Last year, we introduced Automated Interactivity — a feature that simulates user behavior inside the ANY.RUN sandbox to automatically force cyber attack execution.
The first stage of Automated Interactivity focused on basic user interactions like clicking buttons and completing CAPTCHA challenges. This allowed many analysts to simplify their investigations and streamline the sandbox use via API.
Today, we are excited to announce the release of the next stage of Automated Interactivity — the Smart Content Analysis mechanism that takes its threat detection capabilities to a new level, delivering better and more in-depth examination of the most complex attacks.
Here’s what you need to know about this exciting upgrade.
What is Smart Content Analysis
Smart content analysis is a mechanism that enables Automated Interactivity to execute malware and phishing attacks by identifying and detonating their key components at each stage of the kill chain.
It works in three steps:
- Content Identification: It scans uploaded samples for notable content, such as URLs and email attachments.
- Content Extraction: It extracts the content that needs to be detonated to force the attack to move forward like URLs from QR codes and phishing links that were rewritten by security tools.
- Simulated User Interactions: It then simulates user interactions with the extracted content, for instance, by opening URLs in a browser and launching malware payloads inside archives.
How Smart Content Analysis Adapts to New Threats
Unlike traditional automated solutions that are limited by pre-programmed algorithms, ANY.RUN’s Smart Content Analysis is built to continuously evolve with the current threat landscape.
Our team of threat analysts update it with new attack scenarios as soon as they are detected. This ensures nearly instant adaptability to the latest threats and techniques.
Why Use It
The upgraded version of Automated Interactivity is an excellent addition to your security workflow, as it:
- Improves threat detection for sandbox sessions launched via API
- Helps security specialists with analysis by automating complex tasks, providing them with valuable insights and reducing the learning curve
- Automates repetitive tasks, reducing the manual effort required for threat analysis and allowing analysts to focus on more strategic activities
- Speeds up analysis by quickly identifying and analyzing threats, enabling faster response and remediation
Types of Content It Can Detonate
Smart Content Analysis can automatically identify and detonate different types of content when moving along the kill chain, including:
- URLs inside QR codes: It can automatically extract and open URLs embedded within QR codes, a common tactic for phishing attempts or malware distribution.
- Modified Links: Security solutions and spam filters can often rewrite malicious URLs to prevent them from reaching users. This can prevent automated sandboxes from forcing the attack execution beyond the safe link. Smart Content Analysis easily removes the security layer and detonates the original malicious URL.
- Multi-Stage Redirects: Many cyber attacks employ complex chains of redirects to obfuscate their final destination. Smart Content Analysis quickly locates the hidden page by bypassing the redirect ones.
- Email Attachments: Email attachments are a popular method for attackers to deliver malware. Smart Content Analysis can automatically process and detonate these attachments, as well as their contents.
- Payloads within Archives: Modern attacks often utilize archives (ZIP, RAR, etc.) to bundle malicious payloads. Smart Content Analysis executes these payloads with no problem.
Use Cases for Upgraded Automated Interactivity
Extracting URL from QR and Solving a CAPTCHA
Let’s demonstrate how Automated interactivity works using a multi-stage phishing attack that starts with an email:
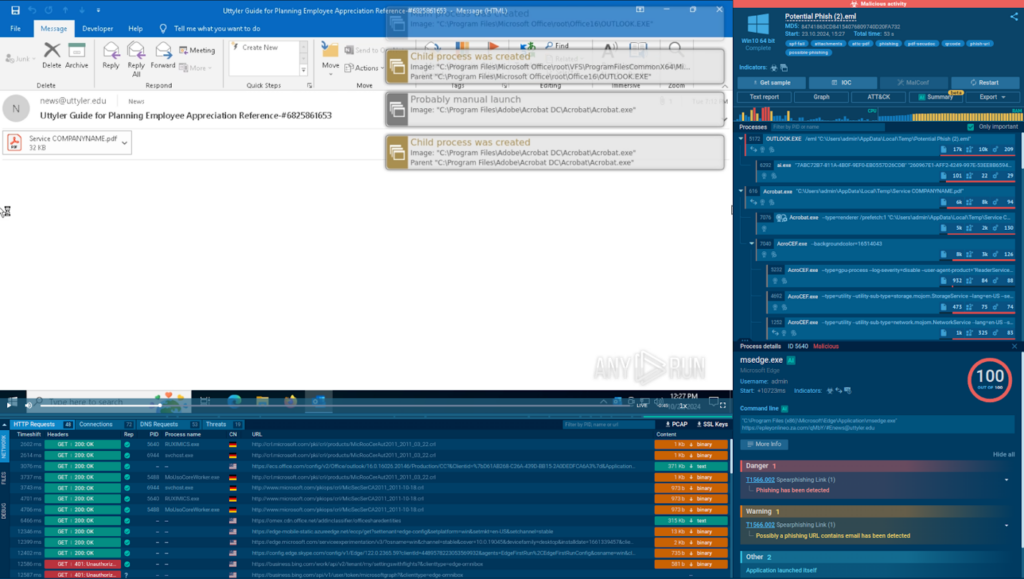
Step 1: We upload the email file to the ANY.RUN sandbox, switch on Automated Interactivity, and start analysis.
