In busy SOC environments, every minute spent waiting for threat validation slows containment and impacts response metrics. The ANY.RUN integration with Tines delivers trusted verdicts and enriched context in seconds to cut mean time to respond (MTTR) and keep investigations flowing without delays.
ANY.RUN X Tines Integration: Faster Triage with Behavior-Driven Context
The new integration lets your SOC team pull actionable verdicts and intel from Interactive Sandbox and Threat Intelligence Lookup straight into the Tines workflows you already use. Instead of jumping between different tabs to confirm behavior or collect indicators, analysts can validate alerts, prioritize critical events, and enrich incidents with behavioral intelligence without leaving the Tines interface.
It is available to all ANY.RUN customers with API access, including Enterprise Sandbox, TI Lookup Premium, and trial users. You can run everything through the Tines visual interface or make direct API calls if you prefer more flexibility.
The goal is simple: bring fast detonation results and fresh intelligence right into your workflow, so investigations keep moving without extra steps slowing you down.
The Difference You’ll See in Your SOC
The integration affects several parts of the investigation workflow, improving both speed and decision quality:
- Reduce mean time to respond (MTTR): Automate detonation and enrichment, so analysts get verdicts and IOCs within minutes, shortening investigation cycles and resolution times across the SOC.
- Improve triage accuracy and cut false positives: Behavioral verification from ANY.RUN delivers ground truth for detections, helping the team focus on real threats and reduce wasted effort.
- Handle more incidents without adding headcount: Routine analysis and enrichment run automatically in Tines, maintaining coverage during alert spikes while freeing analysts for complex cases.
- Meet SLAs consistently as an MSSP: Automated sandboxing and enrichment help MSSPs deliver fast, quality services, and scale response capacity without extra integration overhead.
Combined, these improvements shorten detection‑to‑mitigation time from hours to minutes, lower analyst workload, and boost SOC throughput.
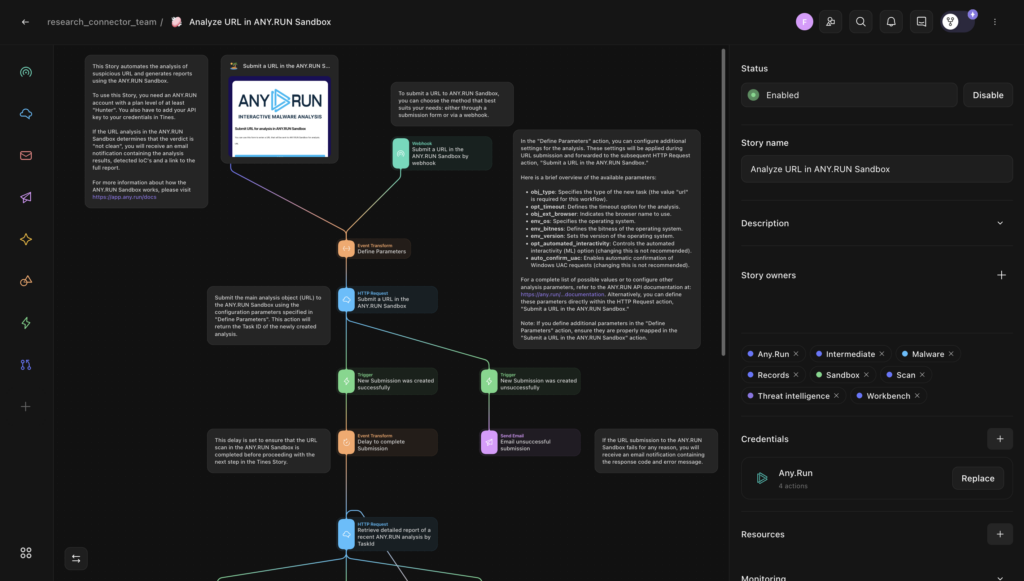
Interactive Malware Sandbox in Tines
ANY.RUN’s Interactive Sandbox integration with Tines brings live, behavior‑based malware analysis into your Tines workflows. Instead of relying on static detections or manual uploads, you get real‑time verdicts, IOCs, and behavioral data in the same environment that runs your automation.
Capabilities
- Submit suspicious files or URLs from any Tines story for automatic detonation and observation.
- Retrieve verdicts, IOCs, and full HTML reports as structured outputs.
- Reuse sandbox results across workflows or forward them to SIEM/EDR platforms through API actions.
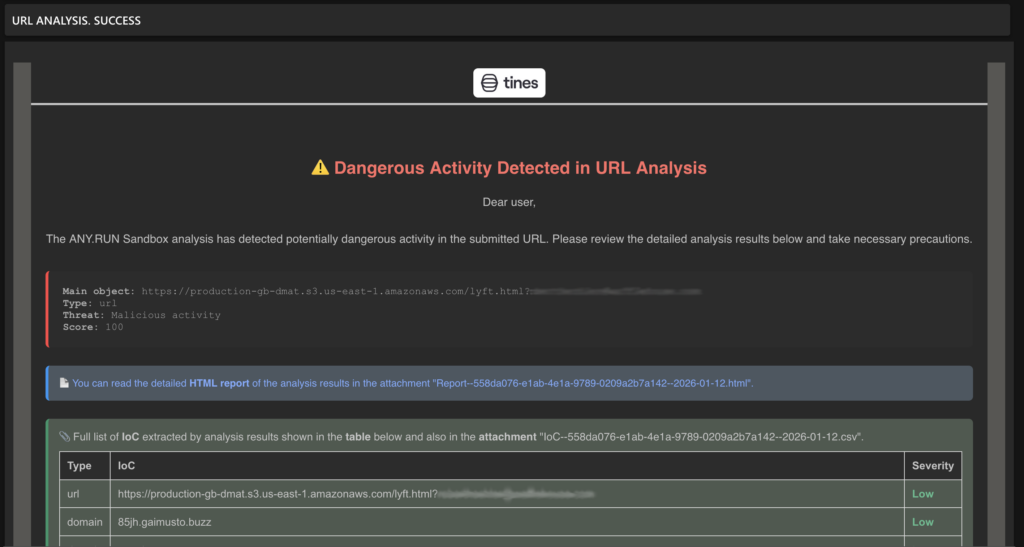
Example: Suspicious email attachments can be automatically sent for sandbox analysis. The resulting verdict and IOCs flow back to Tines, which then updates your SIEM or blocks the relevant indicators.
