Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Crimson is a Remote Access Trojan — a malware that is used to take remote control of infected systems and steal data. This particular RAT is known to be used by a Pakistani founded cybergang that targets Indian military objects to steal sensitive information.
|
Trojan
Type
:
|
Pakistan
Origin
:
|
|
1 January, 2016
First seen
:
|
20 January, 2026
Last seen
:
|
|
Type
:
|
Pakistan
Origin
:
|
|
1 January, 2016
First seen
:
|
20 January, 2026
Last seen
:
|

 434
434
 0
0

 2292
2292
 0
0

 4444
4444
 0
0
Crimson is a Remote Access Trojan — it is malware that cybercriminals or threat groups can utilize to gather information from infected systems. The malware is also known under the names SEEDOOR and Scarimson. It can be used to spy on victims, capture screenshots, steal credentials, and more.
Crimson is known to be used particularly by an APT (Advanced Persistent Threat), a cyber gang founded by a state. Therefore, the Crimson RAT is targeted at a very specific group of victims, among whom are Indian Government organizations and the military.
Crimson RAT is among malware that utilizes information related to the coronavirus to infect the machines of their victims. The strategy of using a natural disaster to exploit the need for information and the stress of potential victims is not new among cybercriminals. In fact, fake information about SARS and other epidemics is still used for phishing by some cyber-attack schemes.
As such, the Crimson malware authors use a fake health advisory email to trick victims into downloading a malicious document.
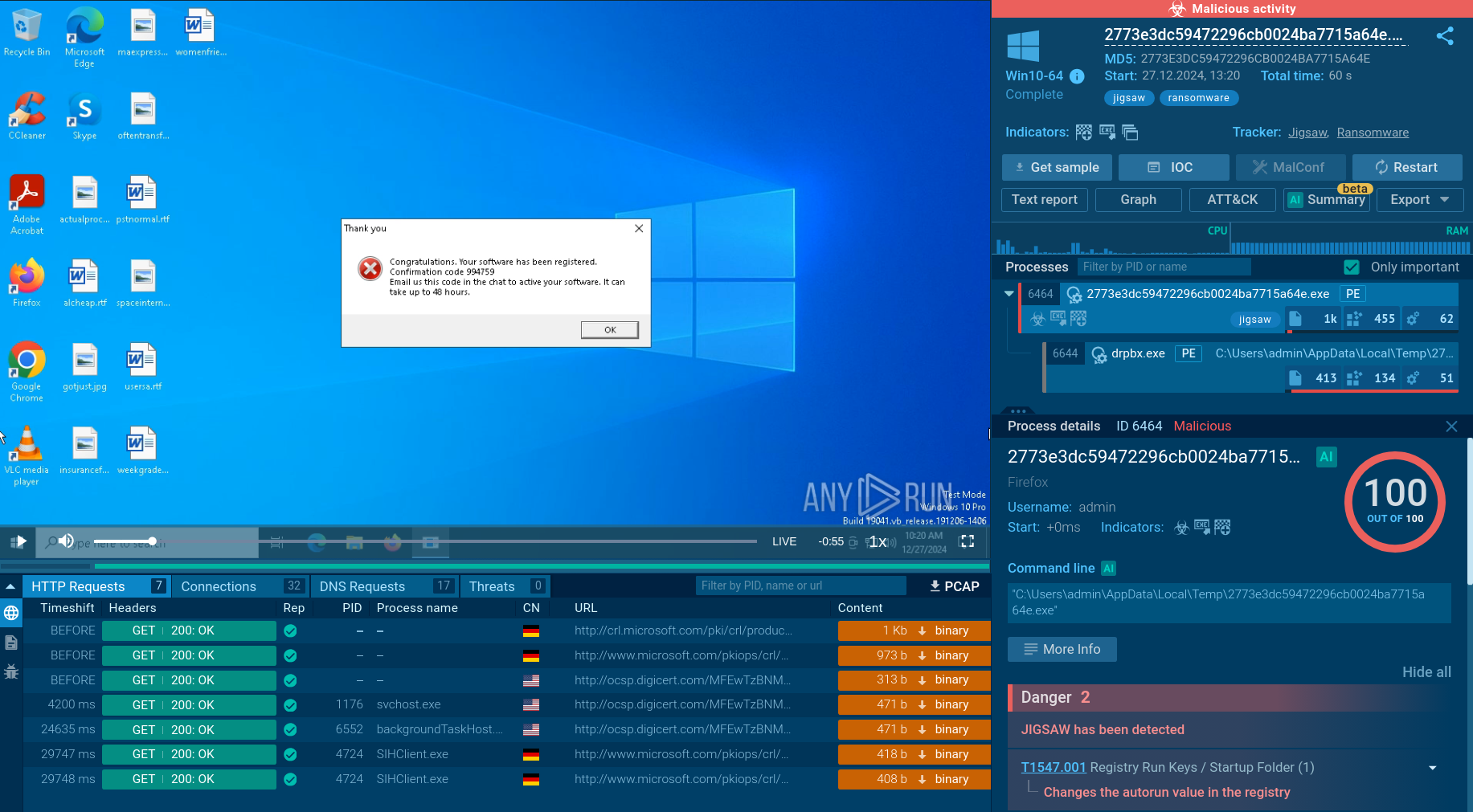
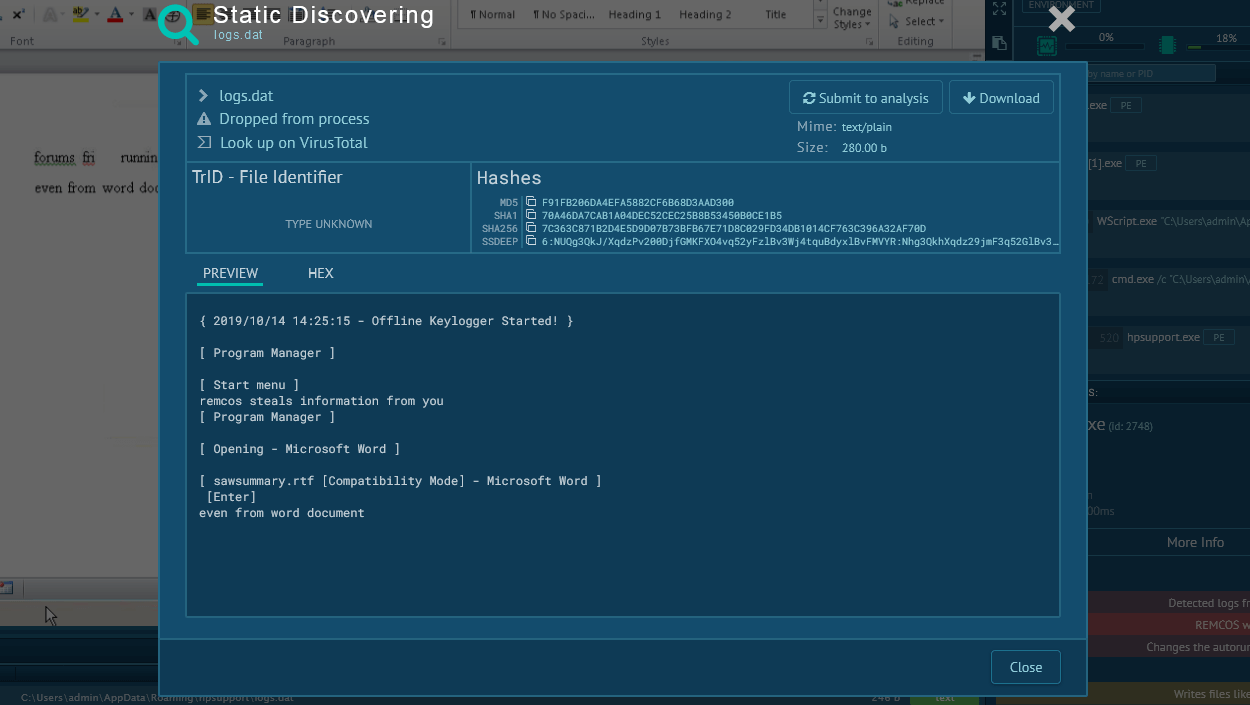
After the RAT is downloaded and installed it can perform several malicious functions, most of which are targeted at information gathering. The RAT can record and share running processes on an infected machine with the attackers, take screenshots, and steal information from web-browsers. Also, the malware has the capability to download files into infected systems from a control server.