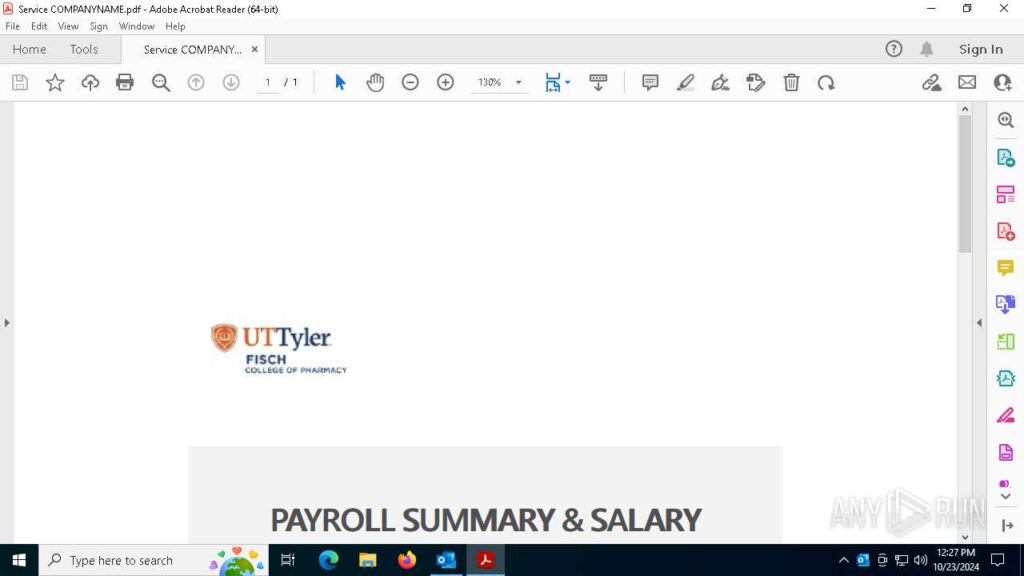
Step 2: Automated Interactivity launches the .eml file via Outlook, identifies a PDF attachment, and opens it.
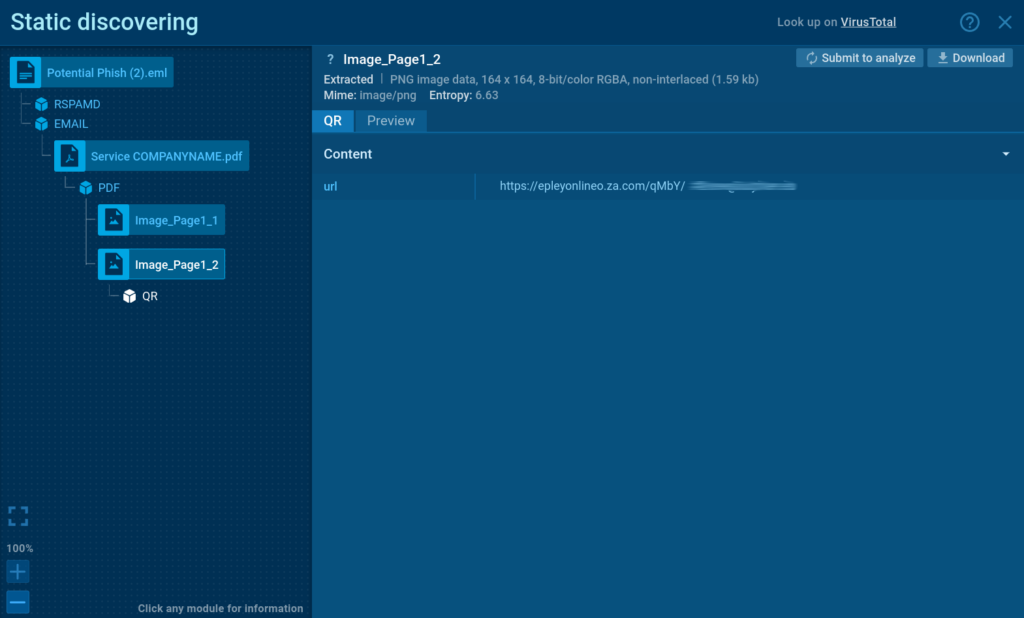
Step 3: After scanning the PDF, it detects a QR code, automatically extracts its embedded URL, and opens it inside a browser.
