In this article, we’ve prepared a brief overview of UAC bypass methods in Windows 11 that are used in modern malware and provided examples of their implementation in active threats. We’ll show how to bypass user account control via:
- Exploitation of COM interfaces with the Auto-Elevate property
- Modification of the ms-settings registry branch
- Infinite UAC Prompt Loop (social engineering)
Let’s investigate these methods.
Exploitation of COM Interfaces with the Auto-Elevate Property
First, let’s quickly define COM.
COM (Component Object Model) refers to objects containing data and methods for working with them. COM objects can be used to create various applications.
You can find the list of COM objects in this registry key:
- \HKEY_CLASSES_ROOT\CLSID.
We are interested in those that have the Elevation – Enable – 1 entry in the registry. This means that the given object runs with elevated privileges without the UAC window appearing.

The main COM objects that can be used for UAC bypass are:
- {3E5FC7F9-9A51-4367-9063-A120244FBEC7} (cmstplua.dll)
- {D2E7041B-2927–42fb-8E9F-7CE93B6DC937} (colorui.dll)
- {E9495B87-D950–4AB5–87A5-FF6D70BF3E90} (wscui.cpl)
Let’s utilize ANY.RUN’s Treat Intelligence Lookup and try to find the use of the COM object cmstplua.dll using this query:
CommandLine:"Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}" We managed to find a recent Formbook sample among the sandbox sessions:
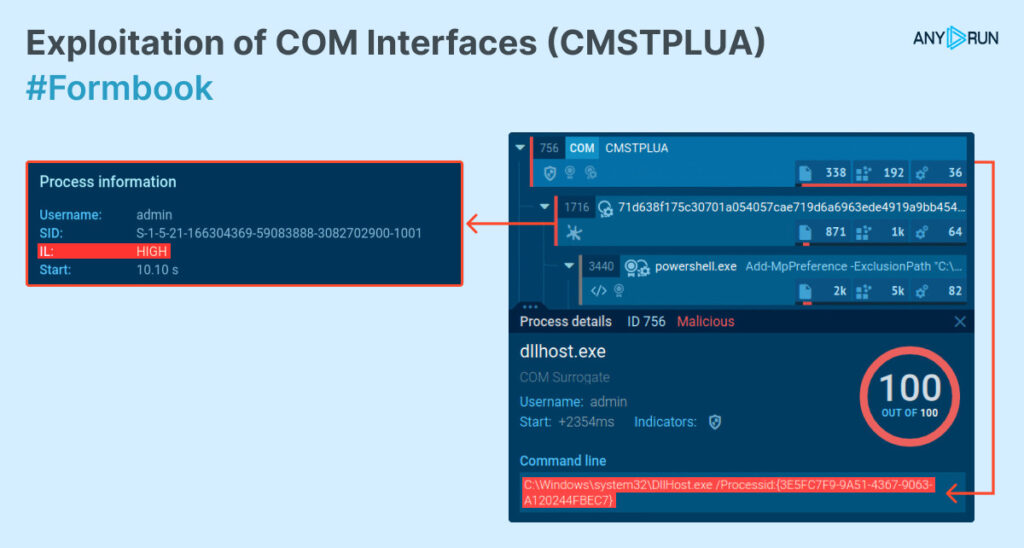
Now let’s try to find the use of the COM object colorui.dll with the help of this query:
CommandLine:"Processid:{D2E7041B-2927–42fb-8E9F-7CE93B6DC937}" We discover old Lockbit samples, but nonetheless, this and the previous method work on Windows 11. You can also analyze methods for UAC bypass inside Windows 10 in the ANY.RUN sandbox for free.
