Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Gootkit is an advanced banking trojan. It is extremely good at evading detection and has an incredibly effective persistence mechanism, making it a dangerous malware that researchers and organizations should be aware of.
|
Trojan
Type
:
|
Unknown
Origin
:
|
|
1 June, 2014
First seen
:
|
18 July, 2024
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 June, 2014
First seen
:
|
18 July, 2024
Last seen
:
|

 429
429
 0
0

 2259
2259
 0
0

 4388
4388
 0
0
Gootkit is a banking trojan – a malware created to steal banking credentials. In fact, Gootkit is classified as one top sophisticated banking trojan ever created. It relies on complex anti-evasion and persistence mechanisms, as well as complex techniques like dynamic web injections.
Since its initial discovery in 2014, Gootkit has been utilized in multiple attacks that targeted bank accounts across Europe, some of which were very destructive.
Gootkit is known to affect the most widely used web-browsers, namely IE, Firefox, and Chrome. Interestingly, this trojan is coded mostly using the node.js programming language – not the first choice for most operators. What’s more, while many similar malicious programs heavily utilize leaked source code of older samples, the virus appears to be written almost 100% from scratch.
The roots of this malware go all the way back to 2010 when what can be called the predecessor of Gootkit was first documented. Classified at the time as an information stealer which did not pose a significant danger, Gootkit has since evolved into a full-fledged banking V.
The malware has been documented in its present form of a trojan since 2014, involved in attacks targeting both private and corporate victims in Europe, mainly targeting banks in France and England. However, Spanish and Italian banks have also been reportedly attacked.
Unlike some other trojan, Gootkit is not available for sale on the internet. Its code hasn’t been leaked, and a Russian-speaking group of hackers has carried out all attacks involving this malware.
Creators of the Gootkit trojan have implemented some of the most cutting-edge anti-evasion tricks to ensure the payload will stay hidden for as long as possible and prevent successful analysis by cybersecurity researchers. Comprised of two main parts, the dropper and the trojan itself – the virus carries out sandbox checks on every stage of its life cycle. Meaning that both the dropper and the actual trojan have unique anti-evasion procedures.
Once the dropper makes its way into a machine, it will conduct the initial VM check, making sure that the malware is not being launched in a virtual environment. This is achieved by verifying the system’s processor value inside the Windows Registry by checking for specific names of virtual servers. In addition, BIOS is also checked to find any values which could point at the malware being launched on a VM. If the malware detects that it is not being launched on a real machine, it terminates all activities and connects to the control server to blacklist the endpoint it was launched in.
However, if the initial test is passed, the loader installs the main Gootkit executable, which, in turn, repeats some of the previous checks while adding several new ones. In one of the new checks, the malware checks the whitelist of names admissible for the CPU to determine that a VM name is absent from the list. Following this test, the malware scans to find VMWare, VBOX, or SONI values on IDE/SCSI hard drives.
Such thorough virtual machine checks are not the only jack up the sleeve that Gootkit has regarding evasion. To increase the success rate of installs, the malware creators frequently make modifications to the generic trojan, changing the targeted processes for injections and filetypes of the executable.
For example, instead of running an .exe file, some samples of Gootkit load a DLL directly into a target process. What’s more, while the majority of malware select the explorer.exe process as their injection target, Gootkit targets a service host (svchost) process instead. Presumably, this is done to further evade detections since injecting into a process with several instances makes Gootkit easier to hide.
In addition to advanced anti-detection methods, Gootkit malware employs equally sophisticated persistence techniques to ensure that its deletion from an infected machine will prove as complicated as possible. The malware provides two main persistence mechanisms, which are used depending on the available system rights. When launched from an admin account, Gootkit can mimic a Windows service with a random name, which helps to confuse users. This way, it can launch before a victim logs on and continues running even after logging off.