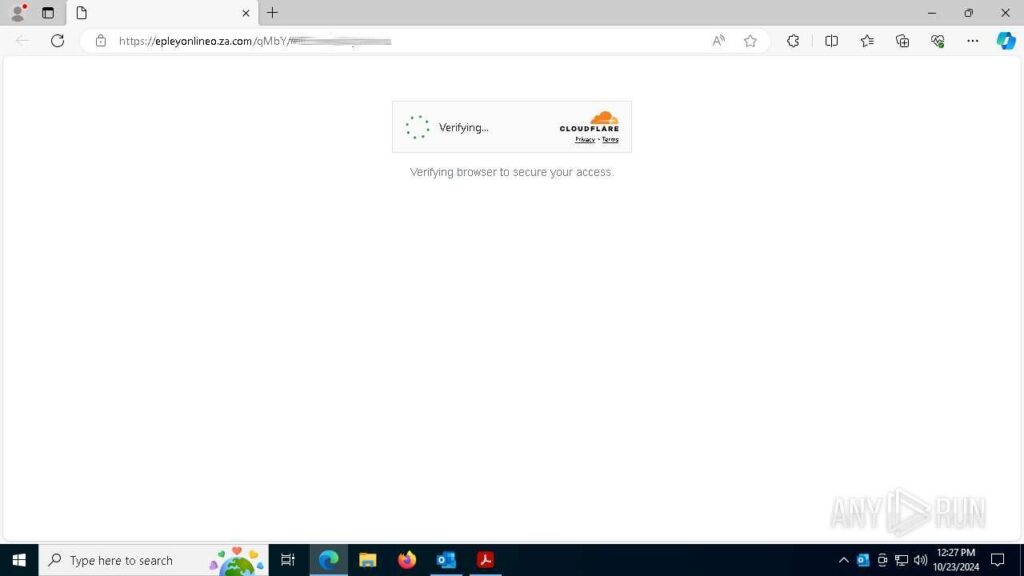
Step 4: The opened page has a CAPTCHA challenge, a common method for evading detection. Thanks to Automated Interactivity, the sandbox successfully solves the CAPTCHA and proceeds to the next stage.
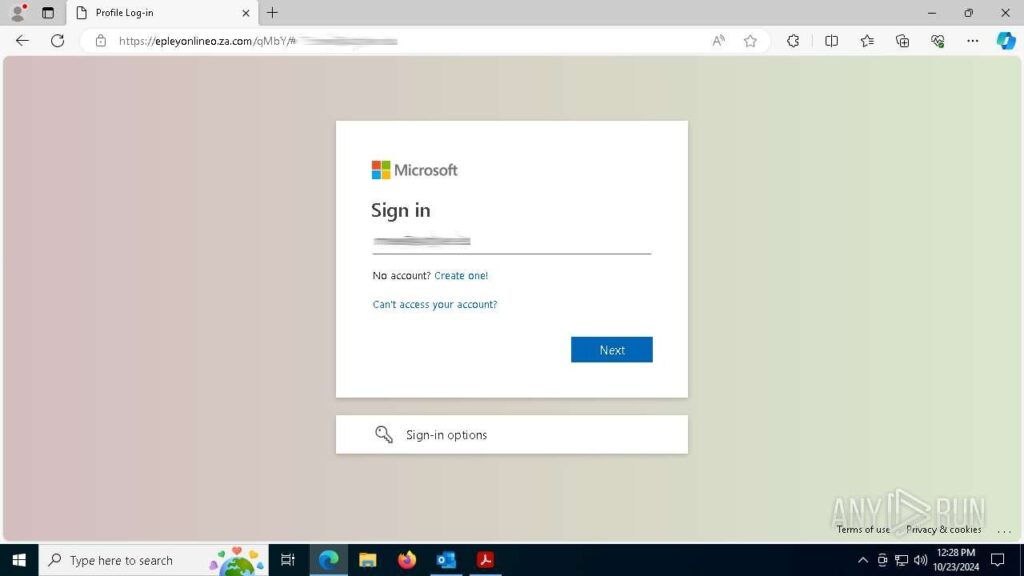
Step 5: Once the final phishing page is loaded, the sandbox instantly assigns the “phish-url” tag to the session and marks it with the “malicious activity” label.