Here is a sandbox analysis of one sample:
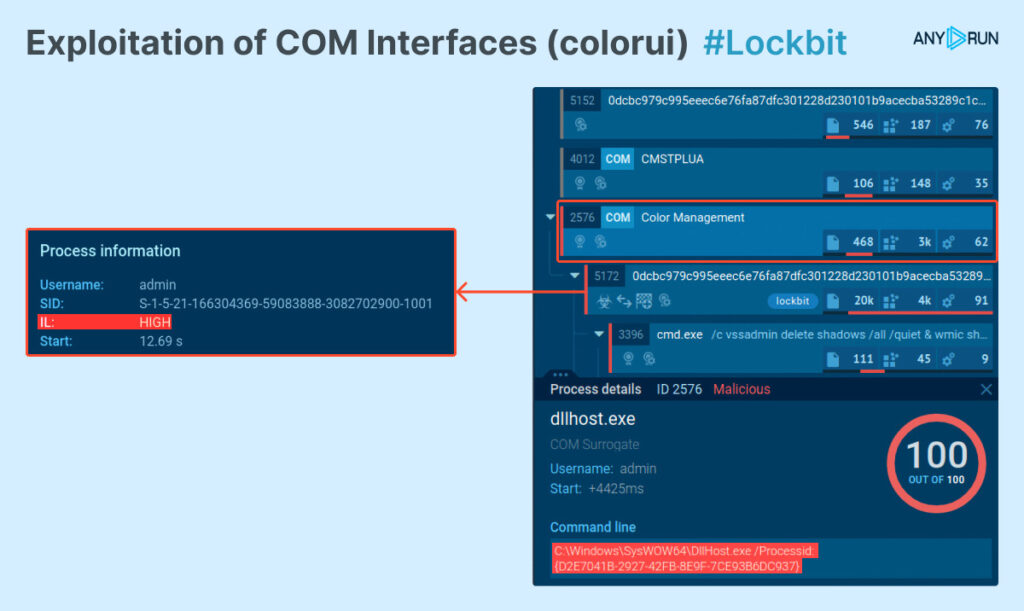
That is why organizations when dealing with Windows 11 UAC cyber security issues must take into account colorui exploitation as one of the most common techniques used by attackers.
Modifying the ms-settings Registry Branch and DelegateExecute Key
This method works because some programs start with elevated privileges and access the non-existent HKCU:Software\Classes\ms-settings\shell\open\command registry branch, and only then the existing HKCR:ms-settings\shell\open\command branch (e.g., fodhelper UAC bypass).
Also, the first branch is writable with the current user’s rights.
This results in a situation where creating the required registry branch and key allows the action to be performed without the UAC prompt appearing.
Let’s once again use ANY.RUN’s TI Lookup and run the following query:
RegistryKey:"\\ms-settings\\shell\\open\\command" and RegistryName:"DelegateExecute" We found BlankGrabber. Note that the path to the executable is written in Default.
Here is an example:
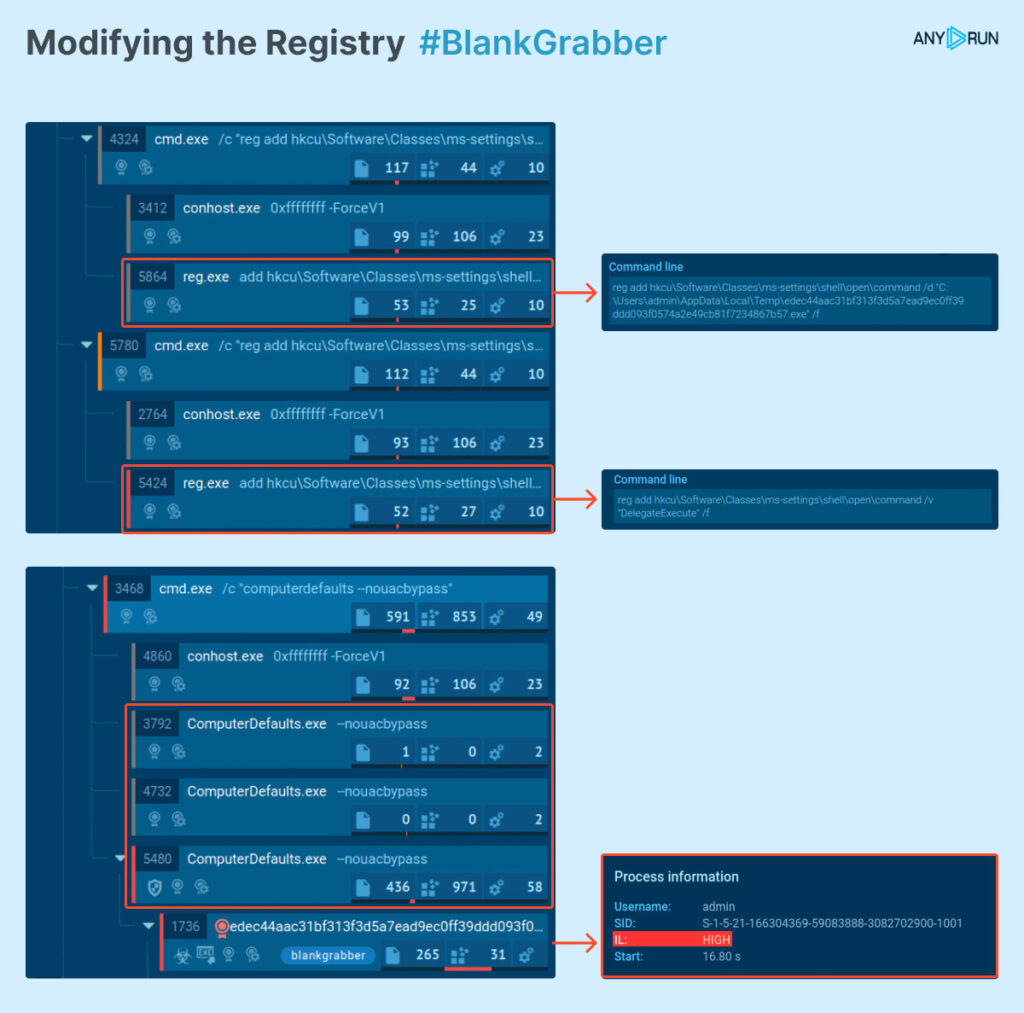
Infinite UAC Prompt Loop