However, if launched from a least-privilege user account, the virus writes itself as a scheduled task and a random name. This task is programmed to run every minute and on every boot, ensuring that the malware will remain on a machine after antivirus software scans and system reboots.
A video of the simulation that was recorded in the ANY.RUN malware hunting service allows us to perform an analysis of the execution of Gootkit and see this virus in action as well as Danabot or Pony. Moreover, you can investigate the vast malware database in the public submissions, too. The video is available here.
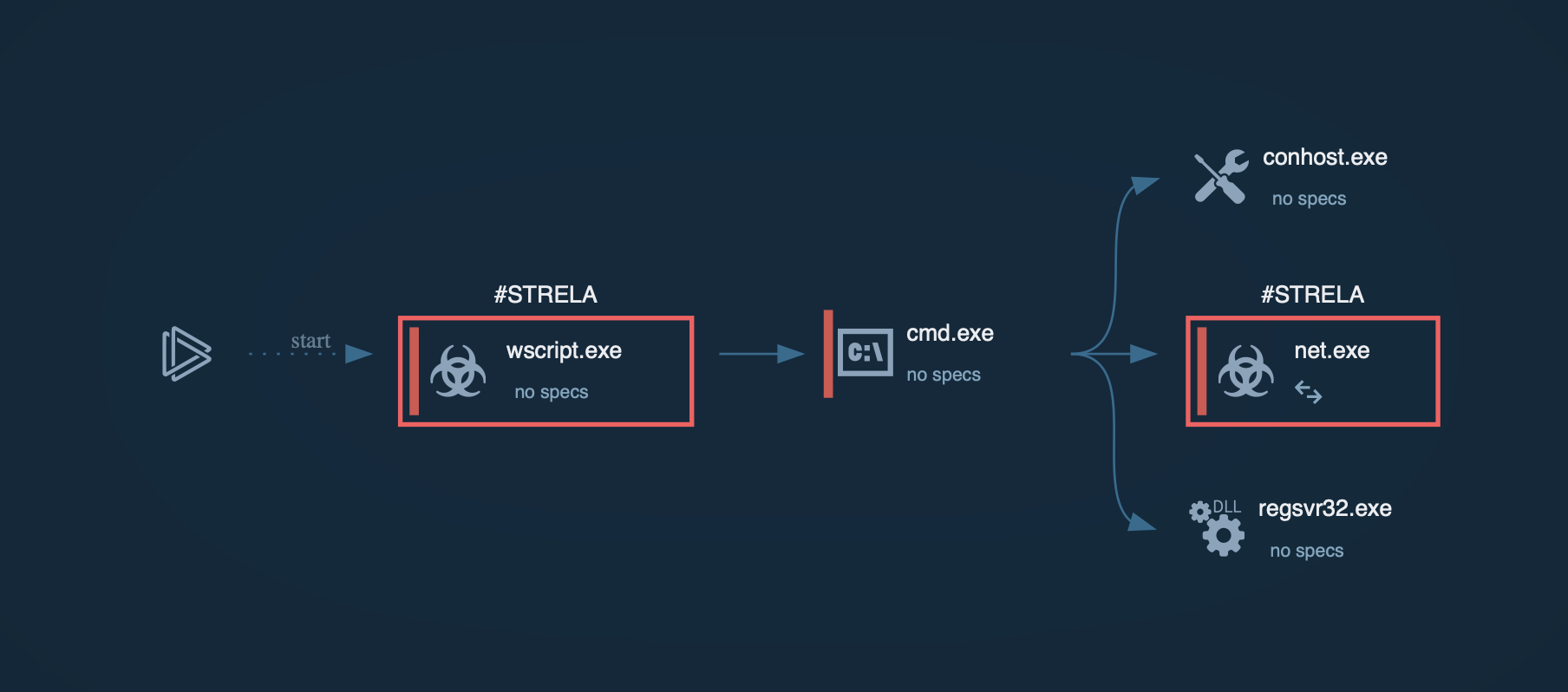
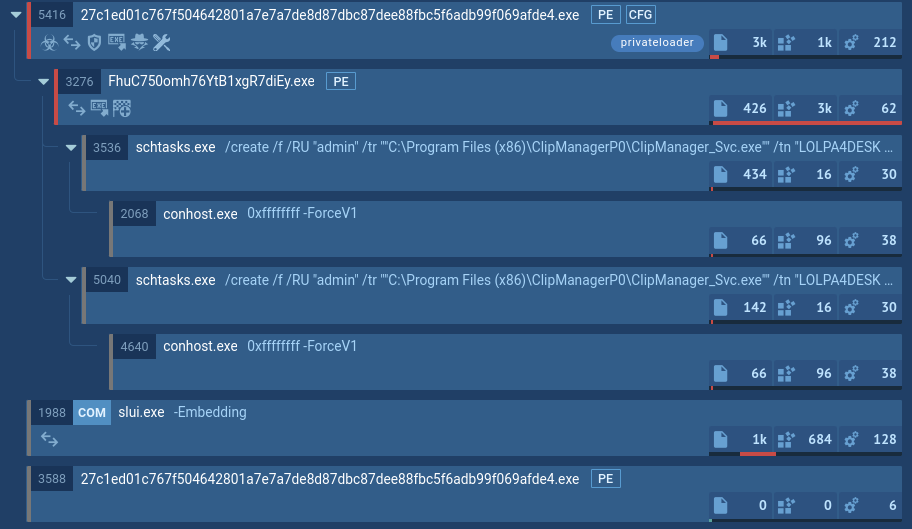