Forcing Formbook Execution from an Archive Attachment
Automated Interactivity is also excellent for analyzing malware attacks.
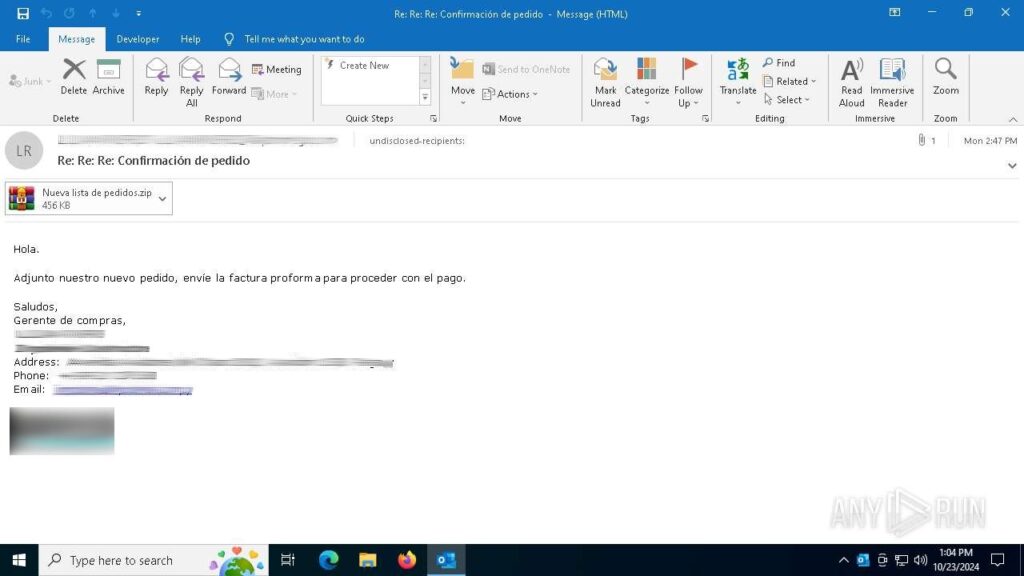
Consider the following analysis session where the feature was used to detonate a sample of Formbook distributed via a phishing email.