In this method, the UAC window repeatedly prompts the user to open an application. It’s impossible to close, so the user has no choice but to agree to run the application. There’s also a chance that the user will accidentally agree.
Example of a simple script:
while($true){try{Start-Process "cmd.exe" -Verb runas -ArgumentList "/c", 'payload && pause';exit}catch{}} 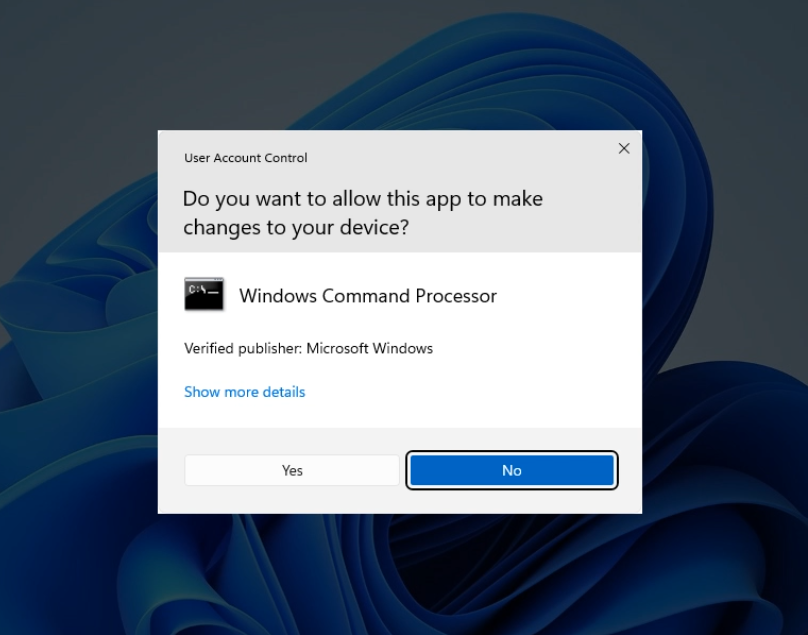
During our research, we came across several cases employing a similar method:
This method is closely related to social engineering, as it directly depends on the user’s actions.
Detection
To detect these methods, you can use the following rules:
Wrapping up
The methods on how to bypass UAC highlighted in this article are not the only ones cyber security experts need to be aware of. There are also custom techniques that are difficult to detect, but they’re few and far between, rarely seen in the wild because they’re just as difficult to implement.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, Yara Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
We’ll show you in an interactive presentation how ANY.RUN can help your security team.










0 comments