Benefits
- Faster validation: Confirm if a file or link is malicious before escalation.
- Consistent triage: Every sample is processed with the same standard, eliminating delays or missed steps.
- Actionable context: Behavioral data and network activity indicators feed directly into response actions.
Threat Intelligence Lookup in Tines
ANY.RUN’s Threat Intelligence Lookup integration with Tines adds context‑rich intelligence to automated processes. Each time a new IP, domain, or hash appears, you can check it against ANY.RUN’s continuously updated database of recent malware activity to enrich your decisions.
Capabilities
- Automatically perform lookups for IOCs inside any Tines story.
- Retrieve brief overviews or full JSON data with reputation, threat family, and activity history.
- Combine Lookup results with internal data sources to refine correlation and playbook logic.
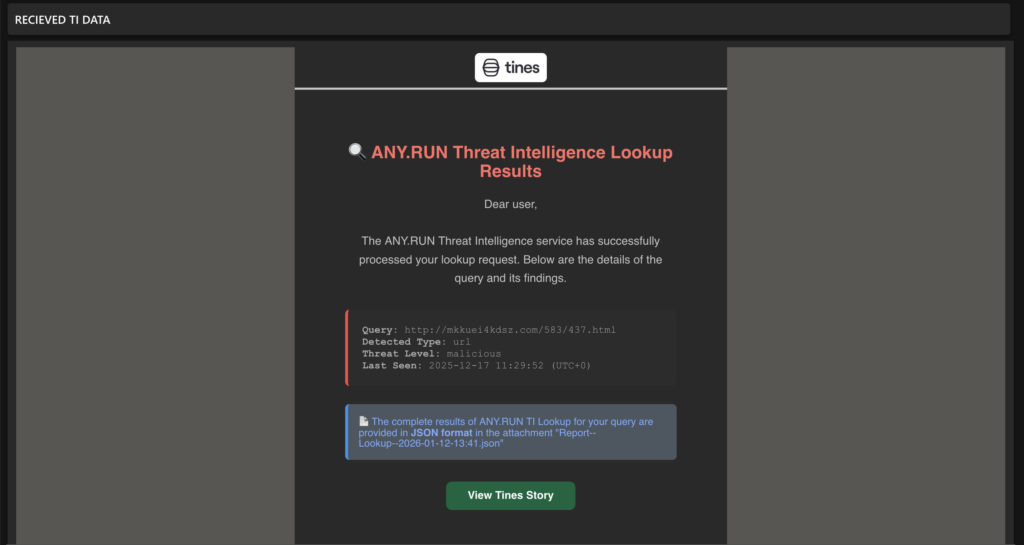
Example: When a newly observed IOC triggers an alert, Tines can automatically query TI Lookup for reputation data and campaign context, helping analysts decide whether to escalate or suppress the event.
Benefits
- Higher detection fidelity: Real‑world sandbox intelligence helps distinguish live threats from noise.
- Smarter prioritization: Know which IOCs are still active and which are already dormant.
- Efficient workflow chaining: Lookup results are ready to power next‑step actions like blocking, reporting, or case validation.
How You Can Get Started in Minutes
ANY.RUN’s integration with Tines includes ready‑to‑use example stories for file analysis, URL analysis, and TI Lookup queries.
You can install it and start testing in just a few minutes, with no complex setup or custom scripting required.
About ANY.RUN
ANY.RUN helps security teams understand threats faster and take action with confidence.
The solution is trusted by over 500,000 security professionals and more than 15,000 organizations across sectors where speed and accuracy define successful response.
ANY.RUN’s Interactive Sandbox lets teams safely run suspicious files and links, watch real behavior unfold, and confirm threats before they spread. Paired with Threat Intelligence Lookup and Threat Intelligence Feeds, it delivers the context needed to sort alerts, cut uncertainty, and stop advanced attacks earlier in the response cycle.
Reuqest a 2-week ANY.RUN trial →
FAQ
It removes the need to switch between tools to validate alerts. Sandbox results and TI Lookup context arrive directly inside your Tines stories, helping your team move investigations forward without stopping for manual checks.
You get verdicts, behavior summaries, IOCs, network activity, risk scores, and optional full HTML reports; all as structured outputs that Tines can use in later steps.
Most verdicts return within minutes. ANY.RUN reveals the majority of malicious behavior in the first 60 seconds, so playbooks don’t stall waiting for enrichment.
Yes. Anyone with ANY.RUN API access, including trial users, can use the integration.
No. Detonations run in parallel on ANY.RUN’s side, and Tines continues the story when the result is ready. Most verdicts return within minutes.
Yes. Tines can pass ANY.RUN results to your existing systems as part of automated response actions.
Yes. It’s built to run reliably during spikes, so routine detonations and lookups continue without interruption.
Absolutely. The prebuilt stories are only a starting point; you can adapt them to match your escalation rules, correlation logic, or existing playbooks.




0 comments