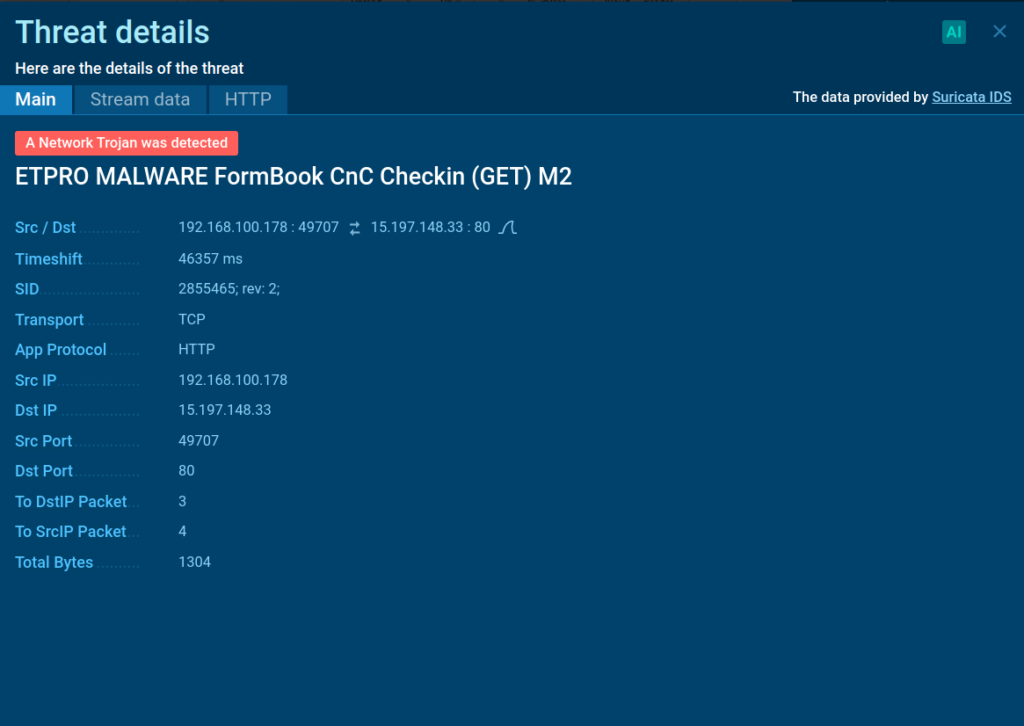
The service was able to automatically extract the ZIP file found in the email. It then identified a Formbook executable inside the archive and ran it to observe its behavior.

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Extracting Rewritten URL
Modern email systems are equipped with spam filtering. While it protects users against threats, it complicates the work of security analysts by blocking their access to the actual malicious content that they wish to examine.
Automated Interactivity bypasses such filters and quickly reaches the resources controlled by the threat actors, saving analysts’ time.
Here is a sandbox session featuring a blocked phishing URL.
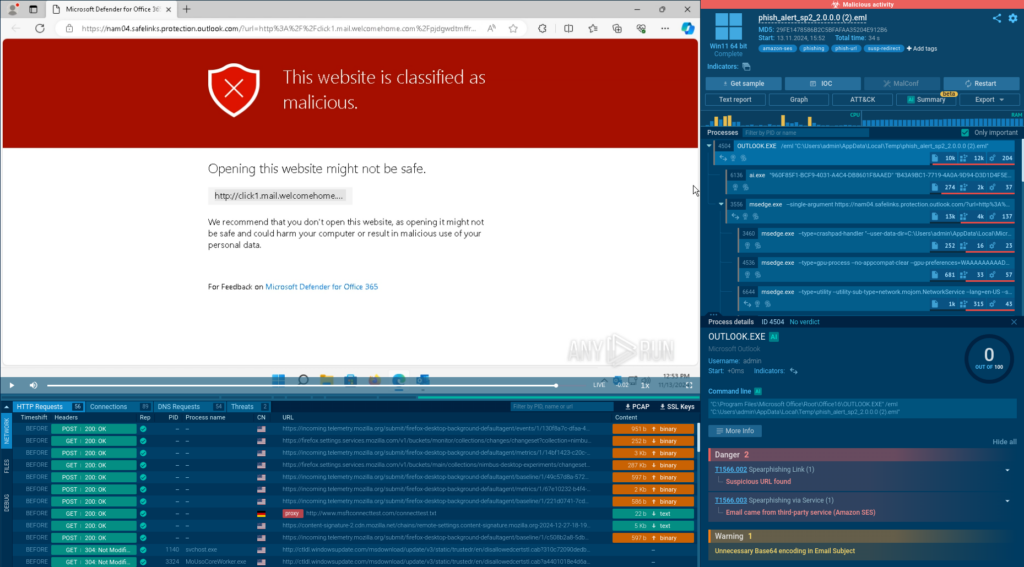
The phishing link inside the analyzed email is rewritten to Microsoft’s domain safelinks[.]protection[.]outlook[.]com and now contains a warning.
While it indicates that the link is malicious, it prevents us from learning more about the threat we’re facing.
To go beyond the block, we can simply enable Automated Interactivity and rerun the analysis.
