International Transport Company
Challenge
A transportation company faced constant cyber threats, especially through email phishing and malware attacks. Attackers frequently changed their infrastructure, making it hard to track and block threats in time. The security team struggled to manually monitor evolving attacks, which risked exposing sensitive communications and disrupting operations.
Solution
The company used ANY.RUN’s Threat Intelligence Lookup to automate threat tracking. They set up custom search queries for specific threats like geo-targeted attacks, CVEs, and phishing domains and subscribed to real-time updates. This allowed them to focus on active threats, convert new threat data into detection rules, and respond faster without manual searches.
Results
- Faster Threat Detection: Automated alerts helped the team spot and block attacks like phishing and malware campaigns before they caused damage.
- Better Resource Use: The team saved time by reducing manual research, letting them focus on high-priority threats and improve overall security.
- Proactive Defense: Real-time updates on active threats allowed the company to strengthen defenses and stay ahead of attackers..
Conclusion
Threat intelligence solutions like ANY.RUN’s TI Feeds and TI Lookup both improve security and deliver measurable cost savings, resource optimization, and risk reduction. By automating triage, eliminating false positives, and accelerating response, businesses can:
- Avoid breach-related costs (downtime, fines, reputation damage).
- Cut labor expenses (overtime, hiring, turnover).
- Optimize security budgets (focus on high-impact threats).
- Future-proof defenses (adapt to evolving attacks).
About ANY.RUN
ANY.RUN is built to help security teams detect threats faster and respond with greater confidence. Our Interactive Sandbox delivers real-time malware analysis and threat intelligence, giving analysts the clarity they need when it matters most.
With support for Windows, Linux, and Android environments, our cloud-based sandbox enables deep behavioral analysis without the need for complex setup. Paired with Threat Intelligence Lookup and TI Feeds, ANY.RUN provides rich context, actionable IOCs, and automation-ready outputs, all with zero infrastructure burden.








0 comments