Welcome to ANY.RUN‘s monthly updates, where we share our team’s achievements over the past month.
In July, we introduced new features in Threat Intelligence Lookup, added Windows 10 for free users, reduced task startup time, implemented numerous YARA rules and signatures, and expanded our Suricata ruleset.
Let’s break down what’s new in ANY.RUN step by step.
Product Updates
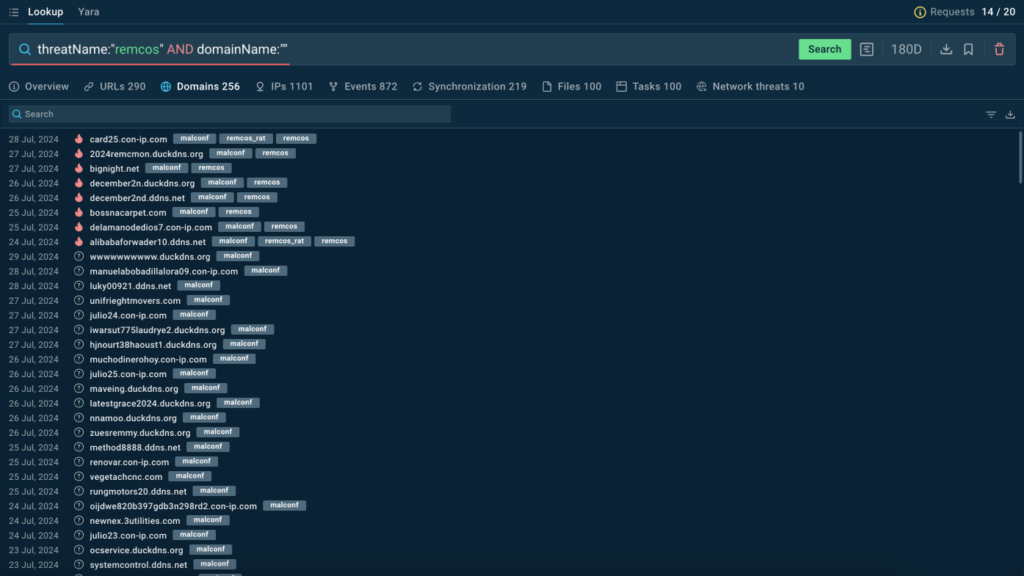
IOCs from malware configurations in TI Lookup
IOCs extracted directly from malware configurations are the most reliable means to identify attackers’ infrastructure. TI Lookup now gives you access to these IOCs, labeling them with the “malconf” tag.
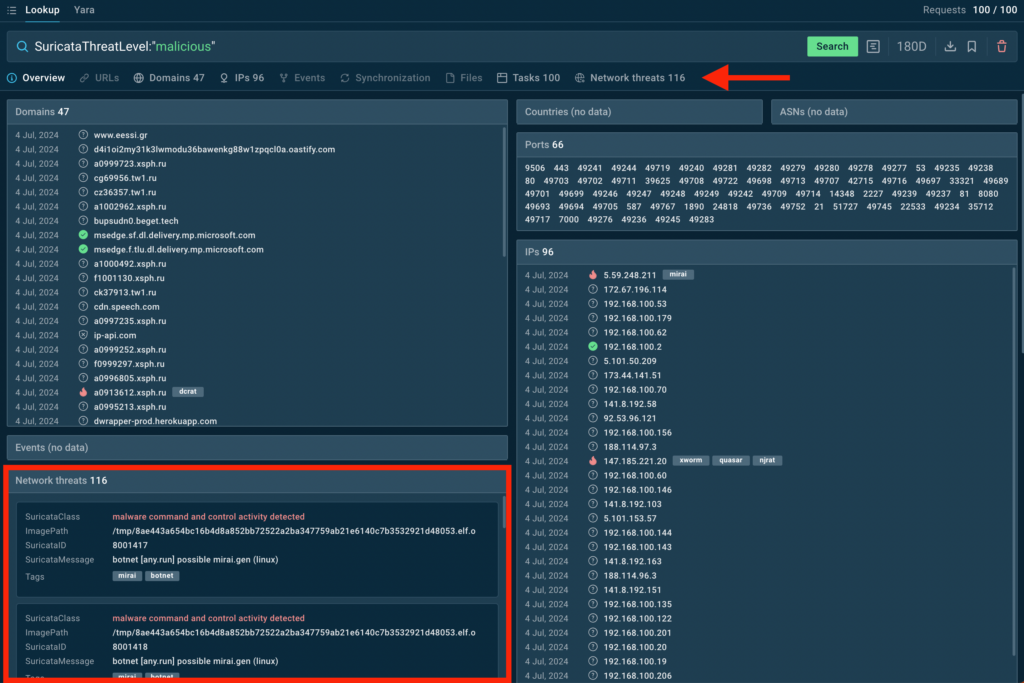
Suricata search in TI Lookup
We’ve also added a new Suricata search feature, allowing you to use parameters like SuricataClass, SuricataMessage, SuricataThreatLevel, and SuricataID to find specific network threats.
