At ANY.RUN, we offer four pricing plans: Free, Hunter, and Enterprise. While the first three are perfect for individual researchers and small companies, they may be limiting for work in large corporate environments.
If your Security Operation Center (SOC) or threat research teams have 5 or more members, if you actively manage team access, or need to drive alignment across security departments — you might benefit from the Enterprise plan.
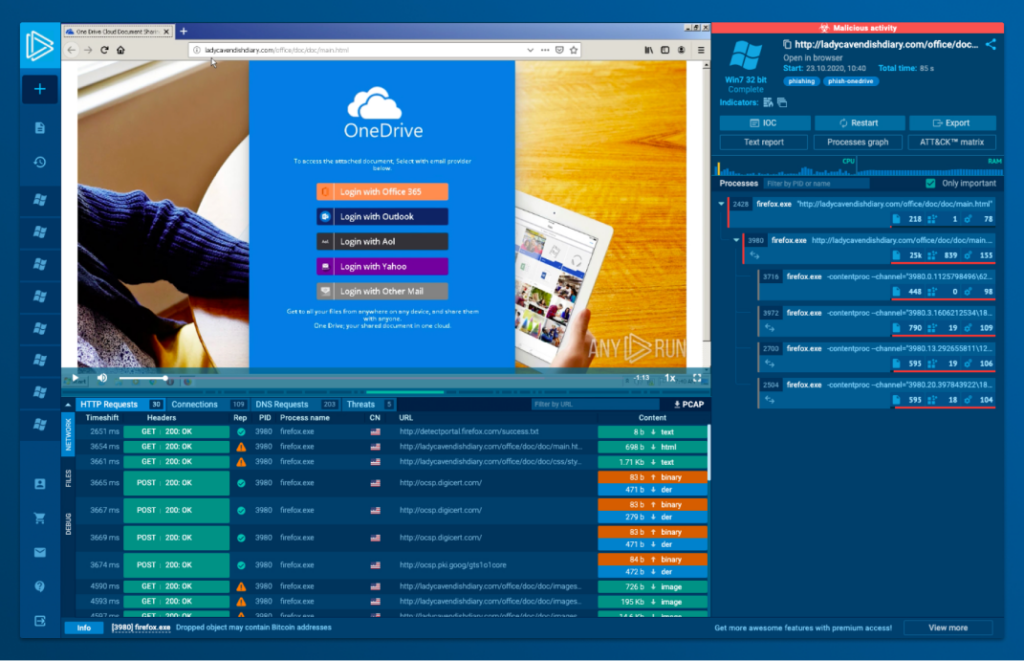
How the Enterprise plan helps teams stay in sync
We know that managing security teams can be difficult: tracking authorization levels, delegating tasks, and setting task restrictions by either team or individual gets progressively more challenging as the headcount of your department grows.
That’s why ANY.RUN’s Enterprise plan has features designed specifically to increase the productivity of large teams.
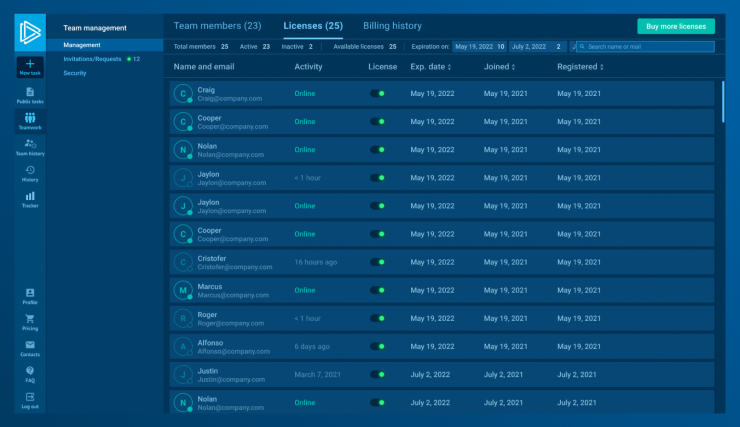
1. License control
Makes it much easier for admins to manage ANY.RUN across enterprises. Team leaders can invite colleagues, distribute and revoke licenses, and create temporary seats with an expiration date.