Figure 1: the lifecycle of Gootkit can be viewed in a visual format on the process graph generated by the ANY.RUN online analysis sandbox.
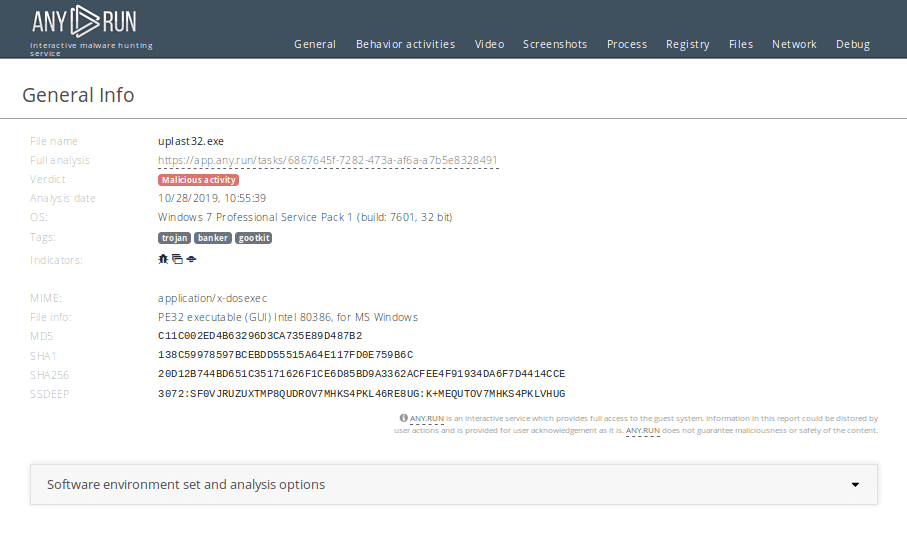
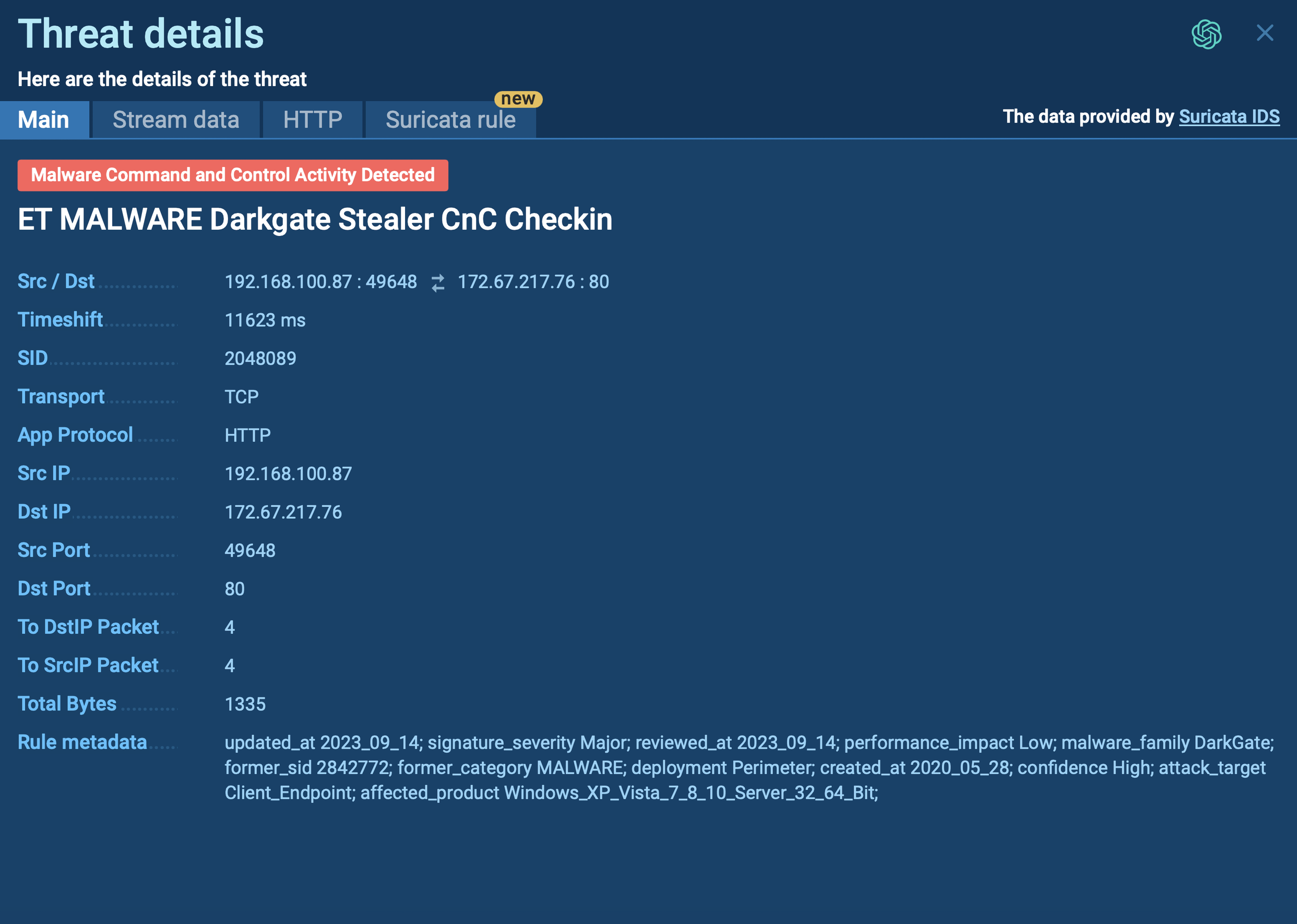
Figure 2: This text report is available at this link provides more detailed information about Gootkit execution processes, artifacts, and more.