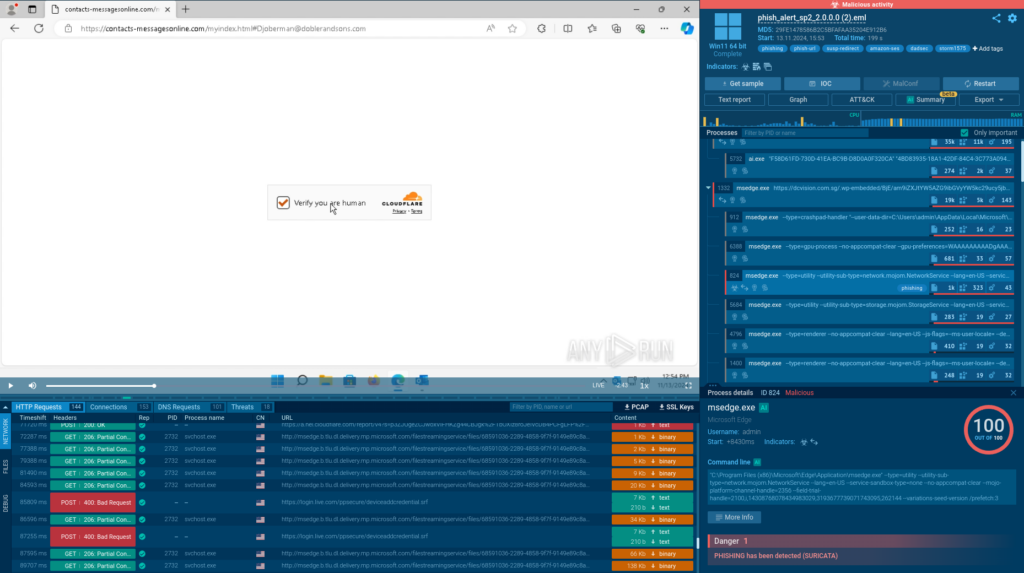
In the new sandbox session, the rewritten URL is skipped, and all the stages of the attack, including those requiring solving a CAPTCHA, are detonated automatically and as intended.
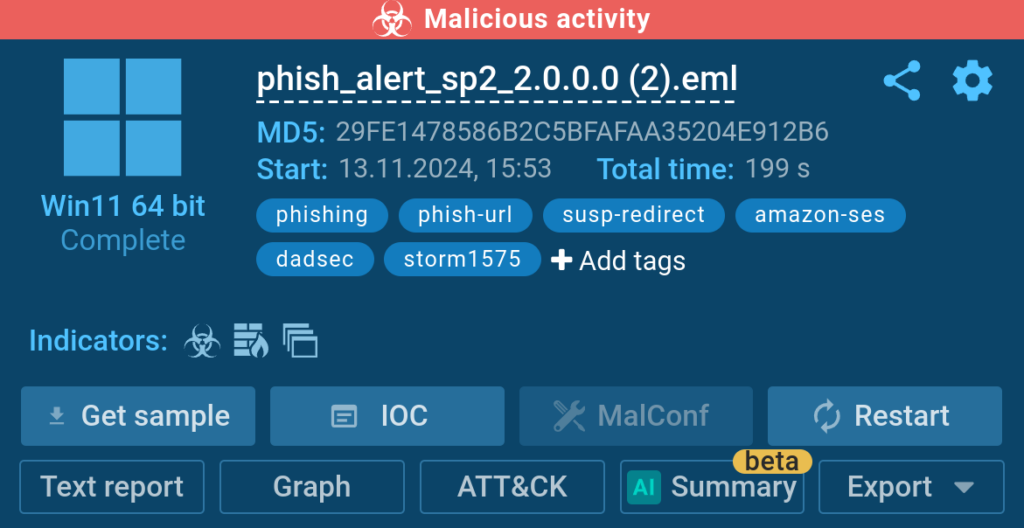
This allows us to go further and discover that the attack is carried out by the Storm-1575 threat actor using the DadSec phishing platform, as shown by the corresponding tags.
What’s Next for Automated Interactivity
Smart Content Analysis is not the final chapter of Automated Interactivity.
We are already working on Stage 3 — another mechanism that will further improve the detection rate and make the sandbox even better at automatically detonating attacks.
Stay tuned for updates!
Try It Now
See how you can speed up your analysis of the latest cyber attacks with Automated Interactivity. The feature is available to Hunter and Enterprise-plan users. It is also activated by default for all sandbox sessions launched via API.