As we mentioned above, the Crimson RAT is operated by an APT. In particular, APT36, which is thought to be sponsored by Pakistani officials to conduct military espionage. Thus, the victims of the RAT are almost exclusively among Indian officials and military personal. It is believed that retrieved sensitive information that the APT collects is used by Pakistan in military efforts against India.
In fact, APT36 is also commonly known under the name Mythic Leopard, has a history of successful attacks on Indian embassies and military infrastructure that resulted in the stealing of tactical and training information. However, other malware samples have been used in previous attacks.
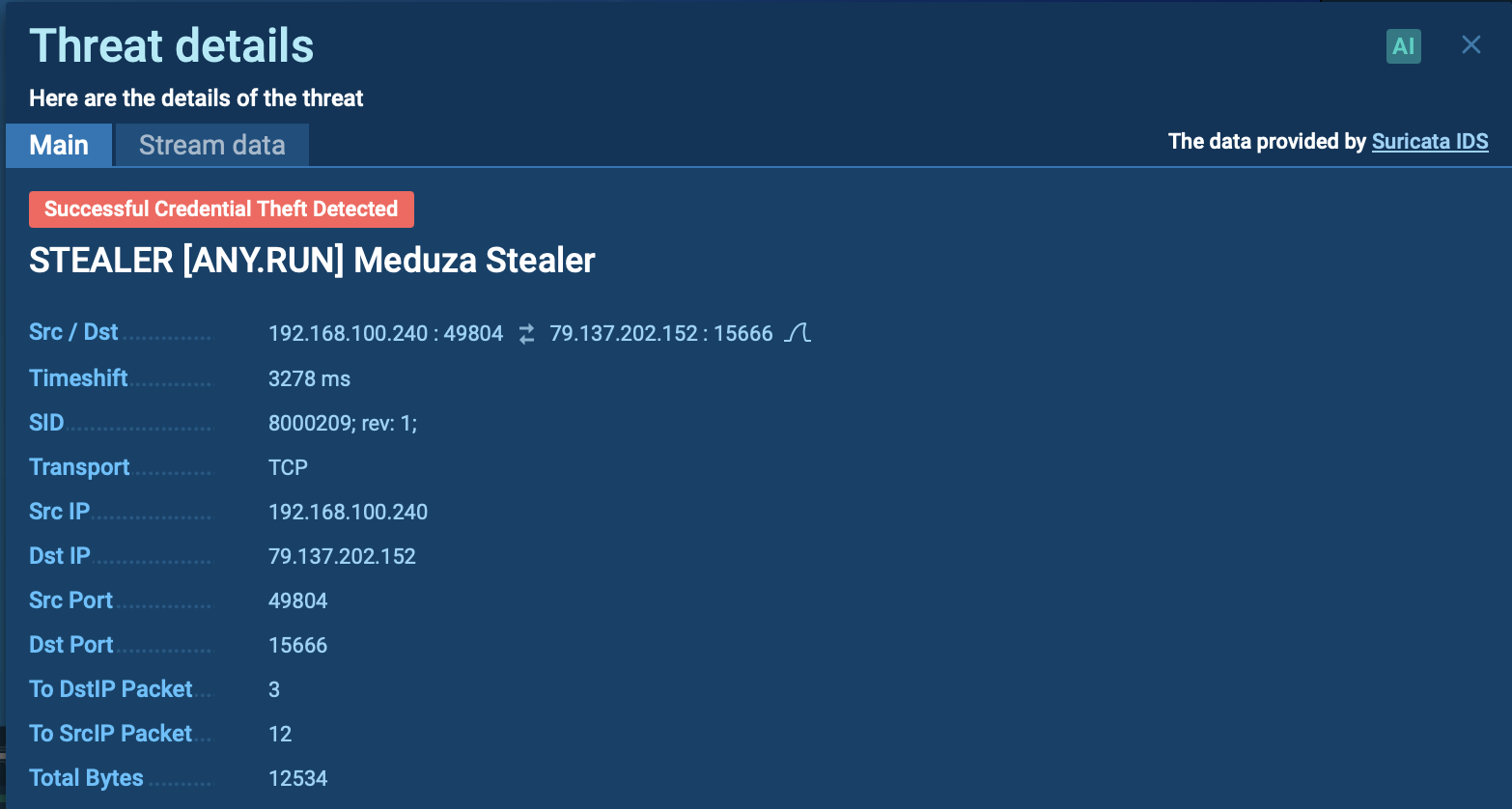
A video recorded in the ANY.RUN interactive malware analysis service shows the execution process of Crimson RAT.