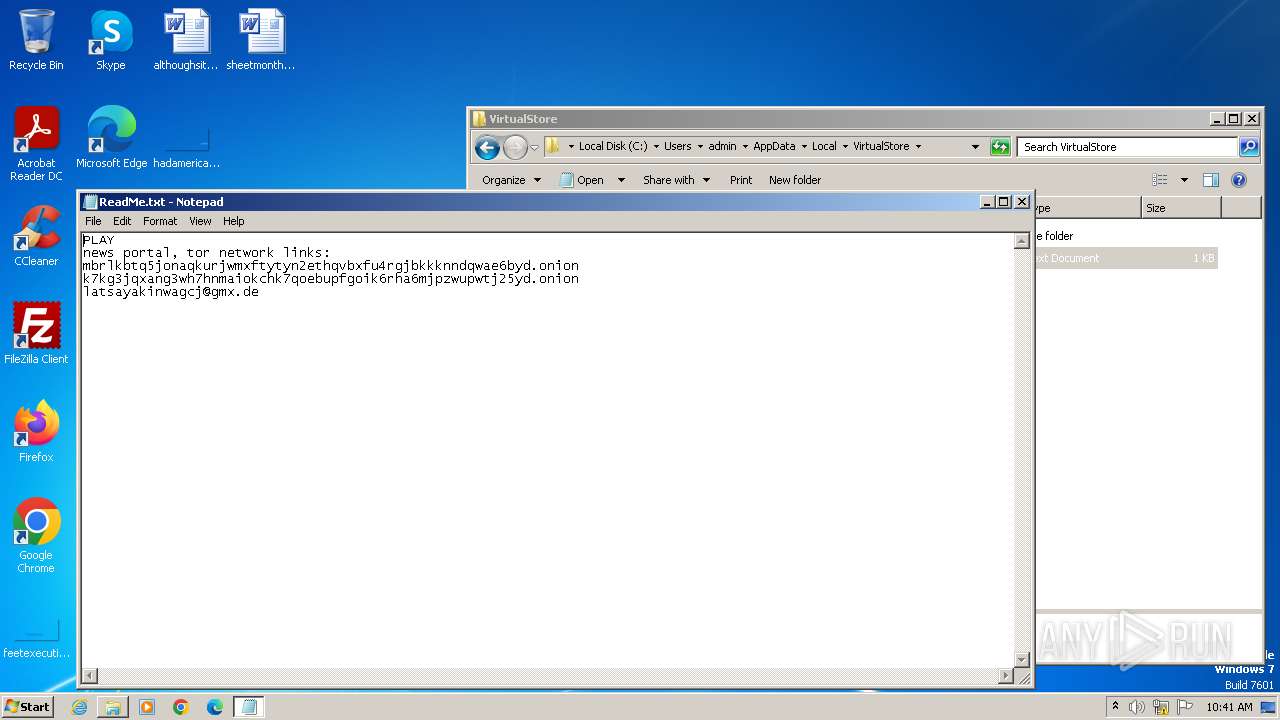
Gootkit often gets into the system as an email attachment in the form of a Microsoft Word file. After the user opens the malicious file, it starts Powershell to download the main payload.
