As cybersecurity threats grow more sophisticated, collaboration becomes a cornerstone of effective defense strategies. This is where MISP, an open-source threat intelligence sharing platform, comes into play.
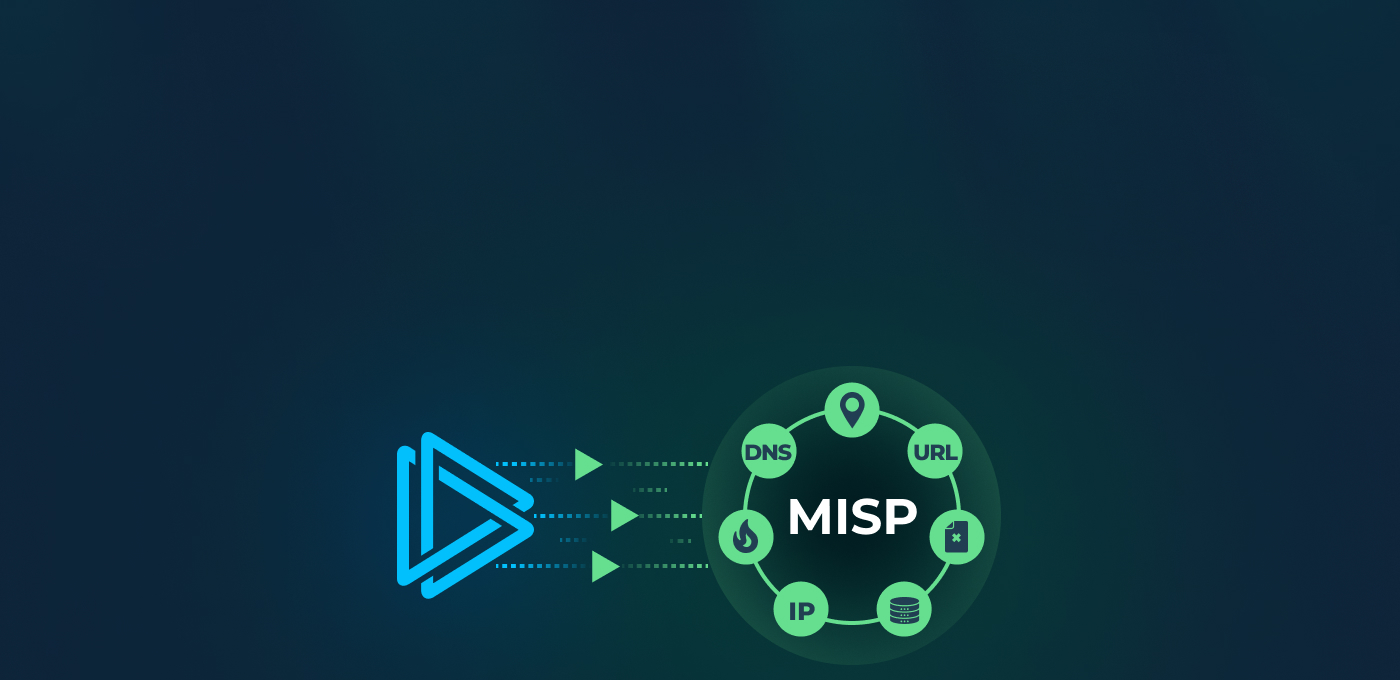
To access and use indicators of compromise (IOCs) from ANY.RUN’s Threat Intelligence Feeds, you can integrate with MISP using our connector.
What is MISP?
MISP, which stands for Malware Information Sharing Platform, is a free, open-source platform designed to facilitate the exchange, storage, and correlation of threat intelligence data. MISP lets organizations and researchers:
- Exchange critical data points to identify cyber threats.
- Share signals or attributes indicating the compromise of information systems.
- Automate the process of data sharing and find correlations between threat data.