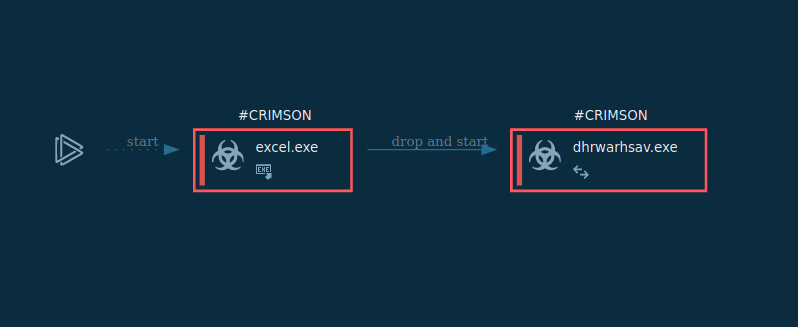
Figure 1: Shows the execution process of the Crimson RAT. This Graph was generated by ANY.RUN.
Figure 2: Displays a text report that users can create in ANY.RUN. Text reports can be used to demonstrate found information and can be customized to show only necessary data.
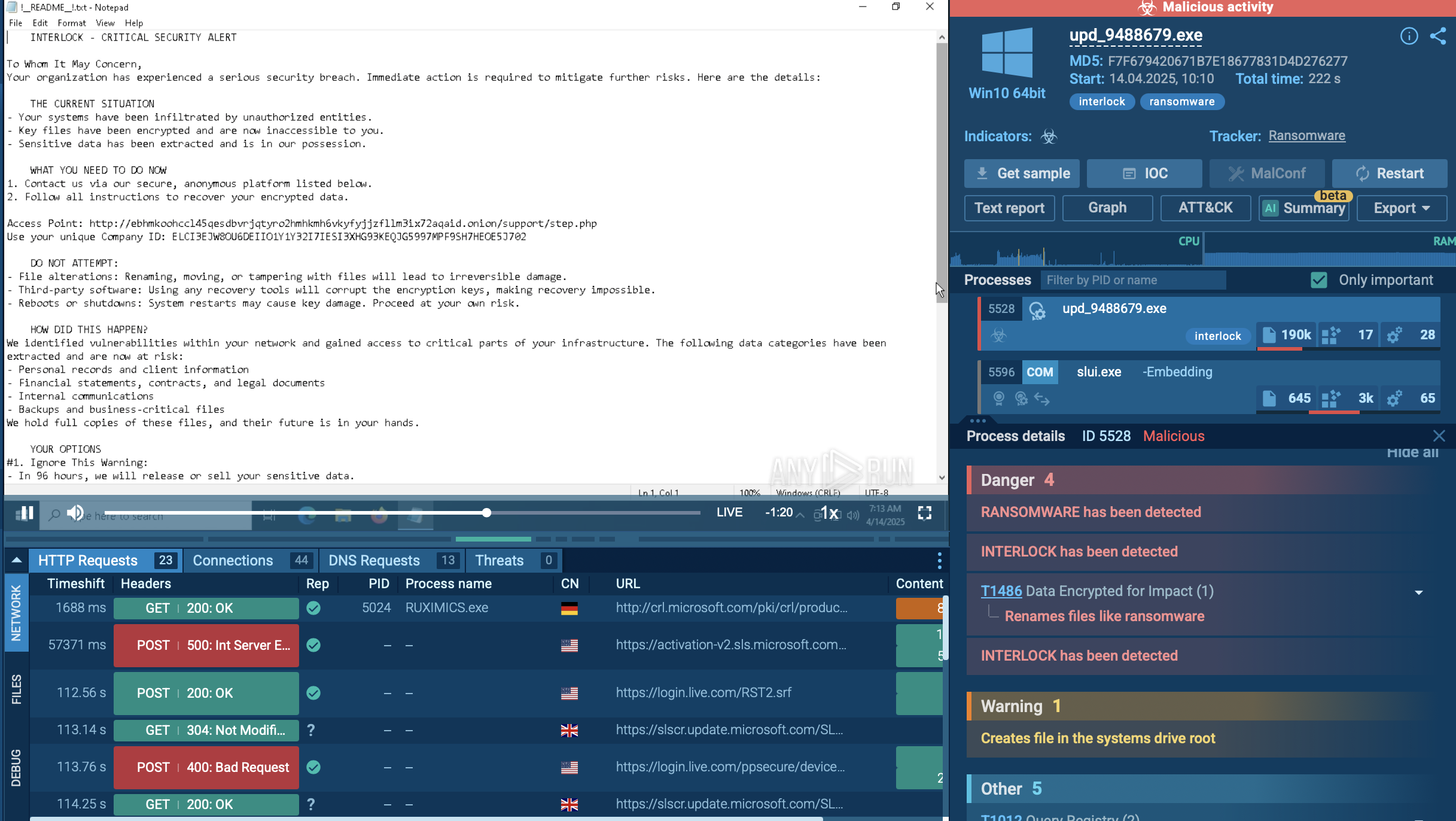
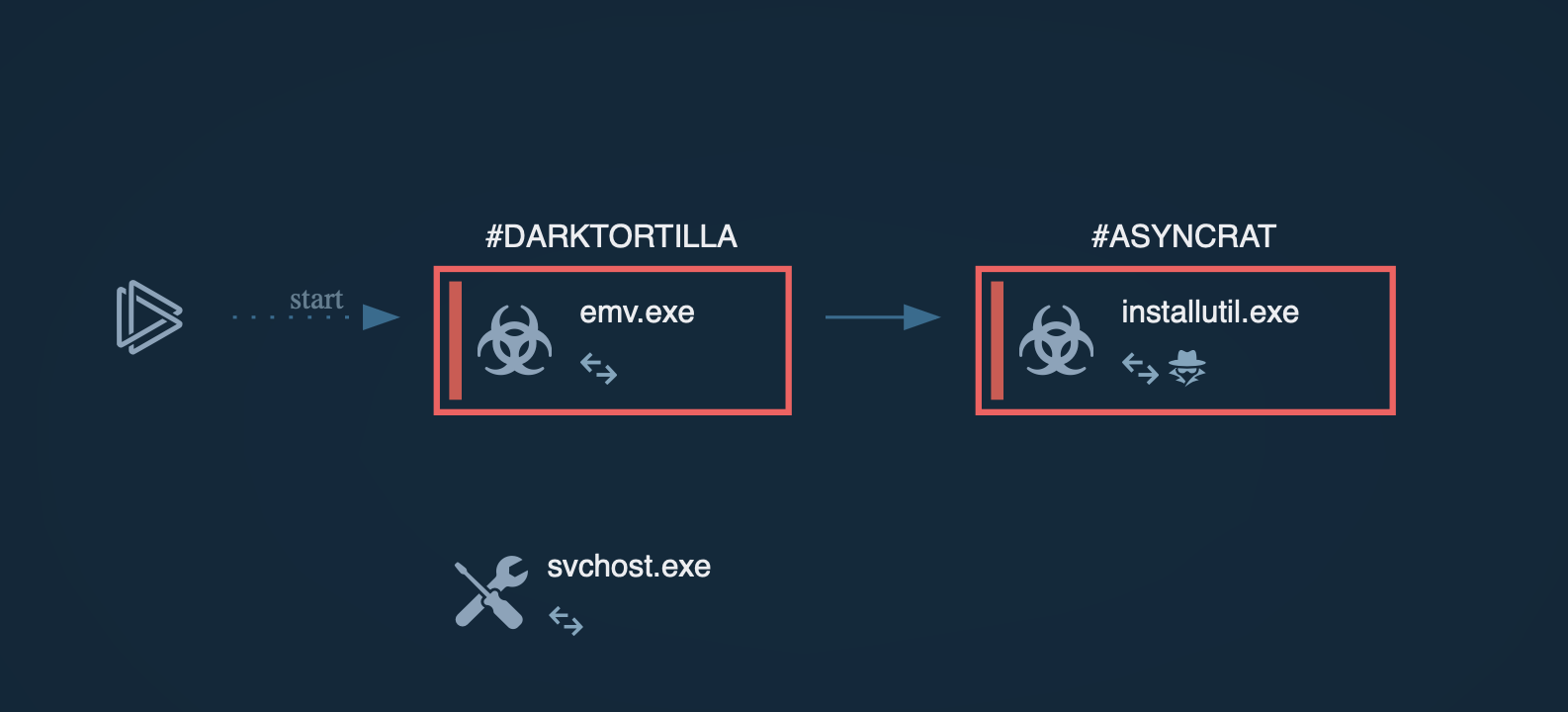
Crimson RAT execution process is pretty straightforward but it can vary from sample to sample. Often, the malware executable file is located directly inside a malicious document and once the user opens it, the file drops the trojan. In other cases, a maldoc can contain a macro that leverages Powershell to download and start a Crimson executable file. After the trojan starts, it will try to