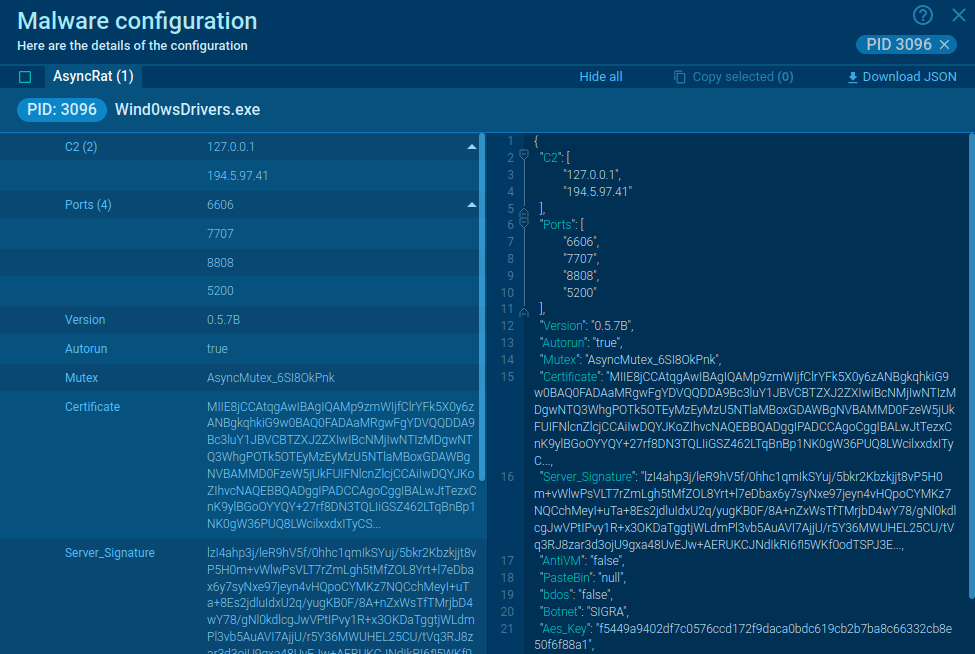
It should be noted that in some cases, Gootkit postpones the execution by putting itself in scheduled tasks. After the main payload execution starts, Gootkit unpacks and launches itself. This process provides the main malicious activity - stealing personal information, downloading other malware, grabbing video of the victim’s desktop, hijacking banking credentials, keys loading, connecting to C2 servers, and so on. In the given example, Gootkit also uses WMIC.EXE to obtain a list of AntiViruses.
Gootkit utilizes multiple attack vectors to infect its victims, including popular exploit kits like Neutrino and Angler, allowing the malware to get into machines with not-up-to-date operating systems.
The second used attack vector is email spam, where Gootkit is delivered to users as a malicious email attachment. Social engineering is used to trick the user into downloading the malicious file.
Several online safety rules can be followed to greatly reduce the risk of infection by malware such as Gootkit. For instance, users are advised to install the freshest OS updates and update applications that users utilize regularly.
At the same time, those applications that are rarely opened should be deleted from the machine. In addition, it is advised to disable ads in the browser and avoid visiting suspicious websites. Furthermore, if a private inbox is used at work instead of a corporate one, a user should restrain from sending sensitive information to and from this personal email address.
It should be noted that opening email attachments in suspicious emails always poses a high risk of injection. Therefore users must never run suspicious programs downloaded from emails sent from unrecognized addresses.
If the analyst wants to do additional work with events from tasks or share them with colleagues, they can export to different formats. Just click on the "Export" button and choose the most suitable format in the drop-down menu.
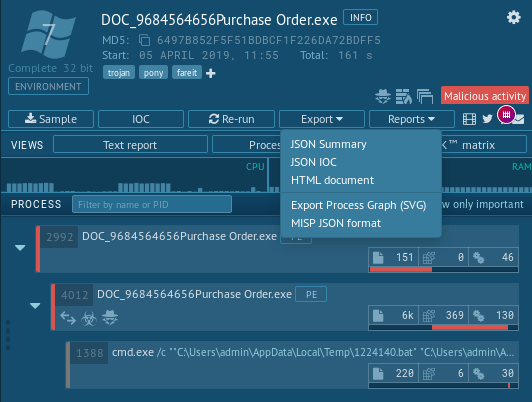 Figure 3: Options for export events from tasks with Gootkit
Figure 3: Options for export events from tasks with Gootkit
Although Gootkit is responsible for a negligible percentage of the overall attacks by financial malware, this trojan should be considered an extremely high-risk danger. Thanks to its sophisticated persistence and anti-evasion functions, it is capable of potentially very damaging attacks.
What’s more, following the trojan development over the years, it is safe to assume that its evolution will continue. Cybercriminals behind the malware will keep producing ways to evade modern security solutions.
That’s why utilizing the most reliable and cutting edge analysis tools, such as the ANY.RUN malware hunting service can be a key to setting up a secure cyber defense against serious threats like Gootkit. Check the service's malware database to find out about other malicious programs.