In 2019, an average company took over 200 days to detect an APT attack. Malware can infiltrate networks and stay undetected for prolonged periods, stealing credentials, or spying after employees. Maybe there is one lurking on your machine right now.
Going into 2020, attackers will be relying less on spraying-and-praying. More than half of all attacks will be designed to target particular organizations.
And when hackers target a business, they develop tailored-maid malicious techniques and carefully pick an attack vector. They utilize zero-day exploits and prepare an effective, and carefully selected toolset. They ensure the highest possible chance of successful infection.
Why Malware Stays Undetected?
Most defensive systems analyze incoming traffic at a single point in time. For example, firewalls detect known network signatures and can block malicious traffic. But what if attackers develop an entirely new signature? Or use a completely new malware strain altogether?
If initial defenses let the malware slip by once, the same web traffic will never be analyzed again. Now, the only thing that can give the payload away is artifacts generated during execution. Finding them still requires a lot of manual labor and the use of complex analysis systems. And if that wasn’t enough, some malware samples can work stealthily.
So here’s the bottom line: the chance of getting infected in 2020 is higher than ever before, and once infected, the malware is likely to stay around.
But retrospective malware analysis can just about save the day.
What is Retrospective Malware Analysis?
Retrospective malware analysis is a process of reviewing logs and network activity from a set time period from the past to find traces of malware behavior. It’s a technique that allows researchers to detect malware after it has infiltrated the system.
Retrospective analysis reveals artifacts that can tell a story about the attackers’ actions and uncover the attack vector. What’s more, conducting retrospective analysis regularly is a great way to reduce APT threats.
Security teams usually utilize multiple tools like SIEMs and network traffic analysis software. As such, retrospective analysis is a complex technique. This is where ANY.RUN comes into play.
Retrospective Malware Analysis with ANY.RUN
ANY.RUN is a great tool for getting insights into malware when you don’t have a lot of data to work with. For example, let’s say that you found a suspicious outgoing connection to a domain name, but the payload was never downloaded.
You can use ANY.RUN public submissions to find out which malware strain attacked the network. Let’s presume that we have a connection to sollight.com.hk.
First, open ANY.RUN Public submissions page.
We can see the list of the most recent tasks.
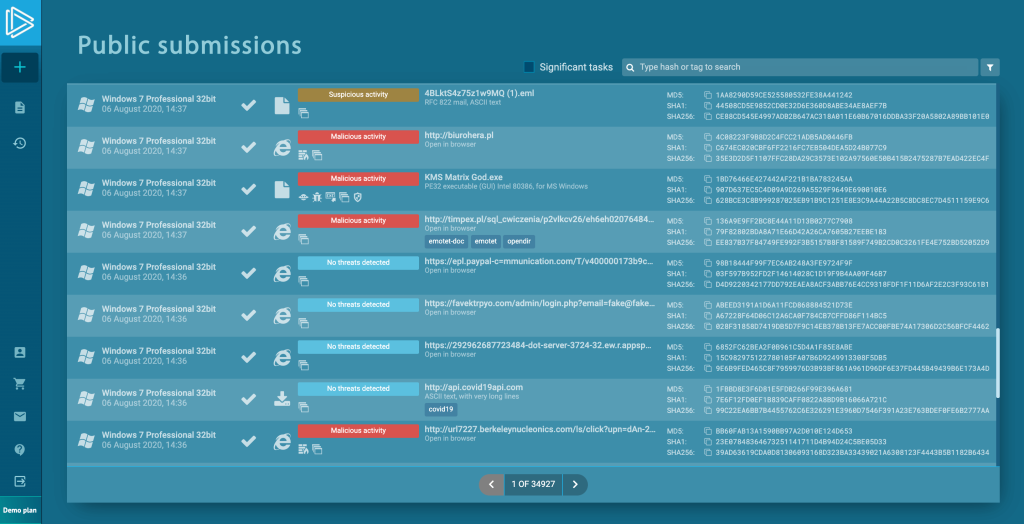
Let’s use the filter icon to bring out the advanced search module.
