First month of the year, and we’re starting it off with updates that support faster decisions and more predictable SOC operations.
In January, we introduced a major workflow enhancement with the new ANY.RUN Sandbox integration with MISP, alongside expanded detection coverage across behavior signatures, YARA rules, and Suricata.
Let’s find out what this means for your team.
Product Updates
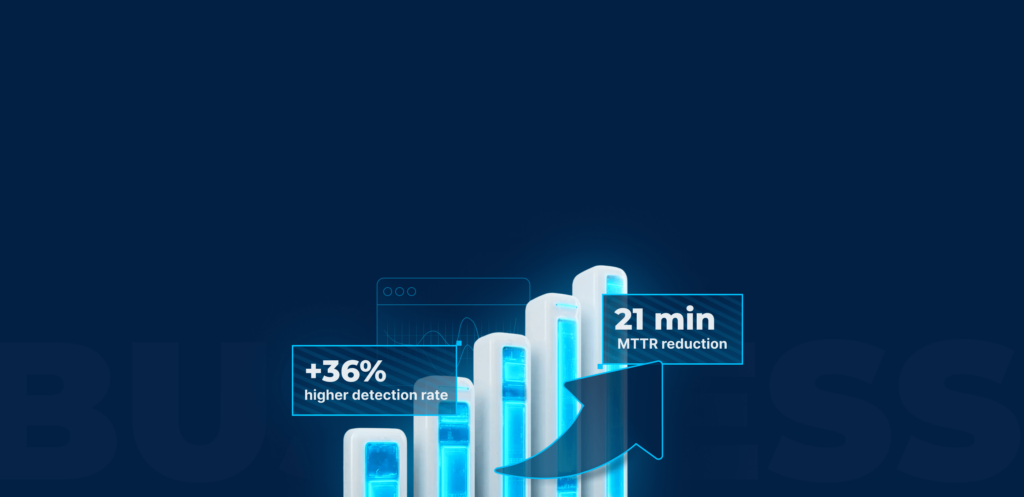
January brought another solid round of improvements focused on practical SOC workflows: faster alert validation, less manual back-and-forth, and earlier decisions that help stop incidents from growing into bigger problems.
The main highlight of the month was the release of the ANY.RUN Sandbox integration with MISP; an important step for teams that use MISP daily for threat intelligence and investigations.
ANY.RUN x MISP: Boost Your Triage & Response
Most SOC teams spend too much time validating alerts, moving samples between tools, and filling in missing context. When execution evidence is separated from threat intelligence platforms, investigations slow down, MTTR increases, and SLAs come under pressure.
With the ANY.RUN Sandbox integration for MISP, analysts can now bring real execution behavior directly into MISP, turning it from a passive intelligence repository into an active investigation layer.
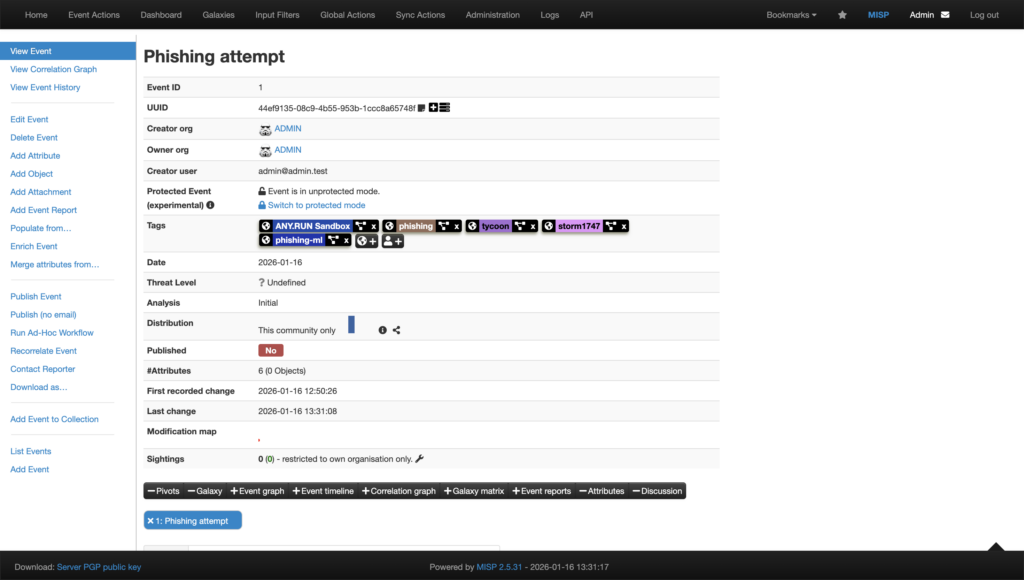
Using native MISP modules, suspicious files and URLs can be sent straight from MISP into the ANY.RUN Sandbox, without any context switching or manual handoffs.
You can easily integrate the modules, using the following links:
Analysis runs automatically using Automated Interactivity. This allows the sandbox to behave like a real user by clicking, opening files, and waiting when needed. This is critical for exposing modern threats that delay execution or hide behind user-driven actions.