Benefits of Integrating ANY.RUN with MISP

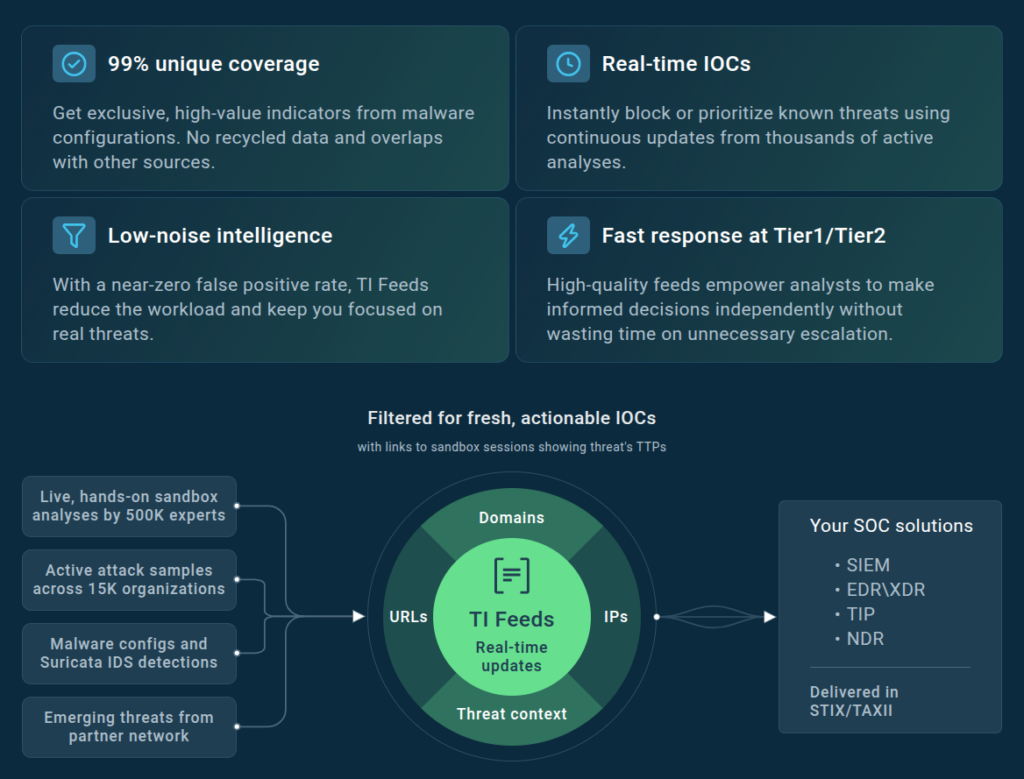
With ANY.RUN’s TI Feeds, you can:
1. Boost your performance rates
Expanded threat coverage empowers your SOC with live threat data coming from over 15,000 companies across continents. TI Feeds helps monitor which malicious activities target business at the moment and in real time, you receive updates to use in proactive defense strategy.
The integration makes network IOCs (IPs, URLs, and domains) from TI Feeds automatically available in MISP for further use in your infrastructure.
99% unique IOCs make for clean threat intelligence without false positives and overlaps with other sources.
2. Gain visibility into emerging threats
For enterprises, high-quality threat intel delivers wide and in-depth insights into latest attacks. When equipped with it, SOC teams improve detection rates and stay ahead of threat actors. Ultimately, this leads to a significant mitigation of potential risks related to gaps in cybersecurity infrastructure.
Through integration, you can easily enrich your incidents and correlation rules with fresh IOCs retrieved from real-world data—ANY.RUN’s Interactive Sandbox analyses done by SOC teams right now.
3. Alert fatigue prevention
The fact that TI Feeds are made of unique, noise-free, and fresh data lowers the workload of analysts. For Tier 1, this means more reliable info that can be used instantly to make smart decisions about the alerts at hand. For Tier 2, this reduces the number of escalations, freeing up their time to prioritize more pressuring tasks.
Fresh network indicators that come with threat context can be applied for monitoring and alert triage. As a result, MTTD and MTTR rates go down, as analysts get empowered with relevant and trustworthy data in real time. This helps them make informed decisions and correlate rules confidently.
How to Integrate ANY.RUN with MISP
To get started with ANY.RUN & MISP integration, you can:
- See documentation for MISP integration on ANY.RUN’s GitHub
- Contact our experts to learn more about ANY.RUN’s solutions
- Reach out to support at support@any.run for technical assistance
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target Windows, Android, and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Get a 14-day free trial of ANY.RUN’s Threat Intelligence service →







0 comments