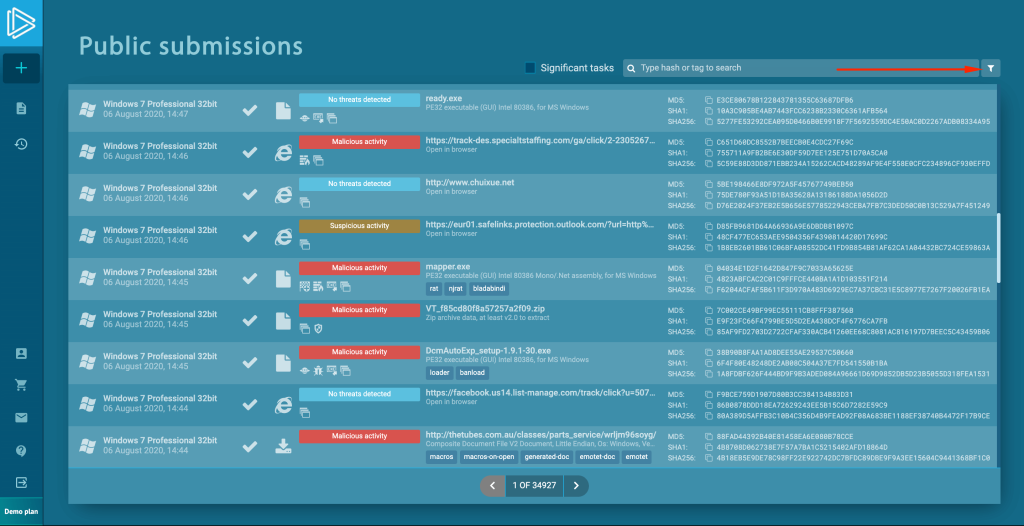
Enter the domain name in the corresponding field. Note that you can also use file hashes, ATT&CK IDs, IP addresses, or Suricata SID numbers to search for malware.
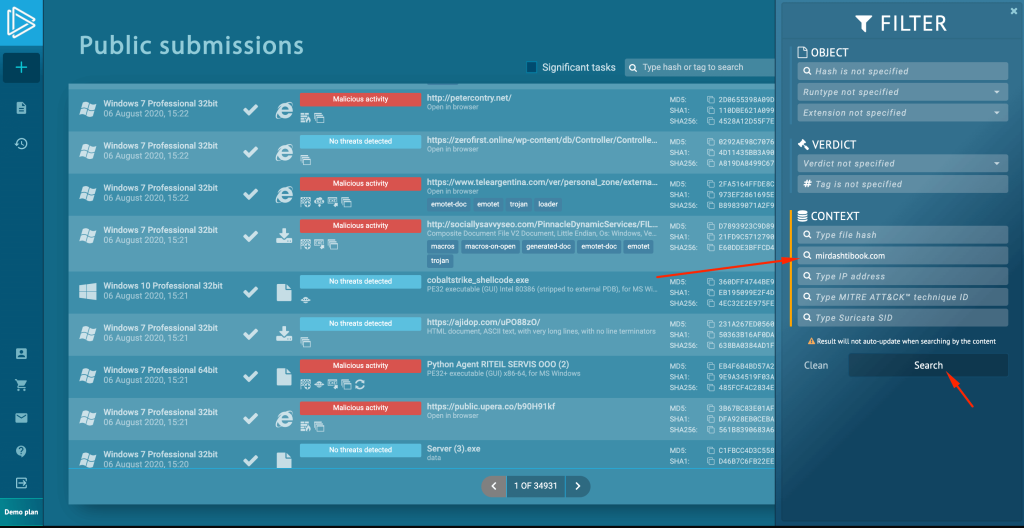
After searching, ANY.RUN displays tasks where outgoing requests to the same domain name have been recorded. Sure enough, some of the tasks classified the threat.
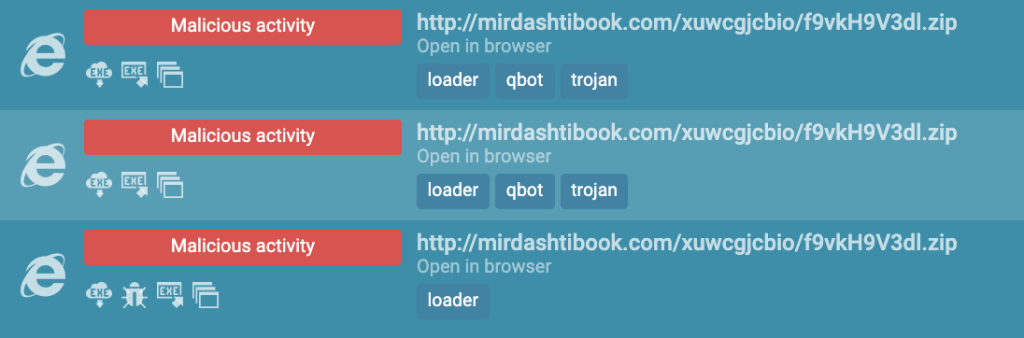
By looking at the tags, we can clearly see that we are dealing with Qbot, also known as the Qakbot trojan.
This way, we established the malware strain in just a few minutes. From here we can explore the task and conduct a behavioral analysis of the threat to learn additional information.
Conclusion
Regular retrospective analysis is a great way to reduce the risk from APT threats or find malware that could have hidden in the system. The process entails dealing with a lot of raw data and sometimes clues that we find can be insignificant on their own.
However, using tools like ANY.RUN, we can quickly get context by using the pieces of uncovered information in a Public submissions search. This way we can save a ton of time and resources, by identifying a threat in minutes.








0 comments