Plus, the Network Threats tab in TI Lookup includes all the discovered Suricata detections, making it easier to identify potential network-based risks.
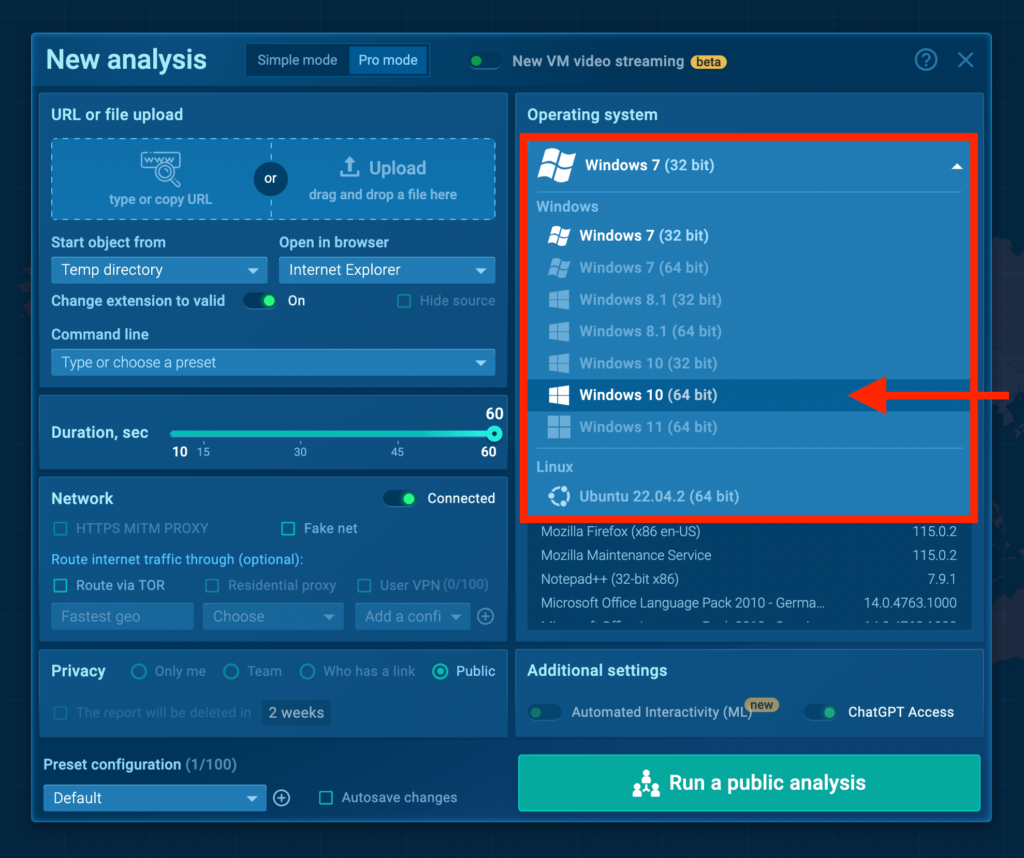
Windows 10 – now free for everyone
We’ve introduced Windows 10 for free users, expanding testing capabilities for all our users.
Analysis sessions take just 5 seconds to start
We’ve significantly optimized our analysis session startup process. Sessions now initiate in less than 5 seconds.
New Signatures
Our malware analysts have been hard at work, significantly expanding our detection capabilities. This month, we’ve added a total of 54 new signatures, including:
- FakeBAT loader.
- Medusa ransomware (2 signatures).
- Borat RAT.
- Blacksuit ransomware (2 signatures).
- Kematian stealer (3 signatures).
- DoNex ransomware.
- DarkRace ransomware.
- Fake-Lockbit ransomware.
- Kematian stealer.
Among them, 35 are new behavioral signatures.
New YARA Rules
Our YARA rule set has also been expanded and refined. New and updated rules cover a wide range of threats, including:
- Luka ransomware.
- Medusa ransomware.
- XMRig (with fixes).
- M0yv (with fixes)
- MetaStealer v.5 TLS Connection.
- Strela Stealer.
- Vidar Stealer.
- XFiles new version.
We’ve also made improvements to existing tools, such as updating the extractor for AsyncRat to now work effectively with BoratRat as well.
Advanced Detection Techniques
In our ongoing effort to stay ahead of evolving threats, we’ve implemented new YARA rules for detecting WMI, PowerShell, and certain WinAPI calls, including their base64 encoded variants.
Expanded Suricata Ruleset
Our Suricata ruleset saw a substantial expansion in July, with the addition of 248 new rules. These include:
- 89 rules targeting fake domains related to the recent CrowdStrike incident. Twitter post. Example in ANY.RUN.
- 46 proactive phishing detection rules.
- 37 informational rules to provide additional context during analysis.
- 35 rules for identifying known phishing domains.
- 11 rules specifically designed to detect redirect sites leading to phishing pages.
About ANY.RUN
ANY.RUN helps more than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.








0 comments