To manually enable Automated Interactivity:
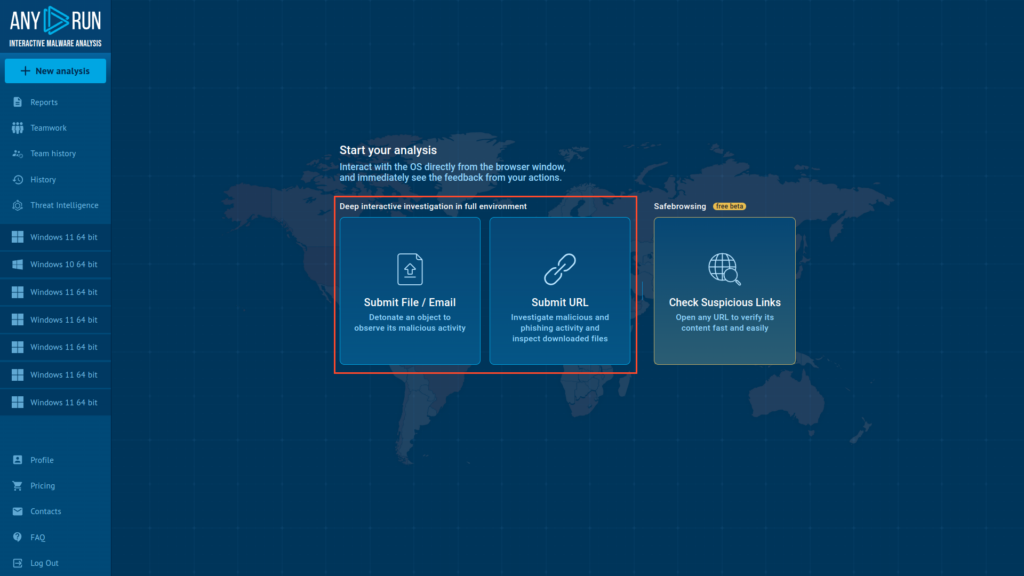
1. Navigate to ANY.RUN’s home screen and submit your sample
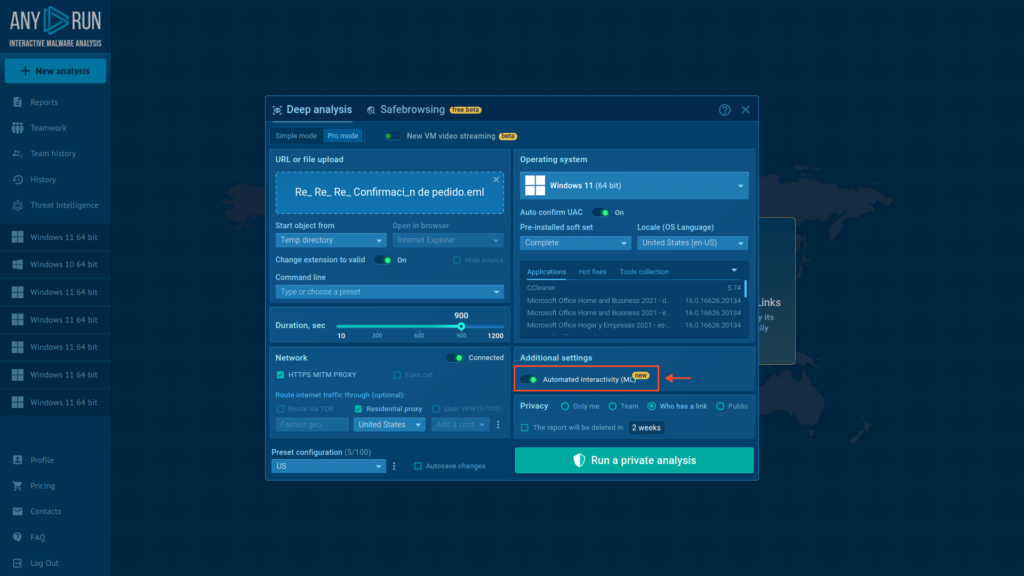
2. Switch on the Automated Interactivity (ML) toggle
3. Run analysis
You can get a 14-day free trial of ANY.RUN’s Interactive Sandbox to try Automated Interactivity along with other PRO features like private and teamwork mode, as well as integration via API and SDK.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need







0 comments