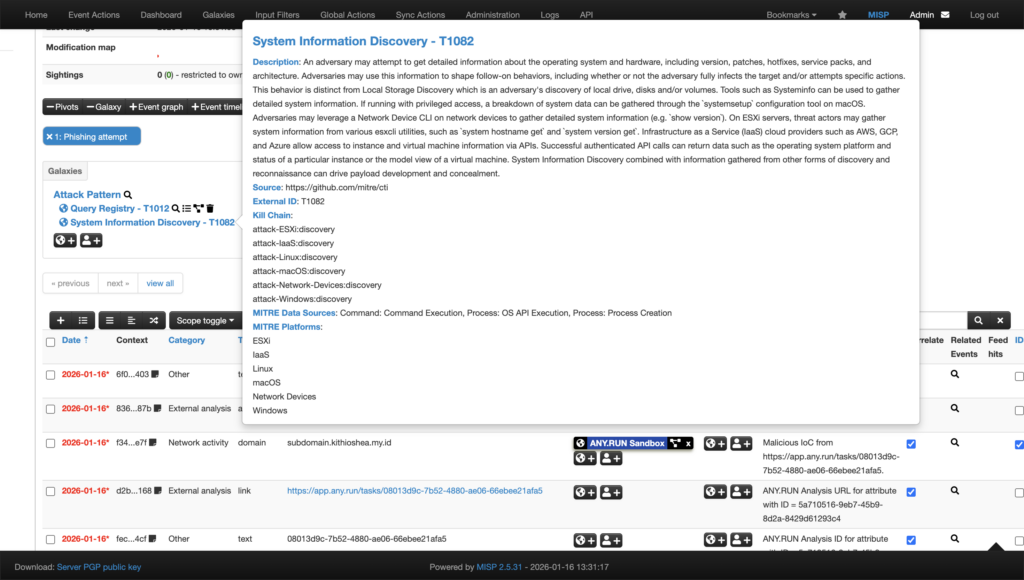
Once execution completes, results are automatically returned to MISP, including, verdict and risk assessment, extracted IOCs, adirect link to the interactive sandbox session, HTML analysis report, mapped MITRE ATT&CK techniques and tactics.
This allows analysts to validate alerts using real behavior, not assumptions, directly inside their existing workflow.
Benefits for Your SOC and Business
For organizations using MISP as part of daily operations, this integration delivers clear operational gains:
- Lower incident costs: Shorter investigations reduce effort per case
- Reduced MTTR: Faster validation and response limit business impact
- Stronger SLA performance: Helps MSSPs meet response time and quality commitments
- No extra headcount: Scale investigation capacity without growing the team
- Zero integration overhead: No custom development required when MISP is already in use

To support proactive coverage at scale, ANY.RUN Threat Intelligence Feeds deliver verified malicious network IOCs from real attacks across 15,000+ organizations, in STIX/TAXII format, ready for use in MISP, SIEM, or SOAR platforms.
Learn more about TI Feeds integration with MISP
- Early detection with continuously updated indicators
- 99% unique indicators for broader coverage
- Verified data to reduce false positives
- Improved correlation across campaigns
- Less manual enrichment work for the team
Threat Coverage Update
In January, our team continued expanding the detection layer across sandbox execution, behavioral analytics, and network visibility, reinforcing ANY.RUN as a unified operational solution for detection, validation, and response.
This month’s updates include:
- 158 new behavior signatures were added to strengthen coverage across ransomware and loader activity, plus common attacker tradecraft, helping security teams spot malicious intent earlier in execution.
- 4 new YARA rules went live in production, improving classification and hunting coverage for active malware and tooling seen in recent investigations.
- 1,897 new Suricata rules were deployed, expanding network visibility for phishing infrastructure (including PhaaS URL patterns), backdoor C2 attempts, and stealer-related HTTP traffic.
Together, these updates help security teams move faster from alert to decision, without switching tools or waiting for late-stage indicators.
New Behavior Signatures
January’s behavior signature updates focus on early-stage execution signals and hands-on attacker activity, helping teams identify malicious intent before payloads fully deploy or damage occurs.