establish a connection with a C2 server and transmit information about the victim's system and the list of running processes on that system.
Crimson RAT spreads using highly targeted email spam campaigns using the same scenario as Quasar RAT. Spear Phishing techniques that leverage the fear of the Covid-19 pandemic are used to trick victims into downloading a Microsoft Office Excel file, which allegedly contains information related to the outbreak. Once the file is opened, it launches malicious macros or exploits vulnerabilities, such as CVE-2017–0199 for example.
Analysts can detect the Crimson RAT based on file operations. To do so, click on the process in the "Process list" section, and in the appeared "Process details" window click the "More info" button. In the "Event" section switch from "Friendly" to "Raw". After that, enter "Edlacar", "Dhrolas", "Ardscar" or "Dtromera" in the "Filename" field. If operations with a folder with such names are found, be sure — that’s the Crimson RAT in front of you.
Crimson the same as Netwalker is a prime example of a threat actor using a pandemic or other natural disaster to gain leverage over its victims and trick them into installing malware. So far this particular malware has been used almost exclusively in military espionage, but it may very well become more widespread in the future.
Since this is a lesser-known malware, not a lot of samples are available to analyze. Thankfully, ANY.RUN malware hunting service presents an opportunity to study this RAT in an interactive simulation, allowing for quick and simple dynamic analysis in a secure online environment.