Let us show you how ANY.RUN can help your SOC team – book a call with us ⬇️
2. Safe work with team privacy
Control over task visibility is more granular, there is two-factor authentication that can be toggled for each team-member for security, and access rights can be tightly controlled: decide who can delete tasks or view employee history.
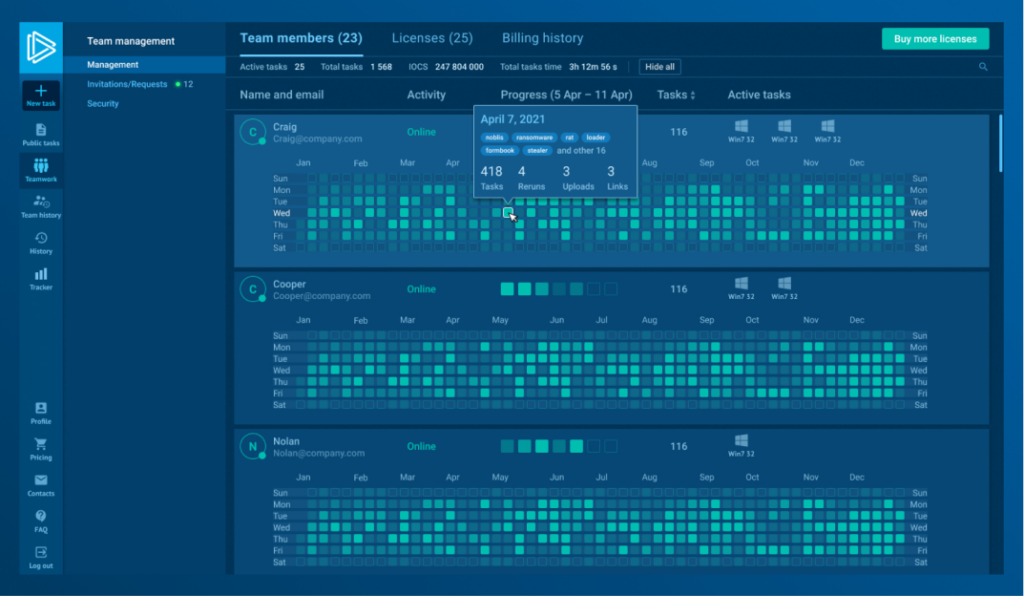
3. Workspace analytics
Gain additional visibility into the workspace: monitor each team member’s activity by day, track the number of tasks completed daily, and filter tasks by assignee or by date.
4. Improved productivity with collaborative workflow
Add multiple team members to the same task to hold supervised analysis sessions, train new hires or crack tricky cases together.
5. Task history via API
Our REST API is designed for companies who want to integrate ANY.RUN into existing frameworks. Fetch task summaries in JSON, retrieve multiple tasks in MISP for subsequent analysis in an IDS or SIEM system, or download the task history of your entire team into your project management software of choice — which is a feature reserved for our Enterprise plan.
The Enterprise plan also inherits all malware analysis capabilities from the Hunter plan — our fullest offering in terms of sandboxing features.
Multiple operating systems and bit options, locale settings to customize execution environment, ability to reboot tasks, network geolocation, and software presets — all to help you save time and increase detection rate.
Here’s what else the Enterprise plan unlocks for you:
- Add 15 minutes to virtual machines. Do more with longer task completion times and never worry about the time limit.
- Analyze files up to 100 MB. Easily analyze malware, no matter the file size.
- Control task privacy. Choose between public and private tasks to control who can see them.
- Priority in the queue. Launch tasks faster and start process monitoring right away with priority queueing.
- Set up a custom VPN. Protect your team’s privacy with a personalized OpenVPN configuration.
- Hunt C2 servers with FakeNet. Intercept HTTP requests and return a 404 error to reveal the Command-and-Control address of malware.
- Synchronize security teams with a custom API. Automatically submit files and URLs for analysis or download them from ANY.RUN to keep your security teams in sync.
And if the Enterprise plan seems like overkill, don’t forget that ANY.RUN has other pricing options!










0 comments