Network stream analysis involves monitoring and examining the incoming and outgoing HTTP requests packet by packet. This helps you identify malware that might be trying to communicate with its control servers or spread to other devices.
When to use network stream analysis?
This technique is handy when you suspect a malware infection but can’t quite pinpoint it. By analyzing network traffic, you can spot unusual patterns or connections.
Network stream analysis also provides valuable insights into malware configuration: proxies, C2 addresses, how the malware packs and retrieves data.
- Figure out what data was stolen. Passwords, logins, cookies: you can track what information has left your system
- Track downloads. You can identify PE file downloads just by looking at the signatures.
How to use the ANY.RUN network stream window
1. Viewing the packets
Locate the packet you need by using the “Network stream” pop-up window on the navigation panel. The window initially displays quick previews so you can quickly scroll through blocks of information.
To examine packet details individually, just select the data you’re interested in. Expand a block by clicking the Show button or directly on the block to reveal the entire packet’s data.
Received and sent packets are displayed in different colors: blue for received and green for sent.
2. Using highlighting
You can use highlighting to help you focus on important information.
- Printable characters such as letters, signs, and figures will be highlighted
- Control characters and others that have less priority will be slightly transparent
If you hold a mouse over the HEX code snippet, its clear text equivalent will be highlighted at the same time.
Highlighting kicks in automatically when you expand a packet. You can toggle it off at anytime with the “higlight chars” toggle.
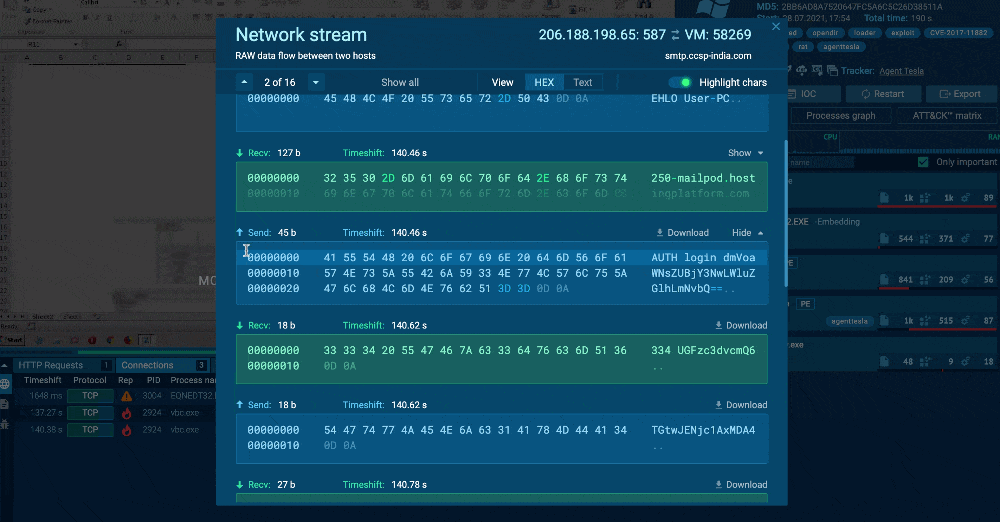
3. Switch between HEX and Text formats
By default, the modal shows HEX data, but you can switch into text mode at any time. In this mode you can also expand packets.
4. View packet details and download packets
The modal header shows the IPs, domain name, the number of sent, and the number of received packets.
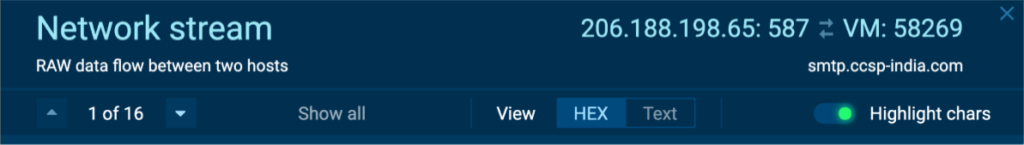
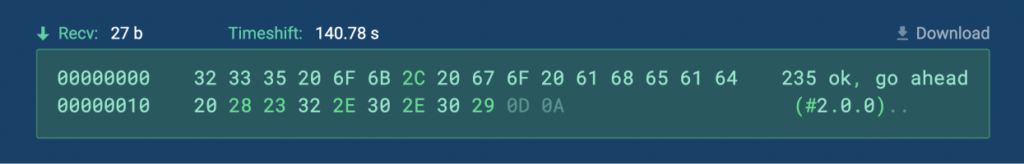
If you select a part of the HEX/cleartext you can download just that part, or you can get the whole packet in binary format using the download button which is above each packet.








0 comments