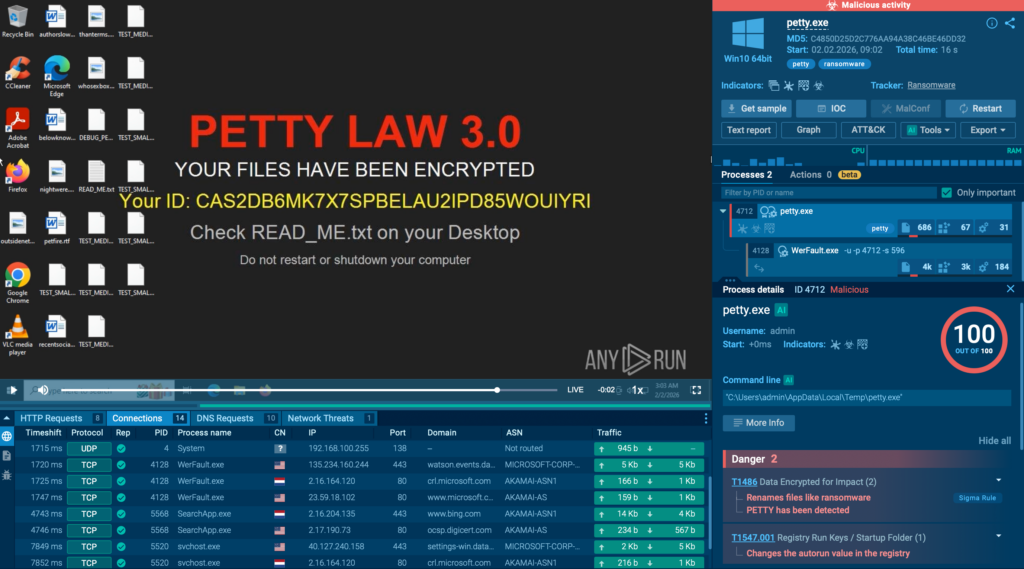
The new detections expand coverage across ransomware families, loaders, stealers, and post-exploitation techniques, with particular attention to abuse of native Windows tooling and suspicious command-line behavior often seen in real-world intrusions.
This month, our team added signatures that detect:
Malware and loader execution patterns, such as
Suspicious use of built-in Windows tools, including
Persistence and system modification techniques, such as
Remote access and administrative tools observed in malicious contexts, including
Mutex- and pattern-based detections, including
New YARA Rules
In January, 4 new YARA rules went live in production, expanding detection and hunting coverage inside ANY.RUN, especially useful when teams need quick classification and reliable pivots during triage.
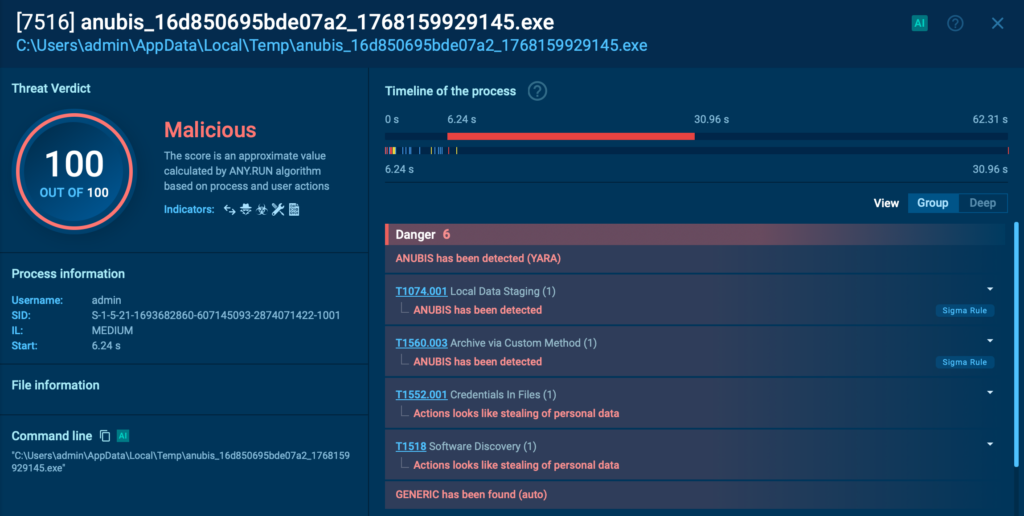
Highlighted additions include:
These rules help security teams tag and cluster related samples faster, validate whether a file matches known patterns, and speed up investigation workflows without relying on a single indicator type.
New Suricata Rules
Our team deployed 1,897 new Suricata rules to expand network-level visibility into phishing infrastructure, backdoor communication, and stealer-related traffic patterns. These detections help teams identify malicious activity even when payloads are fileless, heavily obfuscated, or delivered through multi-stage web flows.
Highlighted additions include:
- Sneaky2FA-related URL pattern (sid:85005763): Tracks HTTP requests to URLs associated with Sneaky2FA PhaaS infrastructure
- VShell backdoor C2 connection (sid:85005789): Identifies attempts by a fileless Go-based backdoor to establish communication with its C2 infrastructure
- SantaStealer HTTP activity (sid:84000895): Detects malware C2 communication based on specific artifacts present in outbound HTTP requests
About ANY.RUN
ANY.RUN is a core part of modern security operations, helping organizations make faster, more confident decisions across the full investigation lifecycle, from early alert validation to deep analysis and continuous threat awareness.
By exposing real attacker behavior in real time, ANY.RUN adds the context that alerts often lack and keeps detections aligned with how threats actually operate in the wild. This allows SOC teams to reduce noise, shorten response times, and focus effort where it matters most.
Today, more than 600,000 security specialists and 15,000 organizations worldwide rely on ANY.RUN to accelerate triage, limit unnecessary escalations, and stay ahead of fast-moving phishing and malware campaigns
Integrate ANY.RUN’s solution for Tier 1/2/3 in your organization →





0 comments